
Hello Everyone…
Lohith Here, (Sr.Security Engineer & Ethical Hacker from Bengaluru). I hope you all are doing well.
This write-up is about the Cloudflare Password Policy Restriction Bypass.
Almost Every organization is following a strong password policy on their application. Sometimes It depends on the product. E.g crypto, banking and e-commerce application. A strong Password policy is compulsory for compliance as well.
I started looking for bugs in the Cloudflare application. This is my 2nd valid report on the Cloudflare Bug Bounty program. The first issue is related to Blind SSRF. The report has already been disclosed.
Cloudflare has a strong password policy in place. It should be 8-character long, with special characters, and numbers, but it’s only on UI. If the attacker intercepts the Signup API Endpoint and he can able to set a weak password for his account.
Exploit Part:
Navigated into the Cloudflare signup/reset page and entered all the details with a strong password on the UI. Then captured the signup request using Burp-Suite (Proxy- tool). Manipulated strong password to weak password ( E.g Hacker@123 to Hacker ).
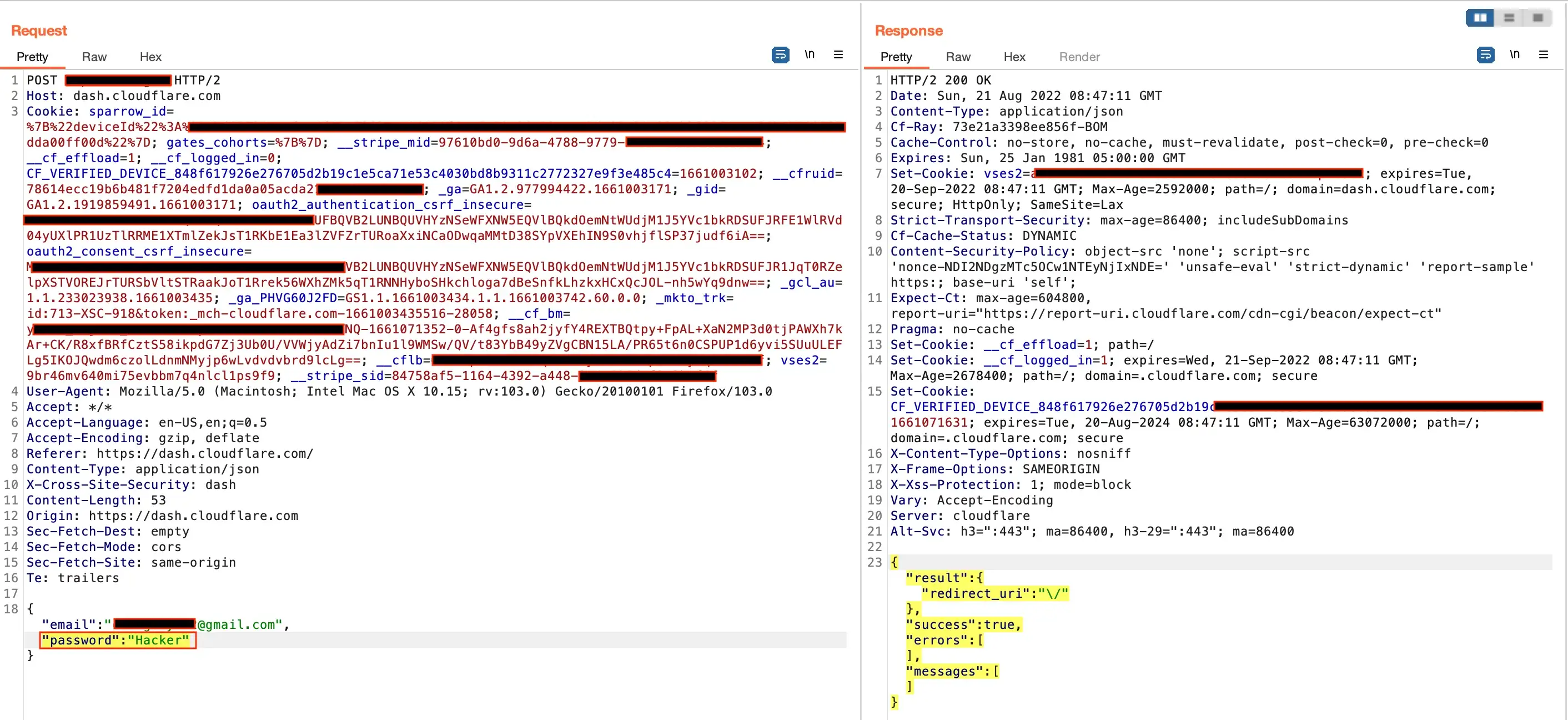
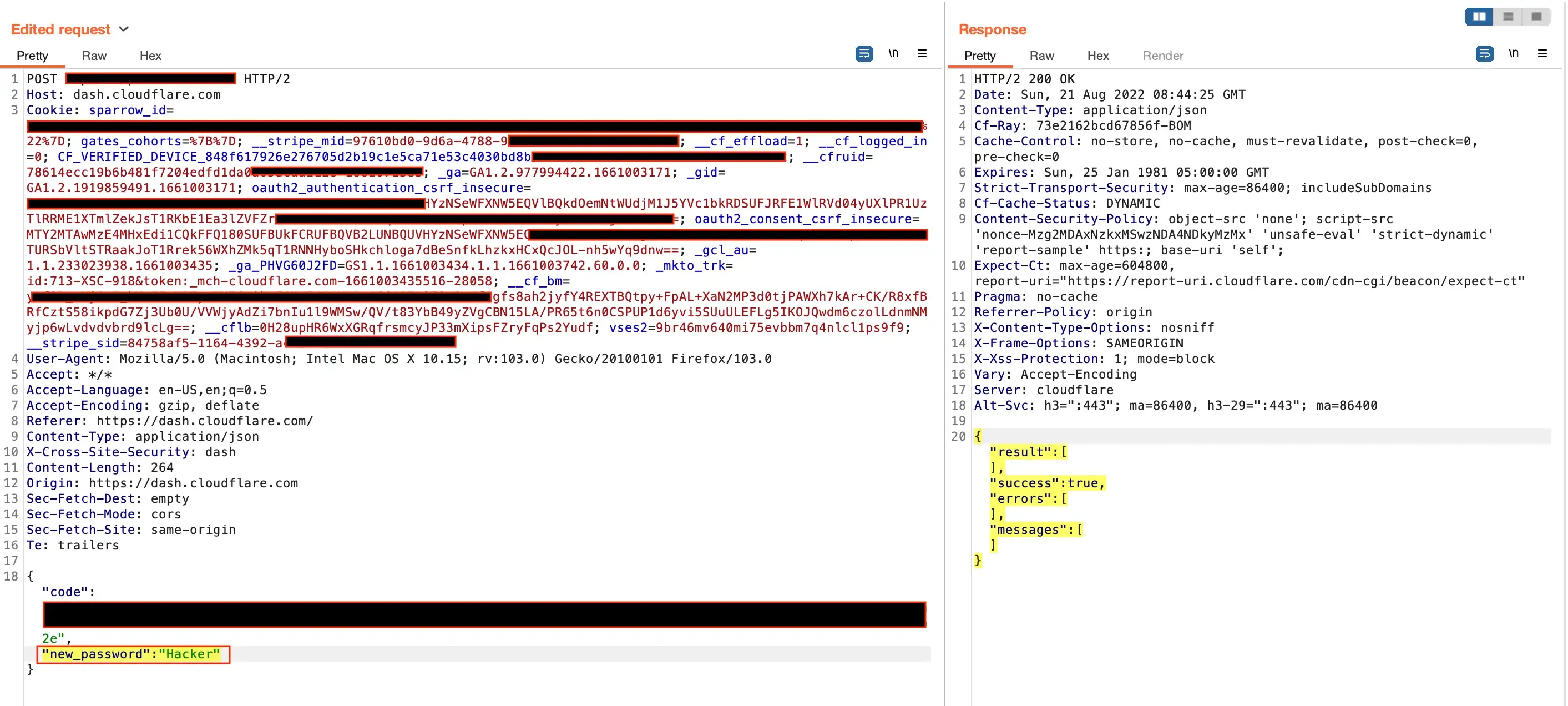
Then I forwarded this request to the server and got a 200 ok response. So my weak password got updated. This way, a user could set up weak passwords for their account. It’s a security and compliance issue.
Report Details:
August 21 — Reported to Cloudflare program on HackerOne
August 22 — Report got triaged
August 23 — Rewarded $200 + $50 bonus for the well-written report.
August 23 — Request for a retest
August 23 — Issue fixed and got a reward of $50 for a retest.
Thanks for reading!….Happy Hacking!