
Hello Guys! I’m 0×2458. I am back with another cool blog to help you increase your bug hunting skills! In this blog, I will talk about Burp Suite and I will share Few BurpSuite Plugins and tools which you can use to maximaize your bug bounty earnings!
NOTE: These plugins not always give you true positives. Sometimes They may generate False Positives So you have to keep a check on that and not report anything BLINDLY!
Without Further ado, Lets start!!
What is BurpSuite?
Burp Suite is a leading set of tools used for web application security testing. It was developed by PortSwigger, a company based in the United Kingdom, and is widely used by security professionals and ethical hackers to identify security vulnerabilities in web applications. Burp Suite consists of several tools that work together to help in the web application security testing process, including a proxy, scanner, spider, repeater, intruder, decoder, comparer, and extender. The tool is highly customizable, with many third-party plugins available to extend its functionality. And in this blog we will talk about some cool plugins!

What are BurpSuite Plugins?
Burp Suite plugins are extensions or add-ons that can be installed in Burp Suite to extend its functionality beyond its default capabilities. These plugins are developed by the Burp Suite community, and they allow users to customize the tool according to their specific testing requirements. Burp Suite plugins can be used for a wide range of tasks, including vulnerability scanning, web application testing, and penetration testing. Some of the popular plugins available for Burp Suite include ActiveScan++, Turbo Intruder, Logger++, and Autorize. By using these plugins, security testers can enhance their testing capabilities, automate repetitive tasks, and discover vulnerabilities that may have been missed otherwise.
Now, you are aware of what BurpSuite is and what are plugins in it. Let’s move to next part!
How to Install Plugins in BurpSuite?
You can install Plugins in BurpSuite by following below steps:
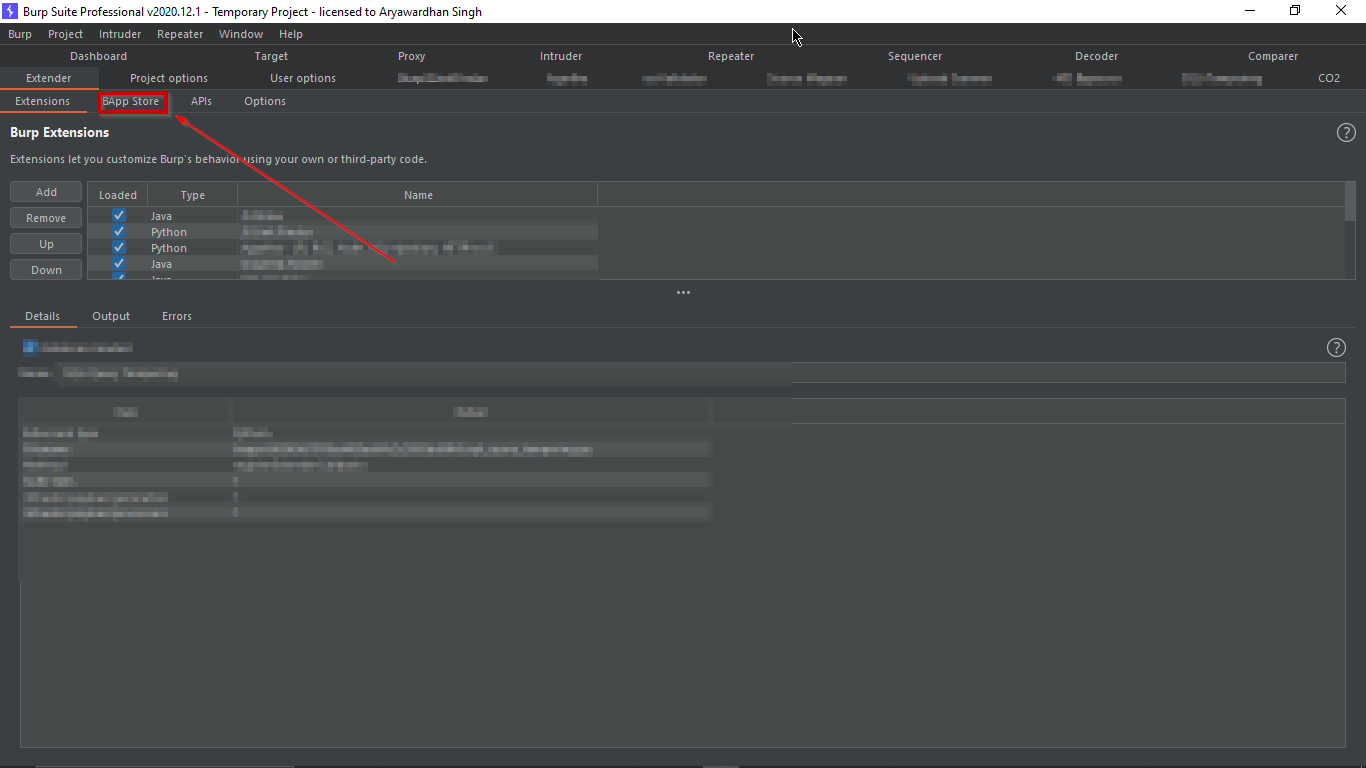
- Open BurpSuite and go to the “Extender” tab.

- Click on the “BApp Store” tab and select the plugin you want to install.
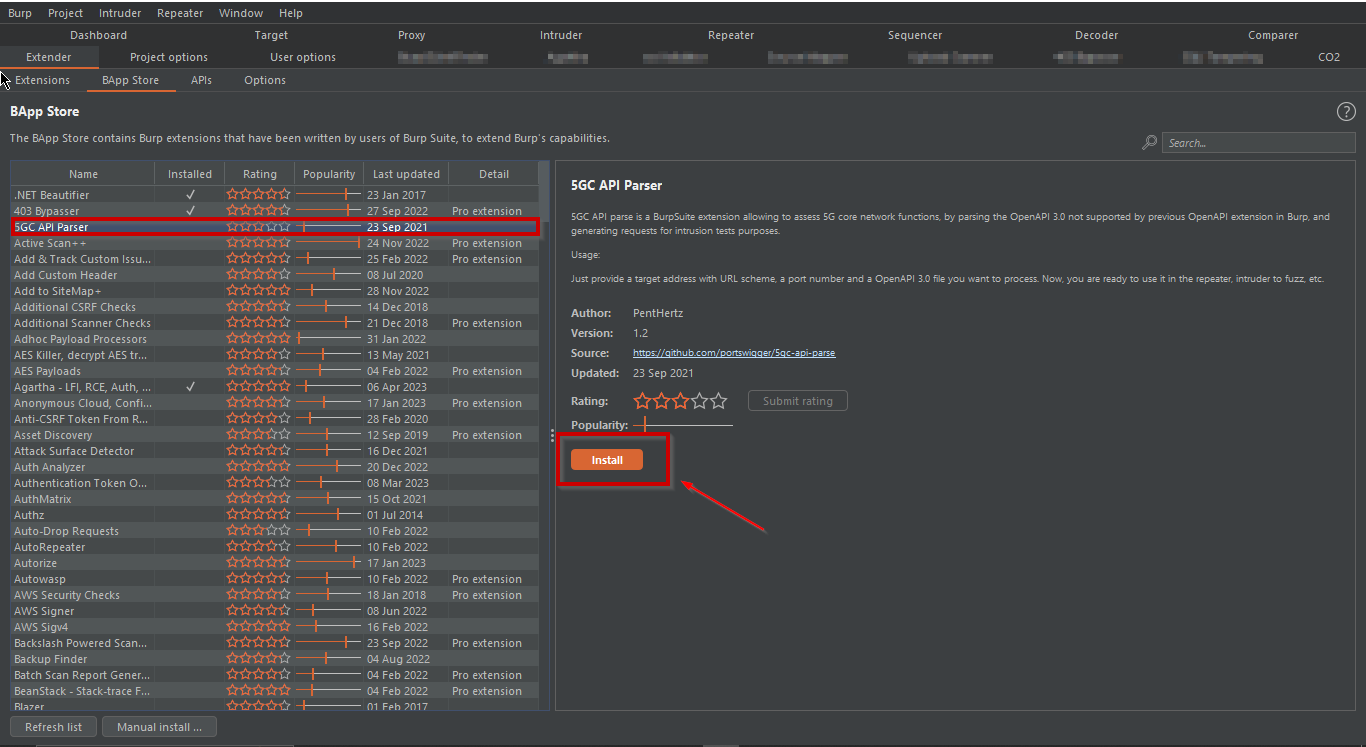
- Click on the “Install” button next to the plugin.
- Once the plugin is installed, you can access it from the “Extender” tab.

How to make the Plugins Active to show results?
To make the installed plugins active, you need to configure two environments:
➤ Java- It will be needed to run java based plugins(not always required)
◦ Go to Download Page of Java’s Official Website.
Download It and install on you windows/linux as preferable.
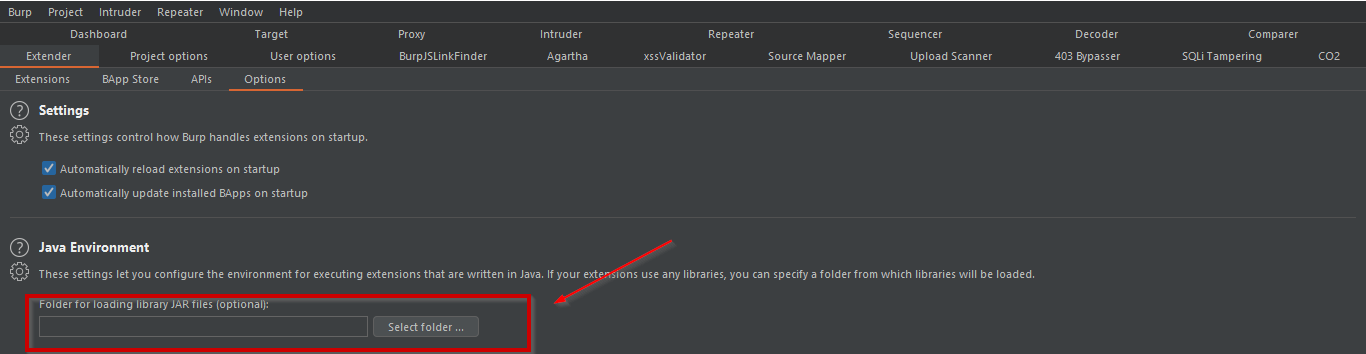
Open Burp > Extender > Options. Here configure your Java file.
➤ Jython- It will be used to run python based plugins. Burp uses jython to run python based plugins. (Always Required)
Go to Download Page of Jython’s Official website
Download Both installer and Standalone file.
Download It and install on you windows/linux as preferable.
Open Burp > Extender > Options. Here configure your Jython file. (Remember you have to use jython standalone file, not installer)

Now you are all set to Use those cool Plugins!!
Plugins
Now we will talk about some plugins which will help you in your Bug Bounties!
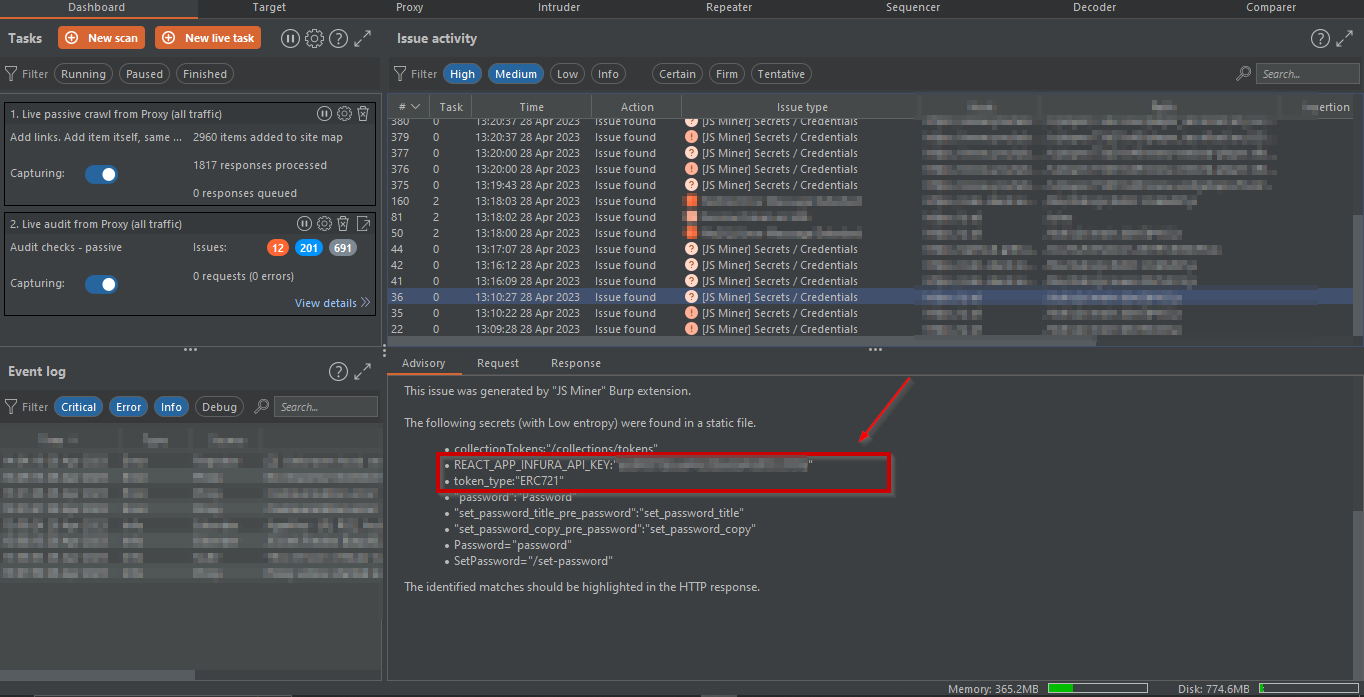
#1. JSMiner:
The JS Miner plugin in BurpSuite is a tool designed to search for interesting content within static files, specifically within JavaScript and JSON files. It helps to identify potential vulnerabilities and sensitive information that may be embedded within the code. This plugin analyzes the source code for common patterns, keywords, and functions that may indicate security risks, such as SQL injections, cross-site scripting (XSS), and information disclosure. By using JS Miner, security researchers can easily identify potential vulnerabilities and take appropriate measures to prevent them.
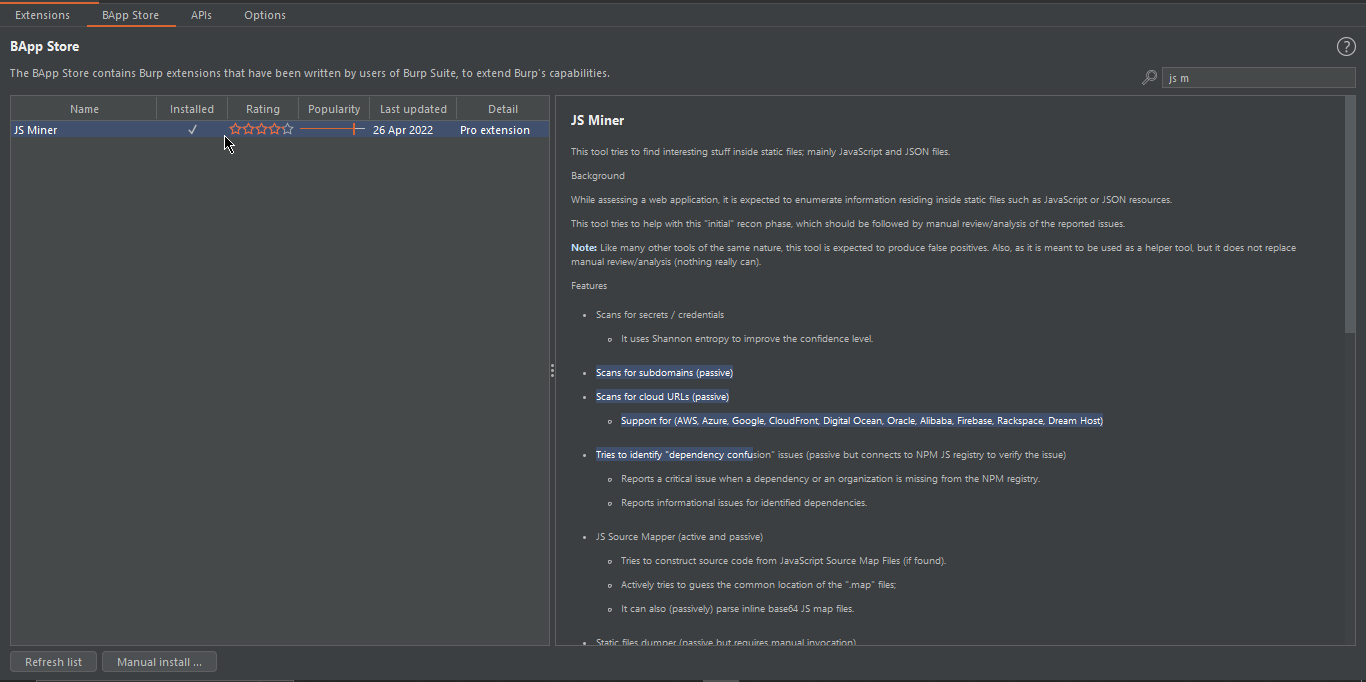
#2. JsLinkFinder:
JSLinkFinder is a plugin in BurpSuite that is used to find links to JavaScript files in web pages. The plugin searches the HTML content of web pages and extracts any links that reference JavaScript files. This can be useful for identifying potentially vulnerable JavaScript files that may contain security flaws or for finding additional web pages to test for vulnerabilities. The plugin can also be configured to search for specific file extensions or to exclude certain URLs from the search. Overall, JSLinkFinder is a useful tool for web application security testing and can save time by automating the process of identifying JavaScript files for analysis.
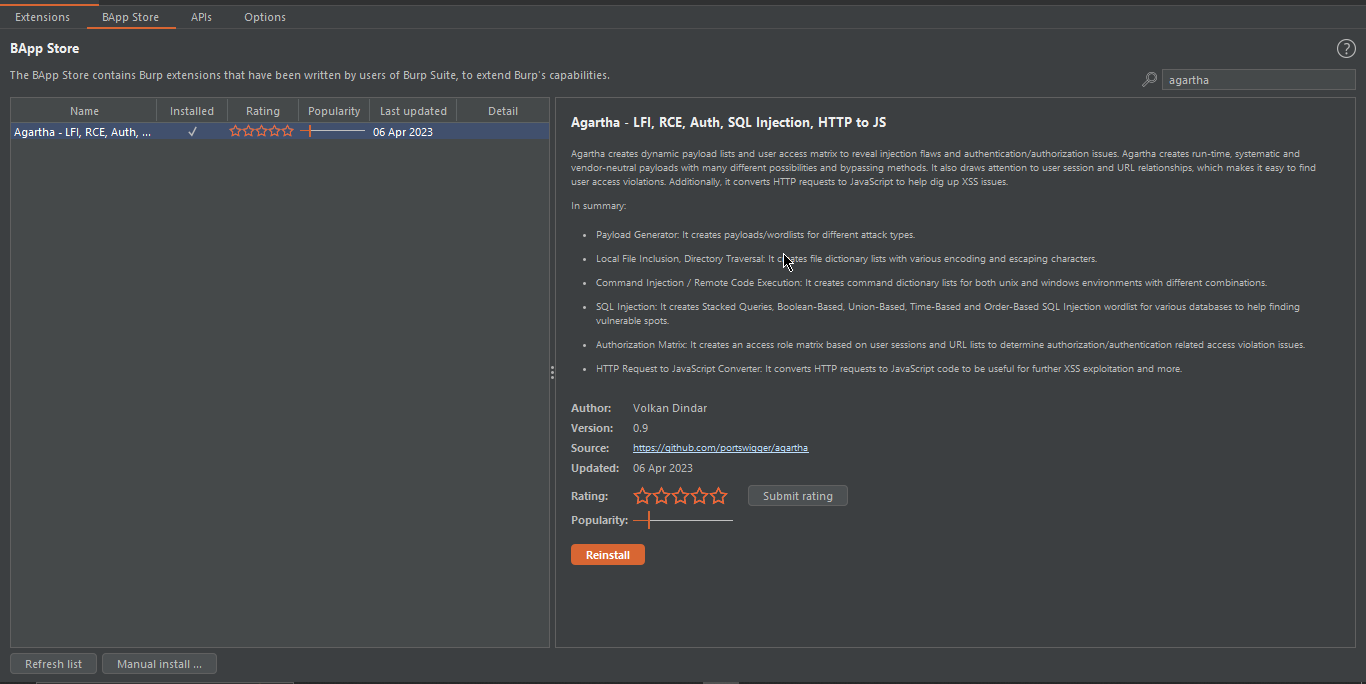
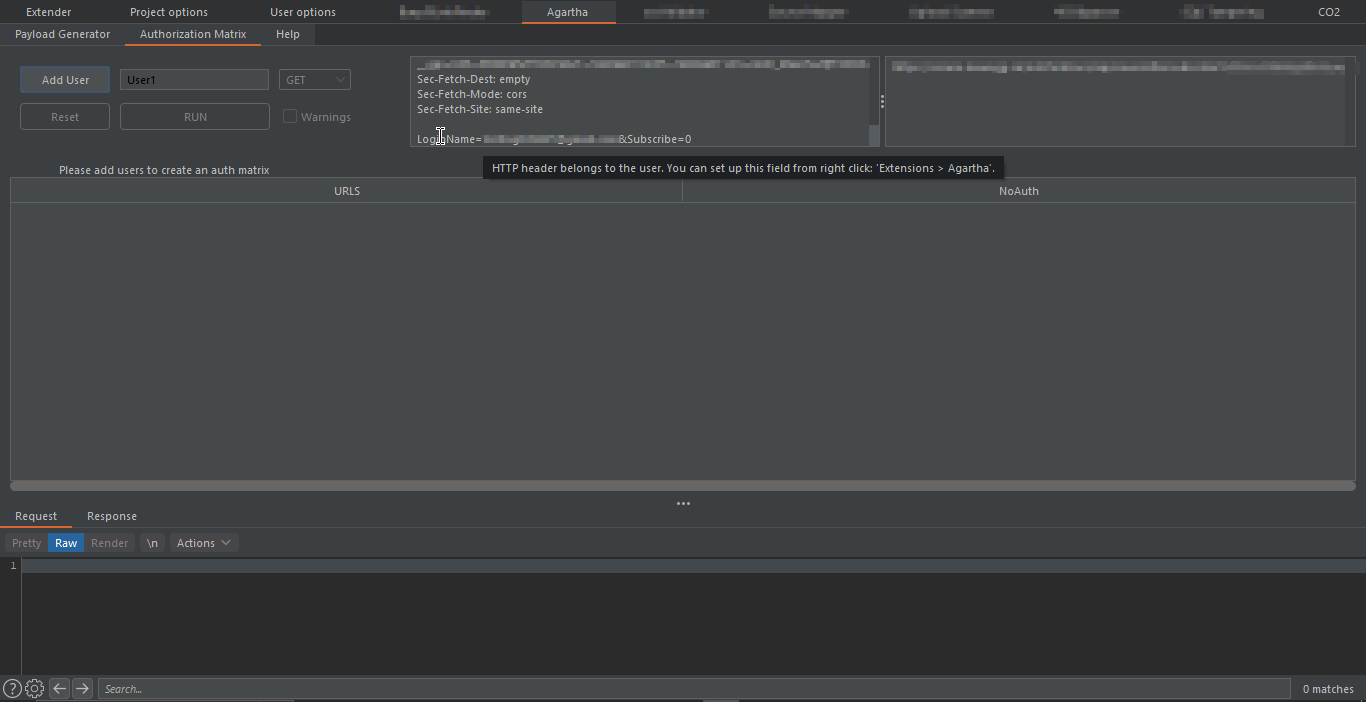
#3. Agartha:
Agartha is a powerful penetration testing tool that can be used to identify a wide range of vulnerabilities, including injection flaws and authentication/authorization issues. One of the key features of Agartha is its ability to create dynamic payload lists and user access matrices, which can be used to systematically test a website for vulnerabilities. Unlike other tools that rely on pre-built payloads, Agartha generates payloads at runtime, making them vendor-neutral and more difficult to detect. Another unique feature of Agartha is its ability to draw attention to user session and URL relationships, which can be used to quickly identify user access violations. This is particularly useful when testing complex web applications that have multiple user roles and access levels. In addition to its payload and access matrix capabilities, Agartha also has a built-in HTTP request to JavaScript converter that can be used to uncover cross-site scripting (XSS) vulnerabilities. By converting HTTP requests to JavaScript, Agartha can simulate how a browser would execute the request and detect any vulnerabilities that may exist. You can end a request to Agartha panel for further exploitation.
#4. GraphQL Raider:
GraphQL Raider is a plugin for BurpSuite that enables testing and manipulation of GraphQL endpoints. GraphQL is a query language for APIs that provides a more efficient, powerful, and flexible alternative to REST APIs. With the growing adoption of GraphQL, it has become increasingly important for security testers to have the ability to assess and identify vulnerabilities in GraphQL APIs. The GraphQL Raider plugin helps security testers to quickly identify and exploit vulnerabilities in GraphQL endpoints by allowing them to interact with GraphQL endpoints and manipulate the queries and responses. The plugin includes features such as a GraphQL query builder, automatic mutation discovery, and an interactive console for querying GraphQL endpoints. Security testers can use GraphQL Raider to test for common vulnerabilities such as SQL injection, blind injection, and authentication bypass. The plugin also provides functionality for fuzzing, mutation testing, and capturing and modifying requests and responses.

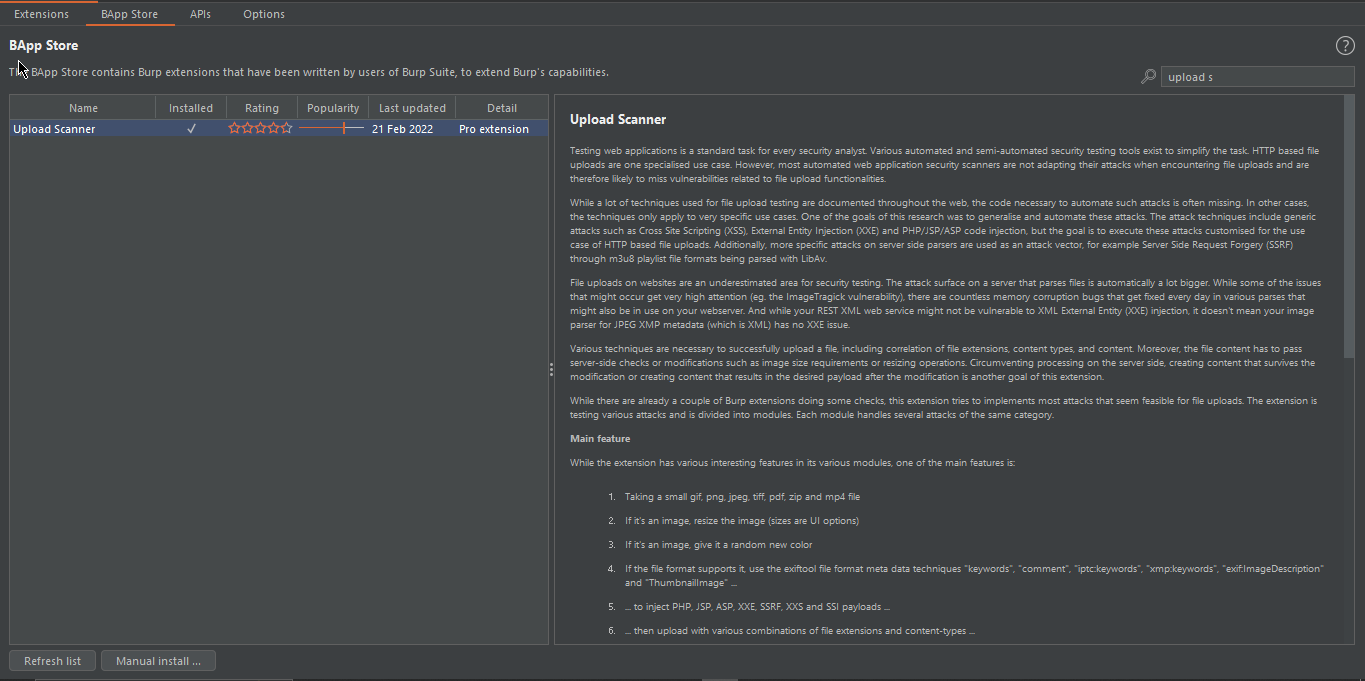
#5. Upload Scanner:
The Upload Scanner plugin in BurpSuite is a tool used to detect file upload vulnerabilities in web applications. It does this by analyzing file upload requests and responses for various types of file upload vulnerabilities, such as unrestricted file uploads or server-side code execution through file upload. The plugin has the ability to detect file upload vulnerabilities in various file types, including image files, PDFs, and even Office documents. It can also detect file upload vulnerabilities that are present in multipart/form-data requests. The Upload Scanner plugin can be a valuable tool in a penetration tester’s arsenal, as file upload vulnerabilities can be a common and critical vulnerability in web applications. By detecting and exploiting these vulnerabilities, an attacker could potentially upload malicious files to the server or execute arbitrary code, leading to a range of serious security issues. You can intercept an upload request and send it to Upload Scanner by Right-Clicking.

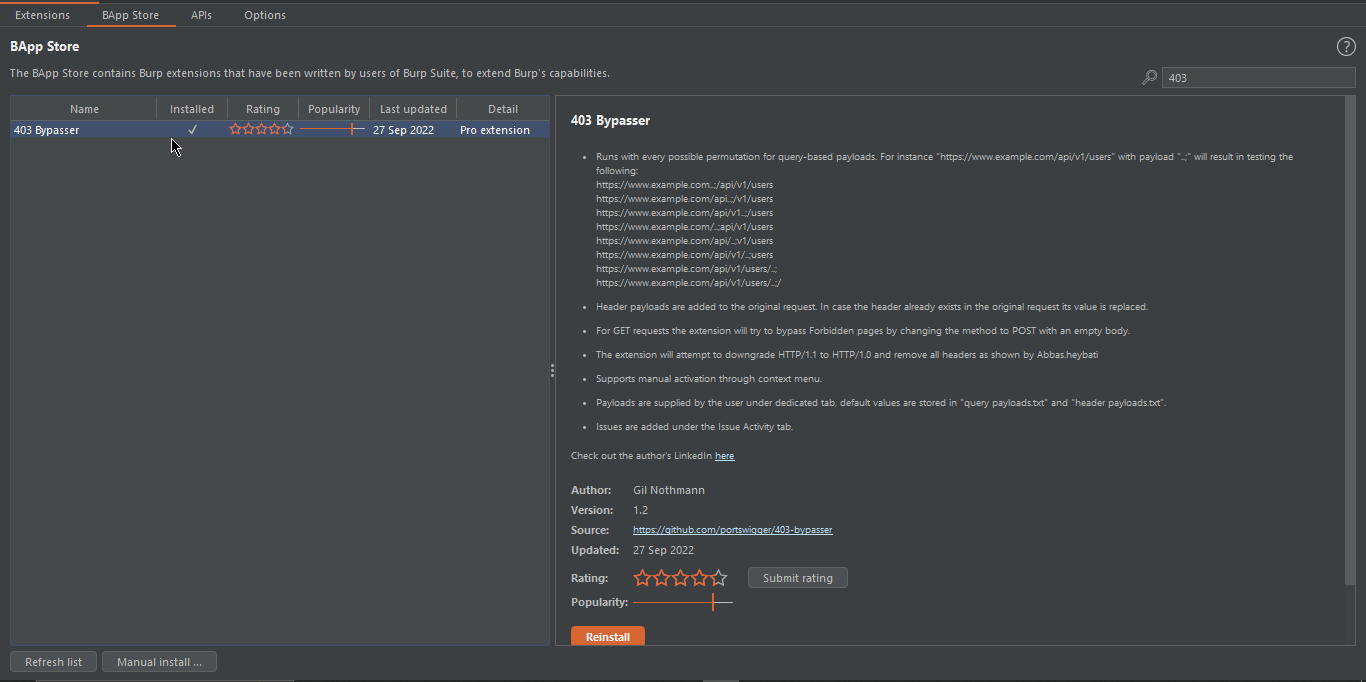
#5. 403 Bypasser:
The 403 Bypass plugin in BurpSuite is used to find vulnerabilities in web applications that may allow unauthorized access to resources that are otherwise forbidden by the server. The HTTP status code 403 indicates that the server understands the request but refuses to authorize it. The 403 Bypass plugin helps identify common techniques that attackers can use to bypass this restriction, such as directory traversal, header manipulation, and parameter manipulation. It can be used to test the security of web applications and ensure that they are properly configured to prevent unauthorized access to sensitive resources. You can intercept a request and send it to 403 Bypasser by Right-Clicking.
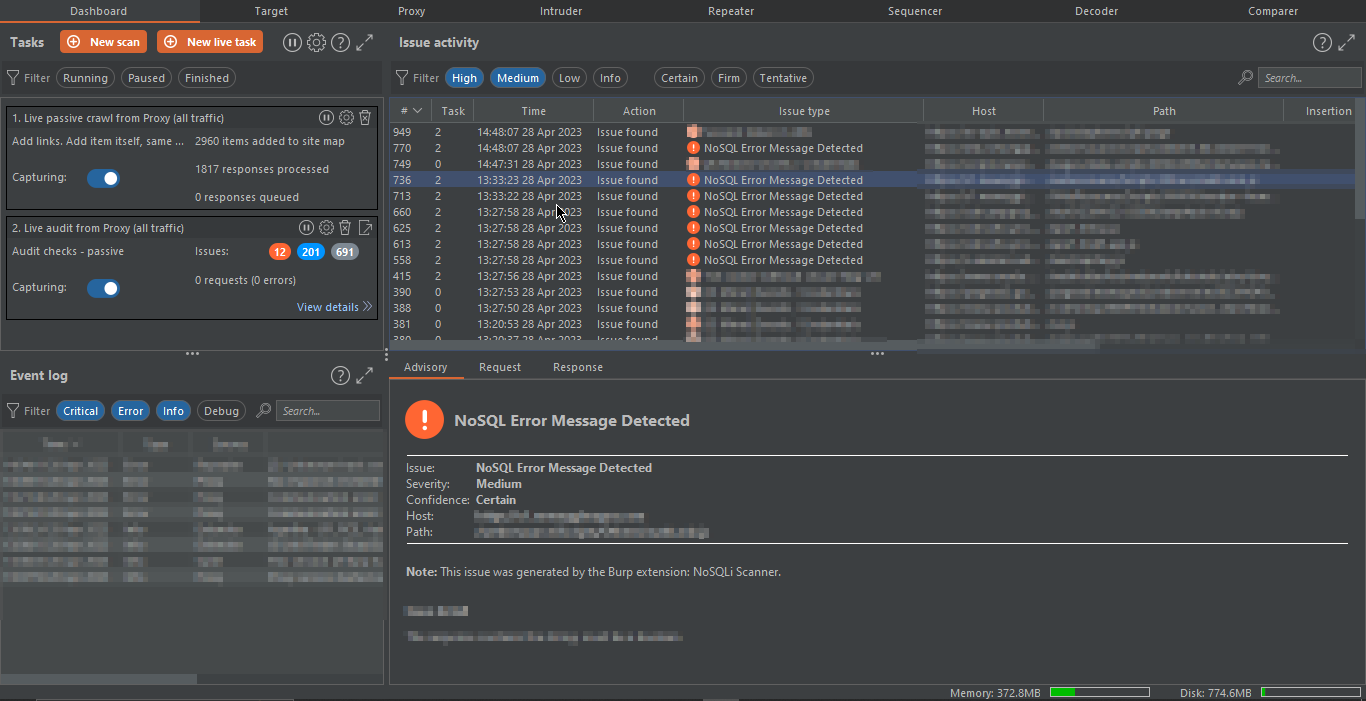
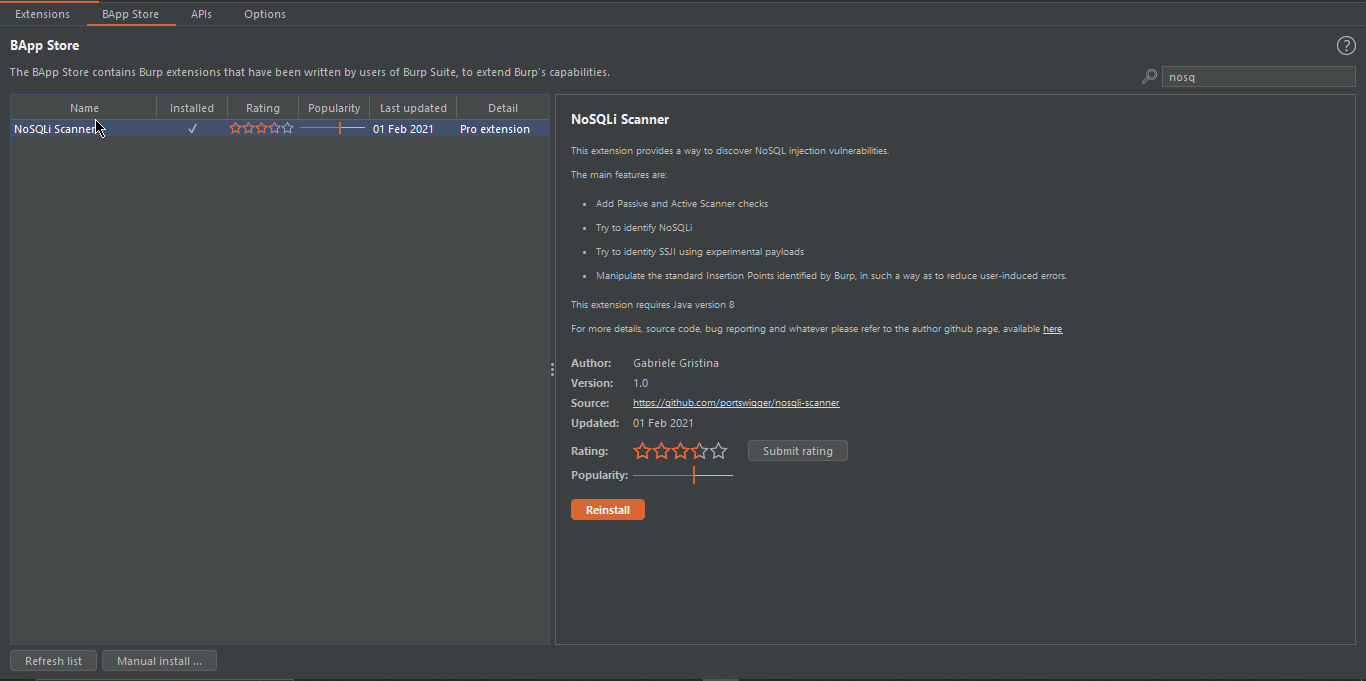
#6. NoSQLi Scanner:
The NoSQLi Scanner plugin in BurpSuite is designed to detect NoSQL injection vulnerabilities. NoSQL databases, such as MongoDB, are becoming more popular as web applications scale and require high performance. However, these databases can be vulnerable to injection attacks similar to SQL injection. The NoSQLi Scanner plugin automates the process of detecting potential NoSQL injection points and attempts to exploit them by injecting payloads into the target application. It is designed to work with different NoSQL databases and supports various injection techniques. By using this plugin, security testers can identify and report potential NoSQL injection vulnerabilities in web applications. This plugin may give many false positives, so be careful!
#7. SQLi Query Tampering:
SQL injection attacks are a common and dangerous type of web application vulnerability. They allow an attacker to execute malicious SQL statements against a target database, potentially compromising sensitive data or even taking control of the entire application. The SQLi Query Tampering plugin for Burp Suite is a powerful tool designed to detect and exploit SQL injection vulnerabilities in web applications. It works by modifying the SQL queries sent by the application to the backend database, injecting additional SQL code that can extract sensitive data or bypass authentication and authorization controls. This plugin includes a wide range of SQL injection attack vectors and techniques, including blind injection, error-based injection, time-based injection, and more. It also allows users to customize and create their own attack payloads, making it a versatile tool for any penetration testing or bug bounty engagement. Using the SQLi Query Tampering plugin can help security professionals identify and remediate SQL injection vulnerabilities in web applications, ultimately making the internet a safer place for everyone.

#8. CO2:
Co2 is a powerful plugin for BurpSuite that enhances its capabilities with various modules. However, it’s important to exercise caution when scanning untrusted sites as the SQLMapper component has had command injection flaws in the past. The extension has its own configuration tab with sub-tabs for each Co2 module, and modules that interact with other Burp tools can be disabled from within the Co2 configuration tab. This eliminates the need to disable the entire extension when using just part of the functionality. The following modules are included in Co2:
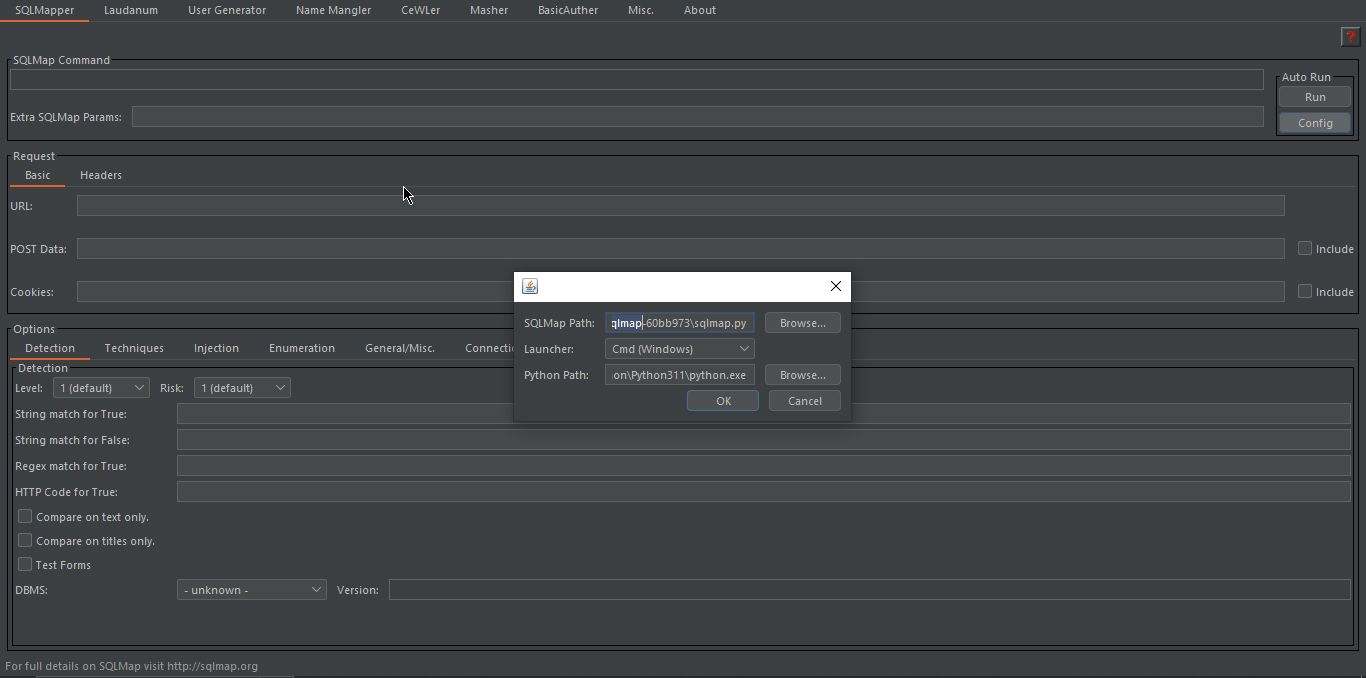
SQLMapper: This is a sqlmap helper that allows you to right-click on any request in Burp and send the request to SQLMapper. The SQLMapper screen will appear pre-populated with the URL, POST data (if applicable), and Cookies (if applicable) from the request. You can then set any other options you need and copy/paste the SQLMap command to sqlmap on your command line.
User Generator: This module uses publicly available census data from the US Census Bureau and popular baby names from the Social Security Administration to generate usernames based on statistical data. The interface allows you to customize the data sets and specify whether you want full names, initials, a delimiter between first and last names, and more. The tool will approximate which name combinations are the most common and sort the list accordingly. The result set is limited to the top 200,000 names to avoid performance issues.
Name Mangler: This module mangles names and domains to generate a list of potential usernames that can be used to test for valid logins.
CeWLer: This module is based on Digininja’s command-line CeWL script for extracting a wordlist from HTML files. The Co2 version works with a list of responses directly inside of Burp.
Masher: This module generates a fuzzy list of possible passwords using a seed list of words and a password specification. Masher combines words from the provided list, appends and replaces characters to build new passwords.
BasicAuther: This module takes a list of usernames and passwords and outputs proper BasicAuth strings that can be used in Intruder.

NOTE: You have to install sqlmap on your desktop and configure it’s path to this plugin. Install sqlpmap’s zip file (for windows, for linux you can download tar.gz file) > Head over to CO2 Plugin > Sqlmapper > Config > Select your sqlmap.py file and it will be ready.
Cool!! We’ve looked into some of the coolest extensions which you can use to maximse your bug bounty!
Note: This Blog is for Educational Purposes. I take no responsibility of any harm cause by my blog.
Conclusion:
In conclusion, Burp Suite is an incredibly powerful tool that can greatly enhance the effectiveness of your bug bounty hunting efforts. With the help of the plugins mentioned in this blog, you can improve your workflow, automate tedious tasks, and uncover vulnerabilities that may have gone unnoticed. From SQL injection to NoSQL injection to authentication bypass, these plugins provide you with the necessary tools to thoroughly test web applications and find critical security flaws. By utilizing these plugins effectively, you can take your bug bounty hunting to the next level and stay ahead of the game. Happy hacking!
Socials:
Twitter: https://twitter.com/0x2458
BuyMeACoffee: https://www.buymeacoffee.com/0x2458
Bonus:
As my regular reader knows, I always give a Bonus part in my blogs. This time it’s a small one.
Came Across an API Token but confused how to exploit it? Keyhacks Repo on Github has your answer! : D
See ya in next blog! Good Luck and Happy Hacking!