Hello Guys..!!
Hope you are doing well
I am Back with a story today about how to test exposed API Keys or Tokens using Nuclei “token-spray” templates.
I hope most of them know or heard about the keyhacks github repo which contains various ways to validate the API keys whether they’re valid or not.
Keyhacks
So, Today I want to tell you there is another quick method to validate the exposed API Keys and Tokens using Nuclei token-spray templates.
This “Token-Spray” directory holds templates that have static API URL endpoints. By providing token input using a flag, Nuclei will test the token against all known API endpoints within the API templates, and return any successful results. By incorporating API checks as Nuclei Templates, users can test API keys that have no context (i.e., API keys that do not indicate for which API endpoint they are meant)
Check the below git repo to go understand the process in more detail.
Nuclei Token Spray
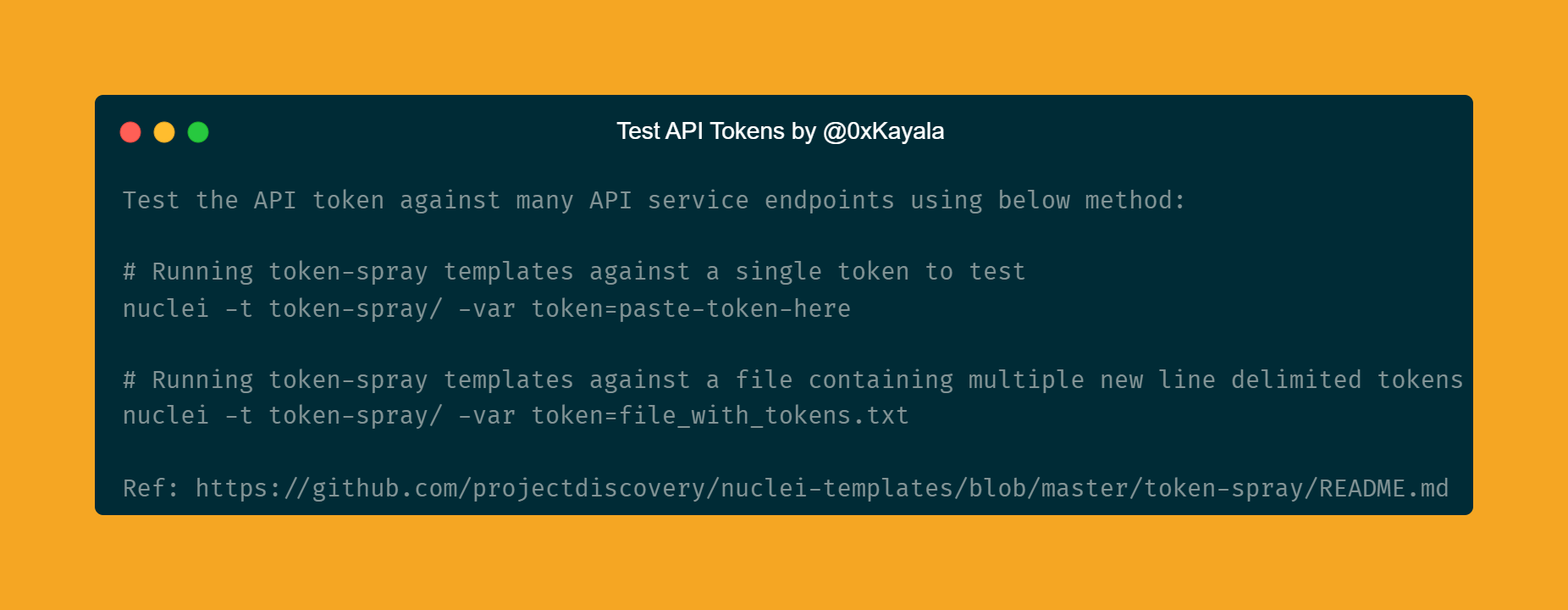
Here are the commands which you can use to validate the API Keys or Tokens:
Running token-spray templates against a single token to test
nuclei -t token-spray/ -var token=paste-token-here
Running token-spray templates against a file containing multiple new line delimited tokens
nuclei -t token-spray/ -var token=file_with_tokens.txt
For Example:
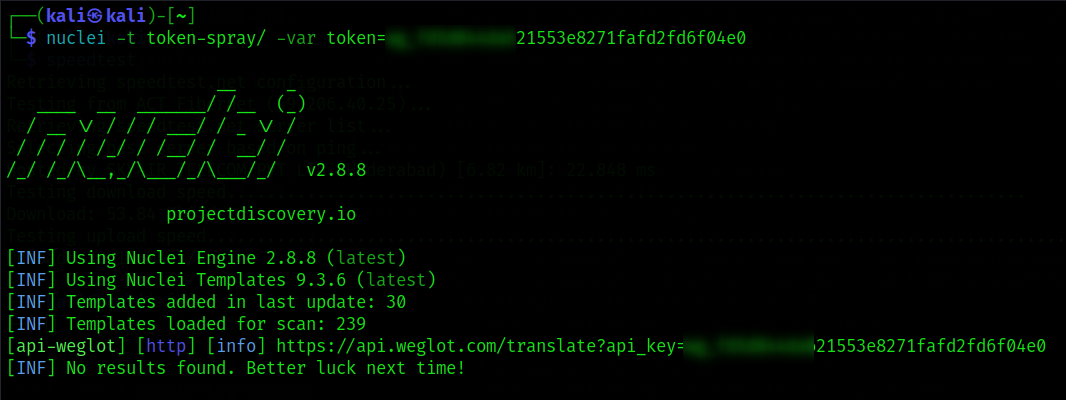
You can check the above screenshot where I pasted the exposed token at the end of the command to know which service it belongs to and later you need to open the endpoint along with the API token to validate it.
If there are multiple API tokens which need to be tested, save them into a text file and use the below command to test all of them in a single take.
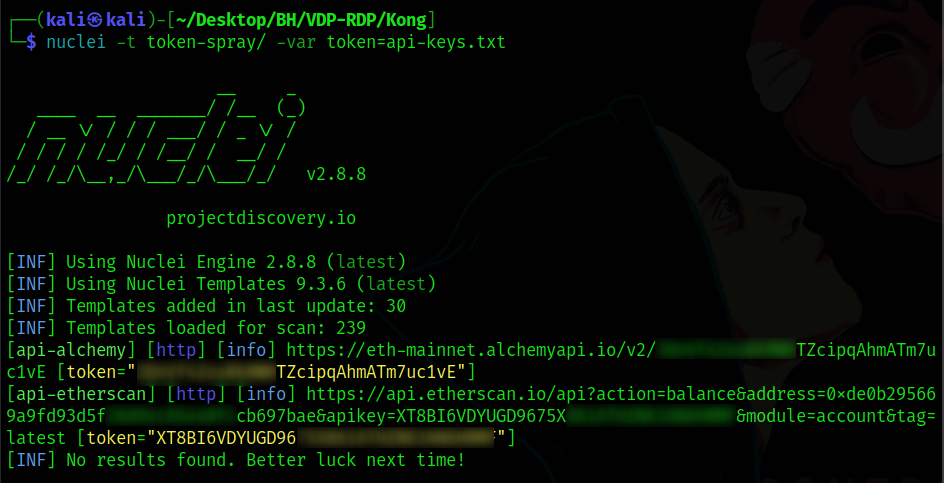
I hope you guys understood how to test and validate the exposed API keys or tokens using this method. I hope this article will be helpful to the newcomers.
So, That’s it for today.
If you like this post, don’t forget to give me 🤍
Resources: Nuclei | Keyhacks
Support me: If you like to support me, buy me a cup of coffee ☕
Follow me: @0xKayala | Satya Prakash