Itis been a while, I haven’t posted anything on medium. But today I am here with another amazing blog post on Malware Analysis. In this blog, we will see what does actually a Malware Analysis and how to get started a career in Malware Analysis.

You can use below given link to join our discord community server and rock with your mates in the community.
Here: https://discord.com/invite/VKJSmqDN5P
What is Malware ?
Malware is nothing, just a term which is used to indicate a malicious software or a program on the digital device. Any software with a malicious intent is a Malware. For example, If you create a program that will delete files from your friend’s computer is a Malware.
Malware can be used for a variety of purposes, including stealing personal information, spying on user activities, disabling or damaging computer systems, and extorting money from users.
What is Malware Analysis ?
In simple terms, “Malware Analysis is the process of identifying the malicious software from a digital device and understand how it works and what it does to target system to protect other system from malware infections.”
In technical terms, “Malware analysis is the process of dissecting and understanding malicious software, commonly referred to as “malware,” with the goal of determining how it works, what its capabilities are, and how to mitigate its impact.”
How to identify the Malware on the system ?
Malwares are generally identified by signatures discovered while analyzing the malware. There are mainly two types of signatures,
- Host Based Signatures
- Network Based Signatures
Host Based Signatures
Host based signatures are specifically related to system or compromised computers. For example, If a computer is infected with malware that creates and changes some registry keys on the computer then this behavior is known as host based signature.
Host based signatures are more effective. A signature is a unique pattern or characteristic that is associated with a particular piece of malware. When a security tool detects the presence of this signature on a system, it can identify the malware and trigger an alert or take action to block or remove it.
Network Based Signatures
Network-based signatures are created by analyzing the behavior, protocol, and other characteristics of known malware and malicious network traffic. These signatures are then stored in a signature database, and security tools use them to compare against network traffic to determine if it matches any known malicious signatures.
These signatures are prepared by monitoring network traffic. It can be created without malware analysis but with malware analysis is more effective.
Malware Analysis Techniques
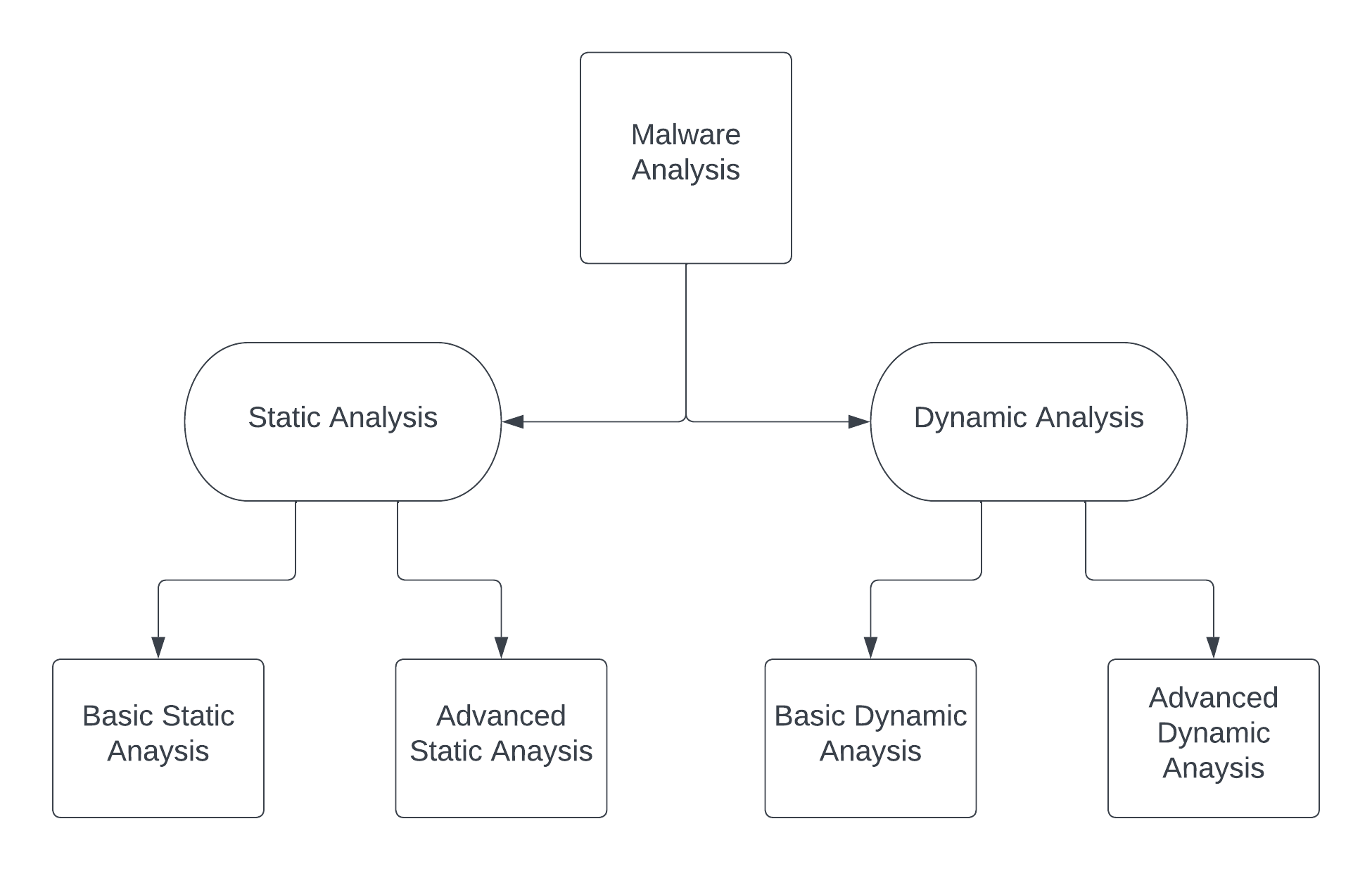
There are mainly 4 types of malware analysis techniques used by malware researchers.
- Basic Static Analysis
- Basic Dynamic Analysis
- Advanced Static Analysis
- Advanced Dynamic Analysis
Basic Static Analysis
Basic static analysis consists of examining the executable file without viewing the actual instructions. Basic static analysis can confirm whether a file is malicious, provide information about its functionality, and sometimes provide information that will allow you to produce simple network signatures. Basic static analysis is straightforward and can be quick, but it’s largely ineffective against sophisticated malware, and it can miss important behaviors.
Basic Dynamic Analysis
Basic dynamic analysis techniques involve running the malware and observing its behavior on the system in order to remove the infection, produce effective signatures, or both. However, before you can run malware safely, you must set up an environment that will allow you to study the running malware without risk of damage to your system or network.
Like basic static analysis techniques, basic dynamic analysis techniques can be used by most people without deep programming knowledge, but they won’t be effective with all malware and can miss important functionality.
Advance Static Analysis
Advanced static analysis consists of reverse-engineering the malware’s internals by loading the executable into a disassembler and looking at the program instructions in order to discover what the program does. The instructions are executed by the CPU, so advanced static analysis tells you exactly what the program does. However, advanced static analysis has a steeper learning curve than basic static analysis and requires specialized knowledge of disassembly, code constructs, and Windows operating system concepts.
Advanced Dynamic Analysis
Advanced dynamic analysis uses a debugger to examine the internal state of a running malicious executable. Advanced dynamic analysis techniques provide another way to extract detailed information from an executable. These techniques are most useful when you’re trying to obtain information that is difficult to gather with the other techniques. In this book, we’ll show you how to use advanced dynamic analysis together with advanced static analysis in order to completely analyze suspected malware.
What are the types of Malware ?
There are mainly two types of malware,
- Mass Malware
- Targeted Malware
Mass Malware
Mass malware, also known as “bulk malware,” is a type of malware that is designed to infect as many systems as possible, often in a short period of time.
Mass malware can take many forms, including viruses, trojans, worms, and ransomware. It is typically distributed through a variety of channels, such as malicious email attachments, compromised websites, or infected software downloads.
Targeted Malware
Targeted malware, also known as “advanced persistent threats” (APTs), is a type of malware that is designed to specifically target and compromise a particular organization or individual.
Targeted malware is often created and distributed by sophisticated threat actors, such as nation-states, cybercriminals, or hacktivists. These attackers use a variety of tactics, such as social engineering and reconnaissance, to gain knowledge about their target and craft a customized attack.
General Rules for Malware Analysis
- Don’t get too caught up in details.
- Focus on key features.
- In different and complex situations, try to get a general overview (Step back and try to see things in another way)
- There is not only one approach.
- If you get stuck, don’t spend too long on any single issue, move on something different.
- Try to analyze the malware from different angles.
This is it for today’s article. If you found it to be interesting and informative then share it with your friends. Thank you for reading till here. Let me know your queries or topics which you want to read an article in the comment section.
You can follow on social media here: LinkedIn, Instagram, Twitter