
A “computer virus” is one of the few transcendent technical terms everyone understands, including children. Regardless of socioeconomic background or age, everyone has an immediate negative connotation to that term. It is usually associated with something destructive to the technology that we all rely on, whether it’s a laptop, smartphone, application, or gaming system, demonstrating how ubiquitous computers and technology have become in our daily lives. Part of the reason is that we have all been exposed to the impact of viruses, such as the flu or the common cold. And like its biological counterparts, a computer virus also replicates and can be transmitted from one host to another, creating problems ranging from annoying to downright destructive.
So, in recognition of over 50 years since the first computer virus was discovered, I have decided to provide a brief historical insight into the history of computer malware from the pre-internet era to the current world of botnets, ransomware, viruses, worms, and more.
To start, here is some basic terminology:
🔹A virus cannot replicate without human interaction, whether clicking a link, opening an attachment, launching an application, or downloading a file.
🔹A worm does not require human interaction and can replicate on its own, tunnel deep into systems, and move between devices.
🔹Malware is a generic term that encapsulates all threats - viruses, worms, botnets, ransomware, etc., - anything malicious that is software-related.
We would be here until tomorrow morning if I attempted to cover all malware and events over the past 50 years in such as short blog post. Instead, I’ve highlighted many of the most notable examples and memorable events of the past 50 years.
𝚃𝚑𝚎 𝚎𝚊𝚛𝚕𝚢 𝚢𝚎𝚊𝚛𝚜
🔹𝟷𝟿𝟽𝟷: 𝚃𝚑𝚎 𝙵𝚒𝚛𝚜𝚝 𝙿𝚛𝚘𝚘𝚏 𝚘𝚏 𝙲𝚘𝚗𝚌𝚎𝚙𝚝
Before the internet existed, at least in the form we know today, there was the Advanced Research Projects Agency Network, or ARPANET, for short. ARPANET began in 1967 with a goal of connecting remote computers to one another over geographically dispersed locations. The first computers were connected in 1969, and one year later, the Network Control Program (NCP) was developed (the predecessor to the modern TCP/IP stack). NCP was the first network transport layer ’protocol to enable data to flow from one computer to the next.
In 1971, the first microprocessor was developed, the Intel 4004. It was the first commercially produced general-purpose CPU. Its size (two inches rather than 12), price ($60), and performance (comparable to much larger and more expensive processors) ushered a new era in computing.
Ironically, 1971 also saw the premier of the world’s first virus Proof of Concept, dubbed “The Creeper.” Although credited and referenced by various entities as the world’s first computer virus, the Creeper actually exhibited the behavior of a worm. Based on a concept first articulated by German mathematician John von Neumann in the 1940s, it was built at BBN (an American research and development company later acquired by Raytheon) by engineer Bob Thomas. It spread through ARPANET computers and posted the following message:

Like it’s modern worm successors, it spread via a network protocol. The intent was not for malicious or devious reasons, but to see if the “I’m the creeper, catch me if you can” message could propagate to other computers via ARPANET.
It did.
Now, Ray Thomlinson, one of Thomas’ colleagues, developed what would be recognized as the world’s first antivirus software. This revised and newer version of the Creeper, known as the Reaper, could move throughout a network and delete any Creeper files it found. Although Creeper was never meant to cause harm, it revealed very real problems that could be caused by such programs.
🔹𝟷𝟿𝟽𝟺: 𝚃𝚑𝚎 𝚆𝚊𝚋𝚋𝚒𝚝
After The Creeper came Wabbit in 1974. This was another virus that could rapidly copy itself across a network. The program would duplicate itself so fast that it would eventually bog down the infected system and cause it to crash. The Wabbit was originally named “Rabbit” and was more of a fork bomb than a virus. It was original named the “Rabbit” for the speed at which it copied itself) until it clogged systems, reducing system performance, before finally reaching a maximum exhaustion threshold and crashing the computer.
🔹𝟷𝟿𝟾𝟸: 𝚃𝚑𝚎 𝙵𝚒𝚛𝚜𝚝 𝙼𝚊𝚌 𝚅𝚒𝚛𝚞𝚜
Contrary to what ever non-technical person says, “Macs are not susceptible to viruses,” the first computer virus found in the wild, dubbed “Elk Cloner,” was designed to target Apple II computers. It was written by a then-15-year-old, who wrote such programs to play pranks on his friends. This boot sector virus propagated whenever an infected disk was run. The virus would reside in memory and look for a clean floppy disk to infect. On the fiftieth boot, Elk Cloner would display a poem to the user:

🔹𝟷𝟿𝟾𝟼: 𝚃𝚑𝚎 𝙵𝚒𝚛𝚜𝚝 𝙿𝙲 𝚅𝚒𝚛𝚞𝚜
In 1986, computing was still rudimentary (slow and not internet connected). The very first iterations of the internet were relegated to governments and universities. It would be at least three years before Internet Service Providers (ISPs) started providing public access to the internet, in 1989.
Sure, Bulletin Board Systems (BBS) existed, but they required making a phone call to a direct point of presence (POP) hosted by the BBS operator. Connections to the BBS were usually limited to the local audience of the BBS because phone calls to the BBS from outside the area code were billed by the minute, making them quite expensive.
However, 1986 also saw the launch of the first PC virus, dubbed “Brain.” Brain is considered the first IBM PC compatible virus and tt changed the information security world as we know it today. It originated in Pakistan but quickly spread worldwide to Europe and North America. Ironically, the virus had replicated from machine to machine because of anti-piracy countermeasures.
The Brain virus was developed by Amjad Farooq Alvi and Basit Farooq Alvi, two brothers from Pakistan who created a boot sector virus that loaded a warning to individuals using a pirated copy of their medical software. Of course, because there wasn’t any internet, it spread through human interaction via the copying of floppy disks. Unbeknownst to the user, the master boot record (MBR) of the victim’s machine was infected while making an illegal copy of the software and spread when the disk was inserted into the next machine. Because there was no way to know that an infected MBR virus was coming along for the ride, it spread until it became a global phenomenon.
Luckily for many, it wasn’t a destructive virus. It hid a particular sector so the machine wouldn’t boot and displayed a notification that included contact information of the Farooq Alvi brothers for remediation. They claim that they wanted affected individuals to call them to discuss how to obtain their software legally. Within the notification, it stated:

Their ingenious plan proved to be so successful that the brothers were swamped with phone calls from all over the world.
🔹𝟷𝟿𝟾𝟽: 𝙲𝚑𝚛𝚒𝚜𝚝𝚖𝚊𝚜 𝚃𝚛𝚎𝚎 𝙴𝚇𝙴𝙲
December 1987, the Christmas Tree EXEC virus made its way into the headlines. Christmas Tree EXEC was the first widely disruptive replicating network virus, which paralyzed several international computer networks. it was written in Rexx on the VM/CMS operating system and originated in what was then West Germany. It made another public appearance in 1990.
🔹𝟷𝟿𝟾𝟾: 𝙳𝚒𝚐𝚒𝚝𝚊𝚕 𝚂𝚃𝙳𝚜 𝚆𝚎𝚛𝚎 𝙱𝚘𝚛𝚗: 𝚃𝚑𝚎 𝙼𝚘𝚛𝚛𝚒𝚜 𝚆𝚘𝚛𝚖
The difference between a virus and a worm is that a worm doesn’t need human interaction to propagate. Over 30 years ago, the worlds first digital STD, the Morris worm was born. It was called the Morris worm after its author, Robert Morris. This worm was not malicious. It was created as a Proof of Concept to see if hands-off replication was possible.
The worm contained several firsts. It exploited vulnerabilities in various programs and services and checked to see if an existing infection was present, all behaviors of modern malware. And because Morris was worried that system administrators would quarantine the worm and ignore the infection, he programmed it for persistence; however, there was no way to stop the self-replication process, so it caused high loads on devices, rendering them inoperable, and caused a denial-of-service (DoS) in network as it spread from machine to machine.
Mr. Morris was the first convicted under the Computer Fraud and Abuse Act; however, he later because a successful entrepreneur and was awarded tenure at the Massachusetts Institute of Technology (MIT).
🔹𝟷𝟿𝟾𝟿: 𝚆𝚘𝚛𝚕𝚍’𝚜 𝙵𝚒𝚛𝚜𝚝 𝚁𝚊𝚗𝚜𝚘𝚖𝚠𝚊𝚛𝚎
In 1989, the CyberAIDS virus debuted, making it the world’s first observed ransomware. Coincidentally, internet access was also first publicly available in 1989 for the first time through an ISP called TheWorld, out of the United States; however, ransomware did not take advantage of internet connectivity to infect and target victims until 2005.
In 1989, the human AIDS virus was highly topical and relevant worldwide, similar to today’s COVID-19-related news. The CyberAIDS virus was sent via mail (yes, physical mail, not email) to AIDS researchers worldwide via 20,000 infected floppy disks. Once the disk was run, it contained a questionnaire about AIDS. But on the ninetieth reboot, it changed file names to encrypted strings and hid them from the user. The screen then displayed a demand for $189 for a yearly lease of $385 for a lifetime license, sent to a PO Box in Panama. Only bankers’ drafts, cashiers’ checks, or money orders were accepted.
The CyberAIDS virus was attributed to the late Dr. Joseph Popp, who claimed that he created the ransomware to donate the funds he collected to AIDS research; however, other reports state that he was upset with the World Health Organization after being rejected by them for a job. On an interesting note, Dr. Popp did not send any of his floppy disks to researchers in the U.S.
Forensic analysis of the malware revealed that the encryption key of the malware was “Dr. Joseph Lewis Andrew Popp Jr.” Dr. Popp was arrested and charged in the U.K., but during criminal proceedings, he was declared mentally unfit and deported back to the United States.
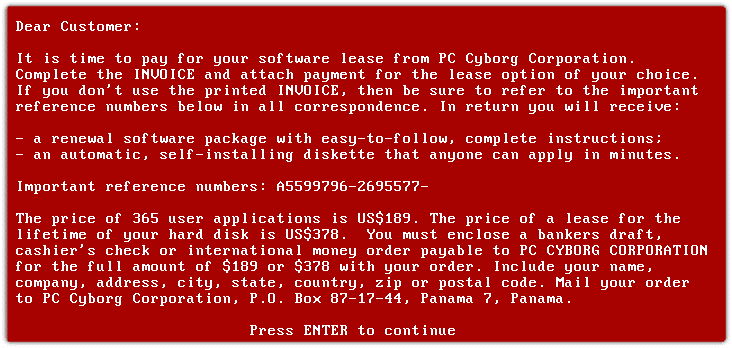
The AIDS Ransomware note
🔹𝟷𝟿𝟾𝟿: 𝙵𝚎𝚜𝚝𝚎𝚛𝚒𝚗𝚐 𝙷𝚊𝚝𝚎 𝙰𝚙𝚙𝚕𝚎 𝙿𝚛𝚘𝙳𝙾𝚂
The Festering Hate Apple ProDOS virus spread from underground pirate BBS systems and started to infect mainstream networks.
Festering Hate was the last iteration of the CyberAIDS series extending back to 1985 and 1986. Unlike the few Apple viruses that had come before which were essentially annoying, did no damage. But the Festering hate series of viruses were extremely destructive, spreading to all system files it could find on the host target computer (hard drive, floppy, and system memory) and then destroying everything when it could no longer find any uninfected files.
🔹𝟷𝟿𝟿𝟸: 𝙼𝚒𝚌𝚑𝚎𝚕𝚊𝚗𝚐𝚎𝚕𝚘
Michelangelo was the next high-profile virus to make a significant impact. Michelangelo was a boot sector virus that targeted DOS partitions. It was written in Assembly, and like its predecessors, it was spread via floppy disks due to its targeting of the master boot record and infection of attached floppy stores, allowing it to spread during the copying and loading process.
It was named Michelangelo because it had been programmed with a time bomb - an instruction to awaken on March 6, Michelangelo’s birthday. What made it infamous was that after it was discovered, there was a lot of media coverage warning users to either leave their computers off on that day or change the date on their machines to a day ahead to avoid being impacted. this was the first time a virus had received so much attention from the mainstream media, in both print and television, helping to spur anti-virus software sales worldwide.
John McAfee had been quoted by the media as saying that five million computers would be affected. He later said that pressed by the interviewer to come up with a number, he had estimated a range from five thousand to five million, but the media naturally just went with the higher number.
🔹𝟷𝟿𝟿𝟺–𝟿𝟻: 𝚃𝚑𝚎 𝚆𝚊𝚛𝚎𝚣 𝚂𝚌𝚎𝚗𝚎 𝚊𝚗𝚍 𝚝𝚑𝚎 𝙵𝚒𝚛𝚜𝚝 𝙿𝚑𝚒𝚜𝚑𝚒𝚗𝚐 𝙰𝚝𝚝𝚊𝚌𝚔𝚜
As internet usage gained traction in the United States through the launch of services such as America Online (AOL), CompuServe, and Prodigy, so did the growth of scams and phishing. For many who grew up in AOL chatrooms (*raises hand), the progz (slang for programs) and warez (slang for software) scene of the mid-90s was revolutionary. I remember the Punterz “progz”, which were a warez for AOL that mad aggressively booted people offline, and, of course, the granddaddy of all AOL hacking programs, AOHell. Because dial-up internet access was quite expensive, being provisioned by the minute (also being distributed with the AOL software burned onto a DVD and included for free with every magazine you purchased), many threat actors were interested in stealing account credentials.
Legacy AOL installation mediaNew programs began being traded on illicit warez chatrooms that contained Punterz (to kick people offline), phishing progz (to steal user accounts), and tools used to generate random credit cards. One of the most famous programs was AOHell, a play on the name of AOL, which contained a random account creator that used randomly created credit card accounts to open an account for free for a month.
It also contained one of the first earliest uses of phishing as we know it today. AOL instant message (AIM) bots sent indiscriminate IMs to targets asking them to verify their account credentials, claiming there was a problem with billing or some similar issue. To continue talking to the bot, the victim would have to “verify their identity” by entering their username and password. This information was then harvested by the users of the AOHell program to use or sell for free account access and spam.

A splash screen of the AOHell program depicting Steve Case in hell
Other nuances seen in AOL warez rooms were programs that promised to do specific things, but that were actually credential harvesters targeting uninformed “n00bs,” or beginner users/newbies.
🔹𝚆𝚎𝚕𝚌𝚘𝚖𝚎 𝚝𝚘 𝚈𝟸𝙺
Wow. We are taking a trip down memory lane! A blast from the past! Do you remember Y2K?
The dawn of the new millennium saw more and more people connected globally. And at the same time, there was a dramatic increase in the volume of attacks due to the increased number of potential victims, driven by the hyper-growth of the internet.
Besides the growth of new high-tech companies (the dotcom bubble), 1999 was a year mired in fear about the “Y2K” bug. While not a virus, per say, Y2K caused mass hysteria and widespread panic because there was a fear that legacy computers would stop operating after December 31, 1999, due to a design flaw in the BIOS, which controls the computer’s motherboard. When rebooted on January 1, 2000, the operating systems date feature within the calendar function would change back to January 1, 1900, since it did not know how to compute any valid years after 1999. This put the thought into people’s minds that Y2K would disrupt everything from gas pumps and elevators to trading floors and power plants. Ultimately, this design flaw proved to be less of a problem than originally thought, and most organizations and individuals escaped unscathed. But the fear of Y2K dominated the news across the world for months.
Everything was fine January 1, 2000.
🔹𝟷𝟿𝟿𝟿/𝟸𝟶𝟶𝟶: 𝚃𝚑𝚎 𝙵𝚒𝚛𝚜𝚝 𝙱𝚘𝚝𝚗𝚎𝚝 𝙰𝚙𝚙𝚎𝚊𝚛𝚜
By 2000, broadband access was starting to gain traction beyond those organizations that could afford access to a T1 line via Digital Subscriber Line (DSL) connections. Home users and organizations were now able to be online 24×7×365. And over the next few years, cybercriminals exploited this ubiquitous access by ushering in the era of botnets and worms.
When botnets first arrived, the term invoked thoughts of Skynet, the fictitious corporate villain from the Terminator movies (and those movies rule by the way). But AI was still the domain of science fiction (and, of course almost 25 years later, we are still only at the beginning stages of AI). But that doesn’t mean that botnets weren’t a problem. Simply put, a botnet is a group of infected and compromised computers that are controlled under the command of a human operator, known as a bot-herder, or bot master. Back then, botnets were simple. I even ran one on my AOL account that would make my account seem active when I was really AFK (Away From Keyboard), so I didn’t get booted from chatrooms. It’s similar to Microsoft’s Teams option to set your status to “appear to be away.” But, botnets infected and spread between machines, with most botnet malware connecting to a predetermined command and control (C2) server on Internet Relay Chat (IRC - think of old AOL chatrooms to receive instructions, as I just mentioned).
The first observed botnet was the EarthLink Spam botnet, which made its debut in 2000. It had one simple task: to send out massive quantities of spam. The EarthLink Botnet accounted for 25% of all email spam at that time, about 1.25 billion messages in total. Because of this brazen campaign, it landed an unprecedented judgment against its operator Khan C. Smith for USD$25 million.
However, the GTbot was introduced in 1999, making it the actual first botnet. In terms of malware, it was very rudimentary. It essentially spread itself to other machines and received commands via IRC. These commands were issued by GTbot controllers, who used this network of affected devices (known as zombies) to launch their distributed denial of service (DDoS) attacks.
🔹𝚃𝚑𝚎 𝚁𝚒𝚜𝚎 𝚘𝚏 𝚝𝚑𝚎 𝚆𝚘𝚛𝚖
Worms are still very much current today and are a part of a threat actor’s arsenal, through not as commonplace today. As explained earlier, worms are different from viruses as they do not need human interaction to spread. And because a worm propagates on it sown, it can spread widely in a short amount of time. Regardless of its intention, being infected by a worm during this time period was usually quite noticeable because it often led to a denial of service (typically due to a flaw). Because they consume ever-increasing operating system cycles, they eventually force an infected machine to come to a grinding halt. The resulting DoS attack can cascade across an organization as the worm spreads, disrupting an entire organization, whether that was its intention or not.
🔹𝟸𝟶𝟶𝟶: 𝙸 𝙻𝙾𝚅𝙴 𝚈𝙾𝚄 𝟸𝟶𝟶𝟶 𝙱𝚕𝚊𝚜𝚝𝚎𝚛 𝚂𝚊𝚜𝚜𝚎𝚛
The I LOVE YOU worm opened the millennium with significant media coverage because it spread around the world at record speed. The I LOVE YOU worm was created by a Onel De Guzman, a college student in the Philippines.
The I LOVE YOU worm propagated using multiple mechanisms. First, it was sent to users via email as a malicious attachment, “LOVE-LETTER-FORr-YOU.vbs.txt.” When opened by the victim, the work would look for the victims’ Microsoft Outlook address book and send out emails impersonating the victim and replicating itself as an attachment. This novel approach caused millions of computers to be infected in days as many people trusted the emails coming from trusted associates, including friends, family, and colleagues. This method of scraping a target’s address book and impersonating them in email is still used as part of a threat actors’ tradecraft (think EMOTET).
🔹𝟸𝟶𝟶𝟶: 𝚃𝚑𝚎 𝙿𝚒𝚔𝚊𝚌𝚑𝚞 𝚅𝚒𝚛𝚞𝚜
The Pikachu virus is believed to be the first computer virus geared at children. It contained the character “Pikachu” from the Pokémon series. The operating systems affected by this virus were Windows 95, Windows 98 and Windows ME.
🔹𝟸𝟶𝟶𝟷: 𝚃𝚑𝚎 𝙰𝚗𝚗𝚊 𝙺𝚘𝚞𝚛𝚗𝚒𝚔𝚘𝚟𝚊 𝚅𝚒𝚛𝚞𝚜
Anyone remember this one?
The Anna Kournikova virus hit email servers hard by sending emails to contacts in the Microsoft Outlook address book. Its creator, Jan de Wit was only sentenced to 150 hours of community service.
🔹𝟸𝟶𝟶𝟹: 𝙱𝚕𝚊𝚜𝚝𝚎𝚛 (𝙼𝚂𝙱𝚕𝚊𝚜𝚝, 𝚕𝚘𝚟𝚎𝚜𝚊𝚗)
By August 2003, Blaster (also known as MSBlast and lovesan) was launched. Home users and workers at large organizations were shocked when their machines suddenly experienced the dreaded “Blue Screen of Death” (BSOD) and rebooted. What they didn’t know was that they had been disrupted by the Blaster worm.
Blaster targeted a remote procedure call (RPC) vulnerability in Microsoft Windows XP (ugh, still my favorite OS) and 2003 operating systems to propagate worldwide. The worm’s goal was to perform a SYN flood attack against windowsupdate.com to prevent machines from accessing updates. Luckily for Microsoft, the author made the mistake of directing Blaster to the wrong domain. The windowsupdate.com domain was nonessential as machines instead used windowsupdate.microsoft.com to receive their updates. Doh!
However, due to a bug in the worm, it also caused a denial of service (BSOD) due to buffer overflow. Continued reboots did nothing to hamper the effort, as it just started over and over, fueling rage in users, shutting machines off over and over. As a result of the wide adoption of internet connectivity, this became the first global denial of service attack. The intentions of the authors were revealed in an ominous message found within the malware’s binary:
The worm resulted from the reverse engineering of a Microsoft Patch Tuesday patch (colloquially known as Exploit Wednesday). Blaster did not affect organizations that had applied the (MS03–026) patches before August 11th. This example stresses the importance of organizations patching systems as quickly as possible once an update is released (and possibly after testing). Unfortunately, to this day - 19 years later - many organizations still ignore this advice.
🔹𝙷𝚘𝚗𝚘𝚛𝚊𝚋𝚕𝚎 𝙼𝚎𝚗𝚝𝚒𝚘𝚗𝚜
🔹𝙲𝚘𝚍𝚎 𝚁𝚎𝚍 (𝟸𝟶𝟶𝟷)
This hybrid worm looked for vulnerable web servers running Microsoft IIS. Once it found a vulnerable server, it displayed the following message:
HELLO! Welcome to http://www.worm.com! Hacked By Chinese!
It also launched DDoS attacks against predetermined sites.
🔹𝚂𝚀𝙻 𝚂𝚕𝚊𝚖𝚖𝚎𝚛 (𝟸𝟶𝟶𝟹)
The SQL Slammer Worm was developed in 2003, and this vicious attack affected over 75,000 computers in less than 10 minutes. The effects from this was slower internet usage worldwide.
🔹𝚃𝚑𝚎 𝙲𝚊𝚋𝚒𝚛 𝚅𝚒𝚛𝚞𝚜 (𝟸𝟶𝟶𝟺)
The Cabir Virus in 2004 was the first to attack mobile phones, while the Koobface Virus the following year, in 2005, targeted social media platforms such as Facebook and Twitter.
🔹𝙼𝚢𝙳𝚘𝚘𝚖 (𝟸𝟶𝟶𝟺)
This was the fastest spreading email worm, surpassing I LOVE YOU. MyDoom still holds the record for this feat.
🔹𝙲𝚘𝚗𝚏𝚒𝚌𝚔𝚎𝚛 (2008)
The Conficker Worm also caused widespread damage in 2008. Not only was the spread and rate increasing with each new development in malware, but also new platforms and devices were also being targeted.
🔹𝚃𝚑𝚎 𝙳𝚊𝚠𝚗 𝚘𝚏 𝙲𝚢𝚋𝚎𝚛𝚌𝚛𝚒𝚖𝚎
🔹𝟸𝟶𝟶𝟻: 𝙼𝚢𝚝𝚘𝚋/𝚉𝚘𝚝𝚘𝚋, 𝙲𝚘𝚖𝚋𝚒𝚗𝚒𝚗𝚐 𝚆𝚘𝚛𝚖𝚜/𝙱𝚊𝚌𝚔𝚍𝚘𝚘𝚛𝚜/𝙱𝚘𝚝𝚗𝚎𝚝
Before Mytob, the world of malware was mainly limited to enthusiasts who created malware out of a desire to create mischief or sheer curiosity; however, the Mytob/Zotob variants changed everything.
Mytob essentially combined the functionality of a worm/backdoor/botnet. It is a variant of MyDoom and was created by the same coder that created the Zotob worm. Mytob infected victim machines in two ways: it either arrived via email through malicious attachments or exploited vulnerabilities in the LSASS (MS04–001) protocol or RCP-DCOM (MS04–012) and used remote code execution. It also utilized the victim’s address book to propagate itself and searched for other machines via network scans to see if they could be compromised.
Mytob was one of the first viruses to specifically block or work against antivirus software by preventing connectivity from the victims’ machine to various update sites. This was done by redirecting all known vendor URIs to 127.0.0.1, a localhost IP. This caused all queries to public-facing websites to resolve to the machine itself, essentially going nowhere.
Mytob was very prolific for its time and was consistently listed at the top of Top 10 charts. It had so many variants within different functionalities that antivirus companies often had the entire alphabet appended to the malware name.
The Zotob variant took remnants of the Mytob source and incorporated MS05–039, which was a buffer overflow vulnerability in Microsoft Plug and Play for Windows 2000. Zotob used this variant to scan for machines vulnerable to MS05–039 to further propagate. Mytob/Zotob variants were incredibly disruptive, taking down the operations of 100 organizations, including the NY Times. It was so disruptive that even CNN News anchor Wolf Blitzer announced that Lou Dobbs could not get on the air for his regularly scheduled programming.
𝚃𝚑𝚎 𝚎𝚛𝚊 𝚘𝚏 𝚜𝚙𝚢𝚠𝚊𝚛𝚎 𝚊𝚗𝚍 𝚑𝚒𝚓𝚊𝚌𝚔𝚎𝚍 𝚜𝚎𝚊𝚛𝚌𝚑 𝚛𝚎𝚜𝚞𝚕𝚝𝚜
🔹𝟸𝟶𝟶𝟻: 𝙲𝚘𝚘𝚕𝚆𝚎𝚋𝚂𝚎𝚊𝚛𝚌𝚑 𝚊𝚗𝚍 𝙱𝚊𝚢𝚁𝚘𝚋
CoolWebSearch, commonly known as “CWS,” was the first cybercrime operation to hijack search results from Google, overlaying search results with those from the threat actor themselves. This was done to steal clicks from Google. CWS was most often distributed using drive-by downloads or adware programs. It was so pervasive and hard to remove that volunteers developed programs and managed web forums to help remove CWS infections for free. CWS Shredder was one of several programs widely used by victims of CoolWebSearch to help remediate their machines.
A similar attack appeared several years later, in 2007. It used a variation of hijacking search results from eBay. It was discovered when a woman in Ohio purchased a car for several thousand dollars, and the vehicle never arrived. Authorities later determined that this car had never been listed for sale and that her machine had malware that injected fake listings on her device via the BayRob malware. In a great example of cat and mouse, the FBI and Symantec waited patiently for years for the cybercriminals to make a mistake, which culminated in their arrests in 2016.
[upl-image-preview url=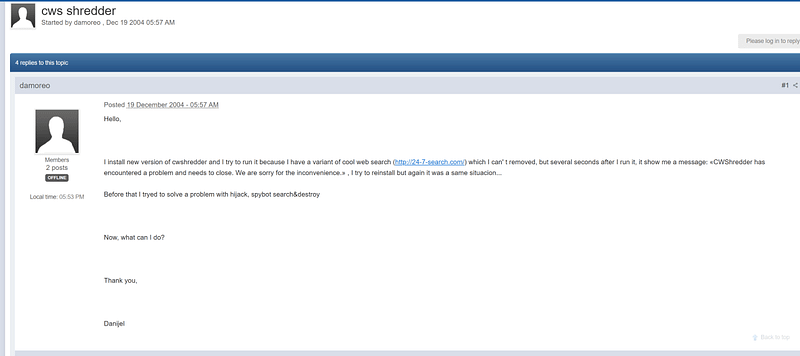
Screenshot of a user asking for assistance around CWS (forums.bleepingcomputer.com)
𝙵𝚛𝚘𝚖 𝚜𝚙𝚢𝚠𝚊𝚛𝚎 𝚝𝚘 𝚜𝚙𝚢 𝚟𝚜. 𝚜𝚙𝚢 𝚊𝚗𝚍 𝚝𝚑𝚎 𝚍𝚒𝚜𝚌𝚘𝚟𝚎𝚛𝚢 𝚘𝚏 𝚗𝚊𝚝𝚒𝚘𝚗-𝚜𝚝𝚊𝚝𝚎 𝚌𝚢𝚋𝚎𝚛 𝚠𝚎𝚊𝚙𝚘𝚗𝚜
🔹𝟸𝟶𝟷𝟶: 𝚂𝚝𝚞𝚡𝚗𝚎𝚝
Ushering in the 2010s was the first discovery of nation-state malware being used to target Industrial Control Services (ICS) devices - specifically, supervisory control and data acquisition devices (SCADA). Stuxnet proved to be the first specific nation-state malware targeting critical infrastructure - in this case, industrial centrifuges (specifically nuclear), causing them to overspin and cause a meltdown. Stuxnet specifically targeted organizations in Iran but soon spread to other SCADA systems around the world. Analysis of the Stuxnet malware highlighted that it wasn’t specific to Iran and could be tailored to any organization running similar ICS devices. In 2012, a NY Times article confirmed that the United States and Israel developed Stuxnet.
🔹𝟸𝟶𝟷𝟷: 𝚁𝚎𝚐𝚒𝚗
Regin is a highly modular Remote Access Trojan (RAT). This allowed it to be highly flexible, adapting to a targeted environment. Regin was also successful because it was very innocuous in its operation. Files that were exfiltrated were often kept in an encrypted container. But instead of being stored in multiple files, everything was held in a single file, thereby avoiding arousing the suspicions of system administrators or AV software. According to Der Spiegel, Regin was a creation of the United States NSA and designed to spy on the EU and its citizens. This information was disclosed through the infamous classified information leak provided by Edward Snowden.
🔹𝟸𝟶𝟷𝟸: 𝙵𝚕𝚊𝚖𝚎
Flame was considered the most advanced malware ever found at the time of discovery. It had everything - a wormlike capability to spread via LAN networks, it could record and capture screenshots and audio, it could eavesdrop on and record Skype conversations, and it could turn Bluetooth workstations into listening beacons that could then exfiltrate and move files to other beacons, ultimately sending files to a predetermined C2 server. Flame primarily targeted organizations in the Middle East.
𝚃𝚑𝚎 𝚄𝚜𝚑𝚎𝚛𝚒𝚗𝚐 𝚘𝚏 𝚝𝚑𝚎 𝙼𝚘𝚍𝚎𝚛𝚗 𝙴𝚛𝚊 𝚘𝚏 𝚁𝚊𝚗𝚜𝚘𝚖𝚠𝚊𝚛𝚎
🔹𝟸𝟶𝟷𝟷/𝟷𝟸: 𝚁𝚎𝚟𝚎𝚝𝚘𝚗
Reveton was not the first “ransomware” of the Internet-connected age. That distinction belongs to GPCODe (2005) and others; however, Reveton was the archetype of modern ransomware, helping establish the look and feel that still exists to this day, including the ubiquitous lock screen that provides details of what happened, how to get in touch with the bad actor, how to pay the ransom, and how to decrypt files, etc.
Reveton also generated a lot of press because it had all the hallmarks of being run by a professional cybercriminal organization. It was not only professional in appearance, but also utilized templates, which was another first. Lock screens would be displayed to the user based on geolocation and present the victim with a lock screen of a local law enforcement organization along with instructions on how to make payment. Reveton used so many templates that researchers often cited releases based on its fall/winter/spring/summer templates.
Reveton Ransom Screen with MoneyPak instructionsVariation with an image of former President Obama🔹𝟸𝟶𝟷𝟹: 𝙲𝚛𝚢𝚙𝚝𝚘𝙻𝚘𝚌𝚔𝚎𝚛 - 𝚃𝚑𝚎
𝙰𝚛𝚛𝚒𝚟𝚊𝚕 𝚘𝚏 𝙲𝚛𝚢𝚙𝚝𝚘𝚌𝚞𝚛𝚛𝚎𝚗𝚌𝚢 𝚊𝚜 𝚊 𝙿𝚊𝚢𝚖𝚎𝚗𝚝 𝙾𝚙𝚝𝚒𝚘𝚗
CryptoLocker was the first ransomware to demand payment via Bitcoin. The price for decryption was two BTC, which in 2013 (depending on the timeframe) was somewhere between $13 and $1,100, which netted the threat actors a modest sum.
CryptoLocker bitcoin ransom demandRemember, this was when cryptocurrency was still in its infancy, and getting non-technical victims to not only pay but understand how to even use cryptocurrency was a hurdle to overcome.
🔹𝟸𝟶𝟷𝟹: 𝙳𝚊𝚛𝚔𝚂𝚎𝚘𝚞𝚕 𝚊𝚗𝚍 𝙻𝚊𝚣𝚊𝚛𝚞𝚜
Besides ransomware, 2013 also ushered in the era of sinister state-sponsored attacks. DarkSeoul, as one attack was called, targeted the Korean broadcaster SBS and banking institutions in South Korea on March 20, 2013. The malware used in this attack, Jokra, targeted a device’s master boot record (MBR) and overwrote them. Many users of internet service providers, telecoms, and ATMs were also affected as their networks were taken offline. This attack was attributed to Lazarus (North Korea), which also targeted Sony Corporation in 2014 by leaking confidential information in response to “The Interview,” a film that mocked North Korean leader Kim Jong Un. The Lazarus team was also associated with attacks against the Bank of Bangladesh in 2016. They attempted to steal $951 million but only managed to get away with $81 million due to various flags in the banking transaction chain.
🔹𝟸𝟶𝟷𝟻: 𝙱𝚛𝚘𝚠𝚜𝚎𝚛 𝙻𝚘𝚌𝚔𝚎𝚛 𝚊𝚗𝚍 𝙵𝚊𝚔𝚎 𝚃𝚎𝚌𝚑𝚗𝚒𝚌𝚊𝚕 𝚂𝚞𝚙𝚙𝚘𝚛𝚝 𝚂𝚌𝚊𝚖𝚜 (𝙱𝚂𝙾𝙳)
Although technically not malware, the first technical support scams and various browser locker variants first appeared in 2015. These nuisance attacks essentially mimic ransomware by causing victims to either panic and call a support number to a threat actor acting as technical support in a different country or by simply paying cryptocurrency to “clean” their system. The scheme deployed malicious JavaScript on legitimate websites that had been compromised. This JavaScript would then render a browser inoperable, frequently displaying warnings and demands in full-screen mode (payment to unlock, selling fake remediation software or technical services, etc.).
Other variations of this strategy were Blue Screen of Death (BSOD) displays, which looked convincing to the victim, including a toll-free number claiming to be Microsoft technical support, but in fact, it was a threat actor in a call center in a foreign country. The threat actor would then attempt to convince the victim to provide remote access to their device for “remediation,” after which they would take control of the victim’s machine to perform further malicious acts while charging exorbitant fees for nonexistent services.
🔹𝟸𝟶𝟷𝟼: 𝚃𝚑𝚎 𝙵𝚒𝚛𝚜𝚝 𝙸𝚘𝚃 𝙱𝚘𝚝𝚗𝚎𝚝 𝙰𝚛𝚛𝚒𝚟𝚎𝚜
The arrival of Mirai surprised many. It was the first botnet to target IoT devices. While it primarily targeted network routers, it included other IoT devices. Mirai was mainly a DDoS botnet. and was involved in notable attacks against Brian Krebs’s website, as well as being responsible for taking down a massive segment of the internet, disrupting access and services worldwide.
Unlike traditional network and end-user devices, most IoT devices are not maintained. That is, they don’t receive updates on an automated basis, as a computer or smartphone does. Instead, they are often neglected and hardly are ever updated, usually because updates require that they be flashed (meaning taken offline so the software and firmware can be overwritten entirely), which can be inconvenient or even disastrous because flashed devices can be bricked (meaning permanently rendered inoperable) if done wrong. To make matters worse, many people who connect IoT devices to the internet directly do not change their default username and password. Mirai exploited this vulnerability, allowing it to propagate without any difficulty. Mirai was so prolific at one point that even famed cryptologist Bruce Schneier thought it may have been the creation of a nation-state.
Mirai was not only a high-profile attack because it was novel but also because it was able to amass a global botnet army in such a short amount of time, allowing it to redirect internet traffic to targeted sites from infected systems around the world. This made it especially hard to defend against, as the flood of traffic came from everywhere. In fact, variants of Mirai are still alive and kicking, as noted in a recent FortiGuard Labs blog, partly because the developers eventually released its code online for other criminals to use.
🔹𝟸𝟶𝟷𝟽: 𝚂𝚑𝚊𝚍𝚘𝚠𝙱𝚛𝚘𝚔𝚎𝚛𝚜 (𝙽𝚂𝙰), 𝚆𝚊𝚗𝚗𝚊𝙲𝚛𝚢, 𝙿𝚎𝚝𝚢𝚊/𝙽𝚘𝚝𝙿𝚎𝚝𝚢𝚊, 𝚊𝚗𝚍 𝙽𝚘𝚝 𝙳𝚒𝚜𝚌𝚕𝚘𝚜𝚒𝚗𝚐 𝚅𝚞𝚕𝚗𝚎𝚛𝚊𝚋𝚒𝚕𝚒𝚝𝚒𝚎𝚜
The ShadowBrokers leak of the United States National Security Agency (NSA) was unprecedented and devastating - not just because it revealed secret malware being developed at the highest levels of the U.S. government, but also because threat actors effectively repurposed the tools and exploits that were released. These tools, codenamed “Fuzzbunch,” were an exploitation framework developed by the NSA. Part of the framework included malware known as DoublePulsar, a backdoor attack that contained the infamous “EternalBlue” exploit. EternalBlue was a zero-day exploit that the NSA kept in their arsenal that targeted Microsoft’s SMB (Server Message Block) protocol (CVE-2017–0444).
It was later used to spread the infamous WannaCry, Petya/NotPetya ransomware, with disastrous consequences. These ransomware variants were so disruptive that they caused the shutdown of manufacturing facilities worldwide. Attribution for this leak was initially blamed on Russia, but to this day, nobody has been able to attribute the ShadowBrokers hack/leak to an entity.
🔹𝟸𝟶𝟷𝟽: 𝙼𝚒𝚗𝚒𝚗𝚐 𝚏𝚘𝚛 𝙲𝚛𝚢𝚙𝚝𝚘
Even though cryptocurrency-related threats were relegated initially to Ransomware or cryptocurrency wallet thefts, 2018 introduced a method never seen before. XMRig is a miner application written to mine for Monero cryptocurrency and is not malicious. It works by utilizing unused CPU cycles on a machine to help solve various mathematical problems used in cryptocurrency mining. However, cybergangs began surreptitiously installing XMRig on compromised machines and devices and then collecting and aggregating the resulting data for their own crypto profit.
Common vulnerabilities exploited by various criminal attackers utilized known exploits in Apache Struts, Oracle Weblogic, and Jenkins Servers. As a result, these attacks were relegated to organizations that used these technologies and, most important to the attackers, the powerful CPUs of the devices they ran on. These vulnerabilities were also targeted because they were remotely exploitable. Compounding matters, many of these internet-facing machines were also unlikely to be patched, either through carelessness or laziness, allowing threat actors to leverage them for profit.
Variants of campaigns that incorporated XMRig in their attacks also targeted mobile devices via malicious Android APKs, docker containers, and supply chain attacks targeting NPM (node package manager), to list a few.
🔹𝟸𝟶𝟷𝟿: 𝙶𝚊𝚗𝚍𝙲𝚛𝚊𝚋 𝚊𝚗𝚍 𝚝𝚑𝚎 𝙴𝚖𝚎𝚛𝚐𝚎𝚗𝚌𝚎 𝚘𝚏 𝚁𝚊𝚗𝚜𝚘𝚖𝚠𝚊𝚛𝚎 𝚊𝚜 𝚊 𝚂𝚎𝚛𝚟𝚒𝚌𝚎
GandCrab ushered in a new wave that has escalated the volume and virulence of attacks by providing ransomware for the masses - for a fee. GandCrab sought to do two things: distance itself from the actual attacks on organizations and generate more revenue. It perfected the business model known as Ransomware-as-a-Service (RaaS). RaaS gave the GandCrab authors the luxury of working on their code while getting others to perform the actual breaches. In this model, affiliates would do all the dirty work (reconnaissance, lateral movement, delivering the ransomware, collecting the money, etc.) while the authors stayed in the background and took a cut (estimates are that they collected between 25% and 40%) of the actual ransom
This proved to be lucrative for both parties, as the authors didn’t have to take the risk of finding and infecting targets, and affiliates didn’t have to spend time trying to develop the ransomware themselves. GandCrab also appears to have followed the Agile development process, with minor and major releases deployed whenever the authors would see fit. GandCrab later announced their retirement in June of 2019, after claiming to have netted $2 billion, most likely because they were feeling the heat of the authorities.; however, the GandCrab authors would later be loosely affiliated with the Sodinokibi/REvil threat actors. REvil has also been loosely affiliated to DarkSide which is most notably credited for the infamous summer 2021 attack on Colonial Pipeline. Other notable RaaS variants that have emerged since GandCrab are BlackCat, Blackmatter, Conti, and Lockbit, to name a few.
🔹𝙲𝚘𝚗𝚌𝚕𝚞𝚜𝚒𝚘𝚗
Between 1971 and early 2000, malware was mostly relegated to mischief and attempts by virus authors to see if something they had created would work. Fast forward 20+ years, and we can see that the threat landscape has evolved from mischief to include profitable cybercrime and nation-state attacks. Likewise, the evolution of the initial term “virus” to today’s all-encompassing “malware” reflects the evolution of threats over the past 20 years. It is not coincidental that the development and changes of such attacks have coincided with the development of the hyper-connected world in which we now live.
As we embark on the next 25 years - thinking ahead for the 75th anniversary of threats - we can only assume that threats will continue to target whatever technology or trends that are trending or topical. We can forecast and predict the next 12 months of how threats will target the ever-expanding attack surface, but there will always remain one same constant that will remain clear: the biggest single risk will always be the human element.
I would love to hear anyone else’s experience if you came from, or grew up within this interesting time period as I did, coming from the era of AOL and progz, and Y2K, so please feel free to drop a comment on your experiences and/or memories! What a time it was to be alive!
Evolution of Packers
50 years of malware, can you believe it? While many things have changed, there’s quite a few things that haven’t changed. Before antiviruses went maintstream, malware was too easy, anyone could make it. But as antivirus became more prevalent on personal home computers, it became harder and harder to sneak your malware past the security products. One big change was the evolution of packers. Packers or crypters as they’re commonly called enable anyone, even beginners, to obfuscate their malware, hide their malicious code and bypass antivirus. These packers include UPX, Themida, VMProtect etc… Over the years this technology has become very mature, making malware analysis and detection quite annoying. But if you know what you’re doing, dumping the unpacked and de-obfuscated code isn’t too difficult. If you’d like to learn how, checkout this guide on unpacking VMProtect.