
Collecting The Volatile Data
As in the last blog i had mentioned about different types of data classification and the Methodology of windows forensics now we will touch each part of the methodology mentioned earlier.
link to Part 1 - https://hacklido.com/blog/271-windows-forensics-the-art-of-investigating-part-1
So let’s start
- Volatile data includes:-
- System time
- Logged on users
- Network Information
- Open files
- Network Connections
- Network Status
- Process Information
- Process-To-Port Mapping
- Process Memory
- Mapped Drivers
- Shares
- Clipboard Contents
- Service/Driver Information
- Command History
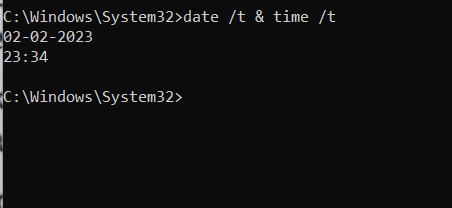
Collecting System Time
date /t & time /t
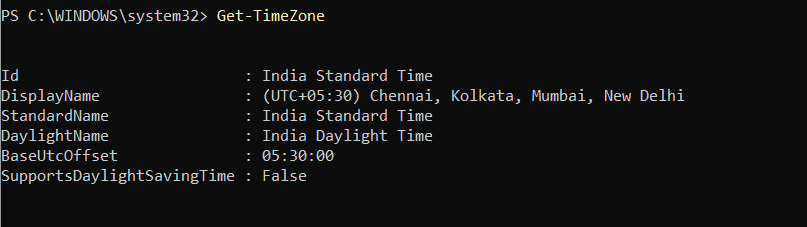
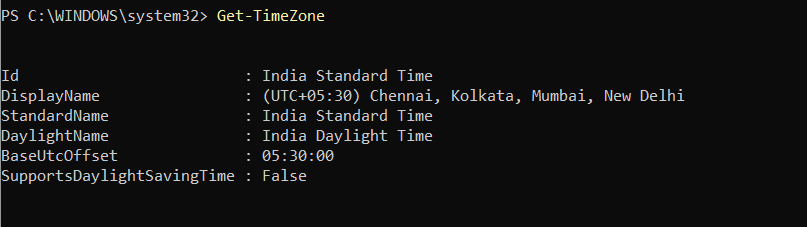
Get-TimeZone
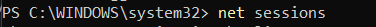
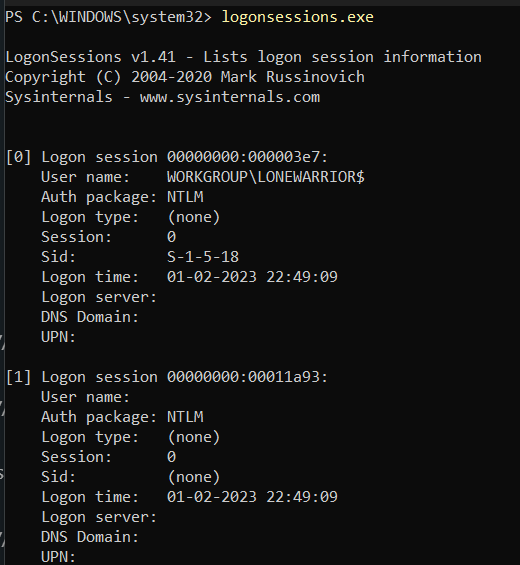
Collecting Logged-on Users
PsLoggedOn
net sessions
LogonSessions.exe
Collecting Open/Shared Files
net file
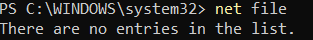
There are no files because i have not shared any files in the network
Network Opened Files by nirsoft
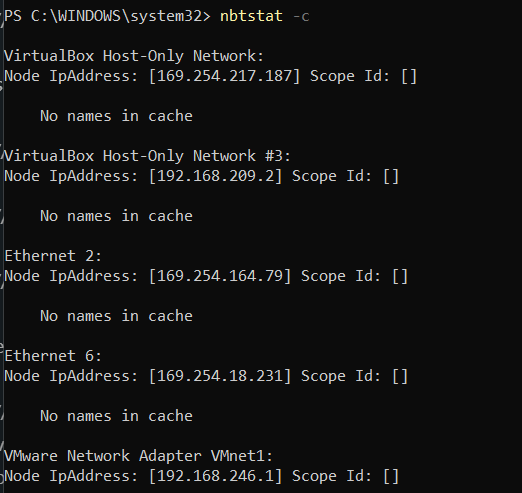
Collecting Network Information
nbtstat -c (Netbios name table cache)
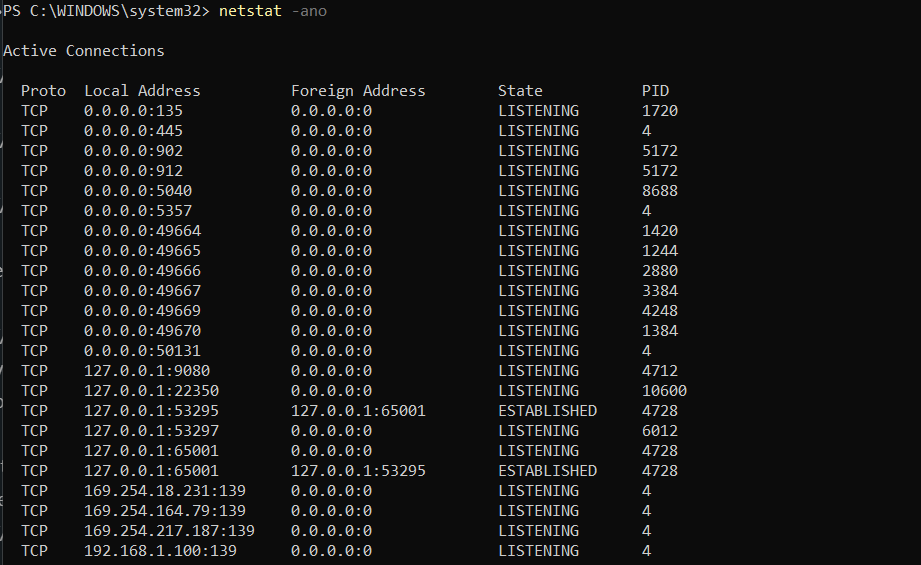
Collecting information about Network Connections
netstat -ano (TCP and UDP Network Connections)
netstat -r (Routing Table)
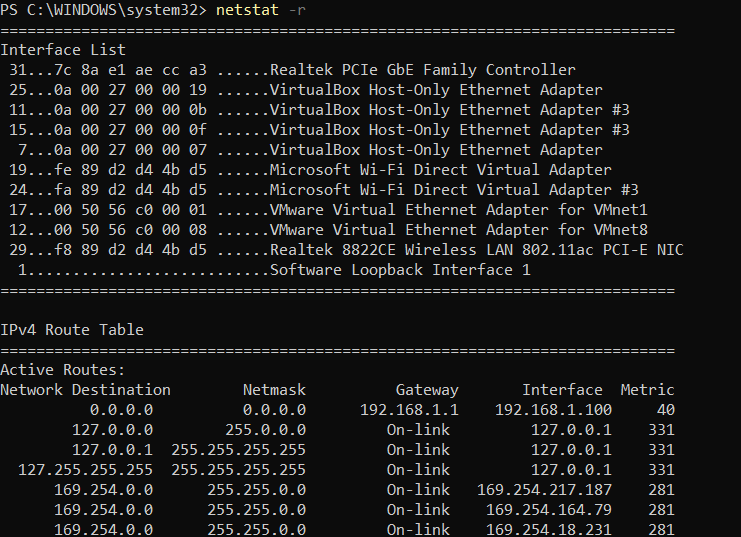
Process Information
Investigate the process running on a potentially compromised system and collect the information.
- Task Manager
tasklistpslistlistdlls
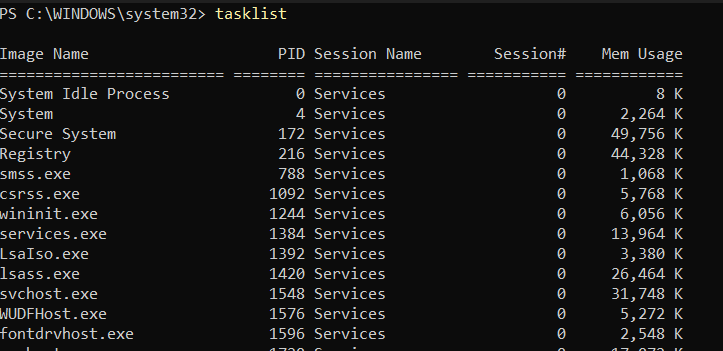
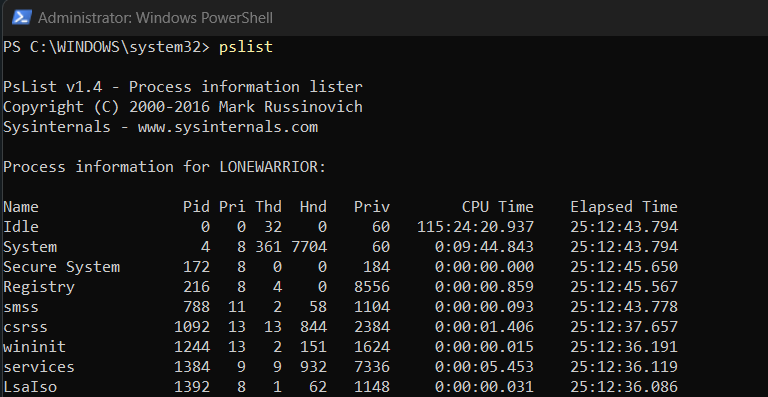
Collecting Network Status
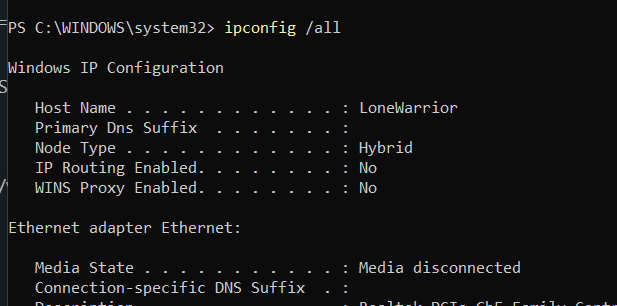
Clipboard Contents
FreeClipboardViewer
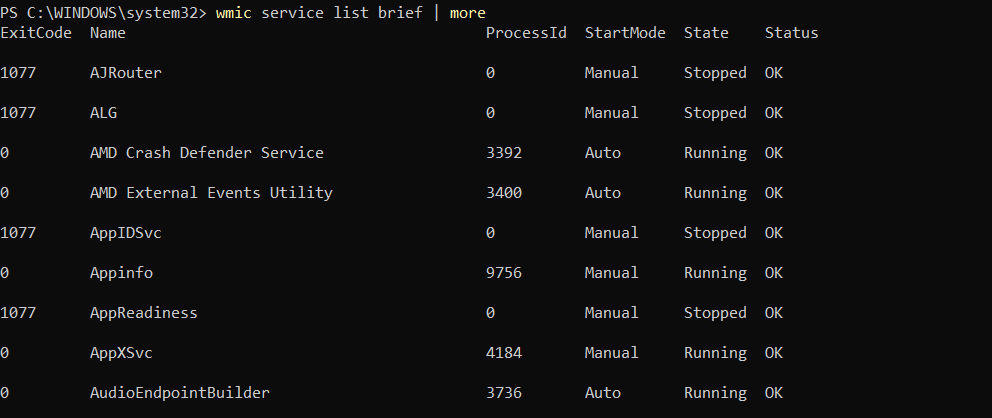
Service and Driver Information
wmic service list brief | more
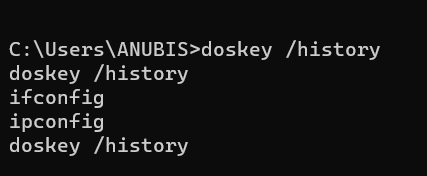
Command History
doskey /history
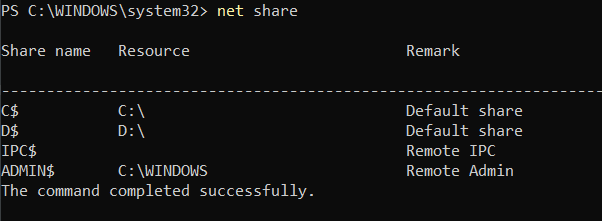
Locally Shared Resources
net Share
If anyone is facing some issues related some commands or tools please consider downloading Sysinternal Suite