Hello Guys..!!
Hope you are doing well
Today we are going to see about how I found multiple Internal Origin IP Addresses of Indian Govt websites which lead me to the Admin Login Panels.

Let’s Start without wasting any more time.
I have used one of the shodan dork methods which @Aditya_Shende has shared on his Linkedin.
I have provided the Link to the Post in the below section.
LinkedIn
The Shodan dork I used to get the various Origin IPs of the Admin Panels of Indian Govt Websites is listed in the last row of the below code block.
Shodan Dork:
ssl.cert.subject.CN:"*.target. com" http.title:"index of/"
ssl.cert.subject.CN:"*.target. com" http.title:"gitlab"
ssl.cert.subject.CN:"*.wur.nl" http.title:"gitlab"
ssl.cert.subject.CN:"*.target. com" "230 login successful" port:"21"
ssl.cert.subject.CN:"*.gov.in"+200 http.title:"Admin"
After Searching with the above 5th dork on Shodan, I got various Admin Login panels hosted on Internal Origin IP addresses which resemble the same content present on the Original website.
For Example:
Origin IP: 27.0.180.151
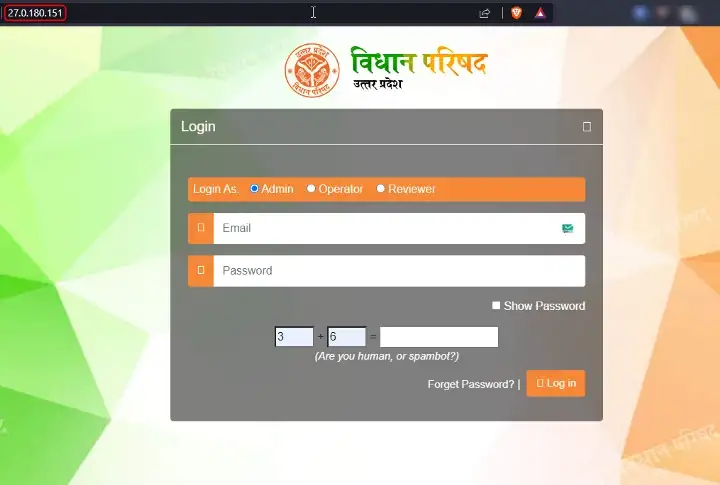
Actual Website: https://vidhanparishad-admin.up.gov.in
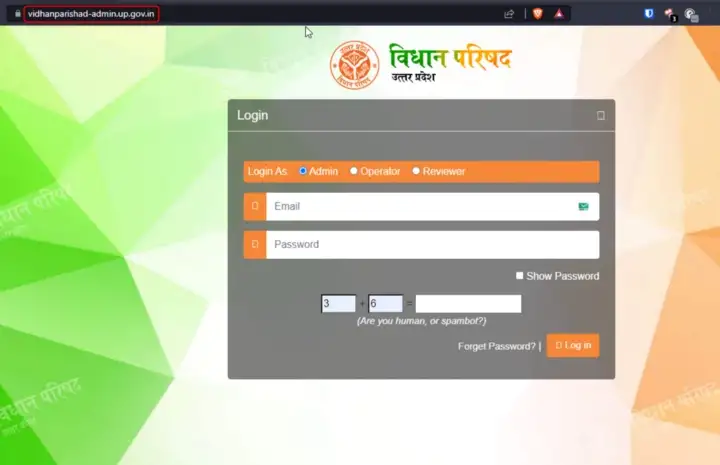
Similarly, I found a total of Six Origin IPs which resemble their respective Original Websites.
The Content and functionality are the same on both the IP and its website.
I have reported regarding the same with CERT-In (Computer Emergency Response Team — India) is the national nodal agency for responding to computer security incidents as and when they occur.
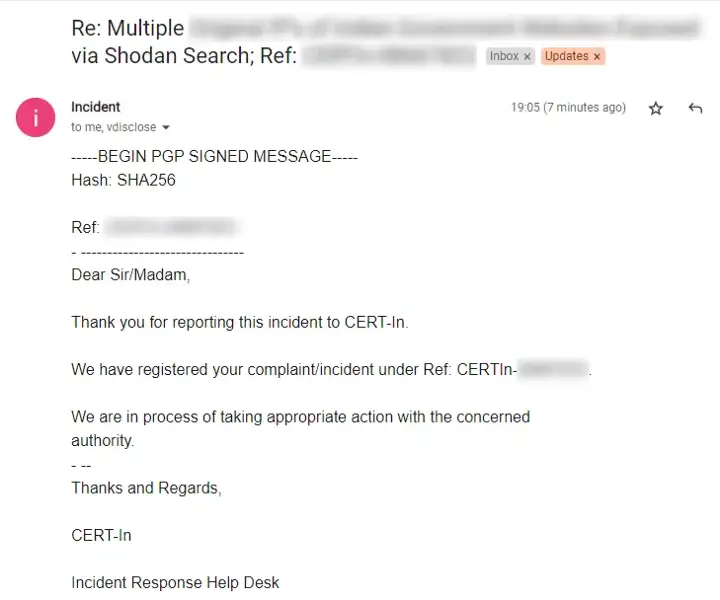
I have received Acknowledgement from the CERT-In regarding my report as Shown above.
So, That’s it for today.
Note: I only revealed the IP and its website for Educational purposes and to make people understand clearly about this scenario. Please don’t judge me.
If you like this post, don’t forget to give me 🤍
Credits: @Aditya_Shende
Support me: If you like to support me, buy me a cup of coffee ☕
Follow me: @0xKayala | Satya Prakash