Factory Default Configuration
- All platforms running Junos are shipped with a factory-default config.
- All factory-default configs allow access using root account.
- A root password is absent by default and in order to save any config changes you need to set the root password.
- Includes system logging by default which tracks system events and writes those events to predefined log files.
[edit]
user@router# show system syslog
user * {
any emergency;
}
file messages {
any any;
authorization info;
}
file interactive-commands {
interactive-commands any;
}
- The default hostname of the device is
Amnesiac
- From the config mode you can use
load factory-default to factory reset the device.
Initial Configuration
- Enter
cli and edit for the configuration mode.
set system root-authentication plain-text-passwordto set root password- To setup SSH, port, password, rate limit, etc…
root@SRX# edit system servicesset ssh root-login - permit root login via ssh or not.set ssh protocol-version - new ones have v2 and its recommended.set ssh rate-limit - rate limits no. of connections per minute (1-250)set ssh port x - port number for the incoming ssh.set ssh no-passwords - to disable password based auth.set ssh connection-limit - to limit max allowed connections. (1-250)
- To config hostname, DNS, etc…
root@SRX# edit systemset hostname SRX-Remote - Changes hostname.set domain-name domain.com - give domain name.set name-server 8.8.8.8 set time-zone Europe/London or we can use GMT-x too.- From operational mode
root@SRX> set date YYYYMMDDhhmm.ss or set date ntp to use ntp server.
set system login message "Your actual message goes here"set cli idle-timeout x - (0 to 10000) where 0 means disable
Login Class
- A set of one or more permissions
- All users who can login to a Junos device must have a login class.
- Defines
- access privileges on the device.
- commands that user can or cannot specify.
- session idle time.
- Pre-defined login classes:
super-user - all permissions.operator - clear, network, reset, trace and view permissions.read-only - view permissions.unauthorized - no permissions.- we can also create a custom login class where we can define all the stuffs.
- To set a class to any user, use the command
set system login user user-name class class-name
User Accounts
- Provide a way for users to access the Junos Device
- Each user has a home directory on the device,
/var/home/username
- Users can access the device without accounts too, with RADIUS (Rempote Authentication Dial-in User Service) or TACACS+ (Terminal Access Controller Access Control System Plus) servers.
- for all user accounts following are mandatory:
- username - unique max 64 char string without spaces, colons or commas
- user identifier - numeric (Auto gened)
- full name
- login class
- authentication method
Authentication Methods
- For each login attempt, Junos tries the authentication methods in order, until the password is accepted.
- If the previous authentication method failed to reply, or if the method rejected the login attempt, the next method is tried.
- Eg config:
authentication-order [radius tacplus];- where it tried with radius first, if rejeted goes to tacplus. Since query to local DB is not configed, the login will fail if the tacplus also fails.
- If the both radius and tacplus servers are down, even though it’s not configed, authentication will happen with the local auth DB.
- Make note that in hte above example, the servers just didn’t respond, so query to local DB will be made irrespective of the config.
Interfaces
Primarily used to connect a device to a network.
Some interfaces are also used to provice a service or a specific function for the system.
Interfaces may be physical or logical.
Every physical interface will have a logical interface associated with it.
Types
Management Interfaces - Used for management purposes, common designations include fxp0 and me0
Internal Interfaces - Communication between Routing Engine and the Packet Forwarding Engine, automatically configed on bootup. Common designation include fxp1 and em0
Network Interfaces - Gives physical connections to other devices, like SONET, Async Transfer Mode, T1 and DS3
Service Interfaces - Provides traffic manuplation services like encryption, encapsulation, tunneling, etc… Either via card (physical) or software.
- Encryption interface -
es
- Generic Routing Encapsulation (GRE) interface -
gr
- IP-over-IP encapsulation (IP-IP tunnel -
ip
- Link services queuing interface -
lsq
- Secure Tunnel Interface -
st
- Internally generated interface to monitor and record traffic during passive monitoring -
tap
Loopback Interfaces - Addressed to same device. Common designation is lo0. Checks device status.
Interface Naming Convention
- Names as type - fpc / pic / port
- fpc - Flexible PIC concentrator - line card slot number
- pic - Physical interface card - interface card slot number
- port - port number
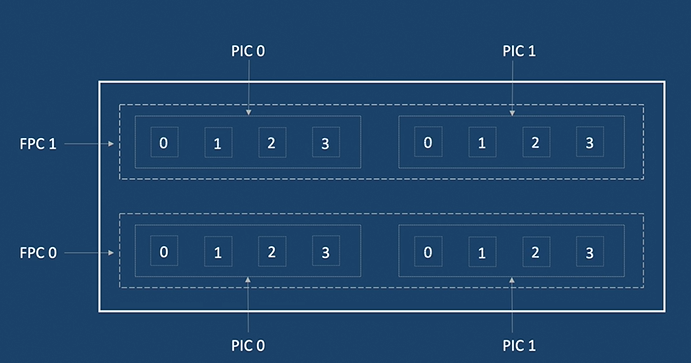
- Eg:
ge-1/0/1
- gigabit Ethernet, fpc - 1, pic - 0 and port - 1
Interface Properties
Physical Properties (common ones)
- Mode - half-duplex or full deplex.
- Speed - link speed.
- MTU - max transmission unit (256-9192 bytes).
- Clock - Internal/External clocking.
- Frame Check Sequence (FCS) - Error detection.
- Encapsulation - PPP, frame Relay, PPPoE
Logical Properties (common ones)
- Protocol Family - inet, inet6, iso, mpls, ethernet-switching
- Address - IP for the inet family
- VLAN tagging
- Firewall filters and routing policies
Address configuration
- We can assign multiple IPs to the same interface and numerically lower one will be taken as preferred address.
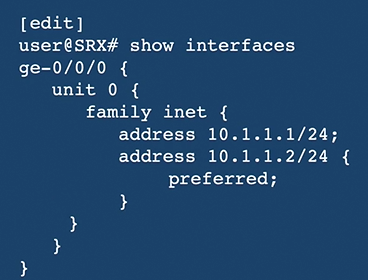
- We can still influence this by setting “primary” keyword in the unit.
Configuration Groups
- Common configuration snippets that can be applied to other parts of the configuration.
- Create a group with config statements and apply that to the rest of the configs.
set interface ge-0/0/1 apply-groups band-config
- here band-config is our group.
- But by default the inherited configs like this won’t be displayed. so we need to use `show interface ge-0/0/1 | display inheritance
Syslog
- Records system-wide, high-level operations, such as interfaces going up ordown, or users logging in to or out of the device
- Logs are placed in files in
/var/log directory. The primary syslog file, which is included in all factory default configs is the /var/log/messages
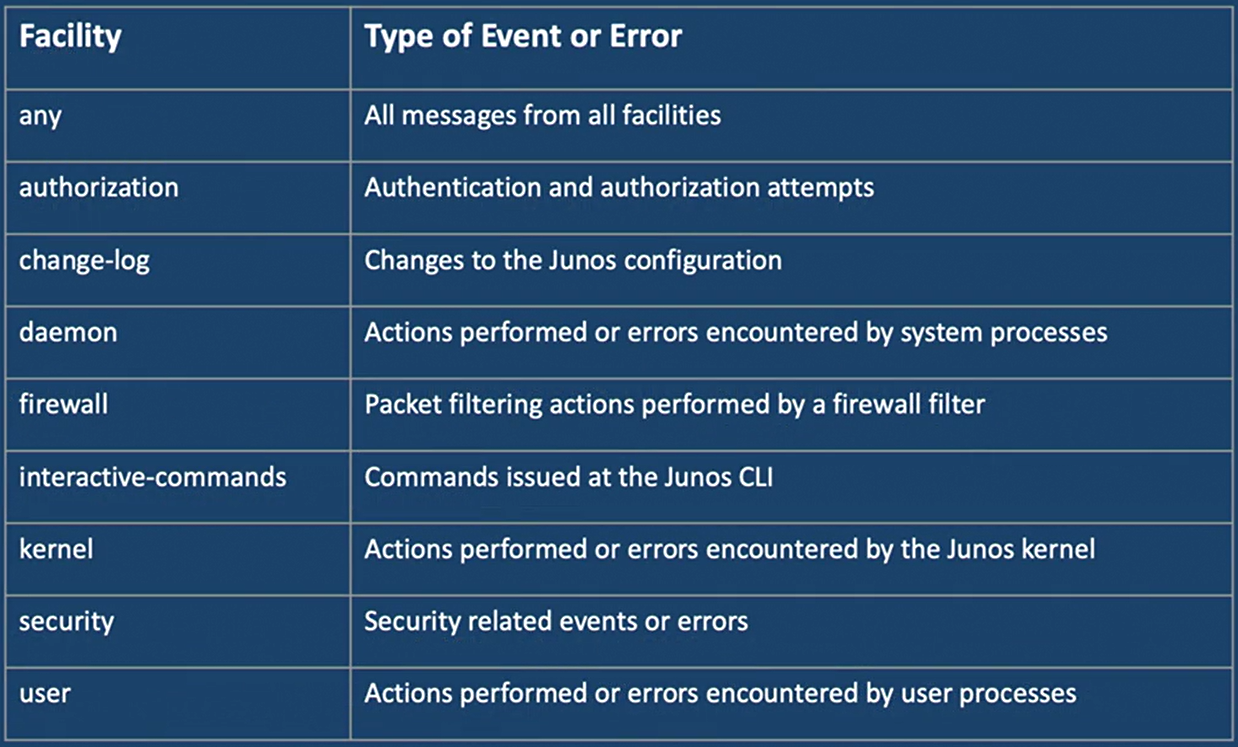
- Each system log messages belongs to a facility - what is a group of messages that are either generated by the same software process or concern a similar activity (Such as authentication attempts)
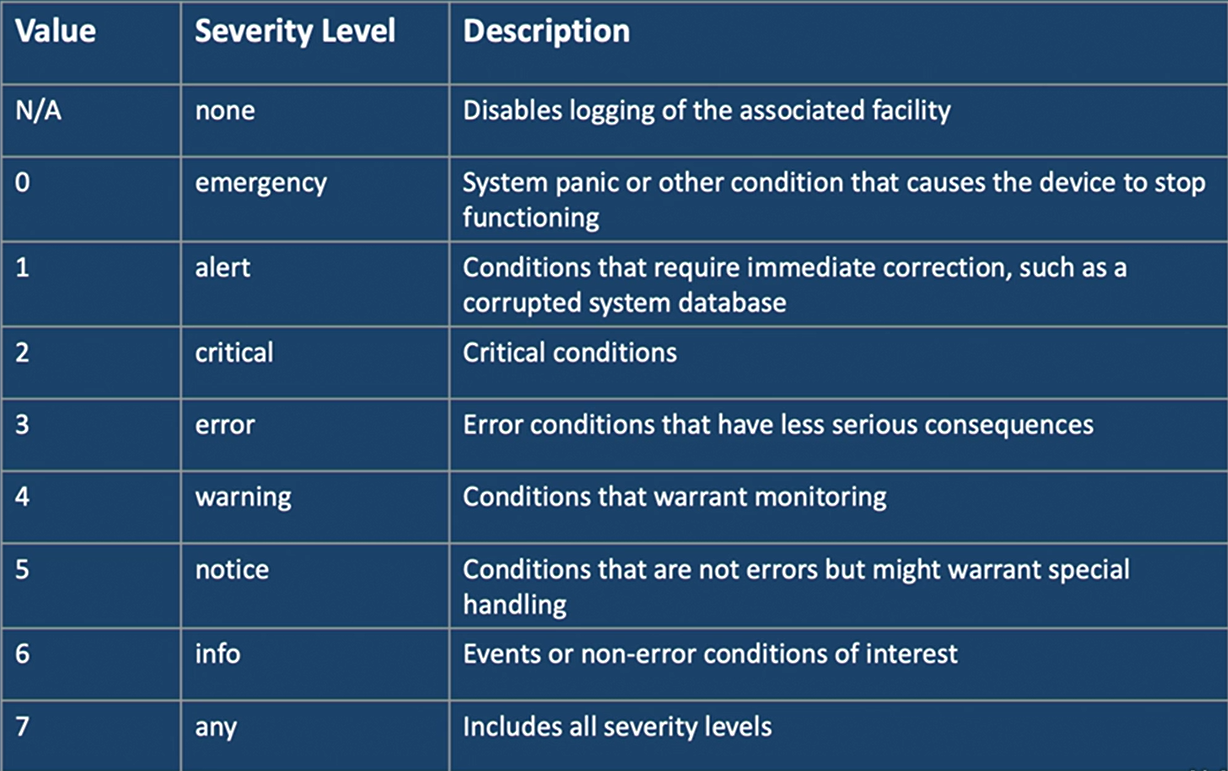
- Each message is assigned a severity level that indicates how seriously the triggering event affects the device functionalities.
- You can run operational mode commands from configuration mode by prefixing with
run command like run show log
set file cli-commands structured-data formats according to the internet draft syslog protocol.- Log files can be archived, the file is closed and compressed and its name is changed to
logfile.0.gz
- Logs are then written to a new file called logfile and its goes into archive with the name
logfile.1.gz until max number of log files are generated.
Tracing
- Tracing allows you to track events that occur in the device: both normal operations and error conditions.
- Tracing in Junos means debugging in other usual vendors.
- When enabled, a trace file is created that is used to store decoded protocol information recieved or sent by the routing engine.
- Stored in
/var/log/ directory or to a remote syslog server.
- It’s better to avoid enabling tracing at unnecessary times to avoid resource consumption.
- To view files updating in real time, we can use
monitor start log-file-name command. monitor stop to end the live mode.
- You can send syslog to rmeote location too,
set system tracing destination-override syslog host 192.168.1.1
SNMP
Simple Network Management Protocol that enables the monitoring of network devices from a central location.
SNMPv1 - initial implementation of SNMP that defines the architecture and framework for SNMP
SNMPv2c - Added support for community strings, which act as passwords to determine who, what and how the SNMP clients can access data in the SNMP agent.
SNMPv3 - provides data integrity, data origin authentication, message replay protection and protection against disclosure of message payload.
This is done usiing 2 entities:
SNMP data is stored in Management Information Base (MIB) in a highly structured, hierarchial format (Tree).
Each object in the MIB have Object Identifier (OID) which names the object.
The “leaf” in the tree structure is the actual managed object instance, which represents a resource, event or activity that occurs on the device.
Get, GetBulk and GetNext requests - manager requests information from the agent, the agent returns information in a Get response message.Set requests - manager changes the value of an MIB object controlled by the agent; the agent indicates status in a Set response message.Trap notification - agent sends traps to notify significant events that occur on the device. These are unconfirmed notifications, whereas SNMP informs are confirmed ones.show snmp mib walk jnxMibs returns the root node and its tree. show snmp mib walk 1 returns all object names.
Rescue Configuration
- User-defined, known-good config that is designed to restore connectivity in the event of configuration problems.
rollback rescue
- If the active config is corrupted, the device automatically loads the rescue config file as the active config.
request system configuration rescue save to save a rescue config file to roll back in future.test configuration /config/rescue.conf.gz can be used to check the config.show system alarms gives possible precations that are not satified, like warnings.
Backups