
Wireless Networks
As the name of Wireless itself suggests, it is such a Network in which no wires are used, hence it is called Wireless Network. The Wifi we use at home or office is a Wireless network.
WIFI has been named IEEE 802.11 standards. IEEE is an organization that works to standardize networks. Wireless communication works through radio channels.
Wireless Encryptions
1.WEP Encryption
Let us first know about WEP encryption, the full name of WEP is Wired Equivalent Privacy, WEP is a very weak encryption that Attackers can crack easily, so you should never enable WEP.
WEP uses a 24-bit Initialization Vector (IV) to form stream cipher RC4 for Confidentiality and the CRC-32 Checksum for the integrity of Wireless transmission
In today’s time, you get WEP disabled by default because it gets hacked very easily, so you get to see the use of WPA or WPA2 only.
If WEP is 64-bit then it uses a 40-bit key similarly WEP is 128-bit then it uses a 104-bit key and if WEP is 256-bit then it uses a 232-bit key. Cipher RC4 Encryption is used in WEP Network.
2.WPA Encryption
WPA uses TKIP (Temporal Key Integrity protocol). It uses RC4 Cipher Stream Encryption. Which is more difficult to crack than WEP and also PSK and EAP authentication have been used in it.
You get to see WPA encryption and WPA2 in today’s time, if you have wifi in your house then if you check its encryption then you will get that too WPA or WPA2 only.
3.WPA2 Encryption
WPA2 is considered a strong WIFI Network. Which is very difficult to crack. There are ways to HACK WIFI with WPA2 SECURITY.
But there are some ways like this. By using WIFI with WPA2 security can be easily hacked. In today’s time, WPA2 WIFI Network is most commonly used.
But still, hackers hack them, you will be told about it. But you should never do this, AES Encryption is used in WPA2 WIFI. Which cannot be easily cracked. Encryption of WPA or WPA2 WIFI has a 128-bit key.
Wireless Threats: Access Control Attacks
You must know about Wireless Threats in Hacking Wireless Networks. Wireless Access Control Attacks aim to penetrate a network by evading WLAN Access Control measures, such as AP MAC Filters and Wi-Fi Port access controls.
• War Driving
• Rouge Access points
• MAC Address Spoofing
• AP Misconfiguration
• Ad Hoc Associations
• Promiscuous Client
• Client Misconfiguration
• Unauthorized Association
• Wireless Threats: Integrity Attacks
In Integrity Attacks, attackers send forged control, the management or data frames over a wireless network to misdirect the wireless devices in order to perform another type of attack (e.g DOS).
• Data Frame Injection
• WEP Injection
• Bit-Flipping Attacks
• Extensible AP replay
• Data Replay
• Initialization Vector Replay Attacks
• RADIUS Replay
• Wireless Network Viruses
Wireless Threats: Confidentiality Attacks
These attacks attempt to intercept confidential information sent over wireless associations, whether sent in clear text or encrypted by Wi-Fi Protocols.
• Eavesdropping
• Traffic Analysis
• Cracking WEP Key
• Evil Twin AP
• Honeypot Access Point
• Session Hijacking
• Man-in-the-middle attack
• Masquerading
Wireless Threats: Availability Attacks
Denial-of-service attacks aim to prevent legitimate users from accessing resources in a Wireless Network.
• Access Point theft
• Denial-of-service Attacks
• Beacon Flood Attack
• Routing Attacks
• Power saving Attacks
• ARP cache poisoning Attacks
• TKIP MIC Exploit
• EAP-Failure
• Disassociation Attacks
• Authenticate Flood
• De-authenticate Flood
Wireless Threats: Authentication Attacks
The Objective of authentication attacks is to steal the identity of Wi-Fi clients, their Personal Information, login Credentials, etc to gain unauthorized access to network resources.
• PSK cracking
• LEAP Cracking
• Identify theft
• Shared key guessing
• VPN Login cracking
• Domain Login cracking
• Password speculation
• Application Login Cracking
Wireless Hacking Methodology
In Hacking Wireless Networks, now we know about Wireless Hacking Methodology, you get many types of attacks for Wifi Hacking like Bruteforce attack, Evil Twin attack, Wifi Jamming attack, Beacon Flood attack, etc.
BruteForce Attack
In Hacking Wireless Networks, first of all, we are telling you about brute force attacks, before this, a Custom Pin attack also comes, which is not used much in today’s time, so you have not been told about it.
Bruteforce attack is used in many places, using this any Wifi can be hacked. In a brute force attack, a list of passwords is used, in which there is a combination of many passwords.If the password matches, then Wifi gets hacked. Hackers first perform brute force attacks only because it is very easy to do, you get such tools in Kali Linux which are easy to use.
You need a lot of patience to do this attack because many passwords are tried in this attack, due to which it takes more time, the speed of the attack depends on the performance of your system.
Evil Twin Attack
There is also an attack in Hacking Wireless Networks, using which hackers can easily hack any Wifi network, which is called the Evil Twin attack.
Evil Twin attack increases the chances of hacking any Wifi. An evil Twin attack is also known as a fake access point attack. You will be told practically about all the attacks mentioned here.Let’s understand the working of an Evil Twin attack like suppose the SSID of our wireless network is named freelearningtech, now here hackers bring down the real network, death authentication attack is used to bring down the network
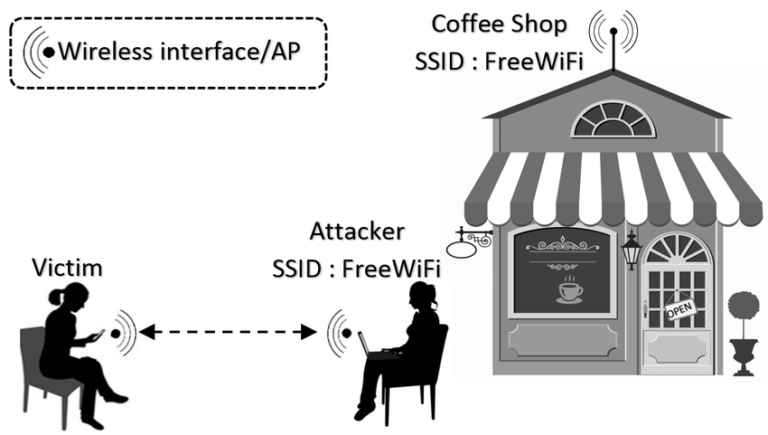
Once the real network is down, all connected devices automatically disconnect and hackers create fake access points with the same name, after which users are shown the fake SSID created by hackers.
After that, when users try to connect to that fake SSID, they are asked for the password again and when users fill in the password, hackers get it, something like this Evil twin attack works
To perform an Evil twin attack, read using two Wifi adapters or you can use a Node MCU and a Wifi adaptor
Wifi Jamming Attack
In a Wifi Jamming attack, hackers can jam any Wifi Network. A wifi Jamming attack can be easily done with the help of Node MCU. Node MCU is used a lot in Hacking Wireless Networks
Beacon Flood Attack
The last attack in Hacking Wireless Networks is being told to you as a Beacon flood attack. In a Beacon flood attack, hackers can confuse the victim by making many fake SSIDs of any SSID.
Like, suppose our Wifi SSID is named Freelearningtech, in the Beacon flood attack hackers can show as many SSIDs as they want with Freelearningtech’s name, this attack is mostly done for fun.
Beacon flood attacks can be done easily with the help of Node MCU, you will also be told practically about all the attacks mentioned here, we hope that you have liked our Hacking Wireless Networks article.
Wifislax
Hacking Wireless Networks also has an operating system in which you get all the tools for Wifi Hacking already installed and which is specially designed for Wireless penetration testing.
The name of this operating system is wifislax, which you easily find on the Internet, it is a unix-based OS. In Hacking Wireless Networks, you must know about wifislax.
Final Words
I hope that now you can know about Wireless Networks, here i have tried our best to tell you more and more about Hacking Wireless Networks.
Profile : Follow me On Instagram