Dear Ethical Hackers, especially beginners at bug bounty hunting!
It is really hard to fix a vulnerability if the person looking into the submitted bug reports cannot reproduce it.
Understand these before submitting bug information,
- As a beginner, and for your peace of mind,
Always seek permission before testing a website that did not have a Bug Bounty Program or VDP. However, just because a website doesn’t have a responsible disclosure program shouldn’t be a restriction for you to report a CRITICAL vulnerability and it will also not invalidate your valid bug report!
As the Coinme first bounty recipient, when I discovered what I discovered on their website https://coinme.com, I just reported it without even checking if they have a BB program or not.
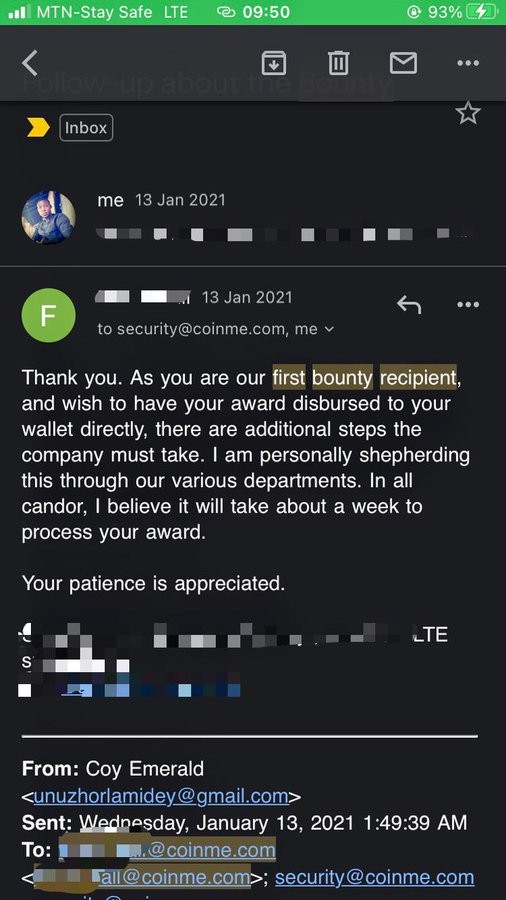
Take Note: Ethical hackers do many things with rules & not against them- but, the fact is , there are many bugs , even critical vulnerabilities that can be accidentally found & without even the run/use of any scanning program.
Try as much as you can to avoid users’ privacy violations i.e do not exploit any findings/discoveries that require accessing user’s account
Keep the information about any vulnerabilities you’ve discovered confidential between yourself, and unless you are working as a team, don’t share your findings with any third party.
Act in good faith, give the company/website the reasonable amount of time to reply to your reports and to resolve the vulnerability before publicly disclosing it. It doesn’t matter how long it takes you to get in touch with the security team.
Remember this, it has taken me several months or even a year to have gotten in touch with some web security team & till the time that I’m making this write-up , Tue, Jan 10 2023, I still have many 2020,2021 reports that I’ve submitted & still 0 responses, yet, they’re not false reports. my point is, Being an Ethical-Hacker also requires patience!
- Make your bug report to be very clear and understandable, so the person receiving the report will be able to reproduce or verify it. Otherwise, you can simply make a video demonstration instead!
Know this very well,
It is hard to fix any issues you might have discovered if you did not report them accurately.
& unlike any other field, complex English is needless, your fluent English is also a joke : if your POC is not reproducible!
- If any organization asks you to stop contacting or reporting bugs to them, I advise you to “STOP” & just do as they have said!
In most cases, you’ll always encounter this if the administrators of the website you are reporting to are ignorant of who the “ethical hacker” is. And sometimes it’s their arrogance and ignorance that will make them respond to you wrongly - dear fellow ethical-hackers, especially beginners, don’t be discouraged over these unpleasant reactions.
I’ve encountered several of these too. The fact is, it’s really hard to get people interested in what has not affected them i.e unexploited bug
I’m encouraging you to look into Hackerone, Bugcrowd and even Intigriti's program
Thousands of domains are out there that will surely appreciate and reward your good work.

Though it takes a crowd and even time to earn a bounty from the above-mentioned platforms, the only unpleasant response you’d get there is “Sorry, it’s Duplicate ”. Or that they need more information- N/A" but not like one of the funniest but dumbest responses that I’ve received from one developer/administrator.
Well, 5 years ago, I was a little hacker! LOL
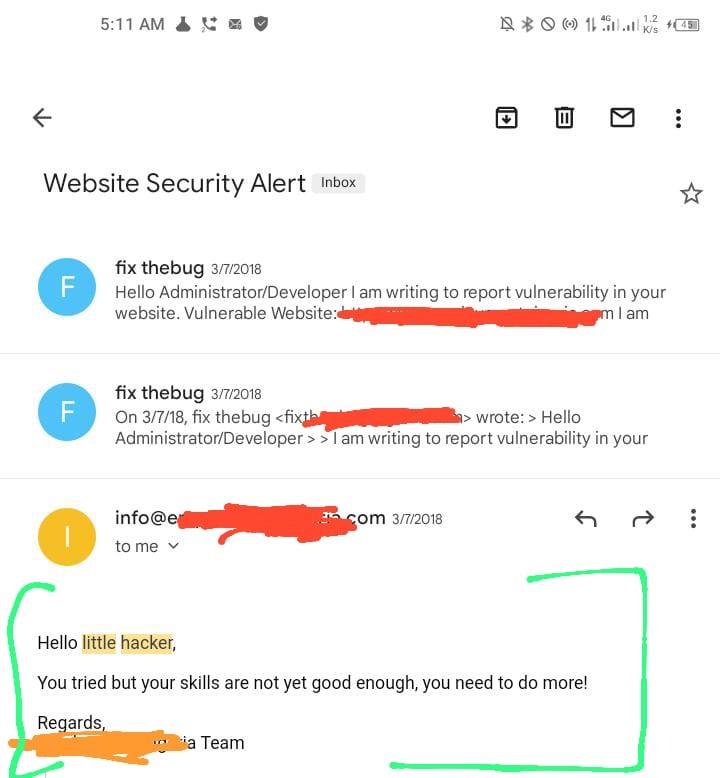
Addition: For those working outside H1,BC, or Intigriti, here are the samples of the brief message that you can also use to submit a “bug report” even through the “contact us” page of the website
Sample I
Hello Administrator/Developer,
Just yesterday ( insert the day) I came across your website and I discovered security bugs on the website. Even though you did a great job with the design and content, you can’t ignore the security part of it so as to avoid website breaking and protecting vital information in the server.
Therefore,
I am writing to report the discovered vulnerability in your domain
Affected Website: Affected Website
Vulnerability Path🙁mention where you’ve found the bug in the website)
I am contacting you about this website vulnerability which allows attackers (intruders) to tamper with site files and modify the website contents. I have more valid proof of what I am saying.
Although this website (affected website) still works correctly, if the problem or the bug is known & revealed to a malicious hacker, the whole website can be compromised. I am happy to explain the bugs to you upon your request and after you reply to this message.
Be assured, I am a Cyber Security Professional –EthicalHacker, so nothing to be afraid of, as I am just contacting you in order to inform you and fix the discovered bugs
Regards
(Your Name)
Cyber Security Expert
Sample II
Technical Analysis & Bug Report
Researcher: (Your name)
Domain: https://coyemerald.com
Bug Type: Developer Mistake
Vulnerable Path: https://coyemerald.com/ignorantarroganttechsupportteam/
POC:
Briefly discuss the reproduction steps.
Alternatively, you can add video instead by making screen recordings.
Regards,
(Your Name)
Note: Always make your report simple, very clear and reproducible and, if you’re contacting any security team through email support, you can make use of one of these unique subjects such as
“I found a bug!”, “Something’s not right”, I think I should let you know” , “Vulnerability Disclosure”
I stated all these to give helpful insights and to also discuss a few of my 10-year experience of being a Bug Bounty Hunter briefly.
And in the next 10 days, I’ll be 27yrs old.
I’m ending this note by wishing myself a very happy birthday in advance !
If you can, please, buy me a coffee.
https://buymeacoffee.com/coyemerald
And you can always visit my website.
https://coyemerald.com to learn more about me