
Welcome to my blog on Document OSINT!
As someone who frequently conducts OSINT investigations, I find it crucial to be familiar with various tools and techniques to retrieve information from documents. In this blog, I will walk you through some of the resources I use to extract valuable data from various types of documents.
Search Engines
Let’s start with the most popular search engine - Google. Google searching is a powerful tool that can help you find information about anything you need. But did you know that Google Docs and Microsoft Docs are also useful resources for document OSINT? With Google Docs, you can search for public documents that have been shared by others, which can include resumes, business plans, and other types of documents. Similarly, Microsoft Docs can be used to search for resumes or other relevant documents.
Cloud Storage
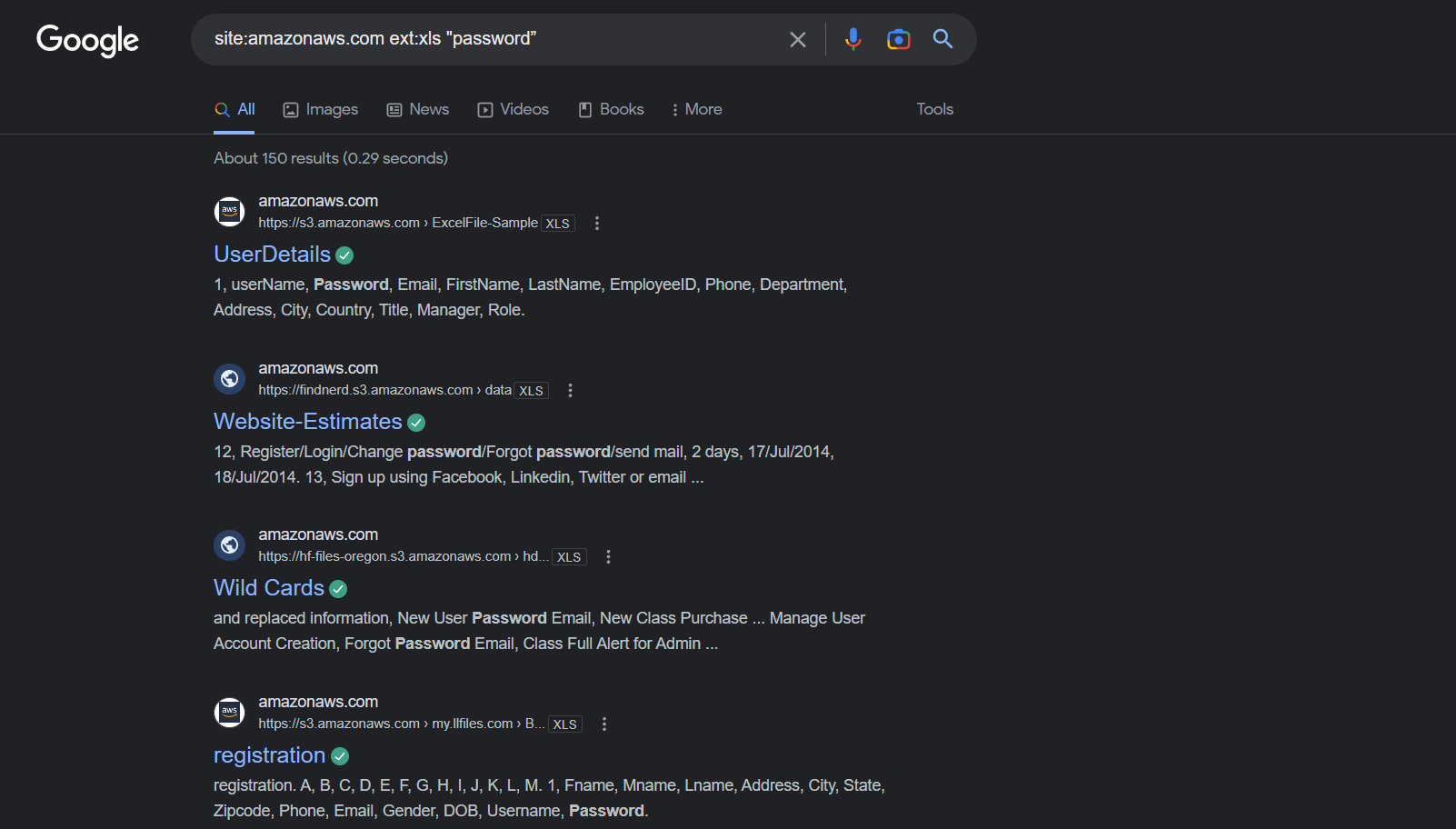
If you’re looking for specific types of documents, Amazon Web Services (AWS) and Gray Hat Warfare can come in handy. By using the search query "site:amazonaws.com ext:xls “password”", you can find 114 Excel spreadsheets containing the word “password.” Similarly, by using "site:amazonaws.com ext:pdf “osint”", you can find 260 PDF files containing the word “osint.” Gray Hat Warfare is a database of open S3 buckets, which can be used to find publicly accessible documents.
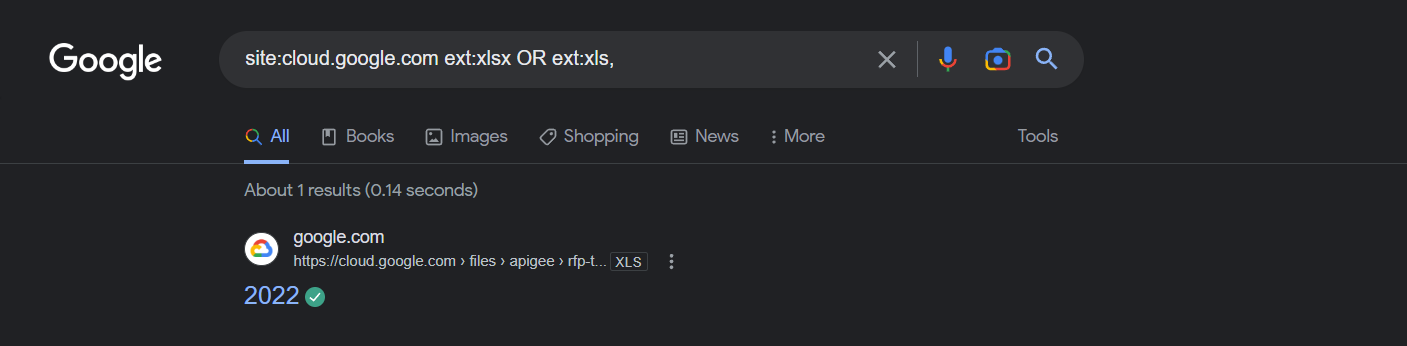
Google Cloud Storage is another useful resource for document OSINT. By using the search query “site:storage.googleapis.com ext:xlsx OR ext:xls,” you can find 2,310 spreadsheets, while using "site:storage.googleapis.com “confidential”" will give you access to 9,502 documents marked as confidential. Moreover, you can use "site:storage.googleapis.com “confidential” ext:pptx" to find 11 PowerPoint files marked as confidential.
Presentation Sites
There are also several presentation repositories that can be useful for document OSINT. Slide Share, 1SSUU, Slidebean, Prezi, Slide Search, Author Stream, Scribd, and PDF Drive all contain various types of presentations that can be valuable for investigations. WikiLeaks and Cryptome are also great resources for obtaining sensitive documents.
Publicly Available Docs
Paste sites like Pastebin, Paste.org, and PrivateBin can be used to find text documents that have been shared publicly. For example, using "sitc:pastebin.com “osint”" will give you access to pastes containing the word “osint.” Additionally, several document metadata applications like ExifTool and FOCA can be used to extract metadata from files.
Vehicle Records
Lastly, rental vehicle records from Enterprise, Hertz, Alamo, Thrifty, and Dollar can be accessed to obtain valuable information about individuals’ travel history.
Conclusion
In conclusion, document OSINT can provide valuable insights into various types of investigations. With the tools and resources mentioned in this blog, you can effectively retrieve information from publicly accessible documents. So next time you’re conducting an OSINT investigation, be sure to keep these resources in mind!
Refer here to get links