
An application which tricks user to subscribe to or purchase content via their mobile phone bill or subscribes/purchase automatically and unbeknownst to the user.
Toll fraud makes mobile subscription charges through Direct Carrier Billing(DCB), specifically WAP billing. Also there are other type of toll frauds like:
- SMS Fraud
- Sending SMS message to premium number
- Call Fraud
- Making calls premium numbers
One of the most famous malware families is Joker which do toll fraud.
What is WAP billing
WAP billing is a mechanism for consumers to buy content from Wireless Application Protocol (WAP) sites that is charged directly to their mobile phone bill. It is an alternative payment mechanism to debit or credit cards and premium SMS for billing. Using WAP billing, consumers can buy mobile content without registering for a service or entering a username or password. The user clicks on a link and agrees to make a purchase, after which they can download content.
WAP billing is particularly associated with downloading mobile entertainment content like ringtones, mobile games and wallpapers. Some commentators have suggested it could compete with Premium SMS as a leading payment channel for mobile content.
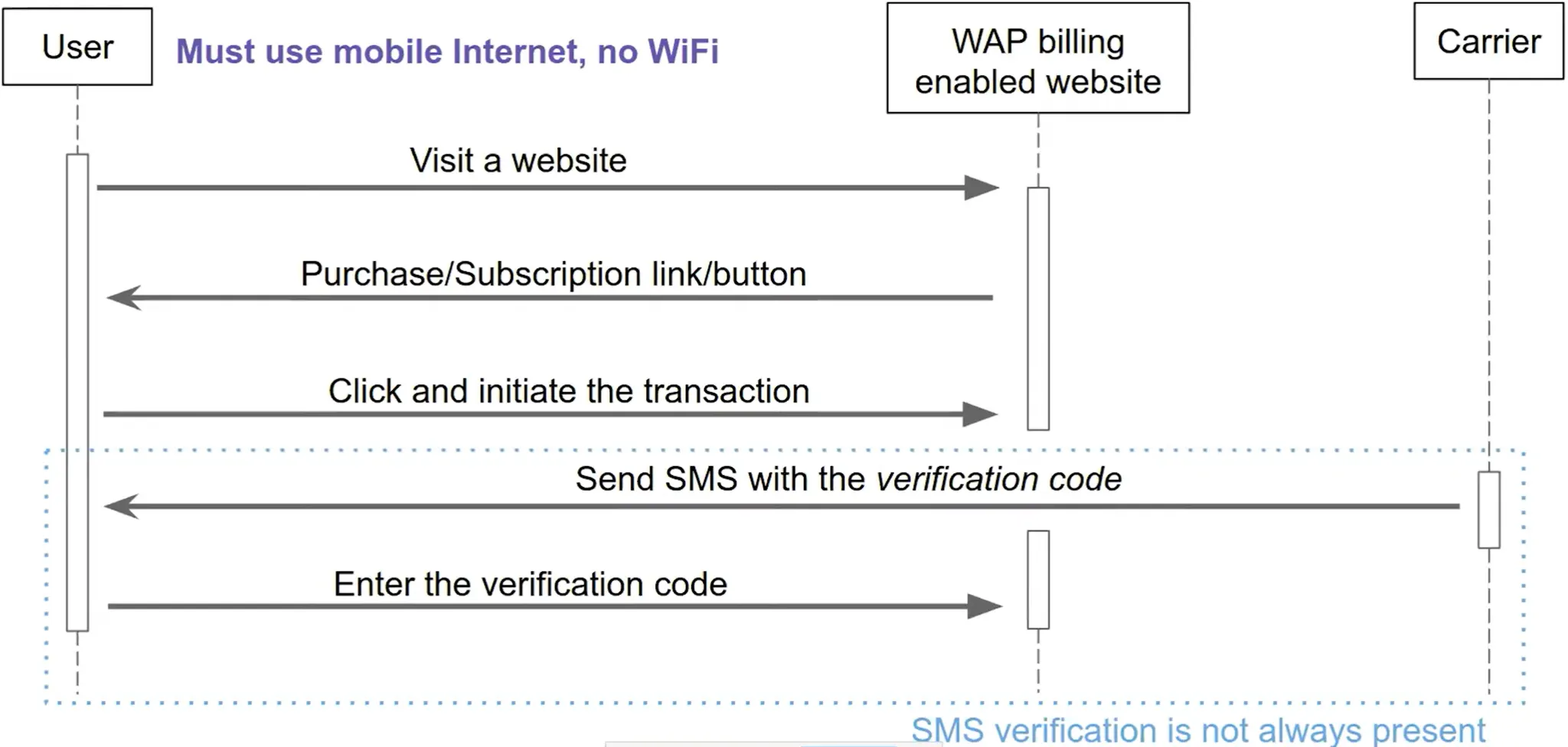
WAP billing
The simple flow of WAP billing:
<aside>
💡 For WAP payment the user must connected to internet by mobile network and not Wi-Fi. It’s clear why.
</aside>
How to find Sim card Operator
fun gettingSimOperator(){
val tm = context.getSystemService(Context.TELEPHONY_SERVICE) as TelephonyManager
Log.v("SimOperator", "[+] Sim Operator Code: ${tm.simOperator}")
Log.v("SimOperator", "[+] Sim Operator Name: ${tm.simOperatorName}")
Log.v("SimOperator", "[+] Network Operator Name: ${tm.networkOperatorName}")
}
The upper code returns the MCC+MNC (mobile country code + mobile network code) of the provider of the SIM.
The output:
2023-09-05 14:07:08.154 10892-10892 SimOperator lab.seczone64.commondevicechecks V [+] Sim Operator Code: 310260
2023-09-05 14:07:08.155 10892-10892 SimOperator lab.seczone64.commondevicechecks V [+] Sim Operator Name: T-Mobile
2023-09-05 14:07:08.155 10892-10892 SimOperator lab.seczone64.commondevicechecks V [+] Network Operator Name: Android
The Approach
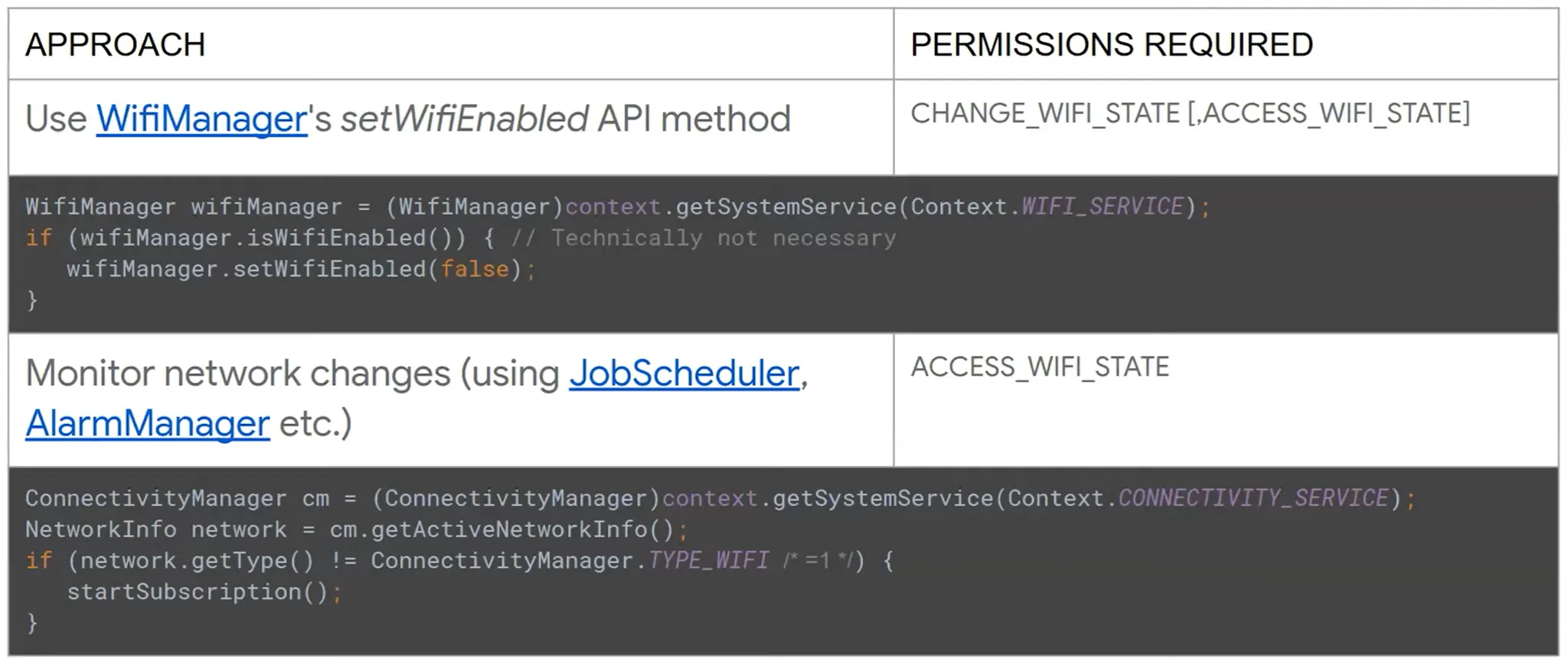
The malware try to disable your Wi-Fi.
The malware open a WAP support website in WebView and do automation by injecting JavaScript to WebView.
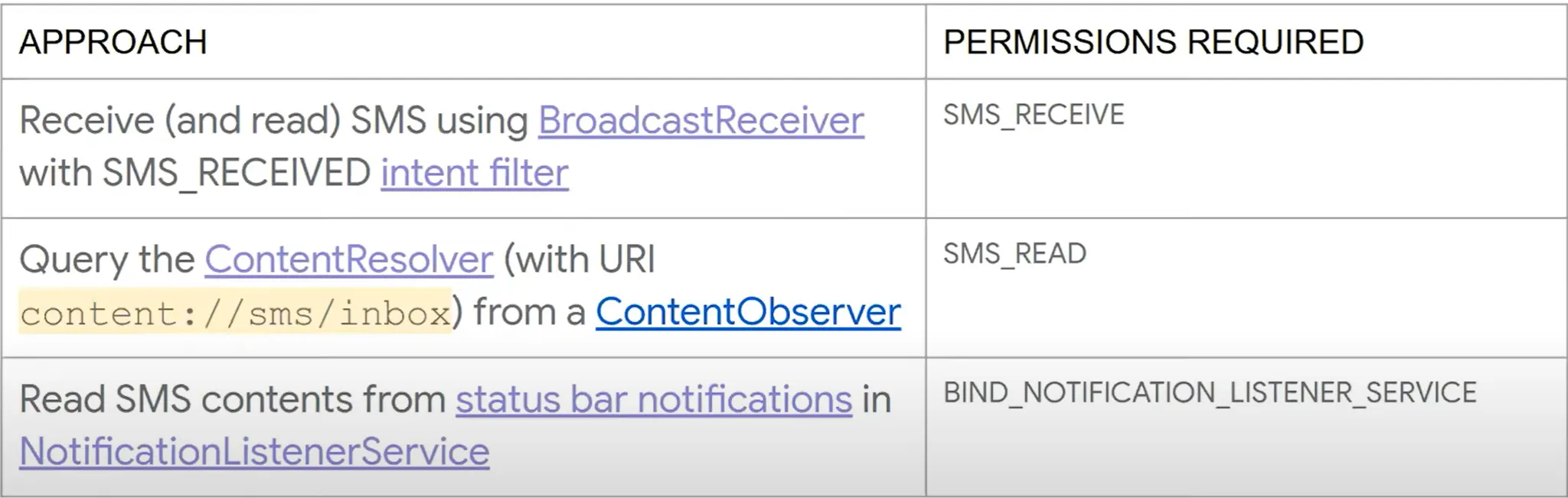
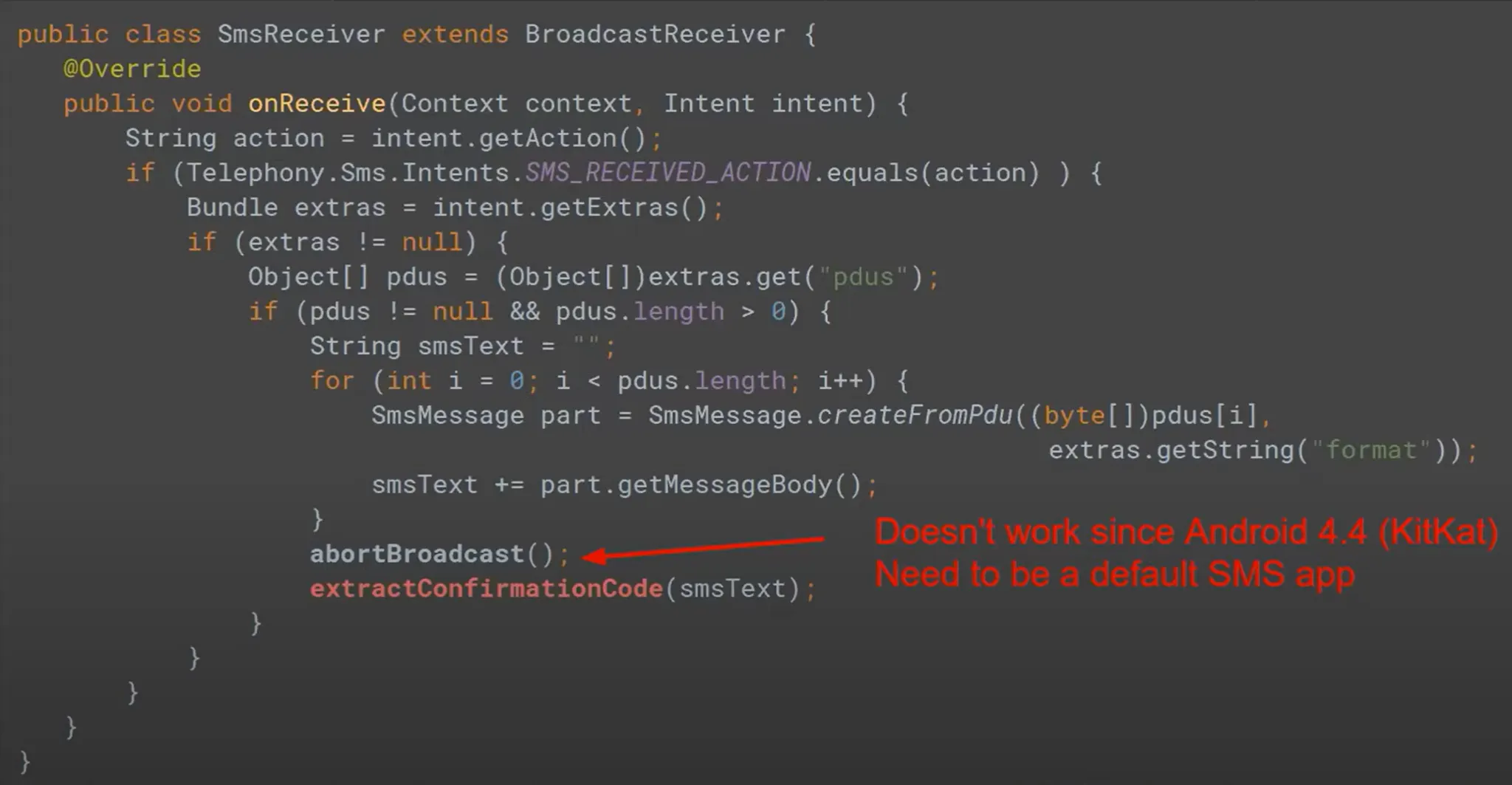
The malware read the confirm SMS.
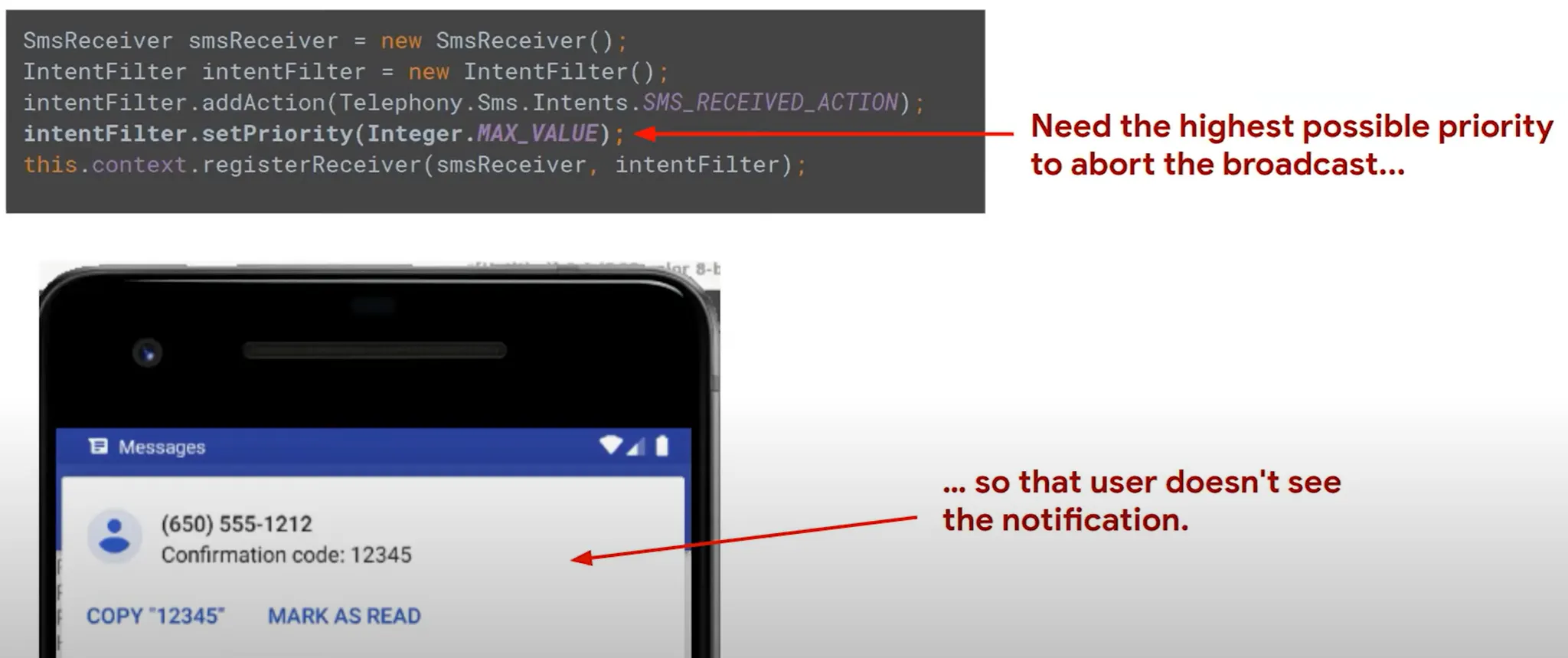
Note: Some malware try to delete or don’t show the confirm SMS. It’s hard task after android 4.4 KitKat.
Done. You will pay on you mobile bill.