
ISO 27001 is an international standard that specifies the requirements for information security management. Organizations that wish to meet ISO 27001 requirements must put in place a comprehensive information security program that meets the highest standards.
Information security responsibilities must be clearly identified for all individuals and personnel to meet the standard. In addition, an effective risk management program is required.
The basic requirements of the standard are as follows:
Organizations must establish an information security management system (ISMS) and use it to review and update their information security policies and procedures and identify and address any risks that significantly impact their operations or resources.
The ISMS should include specific responsibilities and actions for individuals in the organization and set up mechanisms to identify problems and provide feedback.
The system should be integrated into the organization and its governance structure should cover the entire life cycle of information and must be regularly reviewed and updated.
The standard is divided into two sections.
The first (main) section contains 11 clauses (0 to 10).
The second section, known as Annex A, contains guidelines for 93 control objectives and controls.
The main part of the standard’s clauses 0 to 3 (Introduction, Scope, Normative references, Terms and definitions) serve as an introduction to the ISO 27001 standard.
Clauses 4 to 10, which detail the ISO 27001 requirements, are required if the company wishes to comply with the standard. Annex A of the standard supports the clauses and their requirements with a list of controls that are not mandatory, but that are selected as part of the risk management process.
_. Credit:https://www.imperva.com/learn/data-security/iso-27001/_
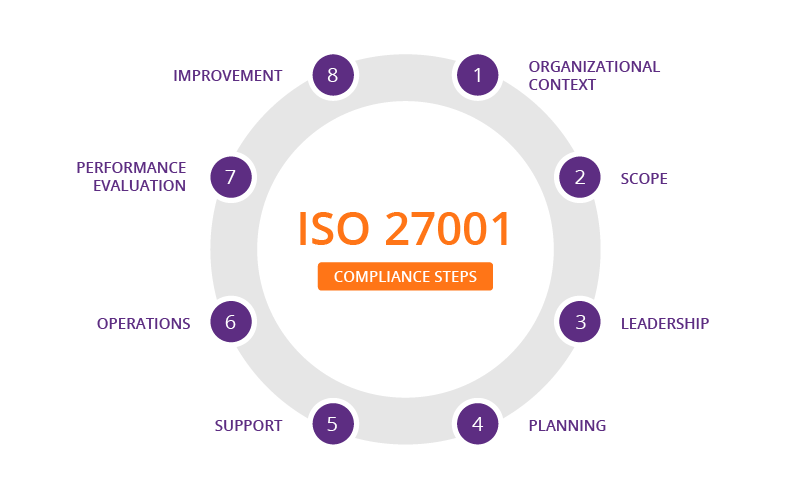
The requirements from clauses 4 through 10 can be summarized as follows:
ISO 27001 clause 4 - Organizational context - Understanding your organization is key to implementing a successful Information Security Management System. It’s important to identify and consider external and internal issues, as well as interested parties. Requirements can be regulatory, but they can also go way beyond.With this in mind, the organization needs to define the ISMS scope.
ISO 27001 clause 5 - Leadership - ISO 27001 has lots of requirements for effective leadership. Top management’s commitment is mandatory for a management system. Organization objectives should be based on the strategic direction and objectives of the organization. Other obligations include providing resources needed for the ISMS and supporting people in their efforts to contribute to it. Furthermore, the top management needs to create a top-level policy for information security. The company should document and communicate its ISO 27001 Information Security Policy to everyone. In order to meet the ISO 27001 standard and report on the ISMS’ performance, roles and responsibilities need to be assigned.
Clause 6 of ISO 27001 - Planning - Risks and opportunities should always be taken into account when planning in an ISMS environment. Information security risk assessments provide a great foundation for planning. Accordingly, information security objectives should be derived from risk assessments. In order to achieve security goals, they need to be aligned with the company’s overall goals and promoted internally because they’re the ones everyone within and aligned with the company works toward. From the risk assessment and the security objectives, a risk treatment plan is derived, based on controls as listed in Annex A.
ISO 27001 Clause 7 - Support - An ISMS is dependent on resources, competence, awareness, and communication.
Documenting information in accordance with ISO 27001 is also required.
You must document, create, update, and control data.
A proper set of paperwork, including a communications plan, is considered necessary for the ISMS to operate effectively.
ISO 27001 Clause 8- Operation - Processes is required for information security implementation.These procedures must be planned, implemented, and monitored.Risk assessment and treatment, which we learned earlier must be prioritized by top management and must be implemented.
ISO 27001 Clause 9- Performance evaluation - The ISO 27001 standard expects the Information Security Management System to be monitored, measured, analyzed, and evaluated. The company must conduct internal audits in addition to checking key performance indicators of its work.
Finally, top management must review the organization’s ISMS and ISO 27001 KPIs at regular intervals.
ISO 27001 Clause 10 - Improvement -The evaluation is followed by improvement.Non conformities must be addressed by taking action and removing the root causes.Furthermore, a process of continuous improvement should be implemented.
Annex A (normative) Information security controls -
This Annex contains a list of 93 safeguards (controls) that can be implemented to reduce risks and meet security requirements from interested parties.
The controls to be implemented must be marked as applicable in the Statement of Applicability.
Hope you guys find this helpful!
Stay tuned for more such Information!
Adios!!!!!