Hello Friend 🙂
In the article I’ve provided a clear difference between three popular buzzwords, you’ll always hear in the cybersecurity world. A lot of times people use these interchangeably & confused them.
Vulnerability Assessment, Penetration Testing, and Red Team Engagement are different domains & each domain requires different approaches, mindsets, Tools/techniques & expertise.

Let’s begin.
Vulnerability Assessment
Objective: The primary objective of VA is to find as many vulnerabilities as possible in the target’s systems on the network.
Scope: VA focuses on the identification of vulnerabilities through automated or manual scanning techniques. It aims to provide a comprehensive inventory of vulnerabilities without actively exploiting or validating them & also defensive measures are turned off.
Methodology: Vulnerability assessment relies on scanning tools and techniques to identify known vulnerabilities, misconfigurations, weak security settings, and other security weaknesses.
Depth: VA provides a surface-level analysis of vulnerabilities, typically based on known security issues. It does not involve extensive exploitation or validation of vulnerabilities like penetration testing.
Validation: Vulnerability assessment does not actively validate or exploit vulnerabilities to determine their impact. It focuses more on providing a list of vulnerabilities and their severity for subsequent remediation actions.
Simulation
As an example, if you were to run a vulnerability assessment over a network, you would normally try to scan as many of the hosts as possible, but wouldn’t try exploiting any vulnerabilities at all:
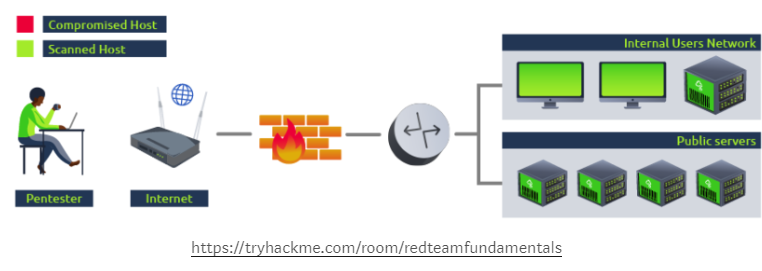
Pros of VA:
- Cost-effective: Vulnerability assessments are generally more cost-effective as they often involve automated scanning tools.
- Compliance requirements: Vulnerability assessments are commonly required by industry regulations and standards, making them essential for meeting compliance obligations.
- Scalability: Vulnerability assessments can be easily scaled to scan large environments and identify vulnerabilities across a wide range of systems and networks.
Cons of VA:
- Limited depth: Vulnerability assessments provide surface-level information about vulnerabilities without validating their exploitability or impact.
- Lack of real-world simulation: Vulnerability assessments do not actively exploit vulnerabilities or simulate real-world attacks, which limits the evaluation of the true severity and potential consequences.
- Dependency on tool accuracy: Vulnerability assessment tools rely on vulnerability databases, and their accuracy can vary, potentially leading to incomplete or inaccurate assessments.
Penetration Testing
Objective: The main objective of penetration testing is to identify and exploit vulnerabilities in a targeted system or network to assess its security controls and determine the potential impact of a successful attack.
Scope: PT focuses on actively simulating real-world attacks, attempting to breach the security defences and gain unauthorized access to systems or sensitive data.
Methodology: Penetration testing employs a variety of tools, techniques, and manual exploitation to identify vulnerabilities, exploit them, and gain access to targeted assets.
Depth: PT involves an in-depth analysis of vulnerabilities, their exploitability, and potential impact. It goes beyond just identifying vulnerabilities and aims to assess the resilience of the organization’s defences.
Validation: Penetration testing validates the effectiveness of security controls by attempting to breach them, providing insights into the system’s actual security posture and potential risks.
Simulation
If we were to perform a penetration test using the same example network as before, on top of scanning all of the hosts on the network for vulnerabilities we would try to confirm if they can be exploited to show the impact an attacker could have on the network:
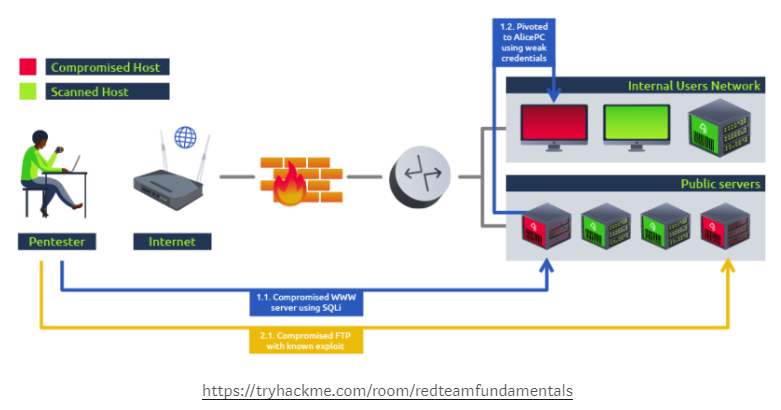
By analyzing how an attacker could move around our network, we also gain basic insight into possible security measure bypasses and our ability to detect a real threat actor to a certain extent.
Pros of PT:
- Specific Vulnerability Focus: PT allows for a targeted approach, focusing on identifying and exploiting specific vulnerabilities to assess their impact on the system or network.
- Detailed Analysis: PT involves an in-depth analysis of vulnerabilities, their exploitability, and potential consequences, providing detailed insights into the security weaknesses of the system or network.
- Customization: PT can be tailored to the specific requirements of the organization, allowing for a more customized assessment that aligns with their unique environment, systems, and business objective
Cons of PT:
- Penetration tests are LOUD: Usually, pen-testers won’t put much effort into trying to go undetected. Unlike real attackers, they don’t mind being easy to detect, as they have been contracted to find as many vulnerabilities as they can in as many hosts as possible.
- Non-technical attack vectors might be overlooked: Attacks based on social engineering or physical intrusions are usually not included in what is tested.
- Relaxation of security mechanisms: While doing a regular pentest, some security mechanisms might be temporarily disabled or relaxed for the pen testing team in favour of efficiency as it is essential to remember that pen testers have limited time to check the network.
Red Team Engagement
Objective: The objective of a red team engagement is to simulate realistic attack scenarios, testing an organization’s overall security controls, including people, processes, and technology. It aims to identify weaknesses that may not be detected by traditional security measures.
Scope: RTE goes beyond vulnerability assessment and penetration testing by emulating real-world attackers’ tactics, techniques, and procedures (TTPs). It assesses the organization’s ability to detect, respond, and recover from advanced and sophisticated attacks.
Methodology: Red team engagements involve a combination of social engineering, physical security testing, network penetration testing, application testing, and other techniques to challenge the organization’s security defences holistically.
Depth: RTE provides a comprehensive and holistic assessment, exploring various attack vectors and exploiting vulnerabilities to test the organization’s resilience against sophisticated attacks.
Validation: Red team engagements validate the effectiveness of an organization’s security controls by attempting to breach them using advanced attack simulations. It helps uncover potential security gaps and provides actionable recommendations for improvement.
Simulation
Taking the same network as before, on a red team engagement where the goal is to compromise the intranet server, we would plan for a way to reach our objective while interacting as little as possible with other hosts. Meanwhile, the blue team’s capacity to detect and respond accordingly to the attack can be evaluated:
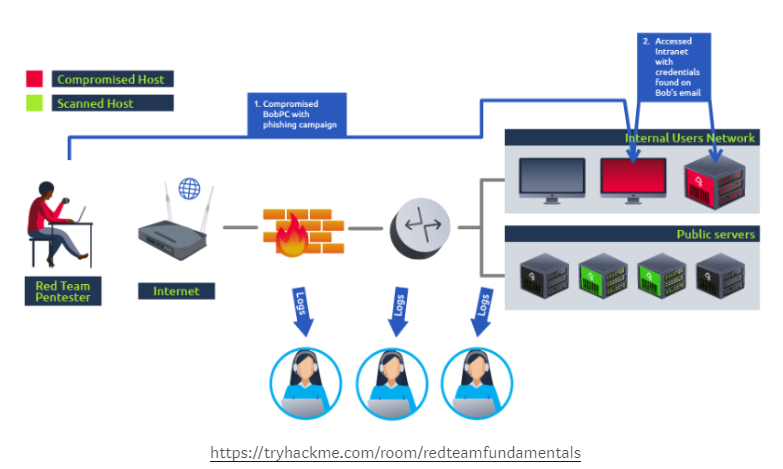
On an RTE, not all of the hosts on a network will be checked for vulnerabilities (like in VA or PT). A real attacker would only need to find a single path to its goal and is not interested in performing noisy scans that the blue team could detect
Pros of RTE:
- Holistic Assessment: RTE provides a comprehensive assessment of an organization’s overall security defences, including people, processes, and technology, by simulating realistic attack scenarios.
- Detection and Response Evaluation: RTE helps evaluate an organization’s ability to detect, respond, and recover from sophisticated attacks, uncovering potential blind spots and weaknesses in the incident response capabilities.
- Realistic Simulation: RTE mimics the tactics, techniques, and procedures (TTPs) of real-world attackers, providing a more realistic assessment of the organization’s security resilience.
Cons of RTE:
- Extensive Resources Required: RTE typically requires significant time, expertise, and resources to plan, execute, and analyze. It may involve a more extensive scope and a higher cost compared to PT.
- Disruption Risk: The realistic attack simulations carried out during RTE pose a greater risk of unintended disruptions, impacting critical systems, networks, or operations.
- Limited Frequency: Due to the resource-intensive nature of RTE, it may not be feasible to conduct it frequently, limiting the ability to assess the evolving security posture over time.
In summary, while vulnerability assessment focuses on identifying and prioritizing vulnerabilities, penetration testing involves actively exploiting vulnerabilities to assess their impact. Red team engagements simulate realistic attack scenarios, testing the organization’s overall security defences and response capabilities. Each approach serves a different purpose and provides a varying depth of analysis and validation.
That’s it, Hope you’ve learned something new 🙂
if want to support us with coffee then ping us here
Question or any suggestion for a new Topic? Ping me on my socials