In the world of cybersecurity, it’s pretty common when companies or individuals get affected because of cyber attacks or Data Breaches.
A total of 108.9 million accounts were breached in the third quarter of 2022, a 70% increase compared to the previous quarter
“Global user breaches are 70% higher this quarter than the last. Every second in the past three months, 14 accounts were leaked - all of them coming from different countries.”
But this is not even the worst part. Surprise right?

The Worst Part is knowing that you’re breached or a hacker/APT Group is living inside your network after months or even years.
According to the IBM report, the average cost of a data breach in 2022 is $4.35 million, with an average of 277 days to identify and contain the breach.
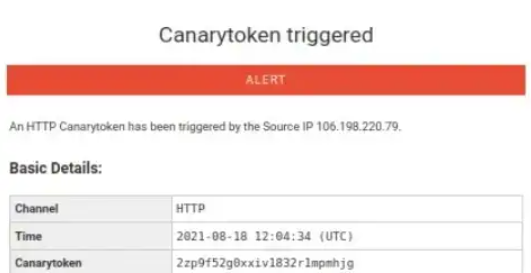
So it’s quite a big challenge to identify the Data Breach, Hacker’s presence in your network, or tried to take access to any of our assets immediately so we can trigger the response plan to minimize risk & strength our Security.
To do this we’ve one of the Fast, Quick & Free Technology known as Canary Token.
Canary tokens are a free, quick, painless way to help defenders discover they’ve been breached (by having attackers announce themselves.)
### What are Canary Tokens?
You must be familiar with web bugs, the transparent images which track when someone opens an email. They work by embedding a unique URL in a page’s image tag and monitoring incoming GET requests.
Imagine doing that, but for file reads, database queries, process executions, or patterns in log files. Canary tokens do all this and more, letting you implant traps in your production systems rather than setting up separate honeypots.
Put the canary token on all your network & when the Attacker interacts with any of it it’ll trigger the company that someone accessed X".
### How to use it?
- Goto this website
- Select the Type of Canary token such as HTTP, DNS, Email, Word, PDF, MYSQL, ZIP file, Folder & 20 + other types.
- Enter your Email or webhook URL to get a trigger Alert. (if don’t want to use a personal email then check this link to generate a fake one).
- Enter a description of that token (helps when you have many tokens in a network so a unique description will identify which asset is exploited).
- Generate a token & Now the canary token is active on a particular asset.
- You can look at manage -> history to check all active token’s status & will get a message in the future if the token is triggered.
### Real-life Use Cases of Cananry token
Word Documents
A malicious Hacker gains access to one of our company intern computer & see a document that can be useful for other lateral movement phases.

When the hacker opens the file the token will trigger & all his info will be sent to us.

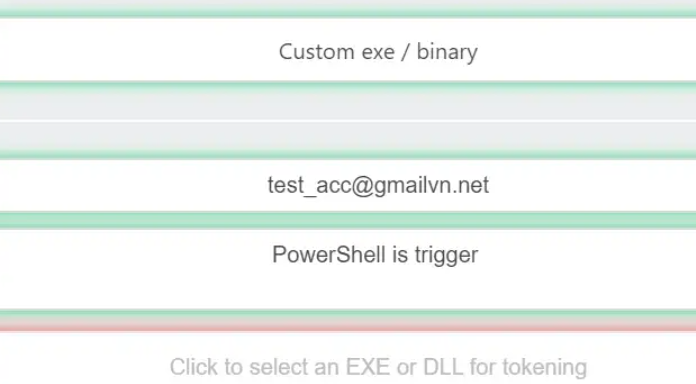
Custom program/binary executed
This is also useful if want to get to know when a hacker executes some binary in your system such as mimikatz, Metasploit post-exploitation scripts, nmap scans, or any other enumeration tools.
AWS Keys
This token provides you with a set of AWS API keys. Leave them in private code repositories, and leave them on a developer’s machine. An attacker who stumbles on them will believe they are the keys to your cloud infrastructure. If they are used via the AWS API at any point, you will be alerted.
That’s it there are more than 30+ token types so not going to cover all here but hope you get the idea of using these to track the hackers.
Check this link to learn about all token types & their use.