Routing Policy
- Allows to control the flow of routing information to and from the routing table.
- Allows to control which routes the routing protocols store into and retrieve from the routing table.
- Can be applied as informatio enters the routing table and as information leaves the routing table.
- A routing policy allows you to choose which routes you accept or reject from neighbors running dynamic routing protocols and also to choose which routes you send to neighbors running dynamic routing protocols.
- Allows to modify attributes on routes as they enter or leave the routing table. Eg: You can change the preference value.
- By modifying attributes, we can control which route is selected as the active route and placed into the forwarding table.
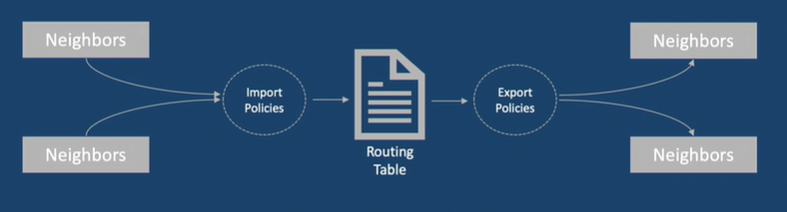
- Import Policies:
- Applied when the routing protocol places routes into the routing table.
- So it can change routes in the routing table and can affect the local route selection process.
- Export Policies:
- Applied when the routing protocol is advertising routes that are in the routing table to either other dynamic protocols or forwarding table.
- So change in attribute do not affect the local routing table; rather, the software applies them to the route while exporting it.
- Only active routes are available for export from the routing table.
Default Routing Policies
Applied on incoming or outgoing routes or packets if there is no explicitly configured policy related to the route or the interface upon which the packet arrives.
Knowing these is essential as we may need to reconfig them to suit our specific needs at different scenarios.
Default Policy of RIP:
- Import: Accept all RIP routes learned from configured neighbors and import into the
inet.0 routing table.
- Export: Reject everything, to export RIP routes an export policy must be configured.
Default Policy of OSPF:
- Import: Accept all OSPF routes and import into the
inet.0 routing table. Applies to only external routes.
- Export: Reject everything, OSPF does not export internally learned routes (directly connected routes on interface running OSPF)
Default Policy of IS-IS:
- Import: Accept all RIP routes and import into the
inet.0 and inet6.0 routing table.
- Export: Reject everything.
Default Policy of BGP:
- Import: Accept all BGP IPv4 and IPv6 routes and import into the
inet.0 and inet6.0 routing table.
- Export: readvertise all active BGP routes.
Components of policy
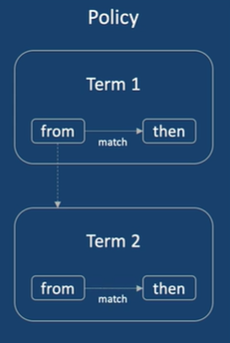
Terms:
- A
if...then statement
- names structures in which match conditions and actions are defined.
- one or more terms can be defined.
Match Conditions:
- criteria against which a route or packet is compared.
- one or more criteria can be configured.
- if all criteria match, one or more actions are applied.
Actions:
- What happens when criteria matches.
- one or more actions can be configured.
from indicates incoming routes and the statement is optional, if left omitted - all routes are considered to be a match.to indicates outgoing routes and is also optional.then statement is also optional and it defines the action(s). Three types of actions
- flow control - decide whether to accept or reject the route and whether to evaluate the next term or routing policy.
- actions that manipulates route characteristics.
- trace action - this logs route matches
- If omitted, next term is evaluated and if not goes to next policy if exists.
The Policy Evaluation Flow:
- Against 1st term. if matches then actions are taken.
- If the action is to accept or reject the route, that action is taken and evaluation of the route ends.
- However, evaluation continues to next term if the route does not match, or if no action is specified, or if the
next term action is specified.
- If the route matches no terms, the
accept or reject action specified by the default policy is taken.
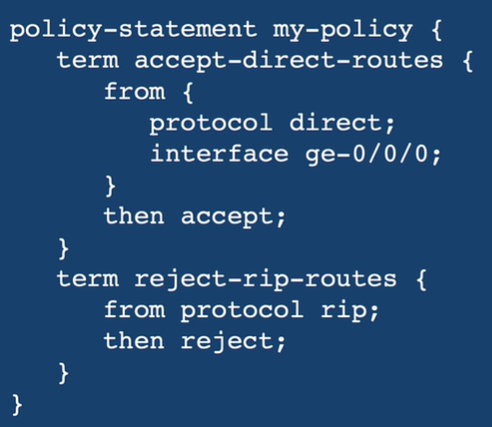
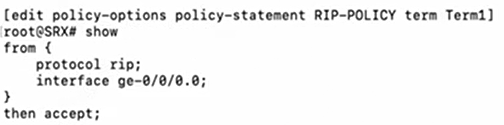
[edit policy-options]
# edit policy-statement RIP-POLICY
[edit policy-options policy-statement RIP-POLICY]
# edit term Term1
[edit policy-options policy-statement RIP-POLICY term Term1]
# set from protocol rip
# set from interface ge-0/0/0
# set then accept
Prefix List
- Named list of IP addresses used to match routes.
- Configured under the
[edit policy-options] hierarchy.
- Can be referenced in multiple terms within a single policy or in different policy.
- Can be used with routing policies and firewall filters.
[edit policy-options prefix-list rfc1918]
# set 10.0.0.0/8
# 172.16.0.0/12;
# 192.168.0.0/16;
# up
# show
prefix-list rfc1918 {
10.0.0.0/8;
172.16.0.0/12;
192.168.0.0/16;
}
- It’s a list of Non Routable Address spaces, all private IPs
[edit policy-option]
# set policy-statement my-policy from prefix-list rfc1918
policy-statement my-policy {
term reject-rfc1918 {
from {
prefix-list rfc1918;
}
then reject;
}
}
- with
prefix-list-filter we can perform not only exact matches, but also - longer, orlonger matches.
- you can specify an action that executes immediately after the match occurs. The
then block is not executed.
policy-statement my-policy {
term reject-rfc1918 {
from {
prefix-list-filter rfc1918 orlonger reject;
// this will reject subnets like >= relation
}
}
}
Routing Filters
- List of prefixes configured within a single routing policy or policy term.
- Not reusable but rather are specific to the policy or term in which they are configured.
- An optional action can be specified to be taken if the
route-filter statement matches.
exact =orlonger >=longer >upto - from route-filter 10.1.1.1/16 upto /24 Relation like this: >=prefix-length-range - from route-filter 10.1.1.1/16 prefix-length-range /20-/24. lower limit >= x <= upper limit.
policy-statement my-policy {
term reject-rfc1918 {
from {
route-filter 172.16.0.0/16 match-type accept;
}
}
}
Applying Routing Policies
- Depending on the routing protocol, you can apply import and export policies at multiple level of the hierarchy
- RIP import policies can be applied at either global, group or neighbor level - this will affect routes from either all peers or a specific neighbor.
- RIP export policies may only be applied at the group level, allowing you to alter routing knowledge for a specific set of peers only.
- BGP - Allows import and export for global, group and neighbors.
- OSPF - allows only protocol-level
[edit protocols rip]
# set import RIP-IMPORT-POLICY-NAME
Firewall Filters
- Rules that define whether to accept or discard packets that are transiting an interface before it enters or exits a port or interface.
- If a packet is accepted, actions such as
- class-of-service - groups similar traffic together and treat each type of class with its own service priority.
- traffic policing - control max rate of traffic sent or recieved.
- Late limit to mitigate DoS.
- Stateless in nature, so each packet is examined individually.
- The structure of firewall filter is similar to that of routing policies.
- Firewall Filters require at least one term.
- Types of actions:
- Terminating - Specified action is performed, no additional terms are examined. Eg:
accept, discard, reject
- Non Terminating - actions like incrementing counter, logging, sampling data or sending info to host. Eg:
count, log, policer to rate limit, syslog.
- Flow Control - perfomrs configure actions on the packet and then evaluate the next term in the filter, rather than terminating the filter.
next term action.
Configuring Firewall Filters
- Firewall can be applied to
lo0 too the loopback interface.
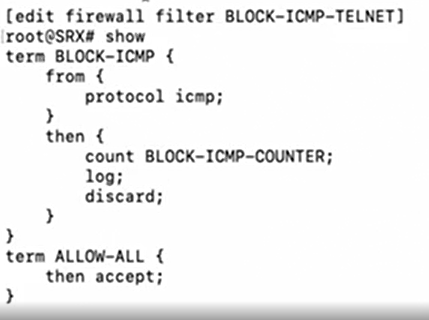
// to block ICMP and TELNET
[edit firewall filter BLOCK-ICMP-TELNET term BLOCK-ICMP]
# set from protocol icmp
# set then discard
# set then log
# set then count COUNTER-NAME
# edit term ALLOW-ALL
[edit firewall filter BLOCK-ICMP-TELNET term ALLOW-ALL]
# set then accept
# commit
[edit interface lo0 unit 0 family inet]
# set filter input BLOCK-ICMP-TELNET
# commit
Traffic Policing
- Rate limiting for both inbound and outbound traffic.
- bandwidth - no. of bits per second permitted on average.
- burst size - no. of bytes the system allows during a burst. (Above bandwidth)
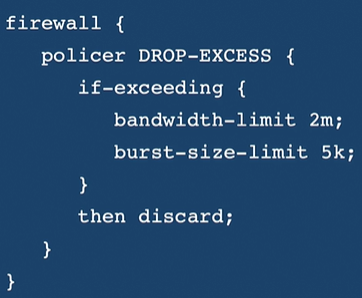
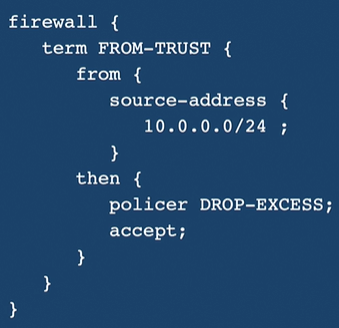
- define the policer and reference it inside the firewall.
- token-bucket algorithm is uesd.