Introduction:
Android has become the industry standard platform for mobile apps, offering a wide range of features and functionalities. The need to fix potential security flaws, however, is growing along with the popularity of Android applications. Parameter manipulation is one such vulnerability, which, if left unchecked, might have dire effects. We will examine the idea of parameter manipulation in Android applications, its ramifications, and mitigation techniques in this blog article.
Understanding Parameter Tampering: A security flaw called parameter tampering, often referred to as data tampering or parameter manipulation, enables an attacker to change the parameters’ values as they are transferred between a client and a server. This vulnerability occurs when input parameters or data transmitted from the client application to the server are not adequately checked or encrypted in the context of Android applications. Attackers may use this flaw to modify data, get around security measures, or obtain access without authorization.
Security hazards and negative outcomes are possible as a result of parameter tampering, and they include:
A. Attackers can alter parameters to get around authentication systems, access restricted resources, or carry out tasks only reserved for privileged users.
B. Data Manipulation: By altering parameters, attackers can manipulate the data sent back and forth between a client and server, compromising data integrity and confidentiality.
C. Financial Loss: Changing the conditions for financial transactions might lead to fraud, unauthorized payments, and fund transfers.
D. Privilege Escalation: By manipulating settings, attackers can increase their level of access within the application, giving them unauthorized control over key features.
POC:-
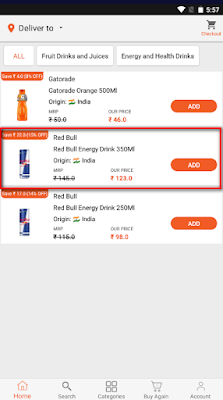
Image 1: Add to cart the product.
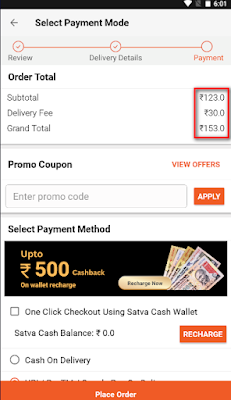
Image 2: The price is 153.
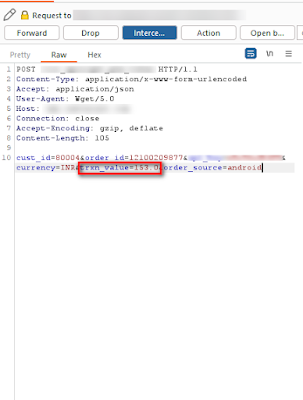
Image 3: Capture the request and you can see the price in the request.
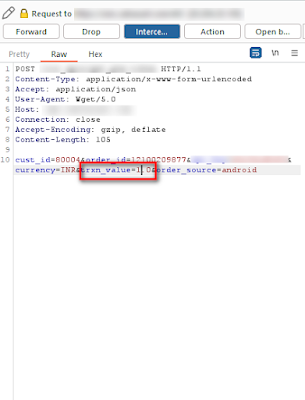
Image 4: Change the price 153 to 1 and forward the request.
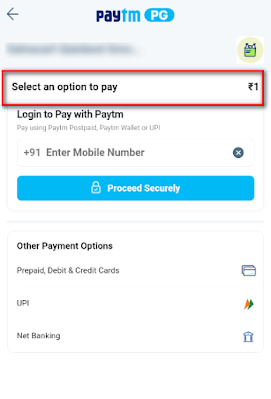
Image 5: The price is successfully changed.
Strategies for Mitigation:
Consider using the following best practices to reduce parameter tampering vulnerabilities in Android applications:
A. Implement stringent input validation and sanitization techniques on both the client and server sides to guarantee that the data being passed is genuine, complies with anticipated formats, and cannot be tampered with.
B. Encryption and Secure Communication: To encrypt data transmission between the client and server, use secure communication protocols like HTTPS. This guarantees that the parameters are private and shielded from prying eyes.
C. Implement strong server-side validation checks to ensure the validity and integrity of the received parameters. c. This involves comparing input parameters to predetermined rules, session data, and user roles.
D. Implement strong session management techniques to make sure that every user session is distinct, securely preserved, and authenticated throughout the application flow.
E. User authorization and access control should be properly enforced to prevent users from tampering with sensitive settings or using unauthorized features.
Disclaimer: This blog post is for informational purposes only. It does not constitute professional advice. Always consult with a qualified security professional before making any changes to your application’s security measures.