Hello! 0×2458 here! This time I’m back with a different and cool Topic- Getting Started with Mobile Application Security! In this Blog, you’ll be learning about various things related to Mobile AppSec, such as Configuring Android for testing, methods, Security Issues, Challenges, etc. Excited? Let’s start!
Section 1: Getting Started with Mobile App Security
1.1: What is Mobile AppSec - An Introduction
Mobile AppSec, short for Mobile Application Security, refers to the practices, techniques, and measures employed to protect mobile applications from potential security risks and vulnerabilities. With the increasing reliance on mobile devices and the growing popularity of mobile applications, ensuring the security of these apps has become paramount.
Mobile AppSec encompasses a range of security considerations, including the protection of sensitive data, prevention of unauthorized access, detection, and mitigation of security flaws, and safeguarding against various types of attacks. It involves both proactive measures taken during the development process and reactive measures to address security issues post-deployment.
The main objectives of Mobile AppSec are:
Secure Data Handling: Mobile applications often deal with sensitive user data, such as personal information, financial details, and authentication credentials. Mobile AppSec focuses on implementing strong encryption, secure data storage, and secure transmission protocols to protect this information from unauthorized access or disclosure.
Authentication and Authorization: Mobile AppSec addresses authentication and authorization mechanisms to ensure that only authorized users can access the application and its associated resources. This includes techniques such as secure login, multi-factor authentication, and session management.
Secure Communication: Mobile AppSec emphasizes secure communication between the mobile application and backend servers or APIs. It involves implementing secure transport protocols, such as HTTPS, and verifying server authenticity to prevent data interception or tampering.
Code and Application Hardening: Mobile AppSec involves securing the application’s codebase against common vulnerabilities, such as insecure coding practices, input validation flaws, and inadequate error handling. Techniques like code review, secure coding guidelines, and security testing are employed to identify and fix these issues.
Secure Offline Storage: Since mobile devices can be easily lost or stolen, Mobile AppSec addresses the security of offline storage. It includes measures to encrypt sensitive data stored on the device, implement secure local storage practices, and enable remote data wiping in case of device compromise.
Secure Updates and Patching: Mobile AppSec emphasizes the importance of regular updates and patches to address security vulnerabilities identified in the application. Timely updates help ensure that the app is protected against newly discovered threats and exploits.
Mobile AppSec is a continuous process that requires a combination of security awareness, secure development practices, rigorous testing, and ongoing monitoring. By prioritizing mobile application security, organizations can build trust with their users, safeguard sensitive information, and mitigate potential risks and threats in the ever-evolving landscape of mobile app security.
1.2: Configure Mobile Devices for Hacking - A detailed Guide
Well, as many of you do think, Mobile Application Security is a hard domain of cybersecurity, but that’s not the case. For me, it’s similar to Web-Penetration Testing(For me!). If you want to begin with Mobile Application Security, all you need is An Android Phone Running Android 6 or earlier, A pc with BurpSuite configured, and a WiFi connection. You need to Configure your Android with BurpSuite and You’re Done! You can now test Android applications! Alternatively, if you don’t have a spare Android Phone, you can test using Android Emulators. Don’t worry, I’ll provide all the steps for configuration. Let’s Begin.
1.2.1 Configuirung Android Devices for Testing:
To Configure Android Device, you need to do the following:
Configure your Burp Proxy listener to accept connections on all network interfaces.
Connect both your device and your computer to the same wireless network.
To interact with HTTPS traffic, you need to install a CA certificate on your android device at the system level.
Step 1: Configure the Burp Proxy listener
To configure the proxy settings for Burp Suite:
- Open Burp Suite and go to Proxy > Options.
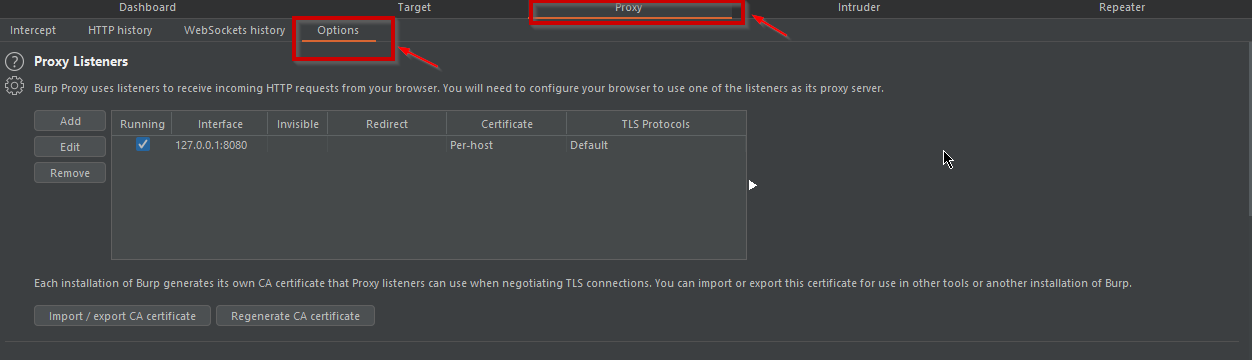
Now, Under Proxy Listners Click on “Add”. A dialogue Box will appear.
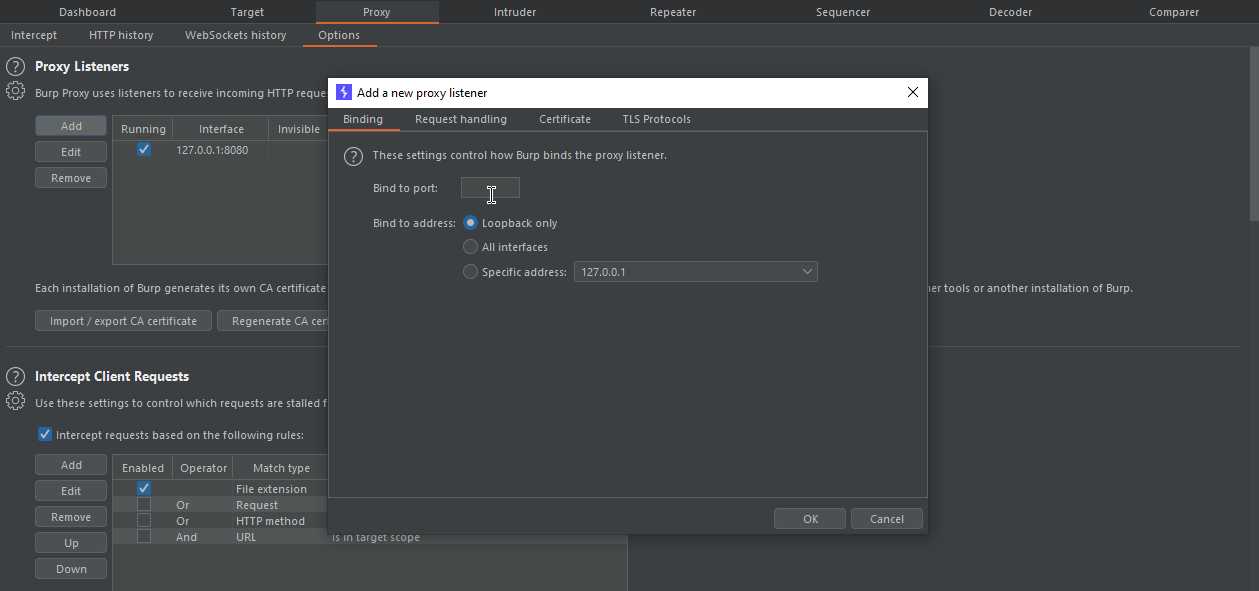
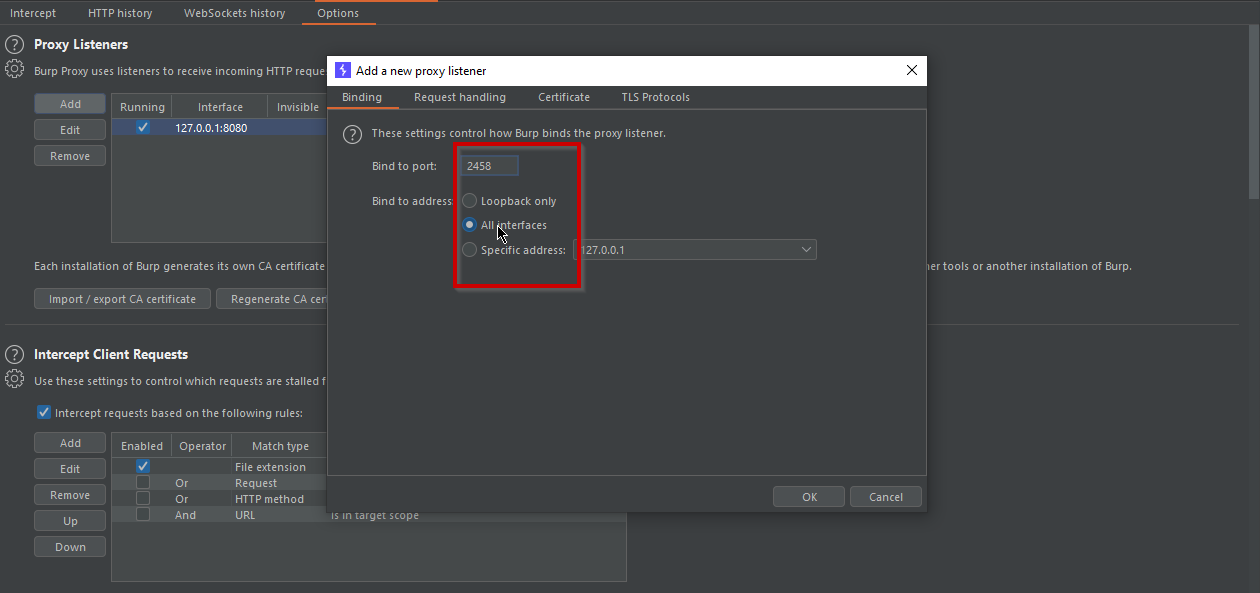
Add the Port Number of your own choise and click on “Listen on All Interfaces” > Ok> Yes.
Step2: Configure your device to use the proxy.
Make sure that your Android device is disconnected from the Wi-Fi network before you attempt to configure the proxy settings:
In your Android device, go to Settings > Network & internet.
Select Internet and long-press the name of your Wi-Fi network.
Select Modify.
From the Advanced options menu, select Proxy > Manual.
Set Proxy hostname to the IP of the computer running Burp Suite.
Set Proxy port to the port value that you configured for the Burp Proxy listener, in this example 2458.
Touch Save.
Step3: Install a CA certificate on your Android device
In order to interact with HTTPS traffic, you need to install a CA certificate from Burp Suite Professional on your Android device. This step is complicated and it varies across devices and versions of Android.
Visit http://burpsuite with the browser.
Download a copy of your Burp CA certificate.
Go to Files > Locate the Certificate.
Install the Certificate by touching on the Certificate.
Step 4: Test the configuration
To test the configuration:
Open Burp Suite Professional.
Go to Proxy > Intercept and click Intercept is off to switch intercept on.
Open the browser on your Android device and go to an HTTPS web page.
You can see that the Traffic is being Intercepted.
However, As I mentioned Earlier, It only works with Android 6 or earlier. For Android 7, this method will not work. I have found a resource for Android 7, You can refer to that. It’s here.
1.2.2 Configuirung Android Emulator for Testing:
Configuring Emulators is pretty much the same thing. Here are the Steps:
Step1: Download an Emulator. My choices are Nox and https://www.ldplayer.net/.
Step2: Follow all the steps Mentioned Above + Turn off all antiviruses and Firewalls, as they block your connection.
1.3 Understanding Mobile App Architectures:
In the vast world of mobile app development, understanding the various components and layers that constitute an application is crucial to understanding its security landscape. A detail on various Layers if a Mobile App is given below:
Presentation Layer:
The presentation layer encompasses the user interface (UI) and user experience (UX) elements of the mobile app. It includes visual components, such as screens, buttons, menus, and input fields, which users interact with. While this layer primarily focuses on usability and aesthetics, it can also pose security risks, such as UI-based attacks like clickjacking or phishing attempts.
Application Layer:
The application layer lies at the core of the mobile app and contains the logic and functionality that drive its operations. It includes modules for data processing, business rules, and integration with external services. Security vulnerabilities at this layer can result in unauthorized access, data leakage, or manipulation of critical app functions. Common risks include insecure data storage, insufficient input validation, and lack of secure communication protocols.
Data Layer:
The data layer deals with the storage and retrieval of data within the mobile app. This includes databases, local storage, and caching mechanisms. Data security risks involve unauthorized access, data leakage, or data integrity issues. Weak encryption, inadequate access controls, and insecure data transmission are among the vulnerabilities that can compromise the confidentiality and integrity of sensitive data.
Network Layer:
The network layer governs the communication between the mobile app and external servers or APIs. It encompasses various protocols and technologies, such as HTTP, HTTPS, RESTful APIs, or WebSockets. Security risks at this layer include man-in-the-middle attacks, session hijacking, or unauthorized interception of sensitive data. Implementing secure communication protocols, certificate pinning, and proper authentication mechanisms are essential to mitigate these risks.
Device Layer:
The device layer encompasses the underlying operating system, device hardware, and other native capabilities utilized by the mobile app. Security risks in this layer can arise from vulnerabilities in the operating system, insecure storage of sensitive data, or malicious exploitation of device features like camera, microphone, or GPS. Keeping the device’s operating system up to date, implementing secure coding practices, and utilizing appropriate permission models are crucial to safeguard against such risks.
By comprehending the different components and layers of a mobile app and recognizing the potential security risks inherent in each, we gain a deeper understanding of the challenges faced in securing mobile applications. As red teamers, it becomes our duty to meticulously examine each layer, identify vulnerabilities, and work hand in hand with developers to fortify the app’s defenses, ensuring the protection of user data and the overall security of the application.
Section 2: Resources for Mobile App Security
2.1 Learning Mobile App Security
Embarking on a journey into the realm of mobile app security requires a solid foundation of knowledge and a continuous thirst for learning. To aid you in your quest for mastering the art of securing mobile applications, I have curated a list of valuable resources. Whether you’re a beginner seeking to understand the basics or a seasoned professional aiming to enhance your skills, these recommended resources will serve as your trusted companions along the way.
Books:
“Mobile Application Security” by Himanshu Dwivedi
This comprehensive guide provides insights into the intricacies of mobile app security, covering topics such as secure coding practices, threat modeling, reverse engineering, and more.
“The Mobile Application Hacker’s Handbook” by Dominic Chell, Tyrone Erasmus, Shaun Colley, and Ollie Whitehouse
Written by renowned experts in the field, this book delves deep into the world of mobile app hacking, offering practical techniques, methodologies, and real-world case studies to enhance your understanding.
Online Courses and Tutorials:
“Mobile Security and Ethical Hacking” (Pluralsight)
This in-depth video course equips you with the knowledge and skills needed to identify and exploit vulnerabilities in mobile applications. Learn about common attack vectors, secure coding practices, and effective penetration testing techniques.
“OWASP Mobile Security Testing Guide” (OWASP)
The Open Web Application Security Project (OWASP) provides a comprehensive guide specifically focused on mobile app security testing. This resource covers a wide range of topics, including threat modeling, vulnerability analysis, and secure deployment practices.
“Android App Penetration Testing for Beginners” (Pentester Academy)
Dive into the world of Android app security with this beginner-friendly course. Gain hands-on experience by exploring common vulnerabilities, performing static and dynamic analysis, and executing penetration tests on Android applications.
“iOS App Penetration Testing for Beginners” (Pentester Academy)
Designed for aspiring iOS app security enthusiasts, this course offers a step-by-step approach to understanding the security aspects of iOS applications. Learn about secure coding practices, analyzing binary files, and exploiting vulnerabilities.
Communities and Conferences:
Mobile Security Testing Guide (MSTG) by OWASP
Stay connected with the vibrant community of mobile app security professionals through the Mobile Security Testing Guide. Engage in discussions, seek advice, and collaborate with like-minded individuals passionate about securing mobile applications.
AppSec conferences (e.g., OWASP AppSec, Black Hat, DEF CON)
Attend industry-leading conferences focused on application security, where experts share their knowledge, present cutting-edge research, and provide hands-on workshops. These conferences offer invaluable networking opportunities and a chance to stay up-to-date with the latest trends in mobile app security.
Remember, learning is a continuous process, and staying informed about the ever-evolving landscape of mobile app security is essential. Utilize these recommended resources as a springboard to enhance your knowledge and skills, enabling you to become a formidable force in the realm of mobile app security. Happy learning and may your journey be filled with exciting discoveries and successful exploits!
2.2: Mobile App Security Tools and Frameworks:
In the ever-evolving landscape of mobile app security, having the right set of tools and frameworks is crucial for effectively identifying vulnerabilities, analyzing risks, and fortifying defenses. Here, we highlight some of the popular tools and frameworks specifically designed to aid security professionals in testing and securing mobile applications. Each tool comes with its unique features and use cases, providing valuable support throughout the mobile app security testing process.
Mobile Security Framework (MobSF):
MobSF is an open-source framework that facilitates mobile app security testing for both Android and iOS platforms. It offers a wide range of features, including dynamic and static analysis, binary scanning, and vulnerability identification. MobSF integrates with other popular tools like OWASP ZAP, AndroBugs, and QARK to provide comprehensive testing capabilities.
OWASP Mobile Security Project:
The Open Web Application Security Project (OWASP) has a dedicated project focused on mobile app security. The OWASP Mobile Security Project provides a set of resources, tools, and guidelines for assessing and improving the security of mobile applications. Key tools within this project include the Mobile Security Testing Guide (MSTG) and the Mobile Application Security Verification Standard (MASVS).
Frida:
Frida is a dynamic instrumentation toolkit that allows security professionals to analyze and manipulate the runtime behavior of mobile applications. It supports both Android and iOS platforms and enables activities such as code injection, function tracing, and dynamic hooking. Frida’s versatility makes it a powerful tool for various security tasks, including identifying and exploiting vulnerabilities.
MobSF Integration Tools:
MobSF offers seamless integration with other renowned tools, expanding its capabilities and enhancing the mobile app security testing process. Some notable integrations include:
OWASP ZAP:
A widely-used web application security scanner that can be integrated with MobSF to perform dynamic analysis of network traffic between the mobile app and the server.
AndroBugs:
An Android application vulnerability scanner that complements MobSF’s static analysis capabilities by focusing on identifying security weaknesses within the app’s codebase.
QARK:
A static code analysis tool specifically designed for Android applications. Integrating QARK with MobSF helps in identifying potential security risks and vulnerabilities during the app’s development phase.
Appie:
Appie is a portable and scalable penetration testing platform for mobile apps. It offers features like dynamic analysis, traffic interception, and manipulation, allowing security professionals to simulate real-world attack scenarios. Appie provides an intuitive graphical interface, making it user-friendly for both beginners and experienced testers.
Drozer:
Drozer is an Android-focused security assessment framework that helps in identifying vulnerabilities and security misconfigurations. It allows for comprehensive testing, including dynamic analysis, application manipulation, and privilege escalation. Drozer provides a command-line interface, making it suitable for automated and script-based testing.
Needle:
Needle is a powerful iOS penetration testing framework that aids in identifying security flaws and vulnerabilities in iOS applications. It offers features such as runtime analysis, code injection, and vulnerability identification. Needle’s intuitive interface and extensive documentation make it a popular choice among iOS security testers.
Burp Suite Mobile Assistant:
Burp Suite, a widely-used web application security testing tool, offers a mobile assistant extension specifically designed for testing mobile apps. The Burp Suite Mobile Assistant allows security professionals to intercept and analyze network traffic, modify requests, and identify vulnerabilities in both Android and iOS applications.
There are still a lot more tools. I will cover them in Part2!
Section 3: Mobile vs. Web: How They Differ in Security
3.1: Understanding the differences between Mobile and Web Security Testing.
In the realm of security testing, mobile applications present a unique set of challenges that differentiate them from web applications. While web security testing focuses primarily on vulnerabilities related to web technologies and network communication, mobile security testing encompasses a broader range of concerns due to the nature of mobile devices and their distinct architecture. Let’s explore the key differences between mobile and web security testing.
Platform Diversity:
Unlike web applications that primarily target browsers, mobile applications run on various platforms, such as Android and iOS. Each platform has its own set of security considerations, programming languages, frameworks, and security features. Mobile security testing, therefore, requires expertise in understanding the platform-specific vulnerabilities and testing techniques.
Device-specific Features:
Mobile devices offer a wide range of features, including cameras, GPS, accelerometers, and biometric sensors. These features provide additional attack vectors and potential security risks. Mobile security testing should encompass the evaluation of these device-specific features and their potential impact on the application’s security posture.
Offline Capabilities:
Mobile applications often have offline capabilities, allowing users to interact with the app even when not connected to the internet. This introduces unique security challenges, such as local data storage, synchronization, and encryption. Testing offline capabilities and their associated security risks require specialized attention in mobile security testing.
Network Communication:
While web applications primarily rely on web protocols like HTTP and HTTPS, mobile applications often interact with various network protocols, including HTTP, HTTPS, Bluetooth, NFC, and more. Mobile security testing should encompass the assessment of these diverse communication channels, including the encryption and authentication mechanisms used, to identify potential vulnerabilities.
Mobile-specific Vulnerabilities:
Mobile apps are susceptible to specific vulnerabilities that are not commonly found in web applications. These include issues such as insecure data storage on the device, insecure interprocess communication, weak user authentication, and improper handling of sensitive data. Mobile security testing should focus on identifying and mitigating these mobile-specific vulnerabilities.
App Store Considerations:
Mobile applications are typically distributed through official app stores, subject to review and approval processes. App store guidelines often enforce security requirements, such as secure coding practices, permission handling, and data privacy. Mobile security testing should ensure compliance with app store guidelines and address any security concerns that could lead to app rejection or removal.
User Interaction and User Interface:
Mobile applications have a distinct user interface (UI) and user interaction patterns compared to web applications. The security of mobile app UI elements, authentication mechanisms, and user input validation must be thoroughly tested to prevent issues like UI spoofing, clickjacking, and user data leakage.
To effectively test mobile applications, security professionals should leverage specialized tools and frameworks designed for mobile app security testing. These tools offer features like dynamic and static analysis, vulnerability scanning, code review, and runtime analysis specific to mobile platforms.
In conclusion, mobile security testing goes beyond traditional web security testing by considering platform diversity, device-specific features, offline capabilities, network communication, mobile-specific vulnerabilities, app store considerations, and user interaction aspects. Understanding these differences and conducting comprehensive security testing helps ensure the robustness and integrity of mobile applications in an increasingly mobile-centric world.
Section 4: Mobile App Security Best Practices
4.1: Best Practices for Mobile AppSec
Mobile app security is a critical aspect of the development lifecycle, aiming to protect user data, prevent unauthorized access, and safeguard the overall integrity of the application. By following industry best practices, developers can build secure mobile apps that instill trust and confidence among users. Here are essential security practices to incorporate throughout the mobile app development lifecycle:
Secure Coding Practices:
Adopt secure coding practices from the outset, including input validation, output encoding, secure session management, and proper error handling. Utilize secure coding guidelines such as the OWASP Mobile Top 10 and platform-specific security recommendations.
Data Encryption:
Implement strong encryption algorithms to protect sensitive data at rest and in transit. Utilize platform-specific encryption APIs and consider end-to-end encryption for communication between the app and backend services.
Authentication and Authorization:
Implement robust authentication mechanisms, such as multi-factor authentication and secure password storage techniques like hashing and salting. Enforce strong password policies and ensure appropriate user authorization levels based on roles and permissions.
Secure Network Communication:
Use secure protocols like HTTPS for network communication to encrypt data transmitted between the app and backend servers. Implement certificate pinning to prevent man-in-the-middle attacks and validate server authenticity.
Secure Storage:
Store sensitive data securely on the device by leveraging platform-specific secure storage mechanisms, such as Keychain (iOS) or Keystore (Android). Avoid storing sensitive data in plain text or easily accessible locations.
Secure Third-Party Libraries and APIs:
Regularly update and patch third-party libraries and APIs used in the app to address known vulnerabilities. Verify the security of third-party components and libraries before integration.
Input Validation and Output Sanitization:
Validate and sanitize all user inputs to prevent common attacks like SQL injection, cross-site scripting (XSS), and remote code execution. Apply context-aware output encoding to protect against output-based vulnerabilities.
Secure Session Management:
Implement secure session management practices, including unique session identifiers, session timeouts, and session encryption. Ensure proper handling of session tokens and avoid exposing sensitive session data.
User Privacy and Data Protection:
Follow privacy regulations and guidelines, such as GDPR or CCPA, by obtaining user consent for data collection and implementing privacy-enhancing measures. Minimize the collection and retention of personally identifiable information (PII).
Secure Updates and Patch Management:
Regularly release security updates and patches to address discovered vulnerabilities promptly. Implement a secure update mechanism to ensure users receive and install updates securely.
Security Testing:
Conduct thorough security testing throughout the development lifecycle, including static code analysis, dynamic application security testing (DAST), penetration testing, and security code reviews. Leverage tools and frameworks designed for mobile app security testing.
Secure Backend APIs and Server-side Components:
Ensure the security of backend APIs and server-side components that the mobile app interacts with. Implement authentication, access controls, and input validation on the server-side to prevent unauthorized access and data breaches.
By incorporating these mobile app security best practices, developers can significantly enhance the security posture of their applications, protecting user data and maintaining user trust. Remember that security should be an ongoing effort, and regular security assessments and updates are essential to address emerging threats and vulnerabilities in the ever-evolving mobile app landscape.
Section 5: Common Mobile App Vulnerabilities and Exploits
5.1: Understanding some Common Mobile App Vulnerabilities and Exploits
Mobile apps are susceptible to various security vulnerabilities that can be exploited by malicious actors. Understanding these vulnerabilities and the potential exploits associated with them is crucial for developers and security practitioners. Here are some common mobile app vulnerabilities along with real-world examples:
Insecure Data Storage:
Apps may store sensitive information, such as login credentials or user data, in an insecure manner. This can include storing data in plain text or using weak encryption algorithms. Attackers can exploit this vulnerability by gaining unauthorized access to stored data, leading to identity theft or data breaches.
Example: In 2014, Snapchat suffered a data breach where millions of user account details were exposed due to weak encryption and inadequate data storage practices.
Poor Authentication and Authorization:
Weak or inadequate authentication mechanisms can enable unauthorized access to user accounts or privileged functionalities. Insufficient authorization controls can allow unauthorized users to perform actions beyond their privileges.
Example: In 2019, a vulnerability in the Facebook SDK allowed attackers to bypass authentication and gain unauthorized access to millions of user accounts in popular mobile apps.
Insecure Network Communication:
Apps that transmit data over insecure channels, such as unencrypted HTTP, are susceptible to interception and tampering by attackers. This can lead to sensitive data leakage, session hijacking, or man-in-the-middle attacks.
Example: In 2017, a vulnerability named “Eavesdropper” exposed millions of plaintext passwords due to improper SSL certificate validation in certain mobile apps.
Code Injection:
Improper handling of user-supplied data, such as not validating or sanitizing inputs, can lead to code injection vulnerabilities. Attackers can exploit this to execute arbitrary code or inject malicious scripts into the app.
Example: The Stagefright vulnerability discovered in 2015 allowed attackers to remotely execute code on Android devices by sending a specially crafted multimedia message (MMS).
Insecure Backend APIs:
Inadequate security controls in backend APIs can expose sensitive user data or allow unauthorized access to critical functionalities. Poorly implemented authentication, insufficient input validation, or lack of proper access controls can be exploited by attackers.
Example: In 2019, an API vulnerability in the T-Mobile website exposed customer account information, including personal and financial details, due to improper API implementation.
Insufficient Session Management:
Weak session management practices, such as predictable session tokens, session fixation, or session timeouts that are too long, can lead to session hijacking or account compromise.
Example: In 2018, a vulnerability in the Tinder mobile app allowed attackers to hijack user sessions by intercepting unencrypted session tokens.
Reverse Engineering and Tampering:
Mobile apps can be reverse engineered, and attackers can modify the app’s code or resources to introduce malicious functionality or bypass security controls.
Example: The Pokémon GO app faced challenges with tampering, where attackers modified the app to spoof GPS locations, cheat in the game, or inject malware into compromised versions.
It is essential for developers and security professionals to be aware of these vulnerabilities and actively implement security measures to mitigate them. By conducting thorough security assessments, penetration testing, and following secure coding practices, mobile app vulnerabilities can be identified and addressed before they can be exploited by attackers. Regular security updates and monitoring should also be employed to protect against emerging threats and vulnerabilities. Some of them Sounds Similar Right? During Web Testing, you have come accross some of them. Right? Absolutely! That’s why both mobile and web ar similar to me. xD.
Section 6: Securing Mobile Devices and Data
6.1: Ways to Secure Mobile Devices and User Data
Mobile devices play a significant role in our lives, and securing them is crucial to protect sensitive information and maintain privacy. Here are some practical tips and best practices to secure mobile devices and safeguard user data:
Keep the Device Updated:
Regularly update the operating system, apps, and firmware on your mobile device. Updates often include security patches that address known vulnerabilities and improve overall device security.
Use Strong and Unique Passwords:
Set strong and unique passwords or passphrases for device lock screens and important accounts. Avoid using common passwords and enable two-factor authentication whenever possible to add an extra layer of security.
Enable Device Encryption:
Encrypt the data stored on your mobile device to protect it from unauthorized access. Most modern devices offer built-in encryption features that can be enabled in the device settings.
Install Apps from Trusted Sources:
Only download and install apps from official app stores such as Google Play Store or Apple App Store. Third-party app stores or sideloading apps from unknown sources can expose your device to malicious software.
Review App Permissions:
Before installing an app, carefully review the permissions it requests. Grant only the necessary permissions required for the app’s functionality. Be cautious of apps that request excessive permissions that seem unrelated to their purpose.
Be Wary of Phishing Attempts:
Exercise caution when clicking on links or downloading attachments from unfamiliar sources, as they may lead to phishing attempts or malware installation. Verify the legitimacy of emails, messages, and websites before providing any personal information.
Use Mobile Security Apps:
Install reputable mobile security apps that provide features like antivirus scanning, anti-malware protection, and app scanning for added security. These apps can help detect and mitigate potential threats.
Secure Wireless Connections:
Avoid connecting to unsecured or public Wi-Fi networks, as they can be vulnerable to eavesdropping and data interception. When using Wi-Fi networks, ensure they are password-protected and encrypted (e.g., WPA2).
Enable Remote Tracking and Wiping:
Enable features like “Find My Device” or similar services provided by the device manufacturer. These features allow you to track the device’s location and remotely erase its data in case of loss or theft.
Backup Data Regularly:
Regularly back up your mobile device’s data to a secure cloud storage or offline location. In case of device loss, damage, or data corruption, you can restore your important information.
Use Mobile Device Management (MDM):
For organizations and businesses, implementing Mobile Device Management solutions can help enforce security policies, remotely manage devices, and ensure compliance with security standards.
By following these best practices, users can enhance the security of their mobile devices, protect their personal and sensitive data, and minimize the risk of unauthorized access or data breaches. It’s important to stay vigilant, stay informed about emerging threats, and adapt security measures accordingly.
Section 7: Challenges in Mobile App Security
7.1 Understanding the Challenges in Mobile App Security
Mobile app security presents unique challenges due to the dynamic nature of the mobile ecosystem. Here are some of the specific challenges faced in mobile app security:
Platform Fragmentation:
Mobile devices run on various platforms such as iOS, Android, and others, each with its own architecture, security features, and development frameworks. The fragmentation of platforms makes it challenging to ensure consistent security across different devices and operating systems.
Diverse Operating Systems:
Mobile apps need to be developed and tested for multiple operating systems, each with its own security considerations. Developers must understand the nuances of each operating system and implement security measures accordingly.
App Store Ecosystems:
Mobile apps are distributed through app store ecosystems, such as Google Play Store and Apple App Store. These ecosystems have their own review processes, guidelines, and security measures in place. However, some malicious apps still manage to slip through the screening process, posing risks to users.
User Awareness and Behavior:
Users play a crucial role in mobile app security. However, user awareness of security best practices and their behavior regarding app downloads, permissions, and updates can vary significantly. Lack of user awareness and adherence to security practices can expose devices and data to potential risks.
Rapid Development Cycles:
Mobile app development often follows agile methodologies, with frequent updates and releases. The fast-paced development cycles can result in time constraints, leading to potential security oversights or inadequate testing of new features.
Third-Party Libraries and Dependencies:
Mobile app development relies heavily on third-party libraries and dependencies. While these libraries can enhance functionality and speed up development, they can also introduce vulnerabilities if not properly vetted and updated.
Offline Data Storage:
Mobile apps often store sensitive data locally on devices, posing additional security risks. Protecting data at rest becomes crucial, as unauthorized access to a device can potentially expose stored data.
Reverse Engineering and Code Tampering:
Mobile apps are susceptible to reverse engineering and code tampering, as the app’s code and assets are readily accessible on the device. Attackers can analyze the code, extract sensitive information, modify app behavior, or inject malicious code.
Secure Communication Channels:
Mobile apps rely on various network connections, such as Wi-Fi, cellular data, or Bluetooth, for data transmission. Ensuring secure communication channels and protecting data in transit is essential to prevent interception or tampering.
BYOD (Bring Your Own Device) Policies:
Many organizations implement BYOD policies, allowing employees to use personal devices for work purposes. Balancing security requirements with personal device usage and varying levels of device security can be a challenge.
Addressing these challenges requires a comprehensive approach to mobile app security. Developers should stay updated on the latest security practices, follow secure coding guidelines, conduct thorough security testing, and actively engage in vulnerability management. User education and awareness programs can also help mitigate risks by promoting responsible app usage and security-conscious behavior.
By understanding and addressing these challenges, organizations and developers can enhance the security of mobile apps, protect user data, and provide a safer mobile experience for their users.
Section 8: Mobile App Security Certifications and Training
8.1: Mobile AppSec Certifications and Training
Obtaining certifications and undergoing specialized training in mobile app security can greatly enhance your skills and credibility in the field. Here are some relevant certifications and training programs to consider:
Certified Mobile Security Professional (CMSP):
Offered by the Global Information Assurance Certification (GIAC), CMSP is a vendor-neutral certification that validates your expertise in mobile device and application security. The certification covers topics such as mobile app vulnerabilities, secure coding practices, and mobile device management.
Mobile Application Security Tester (MAST):
Provided by the International Information Systems Security Certification Consortium (ISC²), the MAST certification focuses on assessing and mitigating mobile app security risks. It covers areas like secure development, threat modeling, and security testing methodologies specific to mobile apps.
Certified Mobile Application Security Engineer (CMASE):
Offered by the Mobile App Security Testing (MAST) Alliance, CMASE is a comprehensive certification program for professionals involved in mobile app security testing. It covers areas such as risk assessment, secure coding, reverse engineering, and secure app deployment.
OWASP Mobile Security Testing Guide (MSTG):
The Mobile Security Testing Guide, developed by the Open Web Application Security Project (OWASP), provides a comprehensive framework and methodology for testing the security of mobile applications. It offers practical guidance and best practices for identifying and mitigating common mobile app vulnerabilities.
SANS Mobile Device Security and Ethical Hacking Training:
SANS Institute offers training courses focused on mobile device security and ethical hacking. These courses cover topics such as mobile app penetration testing, reverse engineering, secure coding, and mobile device forensics.
Mobile Application Security Courses by Online Learning Platforms:
Online learning platforms like Udemy, Coursera, and Pluralsight offer a range of mobile app security courses. These courses cover various aspects of mobile app security, including secure coding, vulnerability assessment, reverse engineering, and secure app deployment.
When choosing certifications and training programs, consider your specific career goals and the areas of mobile app security you wish to specialize in. It’s also essential to check the credibility and recognition of the certification or training provider.
By investing in certifications and training, you demonstrate your commitment to continuous learning and professional growth in mobile app security. These credentials can help you stand out in the job market, open up new career opportunities, and establish yourself as a trusted expert in the field.
Conclusion
Mobile app security is a critical aspect of ensuring the protection of user data and maintaining the integrity of mobile applications. In this blog, we explored various aspects of mobile app security, starting from understanding the fundamentals of mobile app security to discussing common vulnerabilities, best practices, and challenges.
By following best practices in mobile app security, developers can minimize security risks, protect user privacy, and build secure and trustworthy mobile applications. It is essential to stay updated with the latest security trends, leverage security tools and frameworks, and continuously assess and address potential vulnerabilities.
Additionally, individuals interested in specializing in mobile app security can benefit from certifications and training programs that enhance their knowledge and skills. These credentials not only validate expertise but also provide valuable insights into the latest security practices and methodologies.
Remember, mobile app security is an ongoing process that requires vigilance, adaptability, and a proactive approach. By prioritizing security throughout the mobile app development lifecycle and staying informed about emerging threats and best practices, you can contribute to a safer and more secure mobile app landscape.
Stay committed to learning, exploring new techniques, and engaging with the mobile app security community to stay ahead of potential risks and make a meaningful impact in the field of mobile app security.
Socials:
Twitter: https://twitter.com/0x2458
BuyMeACoffee: https://buymeacoffee.com/0x2458
BONUS!!
For this Blog, Bonus Part is Few more Tools which will help you in Mobile-AppsSec:
Android Debug Bridge (adb): This versatile command-line tool is a Dex to Java decompiler useful for producing Java source code from Android DEX and APK files.
APKTool: This reverse engineering tool unpacks Android app packages to ensure the files are readable and can rebuild apps.
JADX: This tool eases the process of decompiling binaries for reverse engineering.
Magisk: This tool for rooting Android devices has evolved over the years into a more powerful tool that boasts a collection of dozens of modules.
Xposed: This tool grants access to many third-party or open-source tweaks that can be used for certain aspects of testing.
So, That’s the End of this Blog. See ya in Next One! Happy Hacking!
#WRAP