TryHackMe — Warzone 2 Simple Walkthrough with Answers by Karthikeyan Nagaraj | 300 Points as on Dec 2022

Tools and Websites Used for this Exercise
1. Brim
2. Virustotal
3. CyberChef (If Needed)
If You Don’t Know What these tools are, you can check out Below!!!
1. What is Brim?
Brim is an open-source desktop application for security and network specialists. Brim makes it easy to search and analyze data from: packet captures, like those created by Wireshark, and. structured logs, especially from the Zeek network analysis framework.
Brim - GithHub Repository
2. What is Virustotal?
It is a Website used to Analyse suspicious files, domains, IPs and URLs to detect malware and other breaches, and automatically share them with the security community.
Virustotal Website
3. What is Cyberchef?
CyberChef is a simple, intuitive web app for carrying out all manner of “cyber” operations within a web browser.
CyberChef Online Hosted
|___________________________________________ LET’S START THE TASK__________________________________________________|
Task 1 Another day, another alert
1. What was the alert signature for A Network Trojan was Detected?
Open the Brim Application inside Tools Directory
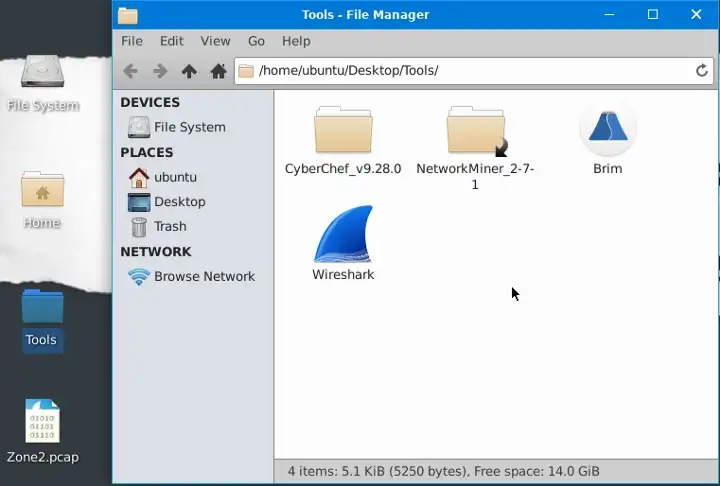
Choose the Zone2.pcap file Available on the Desktop
Click on →Suricate Alerts by Source and Destination Under Query Section
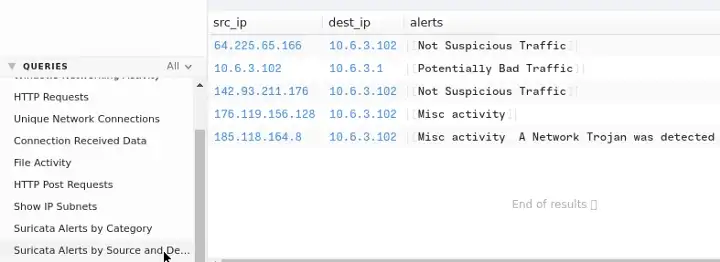
We Have found that the IP 185.118.164.8 is Affected by a Trojan, So Let’s find for any Logs of that IP
Type the IP on the Search Bar
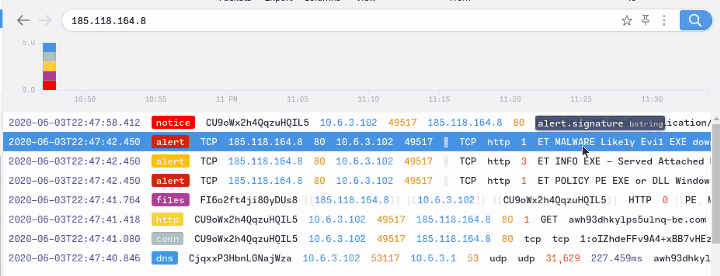
Ans: ET MALWARE Likely Evil EXE download from MSXMLHTTP non-exe extension M2
2. What was the alert signature for Potential Corporate Privacy Violation?

Double Click the Traffic which has the word Policy on Its Signature, to Check the Activity Log
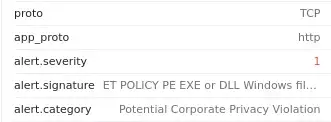
Ans: ET POLICY PE EXE or DLL Windows file download HTTP
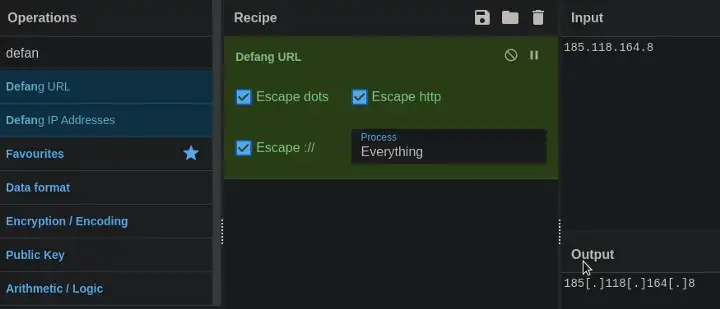
3. What was the IP to trigger either alert? Enter your answer in a defanged format.
The IP we Found on the 1st Question Triggers the Alert, But We Have to Enter the IP in Defanged Manner. You can use the Cyberchef tool to Defang it!
4. Provide the full URI for the malicious downloaded file. In your answer, defang the URI.
Open the Http Traffic
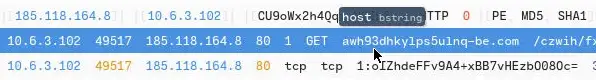
Double Click the Traffic. The Full URL is the Combination of Host and Uri
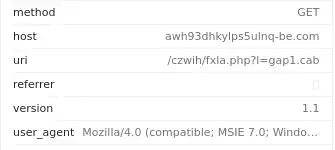
Use Cyber Chef to Defang it
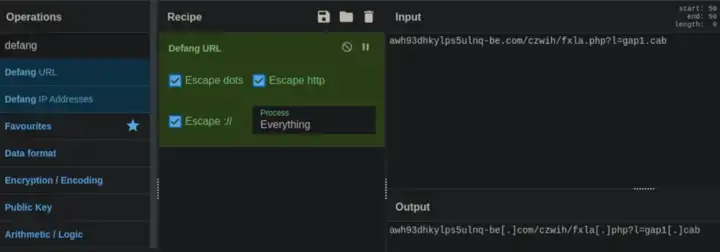
Ans: awh93dhkylps5ulnq-be[.]com/czwih/fxla[.]php?l=gap1[.]cab
5. What is the name of the payload within the cab file?
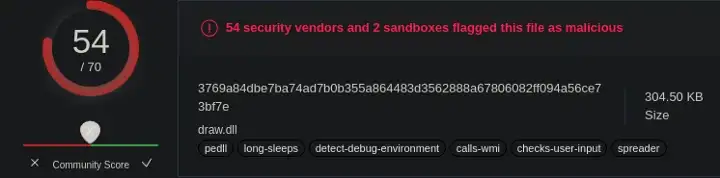
Double-click the traffic tagged Notice and Look Carefully, there’s a Virustotal Link with a Hash. Let’s Search Manually with the hash
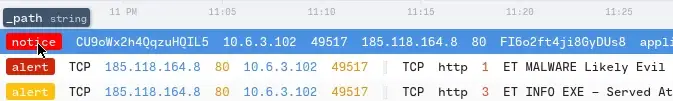
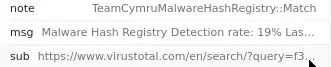
Hash Link - https://www.virustotal.com/en/search/?query=f3e9e7f321deb1a3408053168a6a67c6cd70e114
We Found the Hash — f3e9e7f321deb1a3408053168a6a67c6cd70e114
Search the Hash on Virustotal Manually
6. What is the user-agent associated with this network traffic?
Open the HTTP Traffic to Find the User-Agent
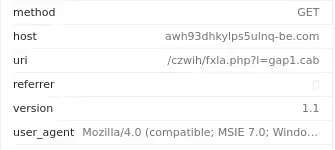
Ans: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 10.0; WOW64; Trident/8.0; .NET4.0C; .NET4.0E)
7. What other domains do you see in the network traffic that are labeled as malicious by VirusTotal? Enter the domains defanged and in alphabetical order. (format: domain[.]zzz,domain[.]zzz)
On the Relations Tab, you can see the Malware Detections of URLs
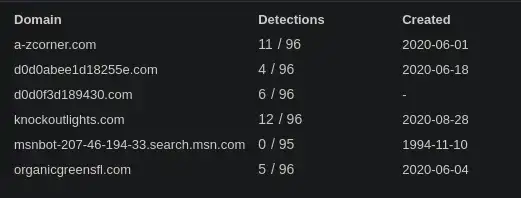
a-zcorner.com
knockoutlights.com
These two URLS are Highly Malicious as it has Highest Detections.
--> We Have to Defang the Urls in Alphabetical Order
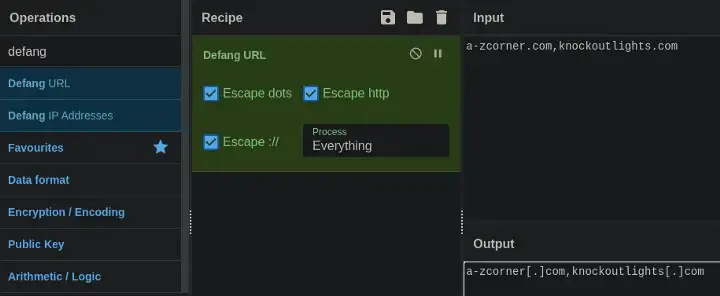
Ans: a-zcorner[.]com,knockoutlights[.]com
8. There are IP addresses flagged as Not Suspicious Traffic. What are the IP addresses? Enter your answer in numerical order and defanged. (format: IPADDR,IPADDR)
Click Suricata Alerts by source and Destination Under Query Section that we Already Found on First Question.
There are two URLS marked Not Suspicious
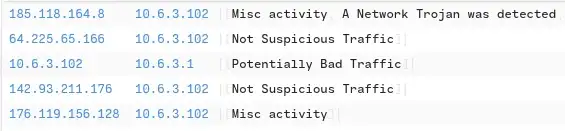
Write the IPs in Defanged Alphabetical Order 64..,142…
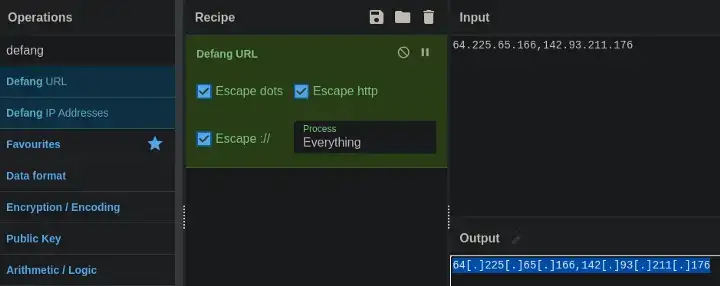
Ans: 64[.]225[.]65[.]166,142[.]93[.]211[.]176
9. For the first IP address flagged as Not Suspicious Traffic. According to VirusTotal, there are several domains associated with this one IP address that was flagged as malicious. What were the domains you spotted in the network traffic associated with this IP address? Enter your answer in a defanged format. Enter your answer in alphabetical order, in a defanged format. (format: domain[.]zzz,domain[.]zzz,etc)
Search the 1st Non-Suspicious IP 64.225.65.166 on Virustotal
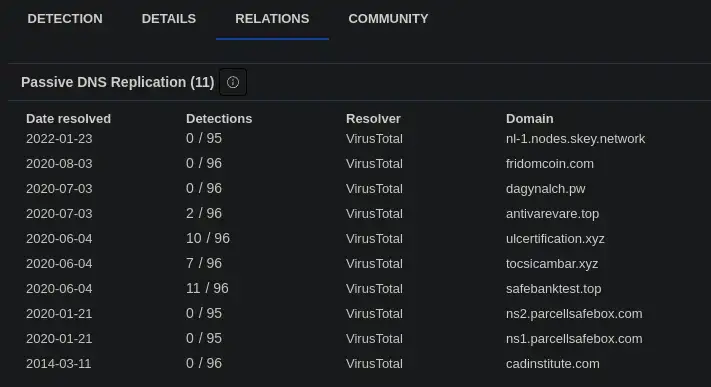
The First 3 Domains based on Detections are the Mal URLS.
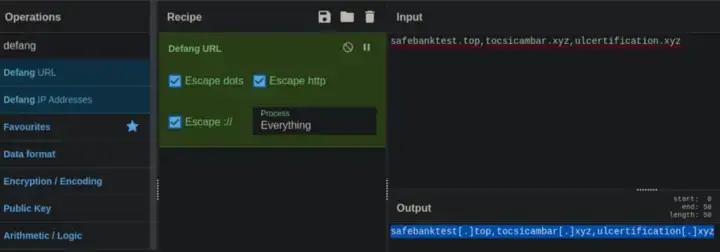
Ans: safebanktest[.]top,tocsicambar[.]xyz,ulcertification[.]xyz
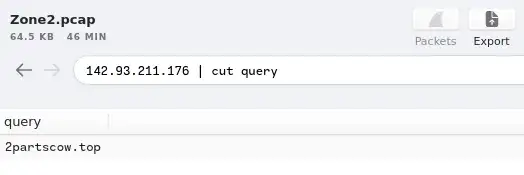
10. Now for the second IP marked as Not Suspicious Traffic. What was the domain you spotted in the network traffic associated with this IP address? Enter your answer in a defanged format. (format: domain[.]zzz)
Now use the Search Query on grim to Find the Domain Related to the 2nd Non-Malicious IP
142.93.211.176 | cut query
Thank you for Reading!!
Happy Hacking ~
Author: Karthikeyan Nagaraj ~ Cyberw1ng
@Hacklido @Cyberw1ng