Sub-domain takeover vulnerabilities occur when a sub-domain (e.g., ‘subdomain.example.com’) is pointing to a third-party service (e.g., GitHub pages, Heroku, etc.) and the third-party service is no longer being used by the organization that owns the main domain (e.g.,‘ example.com’). This can allow an attacker to set up a page on the third-party service and essentially “take over” the sub-domain, potentially leading to phishing attacks or other malicious activity.
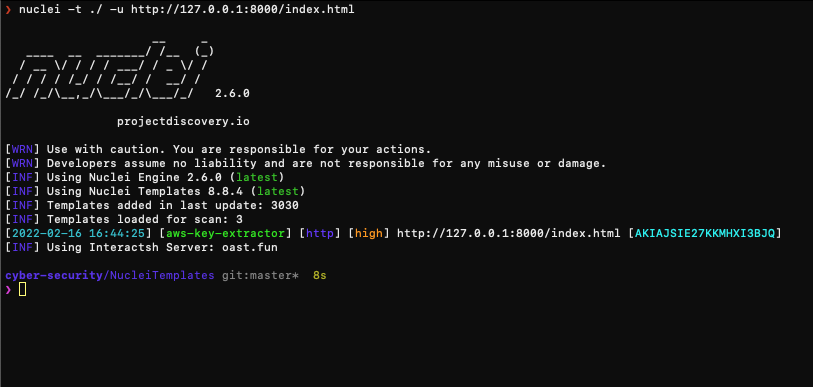
To find sub-domain takeover vulnerabilities, one approach you can use is to use a tool called Nuclei. Nuclei is a fast and powerful tool that can be used to scan websites and discover vulnerabilities.
To use Nuclei to find sub-domain takeover vulnerabilities, you will first need to install the tool and then follow these steps:
Run Nuclei with the ‘-t’ flag and specify the target domain(s) you want to scan. For example: ‘nuclei -t example.com’. This will scan the specified domain and its sub-domains for potential vulnerabilities.
Use the ‘-l’ flag to specify a list of sub-domains you want to scan. This can be a list of known sub-domains, or you can use a tool like ‘subfinder’ to enumerate sub-domains.
Use the ‘-x’ flag to specify a list of templates to use for the scan. Nuclei comes with a number of built-in templates for common vulnerabilities, including a template for sub-domain takeover vulnerabilities.
Run the scan and wait for it to complete. Nuclei will output any potential vulnerabilities it finds, including any sub-domain takeover vulnerabilities.
By following these steps, you should be able to use Nuclei to discover sub-domain takeover vulnerabilities in your target domain(s). It’s important to note that finding vulnerabilities is only the first step – you will also need to take appropriate action to fix any vulnerabilities you discover.
Here is an example of how you could use Nuclei to find sub-domain takeover vulnerabilities in a live environment:
Install Nuclei by following the instructions on the official Nuclei GitHub page (https://github.com/projectdiscovery/nuclei).
Enumerate a list of sub-domains for the target domain. You can use a tool like ‘subfinder’ for this purpose.
Create a list of sub-domains in a text file, with each sub-domain on a new line.
Run Nuclei with the ‘-t’ flag to specify the target domain, the ‘-l’ flag to specify the list of sub-domains, and the ‘-x’ flag to specify the sub-domain takeover template. For example:
nuclei -t example.com -l subdomains.txt -x
templates/takeovers/subdomain-takeover.yaml
- Wait for the scan to complete. Nuclei will output any sub-domain takeover vulnerabilities it finds.
It’s important to note that finding vulnerabilities is only the first step – you will also need to take appropriate action to fix any vulnerabilities you discover. This may involve contacting the third-party service and asking them to remove the sub-domain, or reconfiguring your DNS settings to prevent the sub-domain from pointing to the third-party service.