
In this article, I present a practical lab simulation of the SHELLSHOCK VULNERABILITY, one of the most critical security flaws ever discovered in Unix-based systems.
First identified in 2014, Shellshock exploits a flaw in the Bash shell that allows remote attackers to execute arbitrary commands through improperly sanitized environment variables. By replicating the vulnerability in a controlled environment, this lab provides a hands-on opportunity to understand how Shellshock works, how it can be exploited, and most importantly, how systems can be protected against it.
THE LAB
This article is based on the Lab walkthrough of the related LetsDefend challenge — here’s the link: https://app.letsdefend.io/challenge/shellshock-attack
Now, let’s get deep into it.
We started by performing an initial assessment on the .pcap file, and we found the following:
3 IP addresses are involved in the capture:
→ 10.246.50.2
→ 10.246.50.4
→ 10.246.50.6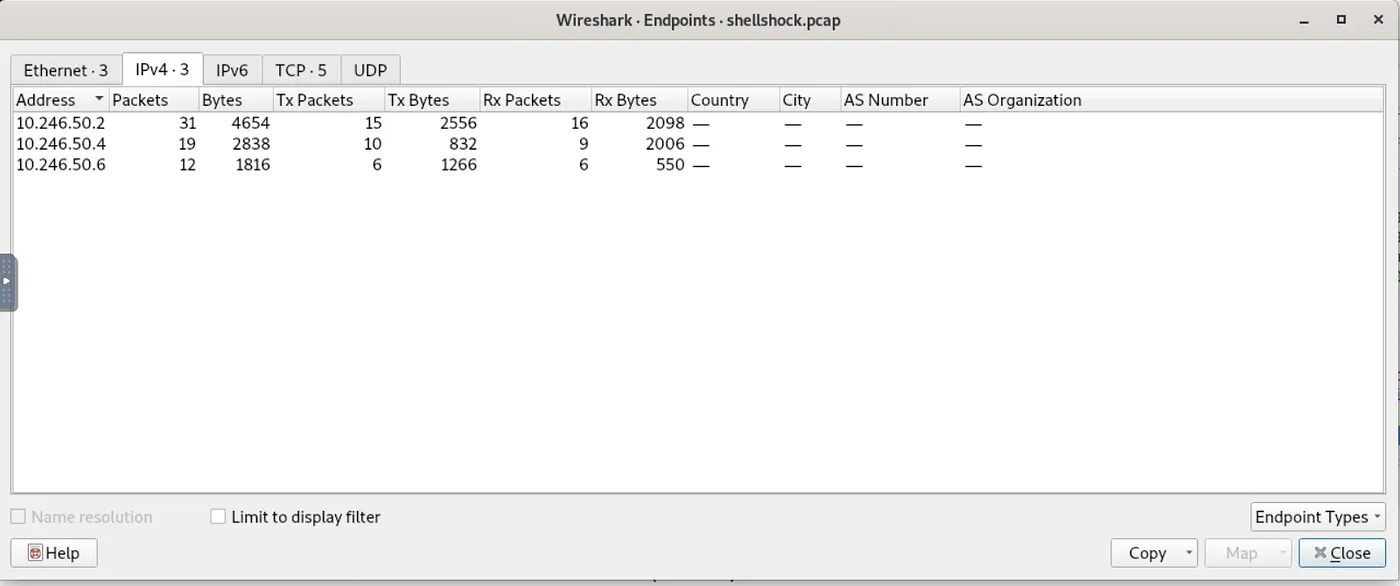
Q1) WHAT IS THE SERVER OPERATING SYSTEM?
First we need to find the server, and to do so we need to analyze the HTTP requests made towards it. We can do so by applying the filter http in the filter bar and discover the following:
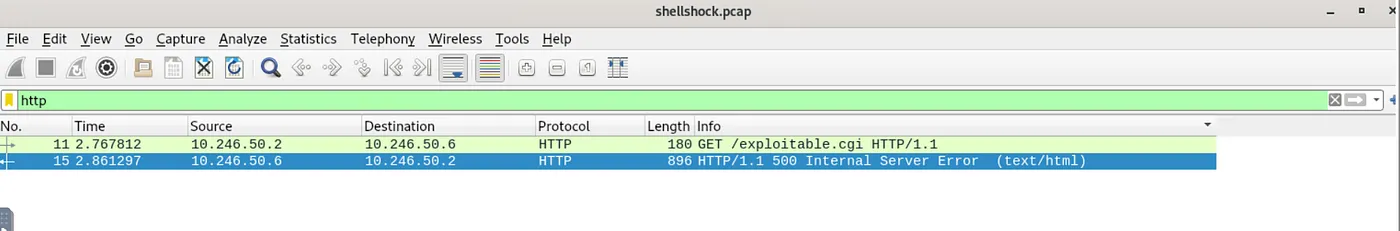
We can see the packet n.15 displays a 500 Internal Server Error and by further analyzing it, we now know that the IP address 10.245.58.2 is indeed our server, and we discover the that the machine runs on Unix OS, in this case UBUNTU.
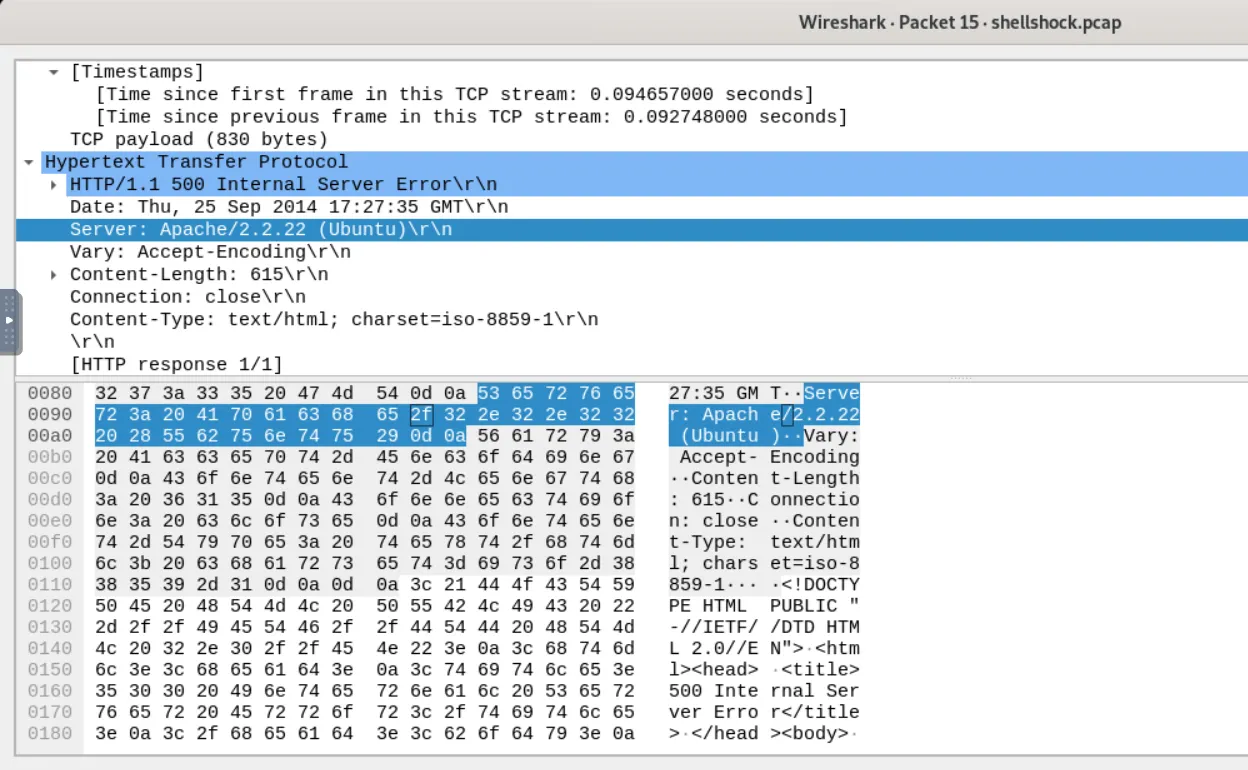
Q2) WHAT IS THE APPLICATION SERVER AND THE VERSION RUNNING ON THE TARGET SYSTEM?
The information is contained in the packet we have analyzed in the previous question: APACHE/2.2.22
Q3) WHAT IS THE EXACT COMMAND THE ATTACKER WANTS TO RUN ON THE TARGET SERVER?
First we need to further document on the methodology of the Shellshock attack by performing a web research. For this matter I’ve used reputable resources from:
WIKIPEDIA → https://en.wikipedia.org/wiki/Shellshock_(software_bug)
NIST → https://nvd.nist.gov/vuln/detail/CVE-2014-6271
CLOUDFLARE Blog → https://blog.cloudflare.com/inside-shellshock/
We can find that the attack was identified in 2014 and given the initial identifier CVE-2014–6271 — involving the creation of a specially crafted environment variable containing an exported function definition, followed by arbitrary commands. These scripts often handle incoming HTTP requests, including headers like User-Agent, Referer, Cookie, etc., and with this, Bash incorrectly executes the trailing commands when it imports the function.