Summary
Local File Inclusion (LFI) is a type of web application vulnerability that allows an attacker to include and execute arbitrary files on the web server. An attacker can take advantage of this vulnerability by passing a malicious file path as a parameter, which could be a local file on the server. This can allow the attacker to view sensitive information, such as configuration files or user credentials, execute arbitrary code, or even gain complete control of the server.
Description
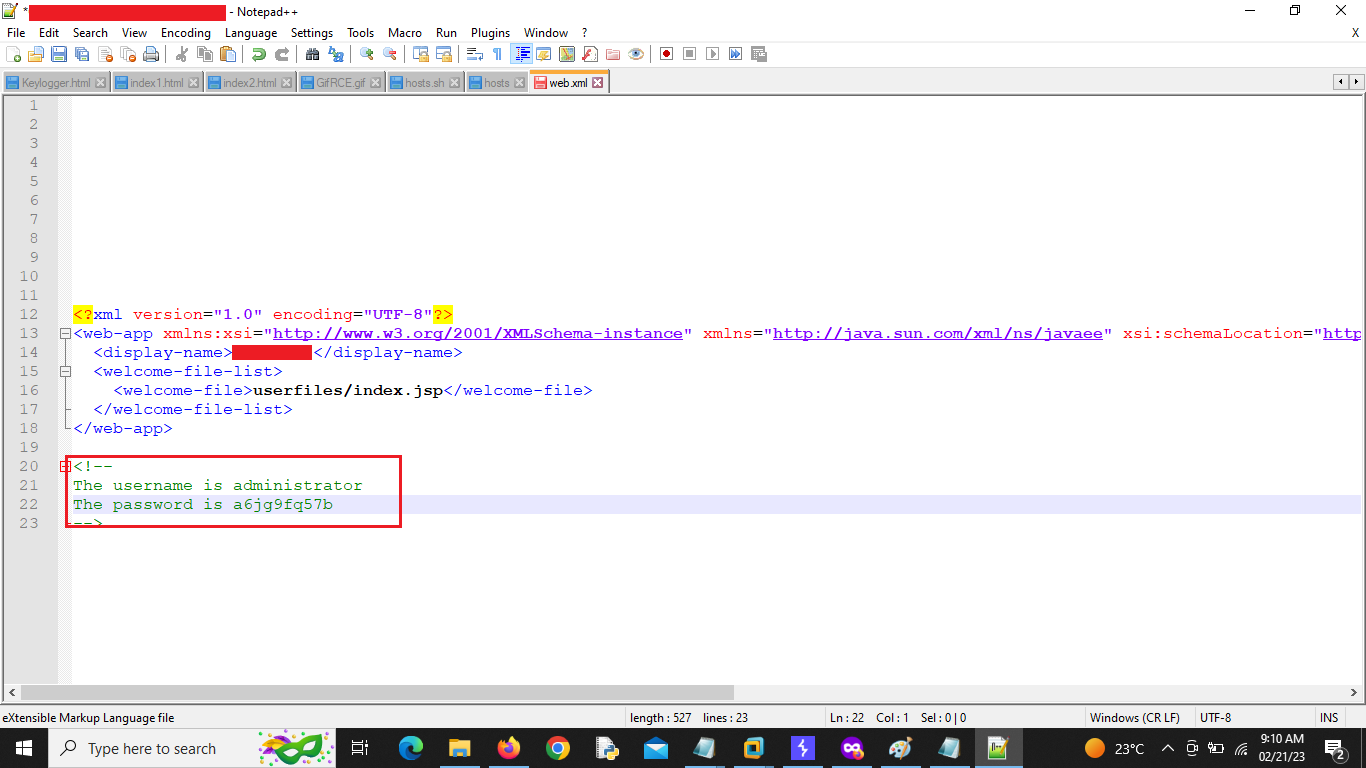
I have found a local file inclusion (LFI) vulnerability on one of the program where I was able to download the web.xml file from WEB-INF/ directory. However the bug is quite simple with a small tweak.
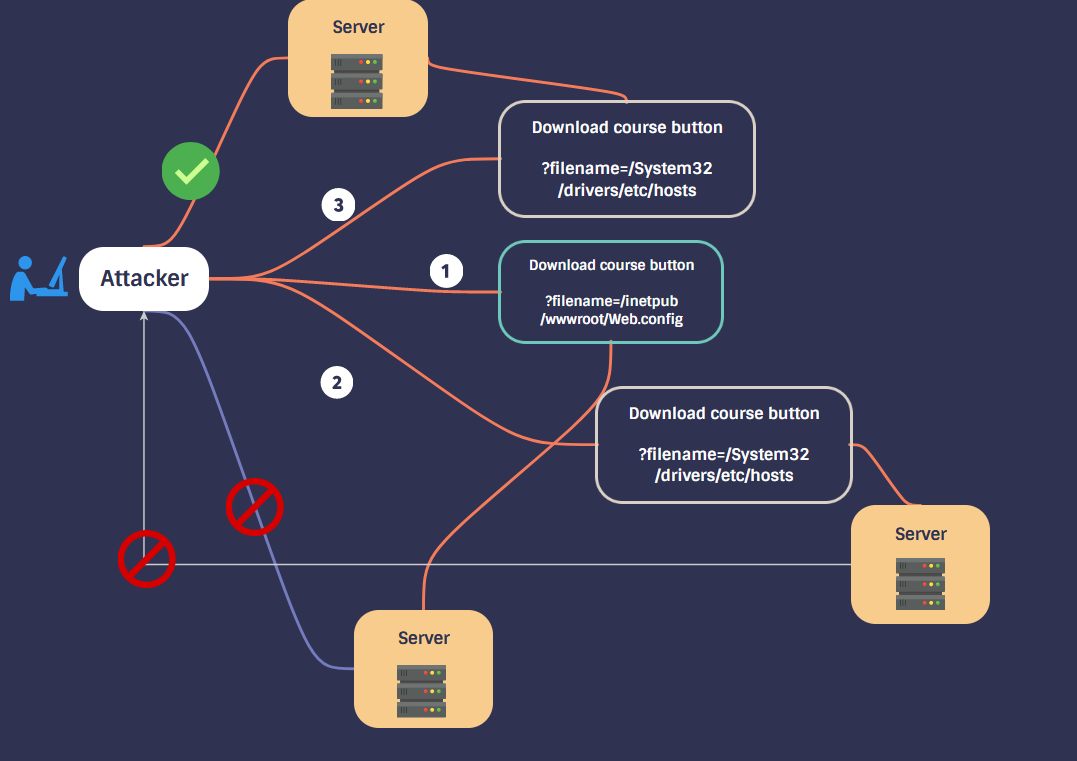
The website had a Download Course Details option where it was fetching course details from a server via filename= parameter, it was a POST request. The website was running on IIS server so initially I thought of downloading some sensitive files however they were all restricted but then I thought of downloading the web.xml file which was successfully downloaded. The downloaded file had the username and password of admin but I was not able to find a login portal so the severity was downgraded. I did not report the bug as the target was OOS (Out-Of-Scope).
How I found this vulnerability ?
I went to the website where there was an option to “Download Course Details”
I right clicked on the button and clicked on Inspect to check the hyperlink and from where it is fetching the file
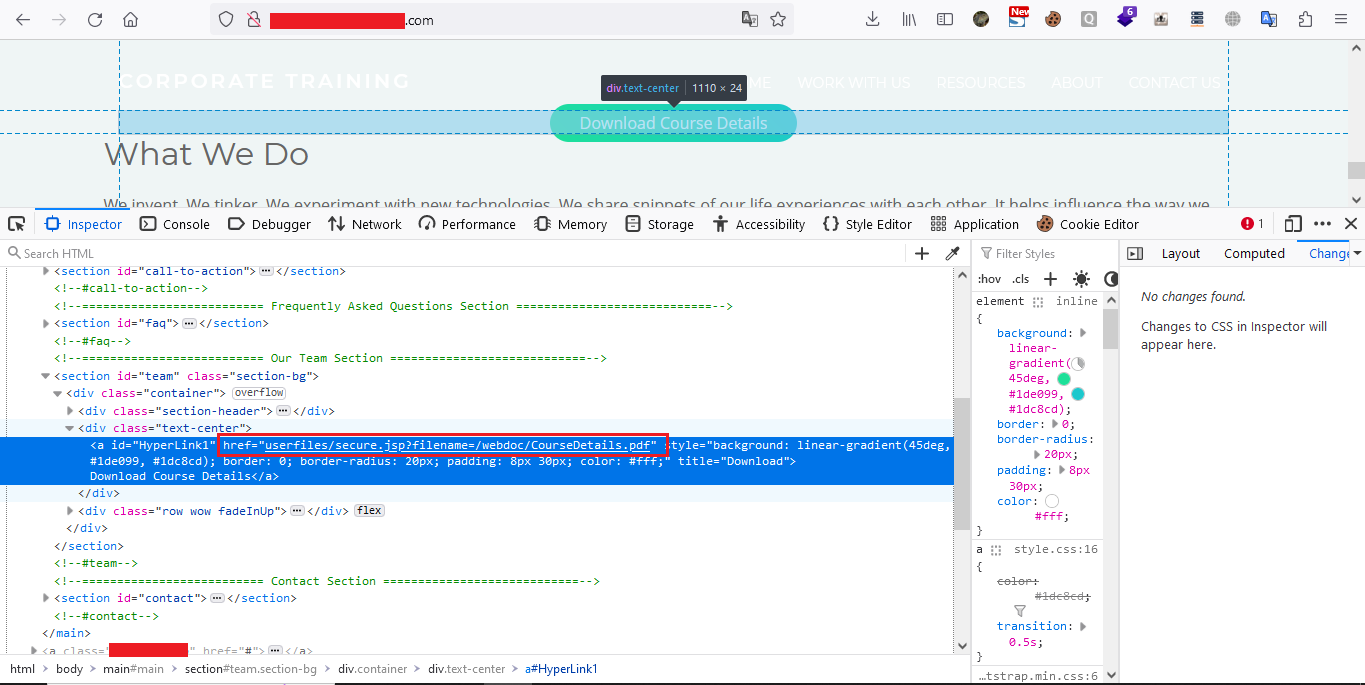
I knew that it was using the IIS server so I searched for the path of web.xml
I edited the path to ?filename=/WEB-INF/web.xml
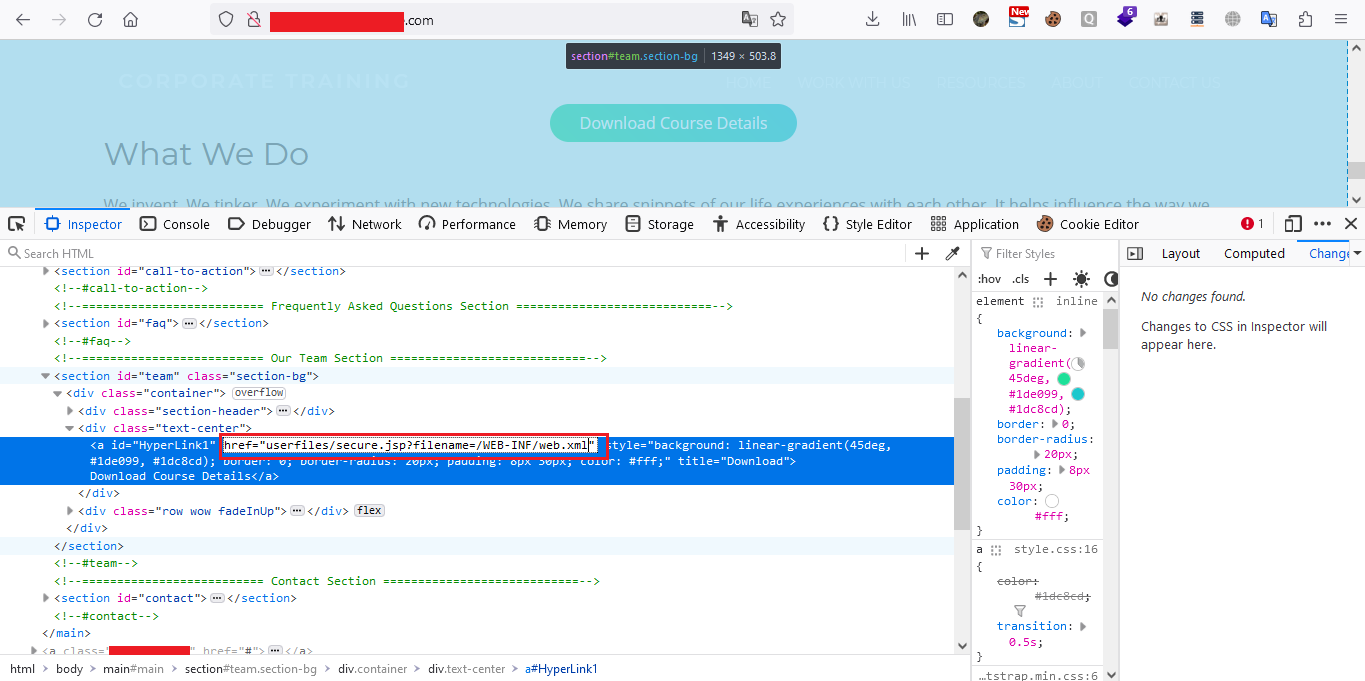
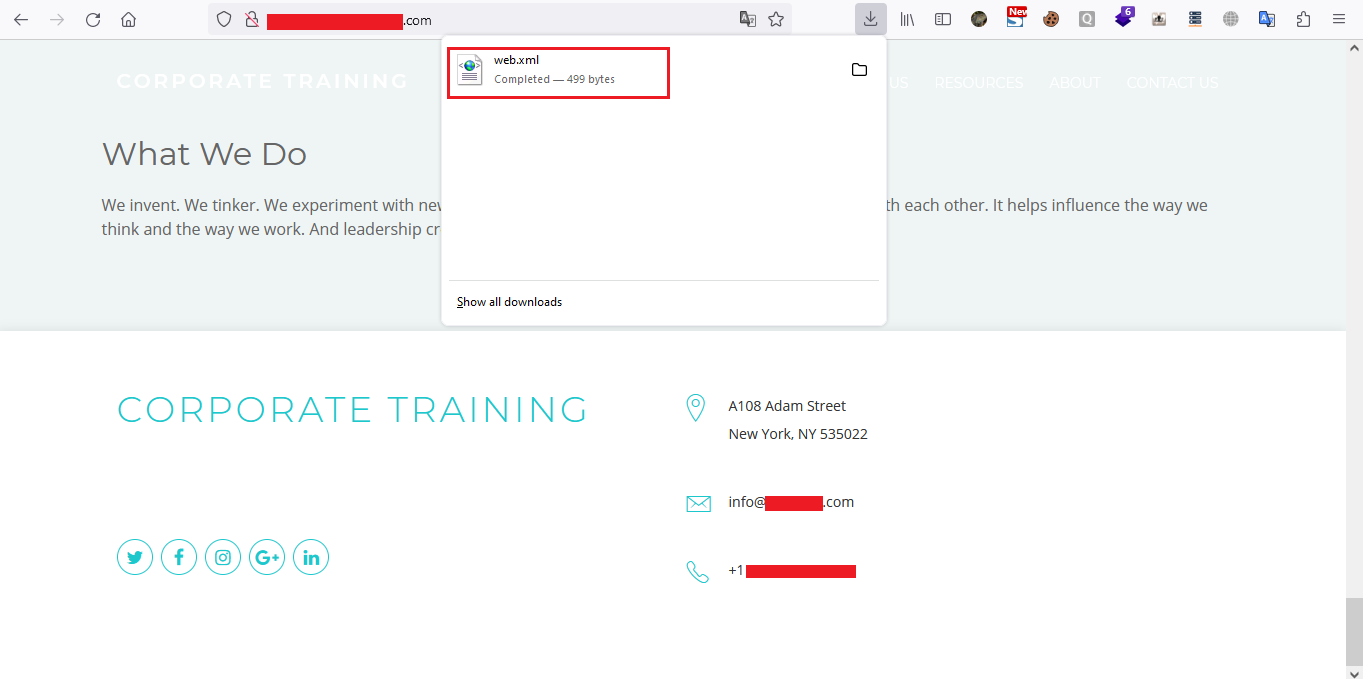
Then I clicked on the button and downloaded the file and opened it, I got the credentials
Why it happened ?
In my opinion,
The website was not validating and sanitizing the user input before processing it. However major of the sensitive files were blocked but blocking particular files is not the ideal solution from my perspective, the user input should validated and sanitized before processing it.
Impact
The impact of an LFI vulnerability can be severe, as it can lead to a complete compromise of the web server and its data. However in my case the impact was limited to downloading the web.xml file as all the major sensitive files were restricted for downloading, so the impact would be medium.
NOTE : If I could have found the login panel that gives me the access with the credentials I obtained then the severity would have been high.
Calculated CVSS
Vector String - CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N
Score - 5.3 (Medium)
Mitigation
Input validation and sanitization should be done if any user input arrives. Server should not process the user input without validation. The validation and sanitization should be done on the client-side as well as server-side. Additionally, the application should avoid using user input to construct file paths and instead use a whitelist approach to specify allowed file paths. Web application firewalls can also be used to detect and block attempts to exploit LFI vulnerabilities.
