Hello Guys..!!
Happy New Year 2023 to all my followers 🥳
Hope you are doing well
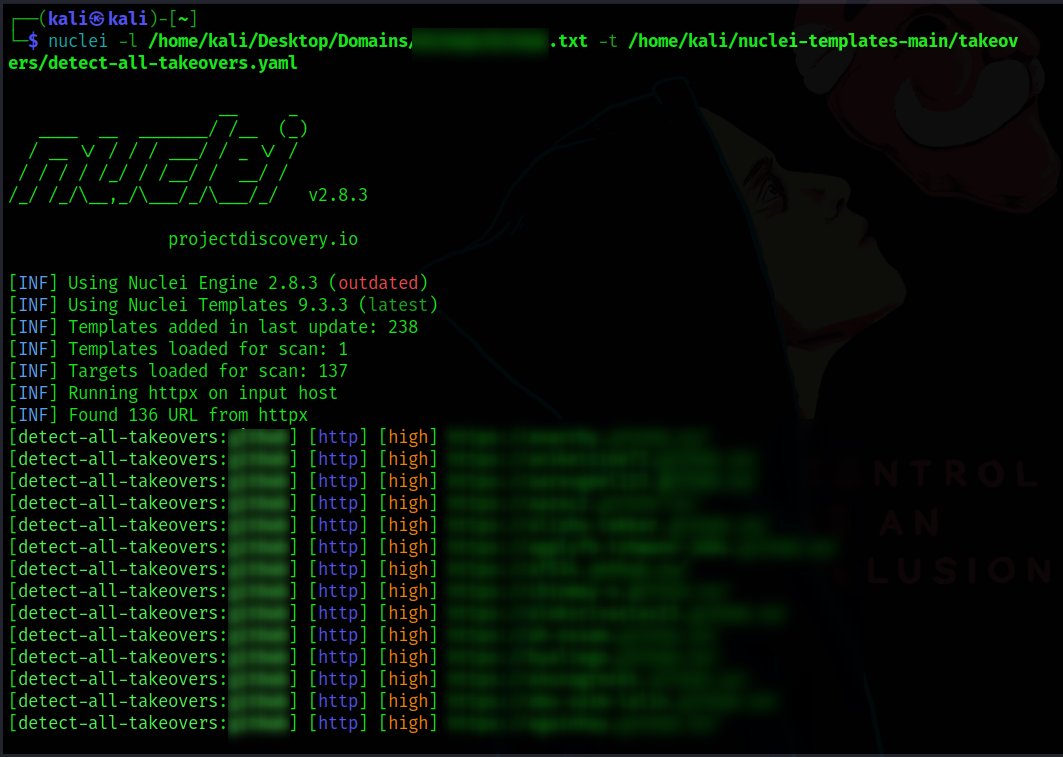
Today we are going to discuss about how I was able to find 136 Sub-domain Takeover vulnerabilities using the Nuclei tool.
Note-1:
For Privacy and Security reasons I am not going to reveal the target domain and the sub-domains which I have collected.
Note-2:
This Article is only for demonstration and education purpose. (So, Don’t ask whether I have reported any of these findings)
Let’s Start without wasting any more time.
I have chosen a random target “domain.com” and collected all the sub-domains using the tool “Subfinder” and saved them into a text file as shown below (Let’s assume google.com as my target)
subfinder -d google.com -o /path/to/google.txt
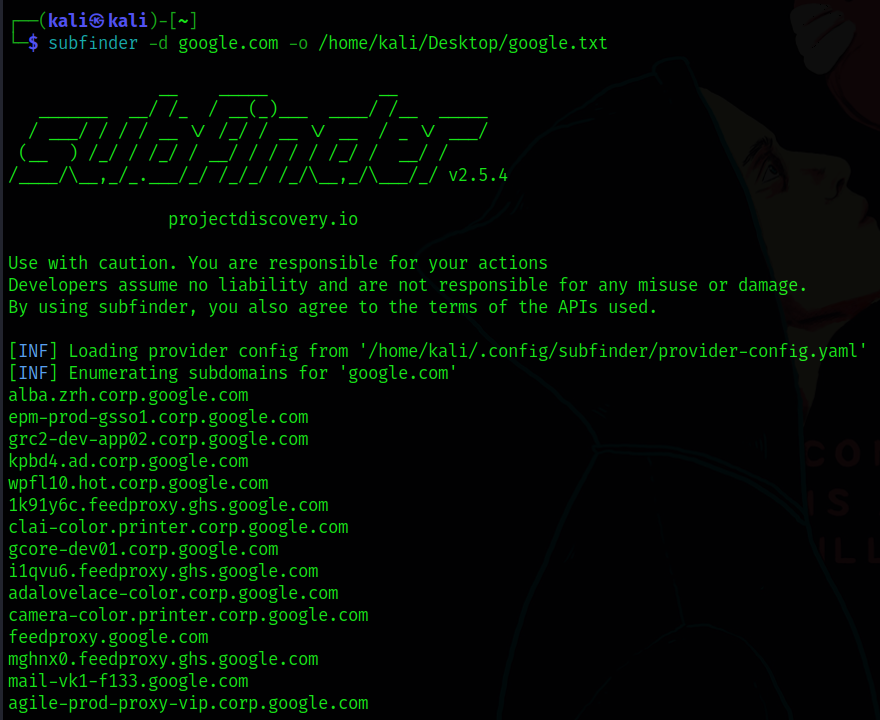
Now I wanted to find a sub-domain takeover vulnerability on the target list which I have collected above.
I wanted to use the Nuclei tool for testing sub-domain takeover vulnerability due to the popularity of the tool.
So Instead of checking each and every sub-domain for takeover, I wanted to automate the process which made me research about the nuclei templates.
So I was looking for a template which can detect sub-domain takeover on the most popular websites where I found about a template called “detect-all-takeovers.yaml”.
So I have tested sub-domain takeover vulnerability on all the sub-domains which I collected earlier using the above nuclei template which gave me 136 Vulnerable sub-domains as shown below.
nuclei -l path/to/subdomains.txt -t /home/parrot/nuclei-templates-main/takeovers/detect-all-takeovers.yaml
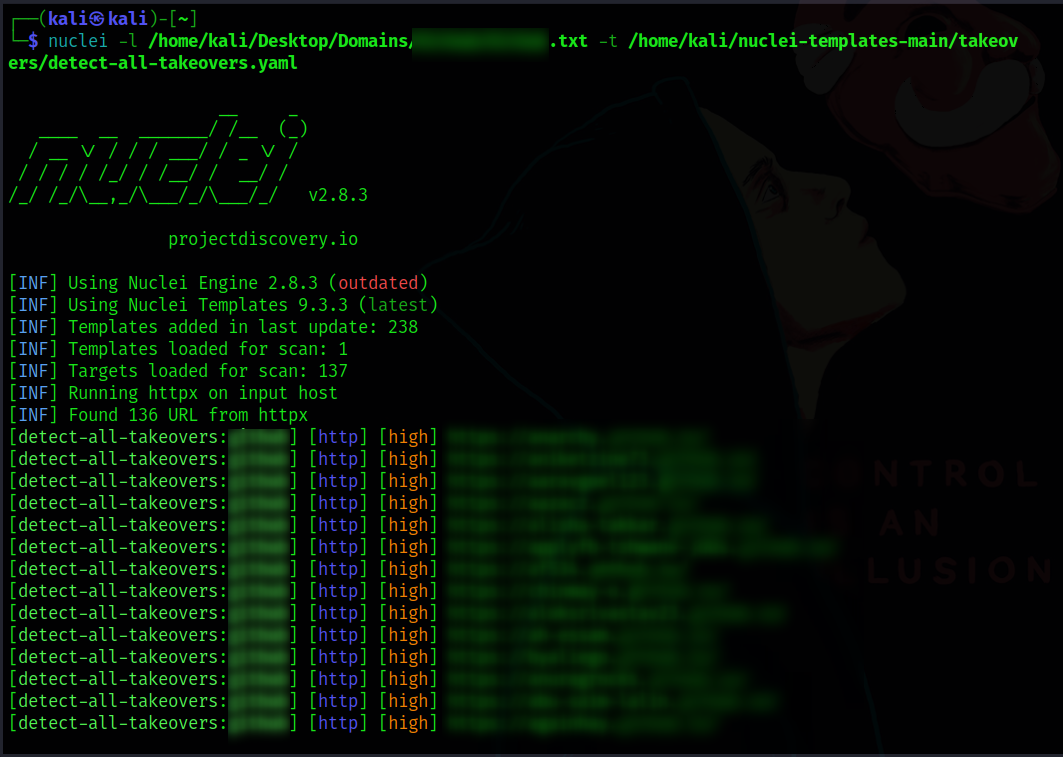
Note-3:
There may be false positives in the tool results. So I recommend checking all the vulnerable sub-domains manually to validate them using the reference article.
So, That’s it for today
Thank you guys for Reading this Post — Happy Hunting 🐞
If this post has helped you in any way, don’t forget to give me a like 🤍
Support me: If you like to support me, buy me a cup of coffee ☕
Follow me: @0xKayala | Satya Prakash