
TEXT INJECTION ATTACK
TEXT INJECTION : Content spoofing attack also known as “content text injection” , “arbitary text injection” or “Virtual defacement” is an attack used by the attackers to modify the website to and that can lead the user to a very intense attack like phishing, And also this a client side attack and its severity is low but it can be lead to attack like xss (cross site scripting) content spoofing attack would be to present false information to a user via text manipulation commonly scammers were use this vulnerability.
Text injection can be easily found if:
User input via parameter or directly in the URL is reflected in the page response.
Content-Type: text/plain.
Application is giving default error pages.
EASY STEPS FOR TEXT INJECTION EXPLOITATION:
An attacker identifies a web application that gives recommendations to its users on whether they should buy or sell a particular stock
The attacker identifies a vulnerable parameter
The attacker crafts a malicious link by slightly modifying a valid request
The link containing the modified request is sent to a user and they clicks the link
A valid webpage is created using the attackers malicious recommendation and the user believes the recommendation was from the stock website.
Attack scenario
url : http://www.iffcokandla.in/data/polopoly_fs/1.2503303.1438121378!/fileserver/file/515806/filename/image.png
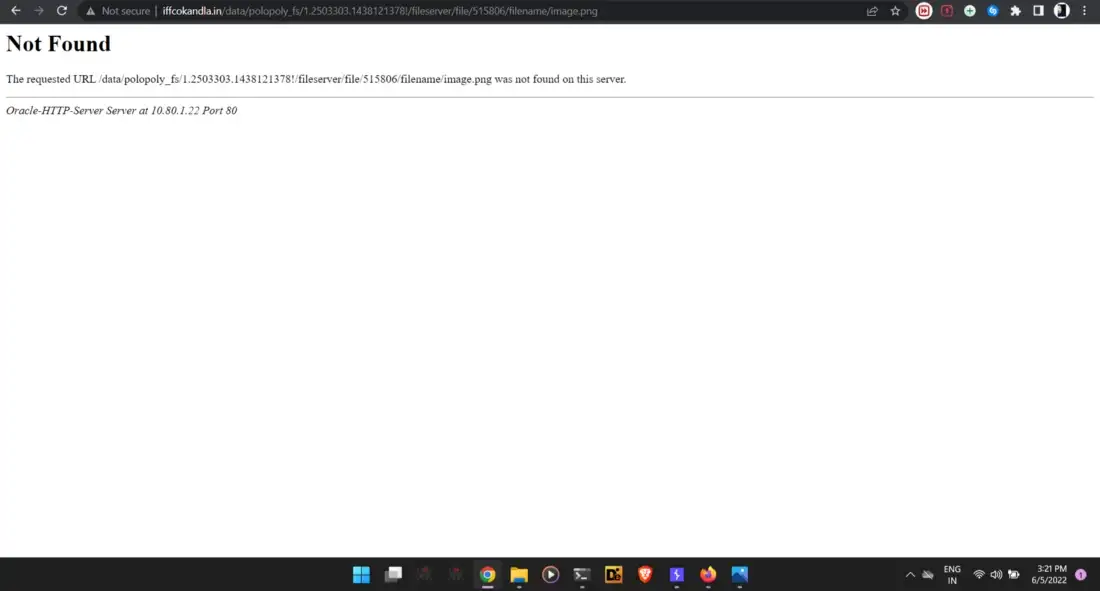
How to do it ?
simply edit the error page url like this.
edited url : http://www.iffcokandla.in/data/polopoly_fs/1.2503303.1438121378!/fileserver/file/515806/filename/image.png/%20please%20visit%20%22evil.com%22%20beacuse%20the%20link%20
now its look like this.
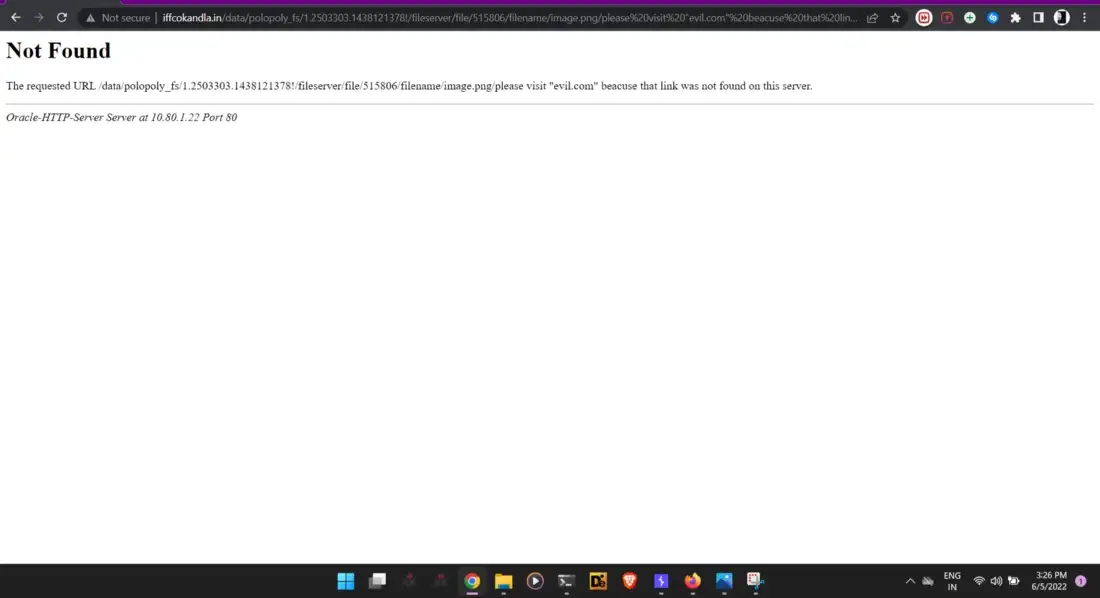
Impact
- An attacker identifies a web application that gives recommendations to its users on whether they should buy or sell a particular stock
- The attacker identifies a vulnerable parameter
- The attacker crafts a malicious link by slightly modifying a valid request
- The link containing the modified request is sent to a user and they clicks the link
- A valid webpage is created using the attackers malicious recommendation and the user believes the recommendation was from the stock website.
How to prevent
- Avoid use of displaying messages via request parameters, instead use temporary sessions.
- Validate the data which are reflecting via request parameter.
- Avoid passing HTML data through request parameter, if you really need it, use proper encoding before passing.
Profile links:
https://www.instagram.com/ved4vyasan/
https://www.linkedin.com/in/vedavyasan-s-a9825b228/
https://twitter.com/ved4_vyasan