Hey guys, so in today’s blog, we will be exploring all the different ways we can use to gather subdomains. This post is specifically written while targeting bug hunters, so it may be useless for people who are not in WAPT or bug bounty.

What is subdomain enumeration?
It is the process in which we collect all the subdomains associated with any given domain. There are multiple ways for doing this ranging from the usage of simple web apps to kali linux tools like sublist3r, we will learn about all possible ways in this guide, so don’t worry and continue reading.
Let’s learn this by example -
Go to crt.sh, enter any domain name in the search box, and click on search.
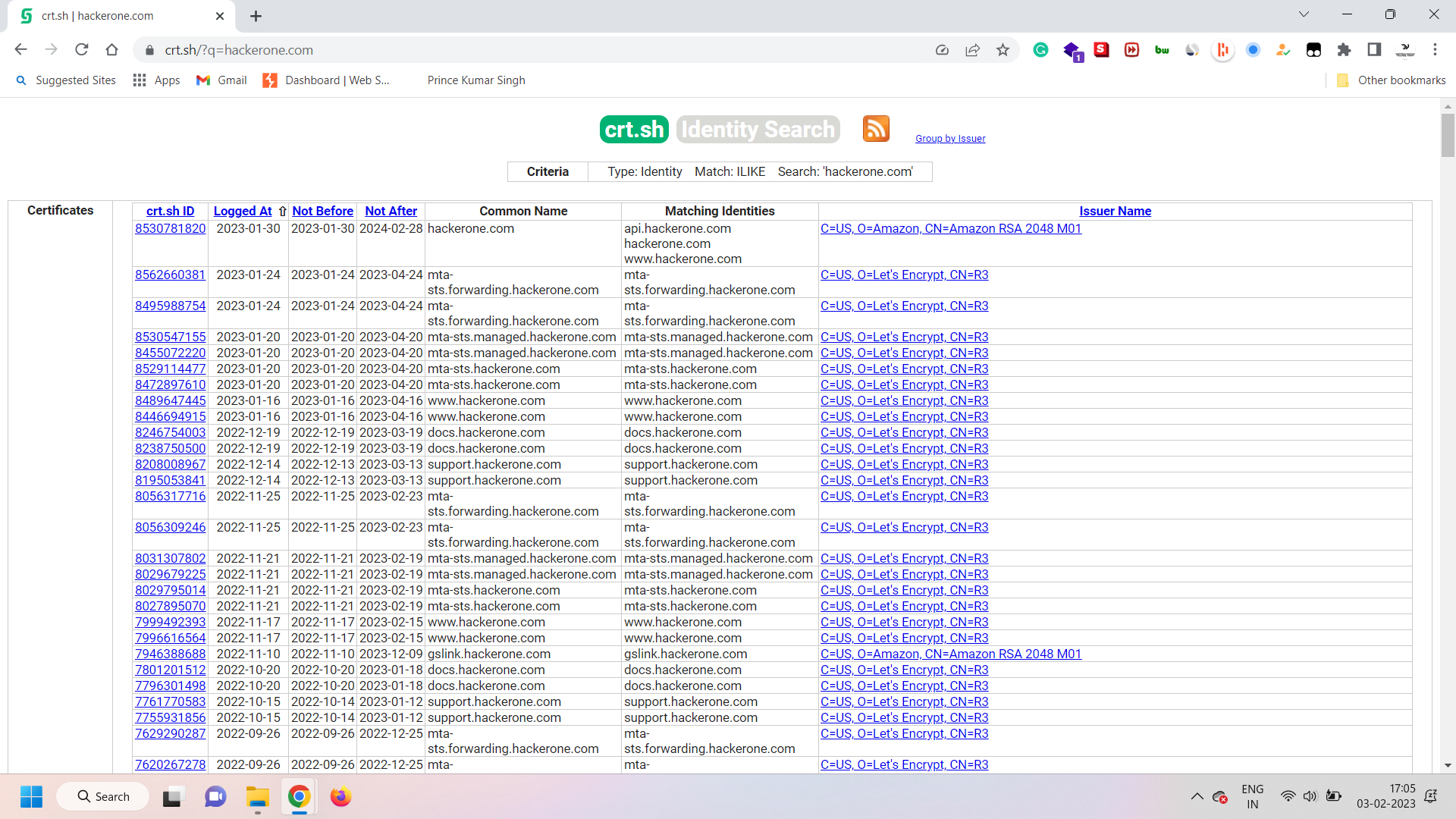
As you can see in the pic above, there is a list of subdomains for the given domain. If you have also performed the search by yourself, you would also get a list of subdomains for the given domain. This process of discovering subdomains is what we call subdomain enumeration.
What’s the need for doing subdomain enumeration?
Subdomain enumeration is useful in many aspects -
- Information gathering - By enumerating subdomains, researchers, and penetration testers can gather valuable information against the target organization such as the services they use, the infrastructure they deploy, etc.
- Increasing attack surface - As we all know, finding bugs on the main domain is difficult as a lot of researchers have already tried hunting on that including some experience security researchers, so it’s always better to hunt on subdomains instead of the main domain.
- Threat Intelligence - It can also provide valuable intelligence about the target organization such as the presence of third-party services.
Now, let’s discuss all the ways we can use subdomain enumeration one by one.
Subdomain Enumeration Techniques -
Using crt.sh
How to: Go to crt.sh, enter the domain name in the search box and click on search. Now, you can see a list of a number of subdomains along with other data.
Note - You can also use an automation tool for this, check out the below repo, it contains all commands for installation and usage.
https://github.com/az7rb/crt.sh
Using shodan -
How to:
Use the below commands one by one -
pip install shodan (For installing official python library for shodan)
shodan init <API_key> (For setting up the api key)
shodan domain example.com (For searching for a domain)
Note - Login to shodan.io , go to your account section and the API key will be visible in the account overview section.
Using Facebook -
How to: Go to the below link and enter your domain in the search box.
https://developers.facebook.com/tools/ct/search/
Now, you can be able to see a list of subdomains. Use them as you want.
Using Virustotal -
How to: Just replace the example.com with the domain https://www.virustotal.com/gui/domain/example.com/relations
Now scroll down a little bit and you will be able to see a list of subdomains.
Using Google -
How to: Just the below dork for searching the subdomains of any domain using google.
site:*.example.com (Replace the example.com with your domain)
These are some easy-to-use tools for subdomain enumeration, apart from these their exist a number of other tools too. I will publish another part of this blog which would include more amazing tools for subdomain enumeration once i hit 200followers on my twitter. Till that enjoy reading blogs on hacklido.
Follow me on Twitter - https://twitter.com/Dheerajydv19