Introduction:
Privilege escalation is a journey. There are no silver bullets, and much depends on the specific configuration of the target system. The kernel version, installed applications, supported programming languages, and other users’ passwords are a few key elements that will affect your road to the root shell.
What does “privilege escalation” mean?
Privilege Escalation usually involves going from a lower permission account to a higher permission one.
Why is it important?
It’s rare when performing a real-world penetration test to be able to gain a foothold (initial access) that gives you direct administrative access. Privilege escalation is crucial because it lets you gain system administrator levels of access.

Here I’ll first teach you some theory about specific privilege escalation techniques & then hands-on experience on a machine. (For practical I’ll focus on the manual methods for privilege escalations but will mention the automated tools that’ll do some work & saves you time). These techniques are helpful for both Red & Blue Teams.
Also, I refer to a lot of the Tryhackme room: Linux Privilege Escalation
1. Privilege Escalation: Kernel Exploits
Theory
The kernel on Linux systems manages the communication between components such as the memory (RAM, ROM), I/O, CPU on the system and applications. This critical function requires the kernel to have specific privileges; thus, a successful exploit will potentially lead to root privileges.
The Kernel exploit methodology is simple;
Although it sounds simple, remember that a failed kernel exploit can lead to a system crash. Make sure this potential outcome is acceptable within the scope of your penetration testing engagement before attempting a kernel exploit.
Practical
First, we need to find the current kernel version of the target system so we can check if it has any vulnerabilities.

uname -a: Will print system information & kernel used by the system. Format -> Kernel name, Hostname, kernel release | kernel version (3.16.0,5.16.0 etc) Machine (Architecture), NIS.
Now we’ve kernel version (3.13.0), Now let’s go on Exploit-DB.
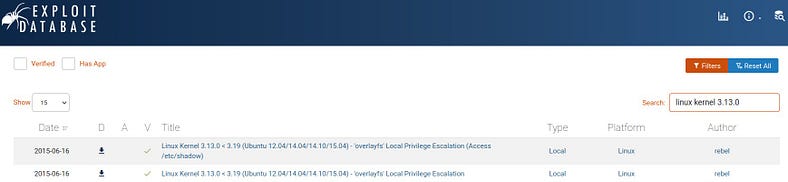
It has some local Vulnerabilities. Check the second one (CVE-2015–1328).
The overlayfs implementation in the linux (aka Linux kernel) package before 3.19.0–21.21 in Ubuntu through 15.04 does not properly check permissions for file creation in the upper filesystem directory, which allows local users to obtain root access by leveraging a configuration in which overlayfs is permitted in an arbitrary mount namespace.
Download the exploit & it’s a C code. Compile the code using GCC etc.

We got the Root access to the system.
Check this tool as it will automatically check the kernel version & list all the vulnerabilities based on priority (if has any) & exploit links so you don’t have to do searching manually.
2. Privilege Escalation: Sudo
Theory
The Sudo command, by default, allows you to run a program with root privileges. Under some conditions, system administrators may need to give regular users some flexibility on their privileges. For example, a junior SOC analyst may need to use Nmap regularly but would not be cleared for full root access. In this situation, the system administrator can allow this user to only run Nmap with root privileges while keeping its regular privilege level throughout the rest of the system.
The sudo methodology is simple;
1. Identify the program that which user can run via root or any other user privileges.
2. Search & find an exploit for that program of the target system.
3. Run the exploit to gain user privileges.
Practical
Check the privileges level of the current user in the target system.
sudo -l: The target system may be configured to allow users to run some (or all) commands with root or other users’ privileges. This command can be used to list all commands your user can run using sudo.
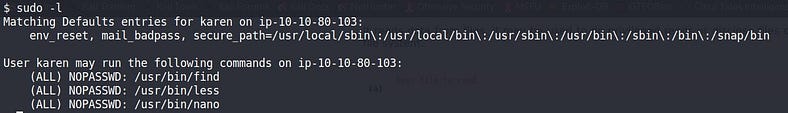
Here, in this case, our current user can run 3 binaries/programs.

I ran a system call exec to spawn a shell that can be used in the find program as an optional parameter. Here since find is running as ROOT privileges so whatever we run on it will get executed as ROOT privileges.
GTFOBins is a curated list of Unix binaries that can be used to bypass local security restrictions in misconfigured systems. Helps in breaking out restricted shells, escalating or maintaining elevated privileges, transferring files, spawning bind and reverse shells, and facilitating the other post-exploitation tasks.
3. Privilege Escalation: SUID
Theory
SUID or Set Owner User ID is a permission bit flag that applies to executables. SUID allows an alternate user to run an executable with the same permissions as the owner of the file instead of the permissions of the alternate user. So for example, There’s a security team & one of the team members JOHN wanted to share this program with his members but the problem is he doesn’t want to share his account password or add all his team members to Sudo entry so they can run it with JOHN privileges what he’ll do is set a SUID bit on his program so whenever his team member will run his program, it’ll get executed with JOHN privileges only for that particular program.
The SUID methodology is simple;
1. Identify the program that has a SUID bit set
2. Search & find an exploit for that program of the target system.
3. Run the exploit to gain user privileges.
Practical
Let’s first find the SUID bit set programs that are under ROOT.
find -perm -4000: will list files that have SUID bits set.

You’ll normally get a lot of SUID bit set programs like at,su, passwd, and mount, etc but they are less prone to any vulnerabilities. Here I found the base64 program which is used to convert the data into base64 or decode it into ASCII/UTF-8.
So what I can do here is read any file from the system with root privileges as this program is root suid bit set.
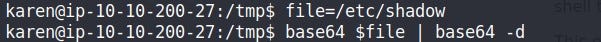
Just create a local environment variable & assign any file you want, run the base64 program & pass the parameter of the name as our local environment variable name.
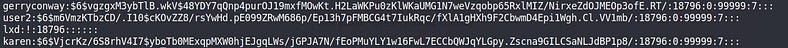
It’ll encode it with base64, and pass that output using PIPE to the base64 decoder & as a result of that, we can read the content of any file with ROOT privileges.
Part 2 ->