Wait, you can do that? The answer is a resounding “yes”. And I’m not the only one who got my OSCP at the age of 16. Meet Mihai, Vanshal, Grant, and this person from Reddit. Admittedly, the number of us is few and far between when compared to the typical demographic of OSCP test-takers. To add to this, I’m a woman and I haven’t seen any other women my age do this. Still, people have done it and it is possible.
I present to you, the beautiful:

How to Get Your OSCP as a Minor
For those that are like me, or simply for the curious, the process is slightly different for minors. I contacted registrar@offensive-security.com and asked them for the registration steps as a minor. As a response, they requested that I send in my government-issued ID and a letter with my parent’s signature. I responded with these and they informed me that I was eligible to take the PEN-200. You must do this before buying the PEN-200.
As a note on money, I know that we’re probably broke high-school students and the cheapest option ($1499) is not very cheap. If you work at a job, your employer may be willing to pay for the training, even if you don’t work in a position related to technology. There’s a slim chance you can convince the school to pay for it. If not, maybe family/friends can help, or you could do what I did and pay for it yourself with the money that you earn from a job/internship.

Also, it’s important that your parents/guardians are on board. They don’t have to be your biggest cheerleaders but make sure that they understand that this involves taking a 48-hour exam. If you’re doing this on a weekend, it could interfere with your sleep before school and it will be very beneficial for you to have a workspace to do the exam at that is free of distractions. Food is another concern and if they’re supportive enough to cook for you, that can be helpful. These are things that you may have to discuss with them, and I know that it can be hard to convince them if they don’t understand the value of an OSCP (or the cost of it). It’s just important to keep in mind that they ultimately have the last call in whether you are allowed to hack into computers for 24 hours instead of doing chores.
I was lucky enough to have parents who didn’t understand but supported me as long as I was willing to pay for it on my own.
My OSCP Journey
This will include my preparation, my mindset, and my exam/report experience.
This simple image is a summary of my OSCP timeline.
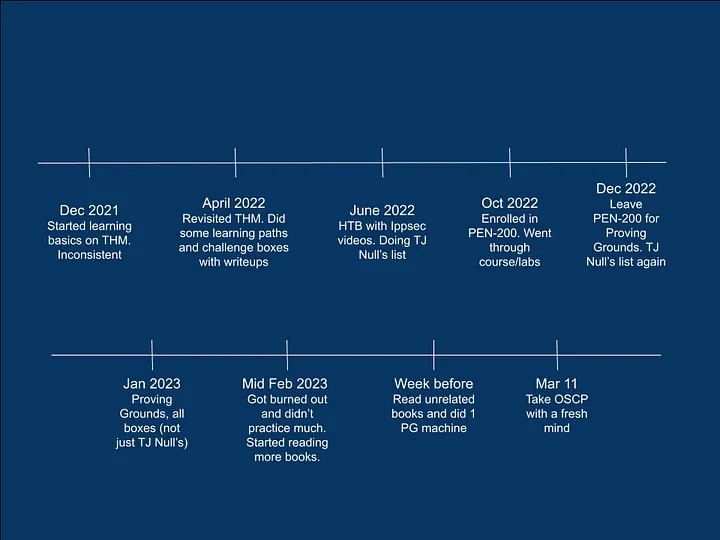
My Background
I started from a bit of a unique position. Because of my (albeit inconsistent) work over the past 3 years, I had been able to establish a technical foundation in coding. I didn’t understand IT or networking, but I understood software. I began my journey with 1 ½ years of experience as a software engineer in part-time internships throughout my first 2 years of high school. I can talk more about this in another post if people are interested because finding these internships was a vast challenge as a minor. This is not necessary by any means, but I do think that the background helped me. In particular, from this, I got comfortable reading documentation, understanding/writing code, and troubleshooting.
The Beginning
My cybersecurity journey started out in late December of 2021 with a TryHackMe course on networking. It began with the fundamental question of how information can travel from one device to the next. Why is it that I can send a message to my mother’s phone without ever having physical interaction with it? And I also wondered about hacking, and, in particular, what it truly looked like.
My journey started out of pure curiosity.

I went through the modules and then didn’t touch TryHackMe again, or anything cybersecurity-related, for another 2 months. I was at an internship at a startup on top of school, which was already exhausting. I knew that doing any more would lead me to burn out.
When my internship ended, I had more free time. I recall using TryHackMe for about 1–2 hours per week in February and March of 2022. But my main focus was finding another software engineering internship because I wanted more experience before I graduated high school. At this point, I didn’t take cybersecurity seriously and I didn’t have the skill to do much relating to it.
Around April of 2022, I started to passively do more TryHackMe alongside my new internship. At this point, I became deeply passionate about understanding the way that the devices worked. The idea of being able to outsmart the way that something functions so as to make it do something it wasn’t intended to do really appealed to me. It was the intellectual challenge that I craved and allowed me the freedom to think creatively. I began to understand the world better from what the modem down the hall does to how my school account works.

Getting More Focused
The summer of 2022 was by far my most prolific period of learning throughout this journey. I watched countless YouTube videos, read numerous research blogs, and just fell in love with this community of diverse thinkers. It’s fascinating the way that cybersecurity folks will use their beautiful brains to challenge their surroundings. I found a video of a guy hacking his car, I learned about the Flipper Zero, and the WiFi Pineapple. Each of these surprised me in the most astonishing way because I didn’t know that these feats and gadgets were possible!
This strengthened my passion for cybersecurity and I began following closely to IppSec. I couldn’t do HackTheBox machines without help from a walkthrough. By the way, HackTheBox is hard! Those machines are way more difficult than the OSCP! If you can’t do them, don’t fret. It takes practice and patience over a long-enough period of time. And that timeline will be different for each person.

I also took this time to learn basic networking and IT from this extremely helpful channel and did some experiments on my home network.
Enrolling in the PEN-200
This was a big step for me. I was unsure of whether I was skilled enough to get started. By this point, I was able to do some of the HTB boxes on TJ Null’s list without referencing a writeup. Getting this course was a big purchase and I didn’t want to waste my money.
I ended up being disappointed with the course. I was hoping for better explanations and the topic exercises didn’t work about 10% of the time which prevented me from getting bonus points. In addition, before I knew about the topic exercises, I tried writing the lab report just to find out it wasn’t accepted after January 2023 for bonus points, so I wasted 1 ½ months writing 400 pages when I could have instead been learning skills that would actually transfer to the OSCP.
The labs weren’t very valuable to me with the exception of the AD networks and the IT network that required pivoting to get to. These two allowed me to practice port-forwarding and AD methodology in a way that was meaningful and transferrable.
After about 2 months, of the PEN-200, I left to find better labs in Proving Grounds. I started by following TJ Null’s list, and then I switched to doing the ones that weren’t listed since I finished the list. It was also around this time that I got really interested in anonymity. So I spent the first week of my Christmas break learning about anonymity. I went on a number of other research tangents throughout my journey. I realized that I had trouble sustaining my OSCP journey without taking the time to explore other topics that interested me, so it was a common occurrence for me to shift my focus away from the OSCP every few weeks to learn something else.

Woman who is stressed for her dear life
In the month leading up to the exam, I had reached a point of exhaustion. I experienced stress from several areas of my life at once and came to the conclusion that if I wanted to do well on my exam, de-stressing was my top priority. At this point, I had compromised over 200 lab machines total. I had the skill, I had my notes, and I had intuition. The final month wasn’t going to make a difference. I was already ready.
As a result, I spent this time reading books about anthropology, neuroscience, and history. I went to the gym and socialized with friends at school I created more free time for myself and did what I needed to relax while also keeping my thinking skills sharp.
I did about 1 PG machine per week. For each one of these, I made a focused effort to practice thorough note-taking and I would write an example report on it.
I scheduled my exam about 2 weeks prior to the exam date. Waiting until so late meant that the only time available for me was 4:00 AM. I reserved this time knowing I would be able to wake up from the adrenaline rush.
Exam Day
I woke up at 12:30 AM. I think the excitement woke me up because I was unable to fall asleep. I went to sleep at 8:00 PM the night before, hoping to wake up at 3:15 AM. It turned out that I didn’t even need to set an alarm that day!
This wasn’t ideal because I had about 3 less hours of sleep than planned. I was still able to make it work, however. I logged on to the proctoring software at 3:45. After walking through the pre-exam checks, I was able to connect to my VPN at 4:00 AM.
Here is a quick timeline of my test since this is already getting lengthy:
Timeline
- 4:00 AM (0pts)- Use RustScan to scan all the hosts and become familiar with my exam dashboard.
- 4:10 AM (0pts)- Start enumerating the first AD machine. I didn’t find anything useful so I moved on temporarily.
- 4:40 AM (0pts)- Start enumerating one of the individual machines. I figure out what I need to do.
- 4:55 AM (10pts)- Submit my first local.txt and try to privesc.
- 5:10 AM (10pts)- Don’t find a quick privesc, so start looking at second independent target. It takes about 20 more minutes, but I find what I need.
- 5:46 AM (20pts)- Got a shell and submitted second local.txt.
- 5:46–6:10 AM (20pts)- Take a break.
- 6:10 AM (20pts)- Enumerate domain controller. At this point, I’m getting really deep into enumeration and finding nothing.
- 8:30 AM (20pts)- Shift focus on 3rd independent target.
- 9:20 AM (20pts)- Found potential vulnerabilities, but wasn’t able to exploit them. Tried privesc on 1st independent target again.
- 10:20 AM (20pts)- Discovered interesting findings. Unable to use them for an exploit. Moved to AD machine.
- 11:20 AM (20pts)- Thorough enumeration, but didn’t find what I needed. I’m starting to get anxious.
- 11:20–11:50 AM (20pts)- Take a break.
By this point, I was starting to lose my cool. I had been awake for nearly 12 hours on insufficient sleep. I went on a walk to clear my mind and brainstorm new enumeration ideas. With my list in mind, I returned to the exam desk:
- 11:50 AM (20pts)- Enumerate AD machine more with new ideas.
- 1:30 PM (20pts)- Still no progress. Briefly contemplate giving up, but decide to keep going (read more about this in next section).
- 3:00 PM (20pts)- Take a nap. Struggle to sleep because of excitement, but eventually relax. Completely exhausted from my enumeration efforts and lack of adequate sleep.
- 4:30 PM (20pts)- Wake up and continue searching AD machine. This time with more of a focus on thorough, methodical, and manual enumeration.
- 5:00 PM (20pts)- Find the missing piece!
- 5:30 PM (20pts)- Successfully exploit first AD machine!
- 6:30 PM (20pts)- Escalate privileges and get proof.txt. Take a short break to cry tears of joy.
- 7:00 PM (20pts)- Encountering difficulties with getting one of my tools to work the way it normally does.
- 8:00 PM (20pts)- I found the solution to my problem after a lot of troubleshooting and continued to move forward.
- 8:30–8:50 PM (20pts)- Take a break.
- 9:05 PM (20pts)- Move laterally to 2nd AD machine and get proof.txt.
- 9:31 PM (60pts)- Privesc to 3rd AD machine as domain admin. Got proof.txt!
At this point, I was in utter disbelief that I had actually done it. I took a break from the exam to go tell my mom how I was able to actually do it. I said, “This all started out as a naive dream that I had last April and I didn’t think it would actually happen. I went for it anyways, and now it’s actually coming true.”
Now, I had the final task of scoring 10 more points before I was eligible to pass. I started by trying to get a foothold on independent target #3, but continue to fail. I go for the privesc on the 1st independent target, but hit numerous dead ends.
- 11:30 PM (60pts)- Shift focus to privesc on 2nd independent target, the one I thought I was least likely to get. My enumeration scripts weren’t working and I didn’t find much in my initial manual enumeration. Then, I went through my notes and tried each enumeration step one-by-one.
- 11:50 PM (60pts)- Discover a vulnerability that allowed me to privesc from a check that I almost didn’t include in my notes. I figured out how to exploit it and attempted it with the expectation that it would fail since I had been failing for the past 3 hours.
- 11:55 PM (70pts)- The exploit succeeds and I can’t believe that I just scored 70 points!

My jaw is dropped as I stare at my terminal output. The feeling that I experienced in this moment is indescribable. My best attempt at illustrating the way that I felt is runner’s high… on a high. I had never felt so uplifted and energetic. This moment made the preceding hours of banging my head against the keyboard worth it. I take a break and just allow myself the time to appreciate that moment before continuing
- 12:30 AM (70pts)- Do more enumeration on 3rd independent target to see if I can get an easy foothold. Realize how exhausted I am and check that I did an adequate job at screenshots and note-taking.
- 1:10 AM-iss (70pts)- End exam early after verifying I had all the documentation I needed to write a good report
I made the difficult decision to end my exam at 70 points, knowing that any mistake I made in reporting, proof screenshots, or flag submission would result in a fail. After triple-checking that my notes were thorough and that my screenshots/flag submissions met the exam requirements, I asked my proctor to end the exam early. I chose to do this for two reasons:
I would rather spend the last 3 hours of exam time sleeping since I knew I had a report to write the next day that required strong mental focus.
If I were to compromise another machine, I would have to add it to my report, which would just make a job the next day more difficult.
Combined, I would have less sleep and more work for the next day. I decided that, ultimately, for me to write a great report tomorrow, I needed the sleep. So I sacrificed the potential extra points for the security that I would have the brain power to make the most beautiful report of my life.
I also do want to mention that I was taking thorough notes and screenshots throughout my exam time just like I had practiced doing. I didn’t have to retrace my steps in order to ensure I had good notes because I had developed good documentation skills before the exam.
I do want to note that I left out many of the breaks that I took just for the sake of brevity. I probably did take a break every 50 minutes on average. Most of them were only 5 minutes, some were 30.
Don’t Give Up

I do want to touch on 1:30 AM. I did genuinely consider quitting. I had previously failed the eJPT exam last July, so part of me figured that I was destined to fail this one as well. Before I allowed myself to spiral, I reconsidered what it cost me to be able to have that moment. I thought about the money that I spent, the hours I took to prepare, and the people who believed in me. I made an agreement with myself:
I told myself that it was okay to fail. As long as I failed knowing that I did everything I possibly could to succeed.
So in order to appease my own mind and fail this exam regret-free, I continued. Ironically, it was my willingness to fail that allowed me to succeed. My stress levels decreased and I was able to actually get some sleep. After my nap, I compromised the first AD machine!
You’ll Run Out of Ideas Before You Run Out of Time
The reason I was able to compromise the first AD machine after 12 hours of being stuck is this: I kept coming up with new ideas. Even if there’s a 1% chance of it working, when you have 100 of those ideas, one of them is bound to be it!
Channel your inner child and keep asking questions and experimenting with ideas, even if you think it won’t work. Most ideas will probably fail, but all you need is one success.
Reporting
I could make a dedicated article just on this topic. To summarize, I cross-referenced multiple templates that I found online and figured out what my report should look like. I then used the template that I thought was the most aesthetic and modified it to fit my needs.
I took pride in the report I created because I was very meticulous about my word choice, adhering to the documentation requirements, maintaining a consistent diction, explaining concepts clearly and accurately, and providing adequate screenshots.
I submitted my report after triple-checking that it was perfect and re-reading it countless times. Then, the wait ensued.
The Aftermath
This exam left me exhausted. I was very sleep deprived, fatigued, and anxious. It takes a significant amount of mental energy to maintain such intense attention to detail for a prolonged period of time. Throughout the exam period, I had a constant rush of adrenaline. And this made it near impossible to fall asleep. After I had submitted my report, I had to next most difficult part of the OSCP: the wait. Luckily, it only took 25 hours for me to get the email that I passed. Each of those 25 hours, I made sure to refresh my inbox every 30 seconds (optional step).
I do want to mention that this exam also takes a physical toll. Sitting at a desk for so many hours, even with breaks, is hard on the body. Make sure to move, stretch, and hydrate. I felt stiff in the few days following the exam.
For the next few days, I felt a lightness and joy knowing that all of my hard work had paid off. That I had dared to try something so ambitious and unrealistic and it actually worked. This was a major accomplishment for me that required overcoming countless challenges.
Takeaways
The OSCP was much more than a test of technical ability. It was an assessment of organizational skills, time management, resourcefulness, troubleshooting, problem-solving ability, capacity to work under stress, and much more. There was a point during the exam when BurpSuite wasn’t working for me, so I had to improvise in order to figure out a different solution. There were points where I almost went down rabbit holes searching for something that didn’t exist. It really takes experience to realize when these things are happening and how to adapt.
Additionally, working under that time constraint with a proctor watching my every move through the webcam was stressful. I also had to make sure I had standards for taking good notes, I had my systems for organizing the log files that I collected, a way to organize my screenshots, I knew the sections and layout of my report, etc.. A failure to do any of these would result in time being wasted, and with such a strict time constraint, there wasn’t much room for error.
Was it worth it?
The short answer is that I don’t know yet. It’s really hard to find cybersecurity work in general as a minor, but I think that having this certification demonstrates my skill and for the few opportunities that do exist, I’ll be more likely to actually get them.
It’s worth noting that when people who know me think about cybersecurity, I’m the first person who comes to mind, which can help in creating more opportunities through word-of-mouth. Additionally, I am more respected by the adults and peers who understand what the OSCP is. When I’m networking, people are more interested in learning about me and working with me than before I was certified now that I have something tangible to back up my skill.
Accomplishing this in high school is a pretty remarkable feat, and people in the industry realize this and respect it. It’s impressive and can help get your foot in the door in combination with other factors such as networking, education, and other experiences/projects. The closer that you get to becoming a legal adult, the more valuable the OSCP becomes in terms of career opportunities, although accomplishing it younger definitely stands out. It’s really a personal decision for you to make based on your situation, limitations, and values.
Imposter Syndrome
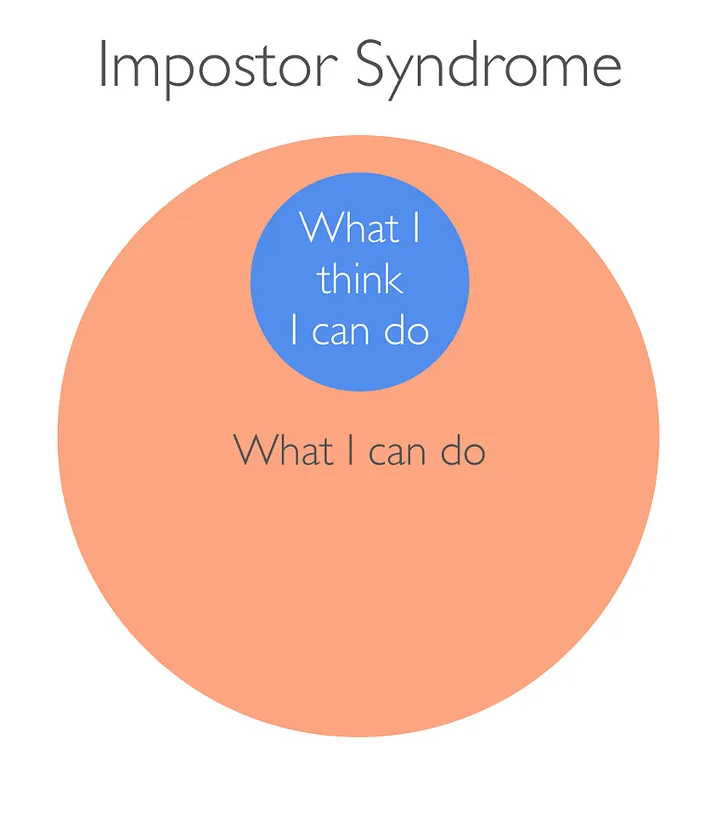
As an update from future me, I would like to briefly mention my struggles with self-esteem following this exam. I set my mind to achieving this certification and diligently spent months preparing for it, but now that I’ve done it, I’ve noticed that I feel even less competent in my own abilities. I’ve continued to learn more and realized just how little I actually know. I’ve convinced myself that I just got lucky in achieving the OSCP and that I didn’t actually earn it.
In the days following the exam, I felt amazing. But in the weeks following the exam, I felt degraded. And honestly, the doors that I thought would open for me just didn’t. I do realize that this is a massive achievement and logically, I truly have developed the mental and technical skills necessary to achieve this, but I also feel the need to work even harder to learn more and prove myself. I put unrealistically high expectations on myself at such a young age and it’s quite overwhelming. It’s like the Dunning-Kruger effect taken to the extreme.
From what I’ve read, imposter syndrome is very common among people in this field, so I take it that I’m not unique in the sense of feeling worse after the OSCP. Despite this, however, I do not regret going for this certification. I’m so glad that I did. I think that imposter syndrome will be a long-term struggle for me going forward.
In honesty, there’ve been times when I thought about quitting because the pressures that I would put on myself would be so extreme. I think that I would face this struggle in any career I enter just due to my personality. Everyone that knows me personally has told me that I will be successful and high-achieving. Somehow, I’ve convinced myself that I am not good/smart enough to accomplish these things and that is really sad. I think that this will get better, though, because I’ve discovered some things that have worked for me in the past. Until then, this has been my experience following the exam.
Next Steps
I’m still deciding on the best ways to allocate my time, but I’m considering doing some combination of these things (subject to change):
- Contributing more to open-source projects
- Creating my own cybersecurity coding projects/tools
- Speaking at a cybersecurity conference
- Strengthening my web application security skills
- Attempt bug bounty hunting
- Expanding my network and looking for more opportunities
- I’m looking to improve both my hard and soft skills while going to high-school full-time. Moving forward, I would like to share more of my journey and hopefully help to strengthen a community of young professionals such as myself.
If you have any questions, my inbox is open. Please reach out to allypetitt@gmail.com. Thanks for reading!