Hello, readers It’s been a while since I wrote a blog, from now on I try to post regularly on whatever stuff is interesting to me. The reason behind this blog, Ever come across a blog or video showcasing SPI firmware extraction there are tons of tutorials out there on firmware extraction from SPI but most of them show using some sort of hardware tools like bus pirate, Attify badge, etc. but here I’ll be showing a method which uses raspberry pi, so no special hardware is needed.
There are tons of tutorials out there to explain spi interface, firmware, spi protocol, etc. Why need to extract firmware? In this blog, I’ll be extracting firmware from DIGISOL DG-GR0101 https://www.digisol.com/products/ftth-solutions/gepon/digisol-gepon-onu-router-dg-gr1010-with-1-pon-1-giga-port/ cable modem. I tried to search for the firmware online but couldn’t find the firmware for this device, may be reached its end of life. If I wanted to reverse engineer the firmware I have to extract the firmware from the device and the firmware is stored in the flash of the IoT device, which might be NOR, NAND, eMMC, etc. We can find the type of flash by opening up the device.
Main PCB
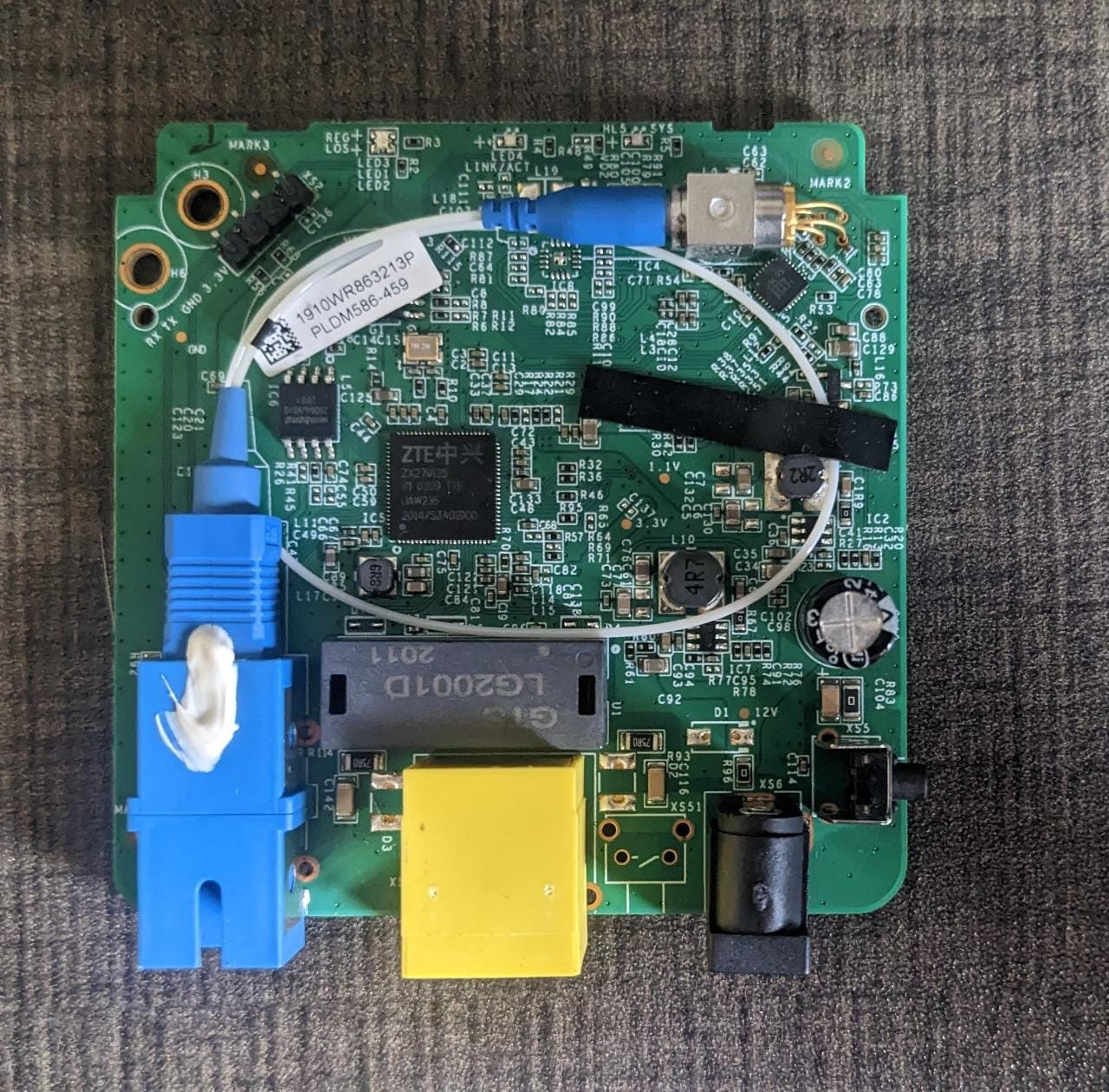
This is the main of the router. Staring at the PCB for a while I found this marking RX, TX, GND, 3.3v which clearly indicates UART, the headers are not present in the PCB I soldered it on the board. We will explore more in our next blog post. Additionally, I found I2C as well which will be covered in a separate blog post.

I found the flash as well. It is a windbond 25Q64JVSIQ SPI flash. When I was talking to my friends & colleagues about IoT security or explaining them, they often asked the question how did you instantly identify that is an SPI flash or most components look similar are you sure that is an SPI flash So you may also have the same question so Ill explain the answer is simple, If you’re unsure of hardware components just google the part number with manufacturer name you can identify the data sheet of that component by that you can identify if its is a flash, soc, amplifier, laser driver, etc. and by experience, you can Identify flash chips by eyeballing.
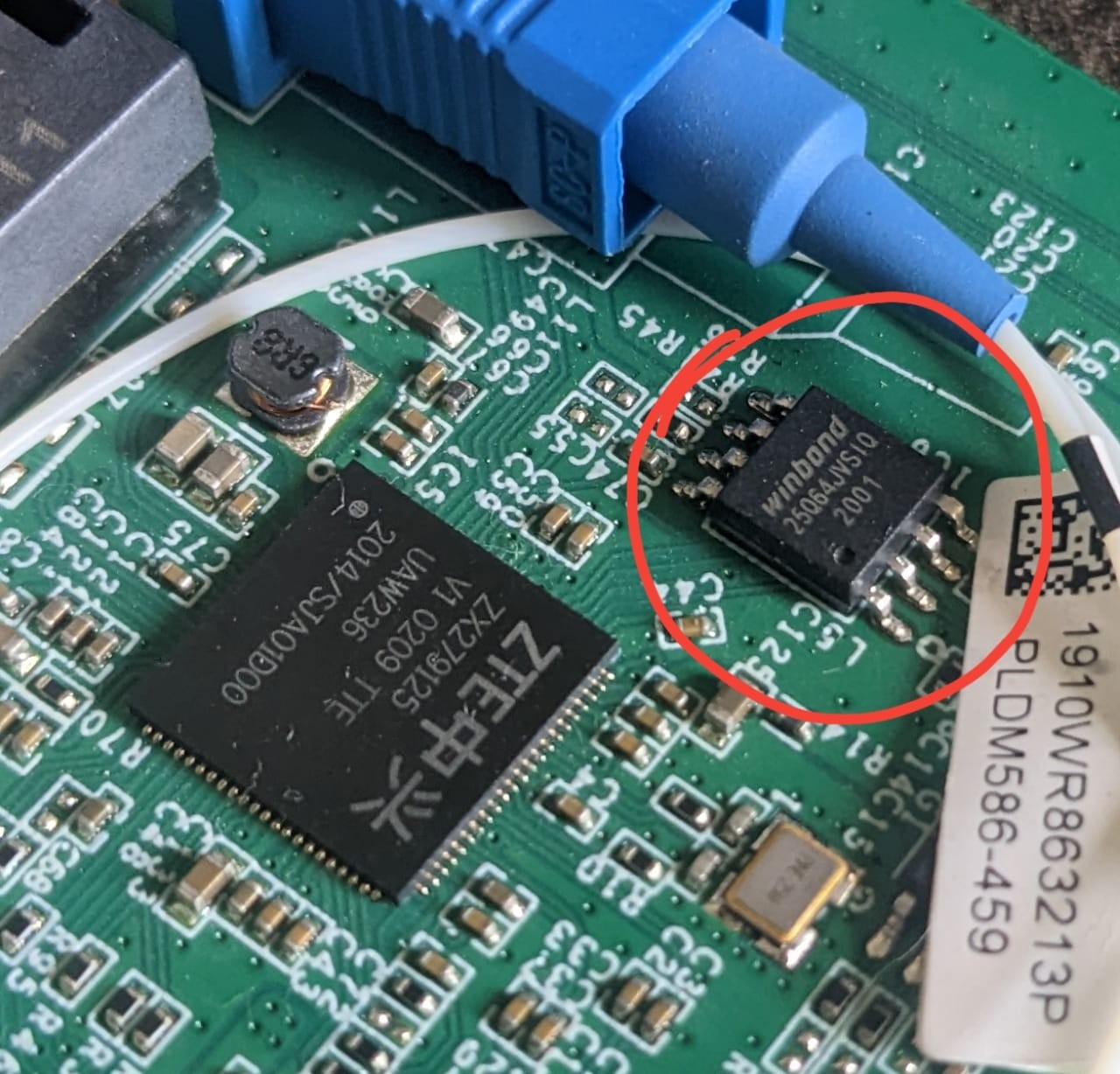
We found SPI, let’s extract firmware from it. The data sheet for this flash can be found at https://www.winbond.com/hq/product/code-storage-flash-memory/serial-nor-flash/?__locale=en&partNo=W25Q64JV. Using the datasheet we found the pin configuration for our flash.
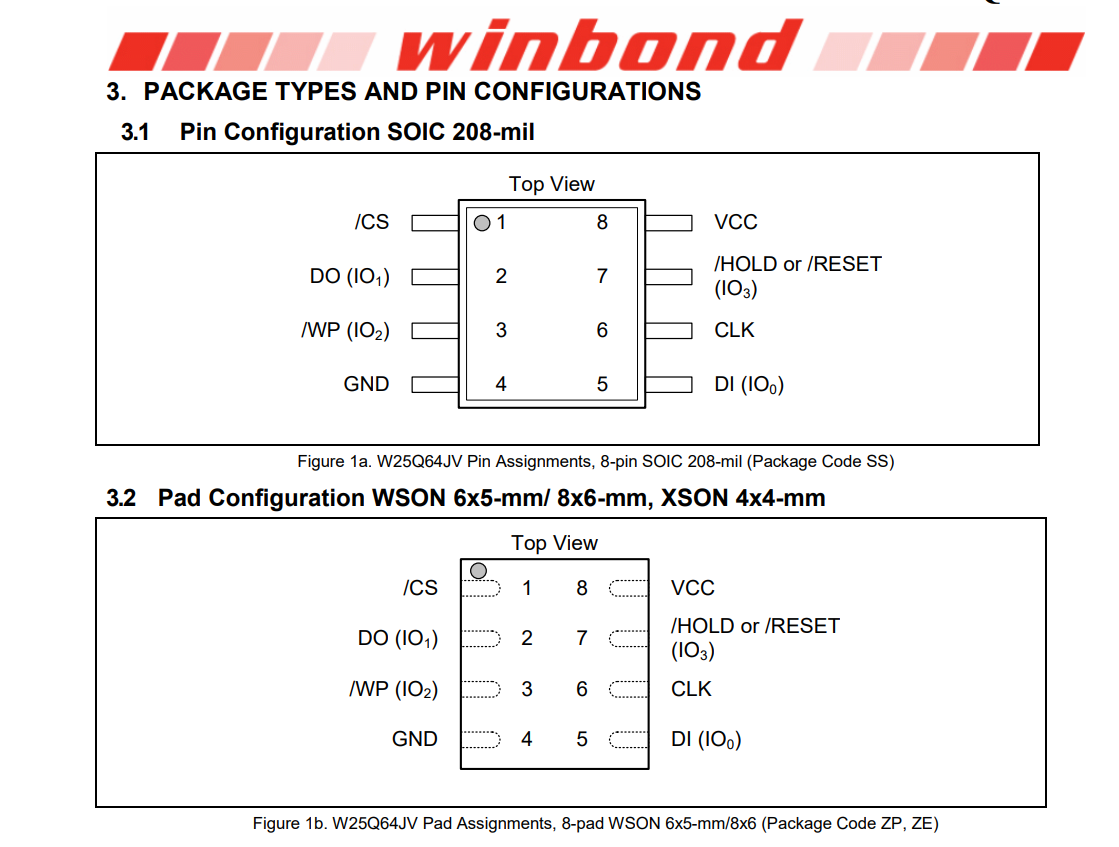
Interfacing SPI
Now login to you’re raspberry pi, I’m using a raspberry pi 3 model B+, but it will work on other raspberry pi models as well and connected over ssh from my terminal. Use the below command to install flashrom and enable the SPI interface in your raspberry pi.
sudo apt update && sudo apt upgrade
sudo apt install flashtom raspi-config
Now to enable spi interface type raspi-config -> Interfacing options -> SPI then enable it.
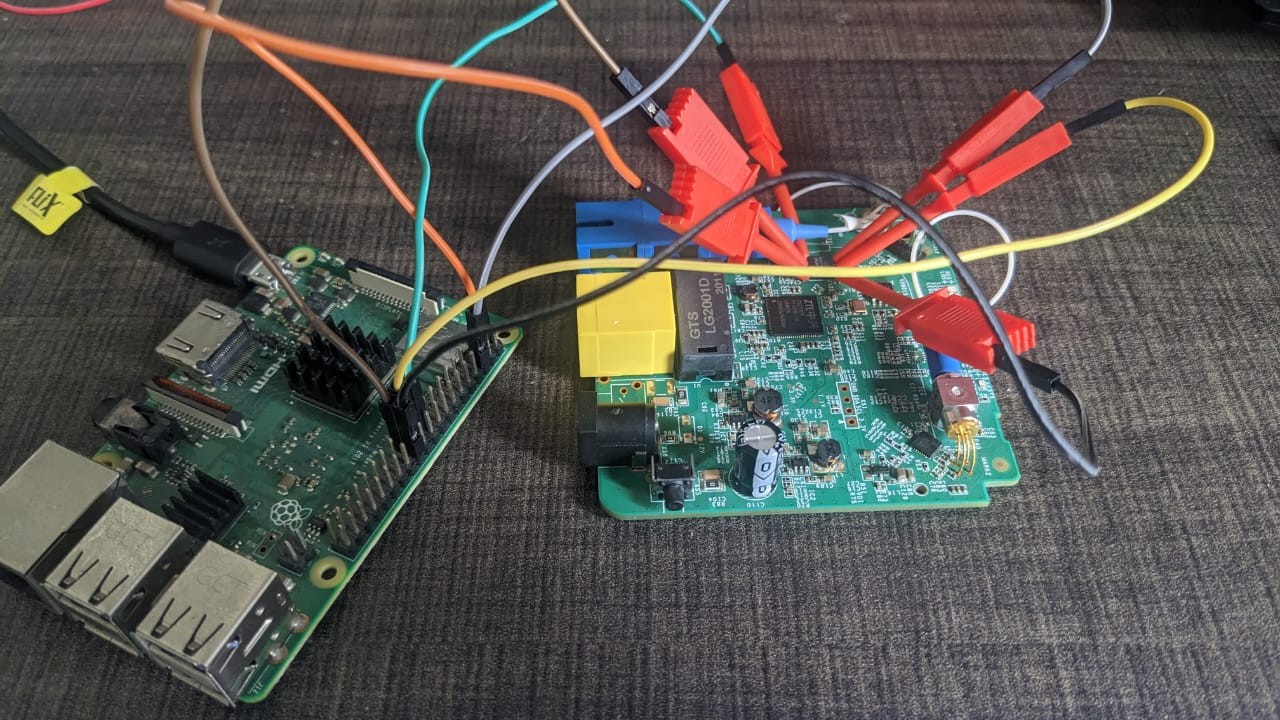
We have 2 ways to connect the SPI flash to the raspberry pi, one way is using a SOIC8/SOIC16 clip we have to hook the clip to the SPI flash and connect the wires with the raspberry pi. The second way is using some test hook clips to hook the pins of the flash. I have a SOIC16 clip but I don’t have the appropriate connector for it and jumper wires are useless in this case. We know the pinouts for Flash from the datasheet for now, to identify pinouts for raspberry pi I found this https://pinout.xyz/ page that shows the GPIO pins of the raspberry pi.
Connect the pins in this order to raspberry pi. The raspberry pi has 2 spi interfaces we are connecting to spi0 of this interface, these are the pinouts for the spi0 interface in raspberry pi.
| SPI PIN | Rasp GPIO |
|---|
| CS | GPIO 8 |
| GND | GPIO 39 |
| VCC | GPIO 1 |
| MOSI | GPIO 10 |
| MISO | GPIO 9 |
| CLK | GPIO 11 |
I connected the test hooks to the raspberry pi using the above pin configuration.

Firmware extraction
Now we can use flashrom tool to dump the firmware from the hardware. Flashrom is a command line utility that can be used to dump firmware from various SPI flashes. Sometimes you may encounter some Flash configurations that are not defined in flashrom in that case we can write our own custom configuration for our Flash.
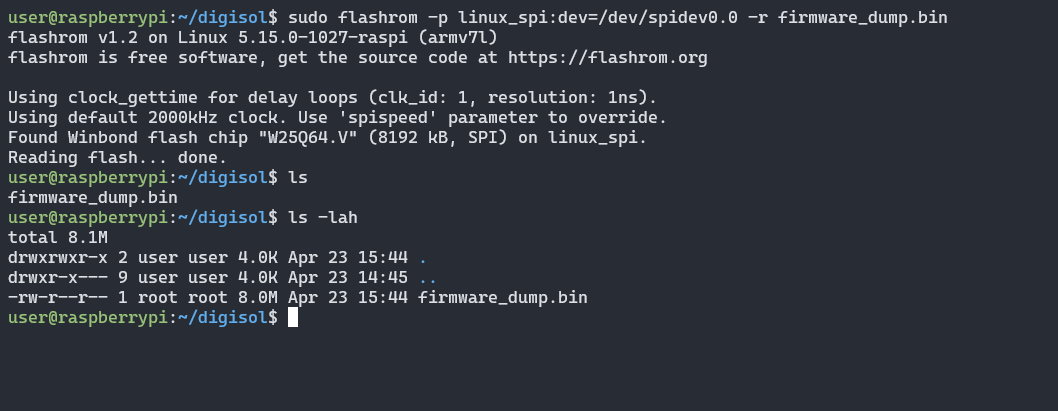
sudo flashrom -p linux_spi=/dev/spidev.0.0 -r firmware_dump.bin
-p parameter used to specify the programmer, as explained previously flashrom supports multiple programmers one of the inexpensive ones is CH341A flasher, then bus pirate, hydra bus, attify badge, etc. Here we used the inbuild one present in the raspberry pi /dev/spidev.0.0. in case you used the spi1 interface used /dev/spidev0.1 then -r parameter is used to mention the dump file, it will write the extracted contents as firmware_dump.bin make sure to dump the files again with a different name and compare it using some sort of hashing algorithm to verify you haven’t missed any bytes.
I have successfully extracted the firmware, so I can start to reverse engineer the firmware from now on. Also, we can even write the backdoored firmware back to flash, which will be covered in an upcoming blog, or at the time of you reading this blog it may be released.