
🎥 In late November 21, 2014 - Sony Pictures Entertainment was hacked by a group of hackers. They leaked a release of confidential data from the film studio like personal information about Sony Pictures employees and their families, emails between employees, information about executive salaries at the company, copies of then-unreleased Sony films, plans for future Sony films, scripts for certain films, and other information.
But, Why to hack Sony Pictures Entertainment? The group demanded Sony to withdraw its upcoming film - The Interview, A comedy about a plot to assassinate North Korean leader Kim Jong-un. The group threatened terrorist attacks at cinemas screening the film. After many major U.S. theater chains opted not to screen the film in response to these threats, Sony chose to cancel the film’s formal premiere.
So this turned up like resistance against the release of this film and apparently this made everyone thought that the hacker group must have emerged from North Korea. After evaluating the software, techniques, and network sources used in the hack, United States intelligence officials alleged that the attack was sponsored by the government of North Korea, which has since denied all responsibility.
But hackers and computer experts questioned the narrative - So there’s room for doubt! Is it really North Korea?
All this chaos started on a very fine morning when the Sony executives received an email from an unknown group so-called “God’sApstls” demanding “monetary compensation” or otherwise, “Sony Pictures will be bombarded as a whole”. This email was treated as spam and was ignored by most of the executives. But the game was already played - malware got activated by that time of interaction with the email and it started to spread in every possible network connection stealthily.
All hell broke loose when a group calling themselves the Guardians Of Peace [GOP] appeared on Sony computers. Within a few weeks mountain of data including movies, salaries, and private emails got dumped on the internet. Not only salacious emails of top executives but also sony employees’ social security numbers, and medical records got leaked online.
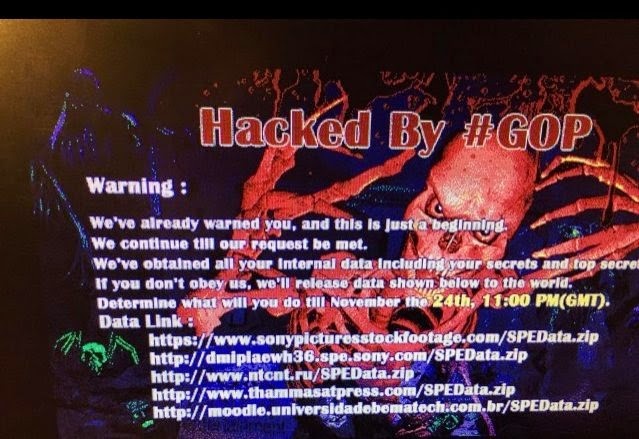
The White House did not make the discussion about the evidence, but the FBI came up with some details. It was the first time a president has blamed a Nation-state for a major cyber attack on American soil.
The FBI announced today that… And we can confirm that North Korea engaged in this attack.
Bret Leatherman is a Special Agent in the FBI’s Cyber Division. Based on what’s publicly known, the hack seems to have gone down in four phases.
- Phase 1 - Spear Phishing.
- Phase 2 - Privilege Escalation.
- Phase 3 - Data Theft.
- Phase 4 - Data Destruction.
First - Spear phishing, was likely how the hackers got into Sony. Somebody within a company or organization would receive an email that looks like a legitimate email that might contain an attachment or a link to a website and once you click on it, you may be directed to a malicious site or you could have triggered a malicious program to run in your computer and thus compromising yourself. For hackers, it is like gaining border access, their piece of software inside the network will let them expand from the border.
Second - Privilege Escalation, Once the attackers get inside the network, their very first step would be escalating their privileges. The attackers were looking for users like “admin” or “CEO” or “CFO” because they have greater access to system files than an ordinary employees. Since the malware affected the entire network, this phase was not hard for them.
Third - Data theft, After gaining god-like access to the network, attackers began to exfiltrate the data. It is said that it might have taken several months for the attackers to exfiltrate all the data from the Sony network.
Forth - Data Destruction, Came the grand finale and this phase makes the Sony hack a unique one. The malware was very much destructive that it almost destroyed all possible documents and files from the Sony network leaving them bare-handed.
But still, all these conclusions made by the FBI did not prove the origin of the attack. How was the U.S Government so sure it was North Korea? Beyond the FBI, the NSA - National Security Agency one of America’s top-notch spy powers was reported to have evidence that it was North Korea. But the NSA won’t confirm or deny anything. Clever guys right? A few weeks after the hack FBI released vague evidence pointing to North Korea in which security experts and hackers quickly found holes and poked them loud.
All these controversies led hackers and security experts to think if it’s really North Korea that is behind the curtains or any other.
First of all, the agenda changed substantially at several points throughout the hack. That kind of
implies multiple different actors to me.
As Marc Rogers Head of Information Security at CloudFlare said, at first the email demanded money which actually doesn’t point to North Korean hackers because they are not unemployed or wandering for money. These all exactly create doubt if North Korea is part of the party. If yes, who else was at the party?
In 2011 - The Anonymous, A notorious hacker group launched a DDoS [Distributed Denial Of Services] against Sony websites to protect George Hotz also known as Geohot, the first guy to jailbreak an iPhone when he was just 17. A few years later he again jailbroke a Sony Playstation 3 which Sony doesn’t seem to like. So maybe The Anonymous was one among the party.
Another interesting story about Sony being a target for hackers is in 2005, security researchers found a suspicious software on CDs by the Sony BMG - Sony’s music division. The software that was on the CD did two things;
- - First it made the computers incapable of copying music.
- - Second the software hid so you won’t be able to uninstall it.
All these incidents make Sony a favorite and potential target for hackers at every step.
As a quite contradiction with the opinion of Marc Rogers, here came Kurt Baumgartner - Principal Security Researcher, Kaspersky labs who think North Korea really is to be the one to blame. Kurtz is an expert in analyzing malicious code and coming up with defensive solutions. The Sony hack malware resembled the darkseoul attack - 2003 on South Korean Banks. There was also an interesting resemblance in both of the malware in that the word “Security” was misspelled in the exact same way.
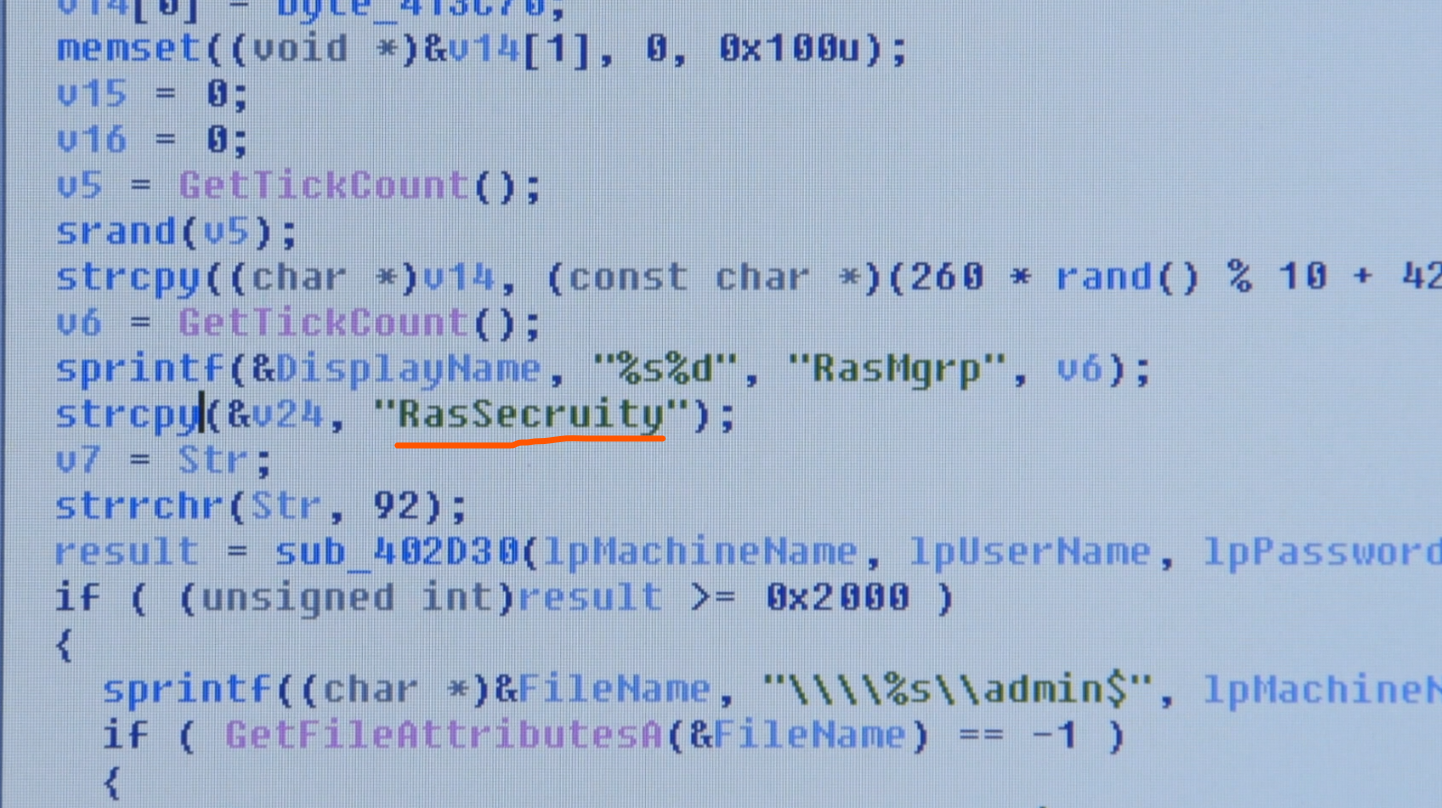
This lead to the conclusion that both the malware shared a common code base. Also, both of the malware were of the “Wiper” category which wipes all the data from the targeted systems. All Though from these understandings it’s still unclear because there is no trace of association between North and South Korean hackers regarding this. Since those code bases are available open to hackers and each will have different versions of them and that is totally a common one. But wait the FBI got another one to put out. The Malware Source code did contain some IP addresses which indicates the computer’s location. FBI said those directly pointed to North Korea but this isn’t conclusive either because IP addresses can be easily faked in milliseconds. Okay for some moment let’s turn our pages to the side of Sony Pictures Entertainment and how they perceived this attack. Maybe the company should have had better security?
It is pretty noticeable from blogs and research papers that the attack was not much sophisticated but still it was successful. That may be because Sony company had less secured networks and followed Security practices inconsistently. Ultimately it all boils down to a fact that really matters is how Sony should have defended this attack rather than a fact showing proofs for the origin of the attack. Whether it’s North Korea or Russia who cares, It’s about people who got affected and held victims in end.
Matthew Preusch is an Attorney who represented Sony employees in the lawsuit against the studio. He said Sony didn’t do what a reasonable company should have done to protect private information on its system. The Poorness was able to be seen clearly starting from poor encryption methods and poor data segregation. But Sony Pictures declined to comment on these allegations and settled the lawsuit out of court. But it’s undeniable that private information that was leaked is going to be alive forever on the internet. so the real victims are the Sony employees.
Whether it is North Koreans or Bored hackers, all competing theories lead to one conclusion that attributing a cyberattack is merely possible.