Microsoft 365 Defender is an integrated threat protection suite with solutions that detect malicious activity across email, endpoints, applications, and identity.
These solutions provide a complete attack chain compromise story that enables a complete understanding of the threat. And, enables you to remediate and protect your organization from future attacks.
In the sample attack chain graphic below, see the attacker activity visible to each Microsoft 365 Defender product.
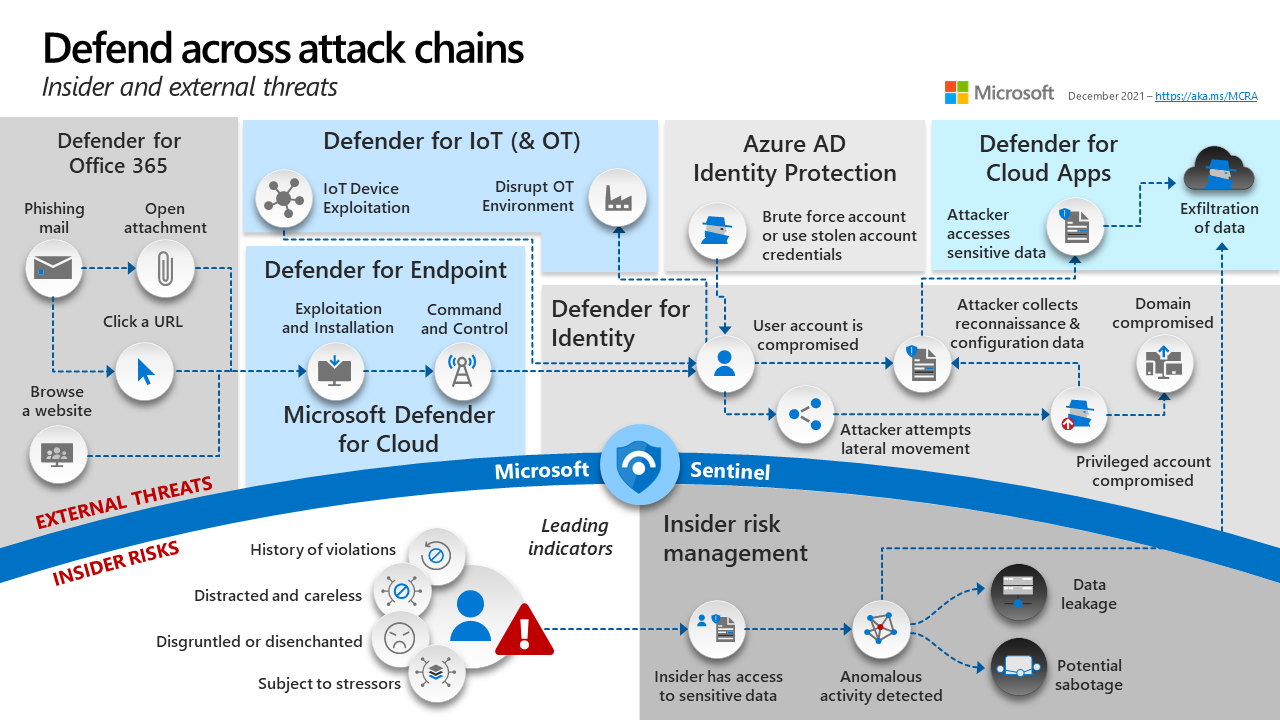
You’re a Security Operations Analyst working at a company that is implementing Microsoft 365 Defender solutions. You need to understand how Extended Detection and Response (XDR) combines signals from:
- endpoints
- identity
- email
- applications to detect and mitigate threats.
Explore Extended Detection & Response (XDR) response use cases
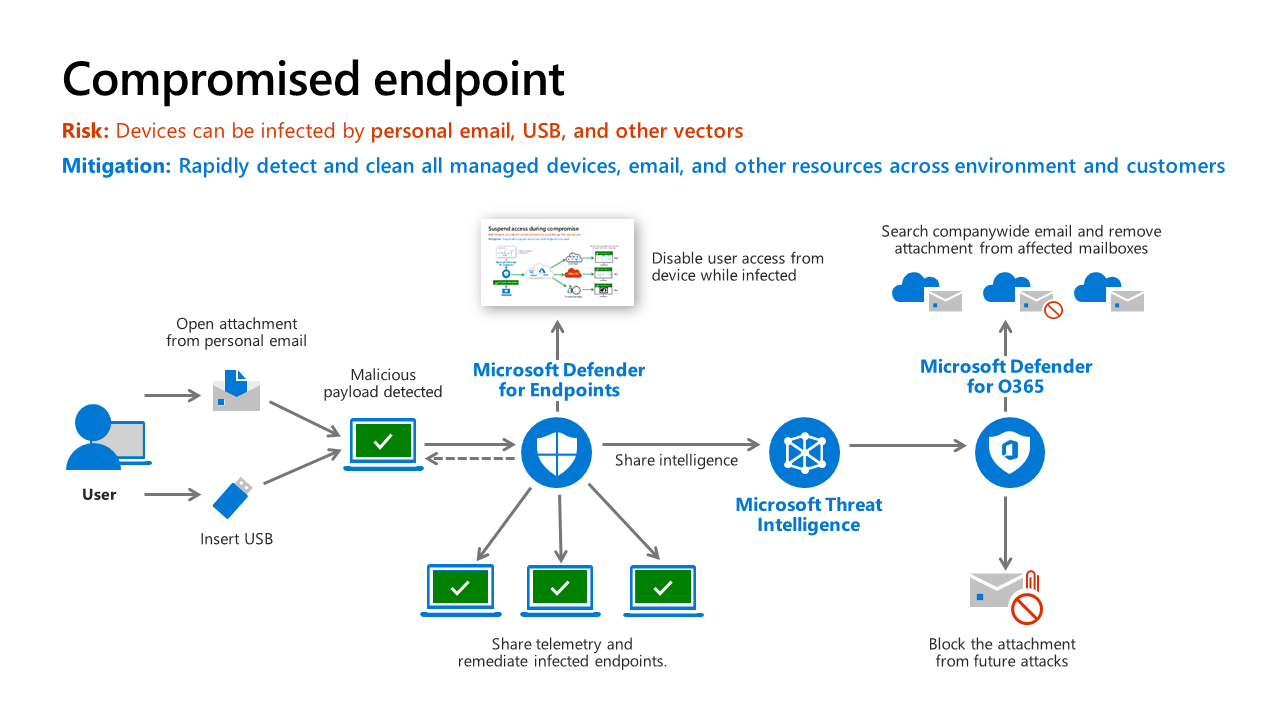
Detection of Threat - This scenario depicts a case where Microsoft Defender for Endpoint detects a malicious payload (which could come from any source, including personal email or a USB drive).
- The victim receives a malicious email on personal email account (not protected by Microsoft Defender for Office 365 (MDO) or a USB drive and opens the attachment.
- Once the attachment opens, the malware infects the computer.
- The user is unaware that an attack has taken place. But Microsoft Defender for Endpoints (MDE) detects this attack, raises an alert to security operations, and provides details about the threat to the Security team.
- Disable user access from device while infected - MDE communicates to Intune that risk level on this endpoint has changed.
- Intune marks the account in Azure Active Directory as noncompliant with organizations policy, and Conditional Access blocks user access based on that.
Remediation
- MDE remediates threat – either via automated remediation, security analyst approval of automated remediation, or analyst manual investigation of threat.
- MDE also remediates this threat across your enterprise and across our Microsoft MDE customers by adding information on this attack to Microsoft Threat Intelligence system
Share Intelligence and Restore Access
- Restore Access – Once the infected devices have been remediated, MDE signals Intune to change the device risk status and Azure AD Conditional Access then allows access to enterprise resources.
- Remediate Threat Variants in MDO and others – The threat signals in Microsoft Threat intelligence are used by Microsoft tools securing other parts of your organization’s attack surface.
- MDO and Microsoft Defender for Cloud use the signals to detect and remediate threats in email, office collaboration, Azure, and more.
Security Operations Model - Functions and Tools.
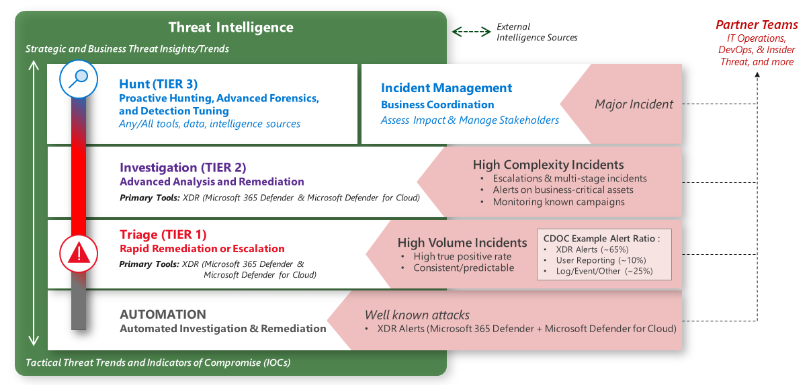
Triage and Automation
- Automation
- Near real-time resolution of known incidents.
- These are well-defined attacks that the organization would have seen several times.
- Triage (Tier 1)
- Focus on rapid remediation of a high volume of well-known incident types that still require quick human judgment.
- These are often tasked with approving automated remediation workflows
- Also involves identifying anything anomalous or interesting that warrant escalation or consultation with investigation (Tier 2) teams.
- Key Learnings for Triage & Automation:
- 90% True Positive - It’s recommended to set standard of 90% true positive for any alert feeds that will require an analyst to respond. This also ensures the analyst won’t be overwhelmed with lotta false alarms.
- Alert Ratio - Cyber Defense Operation Center, XDR alerts produce most of the high-quality alerts and remaining comes from the user reported issues, classic log query based alerts and other sources.
- Automation - Empowers these analysts and reduce the burden of manual effort by automating remediation sequences.
- Tool Integration - Powerful time saving tech that improved time to remediation in Microsoft’s Cyber Defense Operations Center (CDOC) is the integration of XDR tools together into 365 Defender so analysts have a single console for endpoint, email, identity and more. This enables analysts to rapidly discover and clean up attacker phishing emails, malware, compromised accounts before they can do a significant damage.
- Focus - These teams can’t maintain their high speed of resolution for all types of tech and scenarios, so they keep their focus narrow on a few tech areas. Most often this is on user productivity like emails, endpoints AV alerts (versus EDR that goes into investigations), and first response for user reports.
Investigation and Incident Management
- This team serves as escalation point for issues from Triage and directly monitors alerts that indicate a more sophisticated attacker that trigger behavioral alerts, special case alerts related to business-critical assets and monitoring for ongoing attack campaigns.
- Proactively, this team also periodically reviews the Triage team alert queue and may proactively hunt using CDR tools in their spare time.
- This team provides deeper investigations into a lower volume of more complex attacks, often multi-stage attacks conducted by human attack operators.
- This team pilots new/unfamiliar alert types to document processes for Triage team and automation, often including alerts generated by Defender for Cloud on cloud hosted apps, VMs, containers and Kubernetes, SQL DBs ,etc…
- Incident Management - This team takes on the non-technical aspects of managing incidents too including coordination with other teams like communications, legal, leadership, and other business stakeholders.
Hunt and Incident Management
- This is multi-disciplinary team focused on identifying attackers that may have slipped through the reactive detections and handling major business-impacting events.
- Hunt - This team proactively hunts for undetected threats, assist with escalations and advanced forensics for reactive investigations, and refines alerts/automation.
- These teams operate in more of a hypothesis-driven model than a reactive alert model and are also where red/purple teams connect with security operations.
How it comes together
For an idea of how this works, let’s follow a common incident lifecycle, kinda a use case.
- Triage - analyst claims a malware alert from the queue and investigates say from the 365 Defender Console.
- While most triage cases are rapidly remediated and closed, this time it is observed that malware may require more involved/advanced remediation like Device Isolation and Cleanup. So the Triage team escalates the case. Triage team has option to stay involved and learn more.
- Investigation - Takes up the case from Triage team and verifies the conclusions or digs further into it and proceeds with remediation, closes case.
- Later, Hunt may notice this case while reviewing closed incidents to scan for commonalities or anomalies worth digging into:
- Detections that may be eligible for auto-remediations.
- Multiple similar incidents that may have a common root cause.
- Other potential process/tool/alert improvements.