
⭕ Introduction:
Nmap which stands for network mapper is a network security tool. Nmap is a wonderful port scanner.
- Nmap can provide further info about targets like reverse DNS names and device types and Mac addr.
- Nmap can provide info about the operating system of the host and the version of services running on the ports
- You can also use nse (Nmap scripting engine) for further exploitation.
🎯History :
- Nmap’s first release had only 2000 lines of code.
- At the time of its release, Nmap didn’t have many features, at that time Nmap was only designed only to scan open ports on the target machine.
- AT first release Nmap only worked for Linux and was compiled with GCC.
- After only 4 days a stable version was released - 1.25 and it become very famous and came in high demand for a high-performance port scanner.
- After March 1998, after the initial release, the scanner had become the de facto port scanner of the underground hacker community and the blossoming infosec industry.
- By Sep 2003 Nmap 3.45 was released, now Nmap was able to detect services, operating systems, and features such as timing configuration and optimization flags.
- In Dec 2006 Nmap has the most wonderful feature NSE (Nmap scripting engine). The NSE allows users of Nmap to write their modules to trigger on certain ports being open, or certain services - or even specific versions of services.
👩🏭 Uses of NMAP:
- SYS admin uses it for system checking and network checking.
- Because of its ability to change the timing, as well as setting flags of different packets, developers use it in testing embedded network stacks.
- Students and computer engineers use it for daily use.
- Generating traffic to hosts on a network, response analysis, and response time measurement.
- DNS queries and subdomain search
⚔ Port scanning:
Nmap is a port scanner. BUT What is exactly a port?
A Port is a way to access a networked service on a computer. Each computer has 65535 ports which can be closed , open and filtered or unfiltered.
🔥 There are 1024 reserved ports out there.
It is important to note; however, that especially in a CTF setting, it is not unheard of for even these standard ports to be altered, making it even more imperative that we perform appropriate enumeration on the target.
📌 Target specification :
⚡ Scan a single target :
nmap[target]
#nmap 192.168.79.1
⚡ Scan multiple targets:
nmap[target1,target2]
#nmap 192.168.89.4, 192.168.89.7
⚡ Scan from a file:-iL
nmap -iL filename
nmap -iL ~/Downloads/targets.txt
⚡ Scan a range of hosts :
Scan a Range of Hosts
#nmap 192.168.0.1-10
⚡ Scans an entire subnet :
nmap [ip address/cdir]
nmap 192.168.0.1/24
⚡ Scan random hosts : iR
nmap -iR [number]
nmap -iR 0
⚡ Excluding Targets from a Scan: --exclude
nmap [targets] – exclude [targets]
nmap 192.168.0.1/24 –exclude 192.168.0.100, 192.168.0.200
⚡ Excluding Targets from a list --excludefile :
nmap [targets] – excludefile [list.txt]
nmap 192.168.0.1/24 –excludefile notargets.txt
📌Host discovery :
⚡ No port scan: -sn
Nmap uses a ping scan -sn to scan the hosts.
ARP Requests are being sent by the Nmap if scanning a local network.
nmap -sn 192.168.1.0/24 --packet-trace
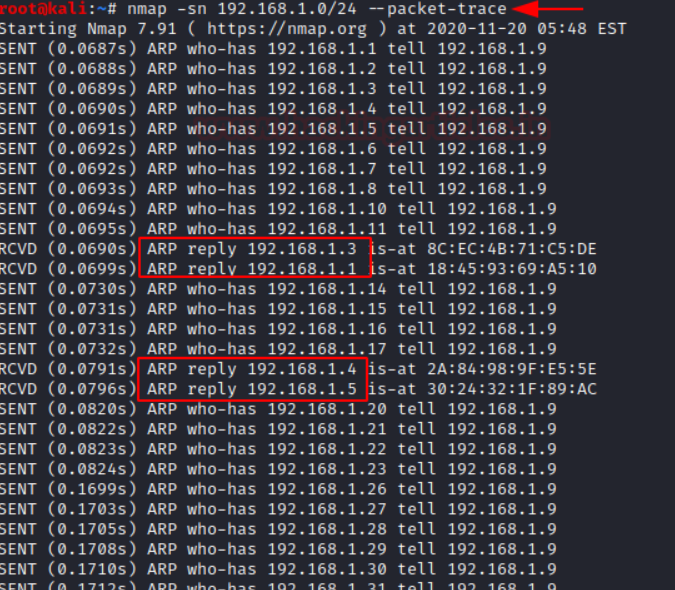
Effects are done using scan by different users outside the network and also when you disable arp-ping by –disable-arp-ping.
- sudo (administrator): When Nmap is run by sudo by the privileged user to scan an outside network, then Nmap uses ICMP echo requests, TCP ACK (Acknowledge) to port 80, TCP SYN (Synchronize) to port 443, and ICMP timestamp request.
sudo nmap [target]
sudo nmap 198.267.82.34
🔥 ICMP is a network-level protocol. ICMP messages communicate information about network connectivity issues back to the source of the compromised transmission. It sends control messages such as destination network unreachable, or source route failed.
- local user: When an unprivileged user tries to scan targets outside the local network, Nmap resorts to a TCP 3-way handshake by sending SYN packets to ports 80 and 443.
nmap [target]
nmap 198.267.82.34
⚡ Don’t ping: -PN
This Nmap scan skips the host discovery stage. As named it doesn’t ping the device. It takes the device active and performs a port scan on the device.
nmap -PN [target]
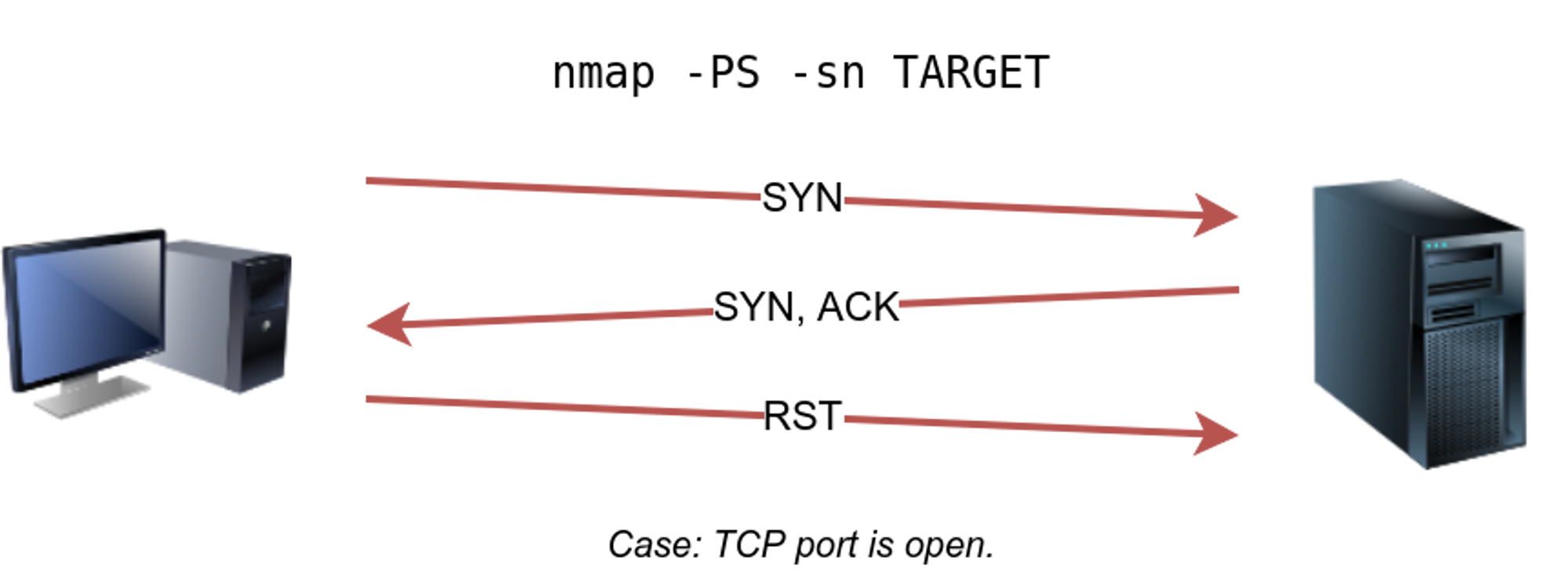
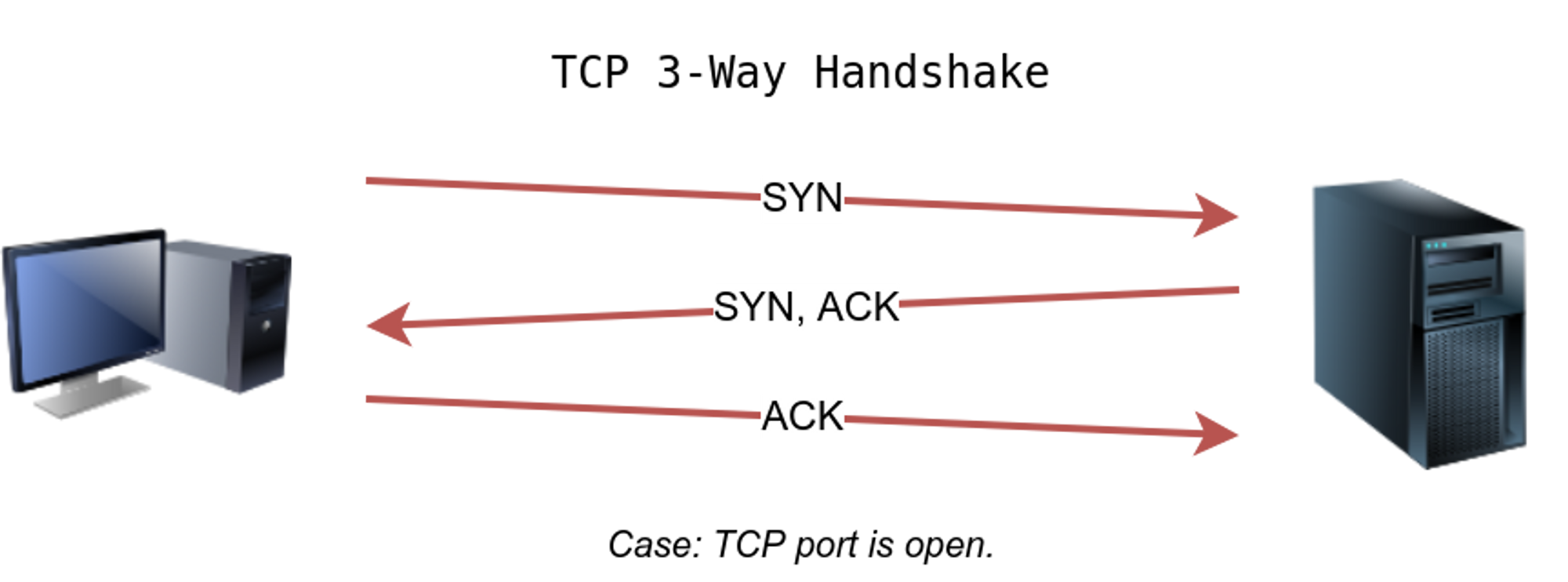
⚡ TCP SYN ping: -PS
In TCP syn scan we send a SYN (synchronize) packet to the victim, if the victim replies with the SYN/ACK then the host is up and if not it will respond with a RST (reset).
If the port is closed a packet with a rst flag is received directly.
🔥 You can also give the port number to scan like: -PS80,443,8080
🔥 Sudoers even don’t need to complete the 3-way handshake as they know the port is up they can send a RST packet.
![]()
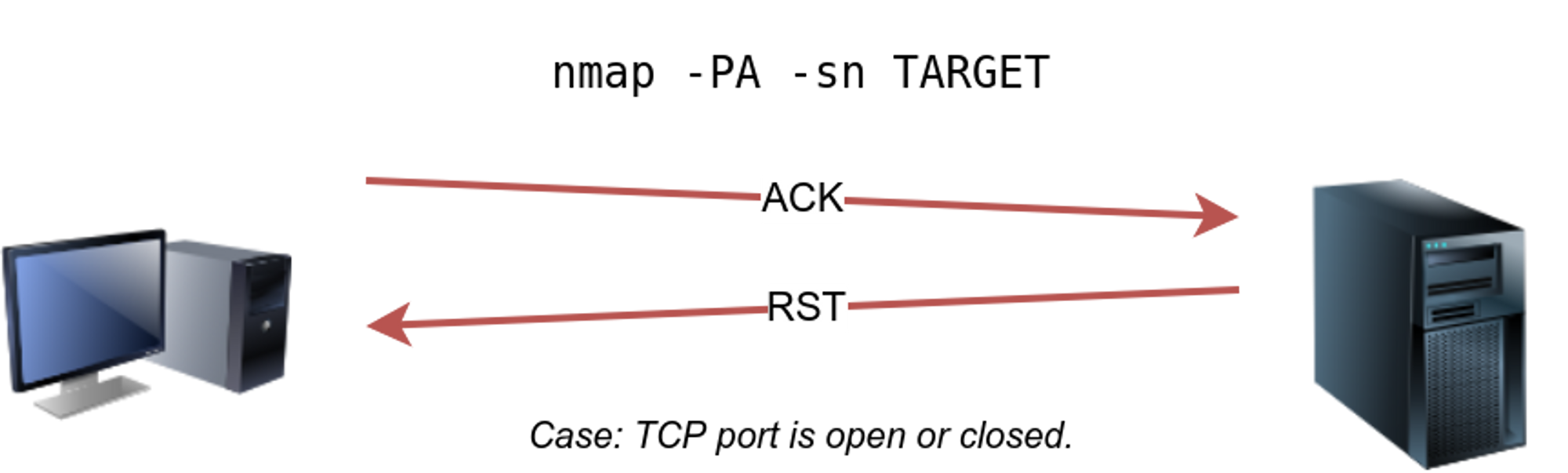
⚡ TCP ACK ping : -PA
This sends a packet with ACK flag set. You need to be root to use this, if you are not nmap will complete 3-way handshake.
Nothing is received if port is closed.
🔥 We can use TCP ACK scan with -PA
⚡ UDP Ping : - PU
In case of UDP as we there is no acknowledgment that data is recieved or not , so while sending the UDP packet , if the port will be closed it will give a ICMP port unreachable packet, if we do not get the ICMP port then the port is reachable and alive.
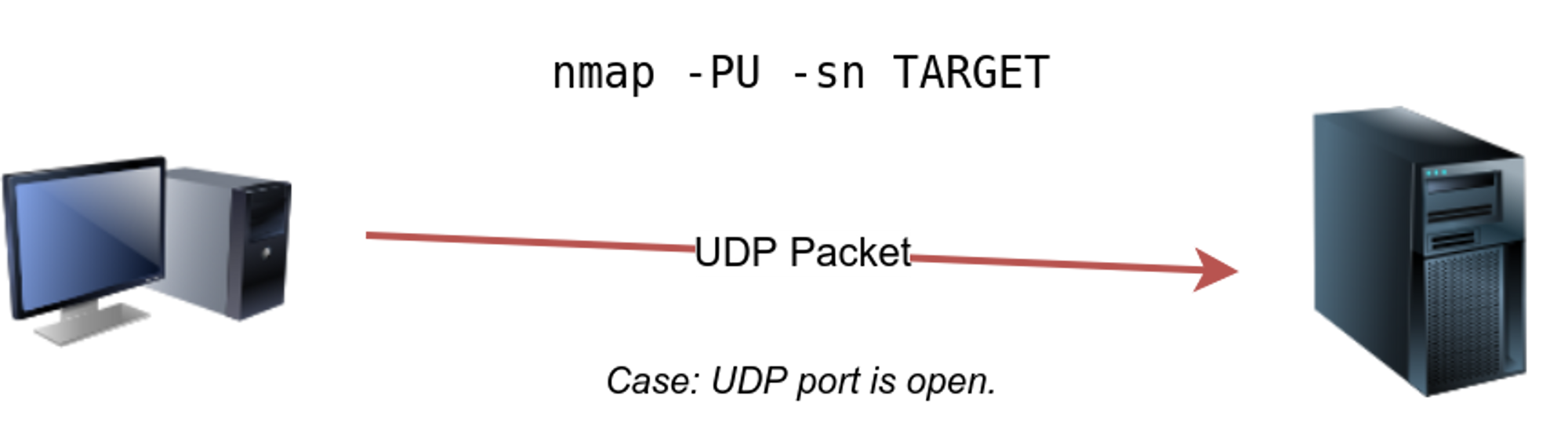
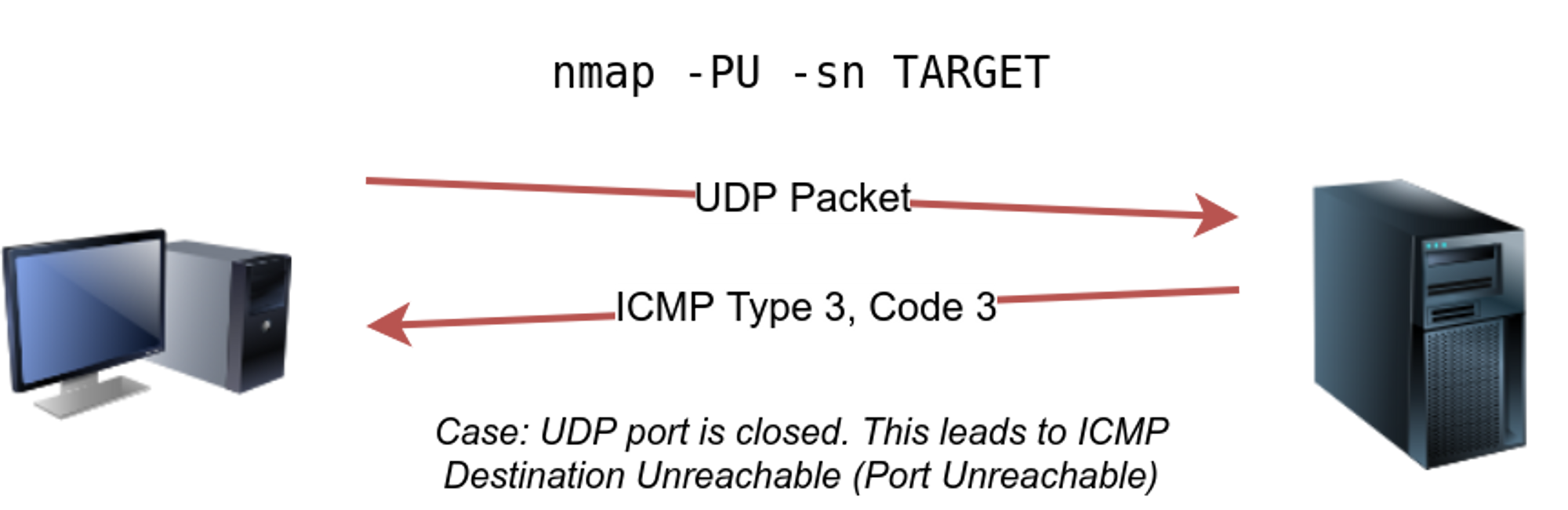
⚡ Arp Scan : -Pr
Arp : ARP is the Address Resolution Protocol, used to translate between Layer 2 MAC addresses and Layer 3 IP addresses.
Arp scan is only possible if you are on the same local network as the target. As when arp scan is used, the operating system sends the arp query to get all the mac address in case of a subnet, and if the target replies to the arp query ,then the host is up.
🔥 We use -PR argument with the Nmap scan
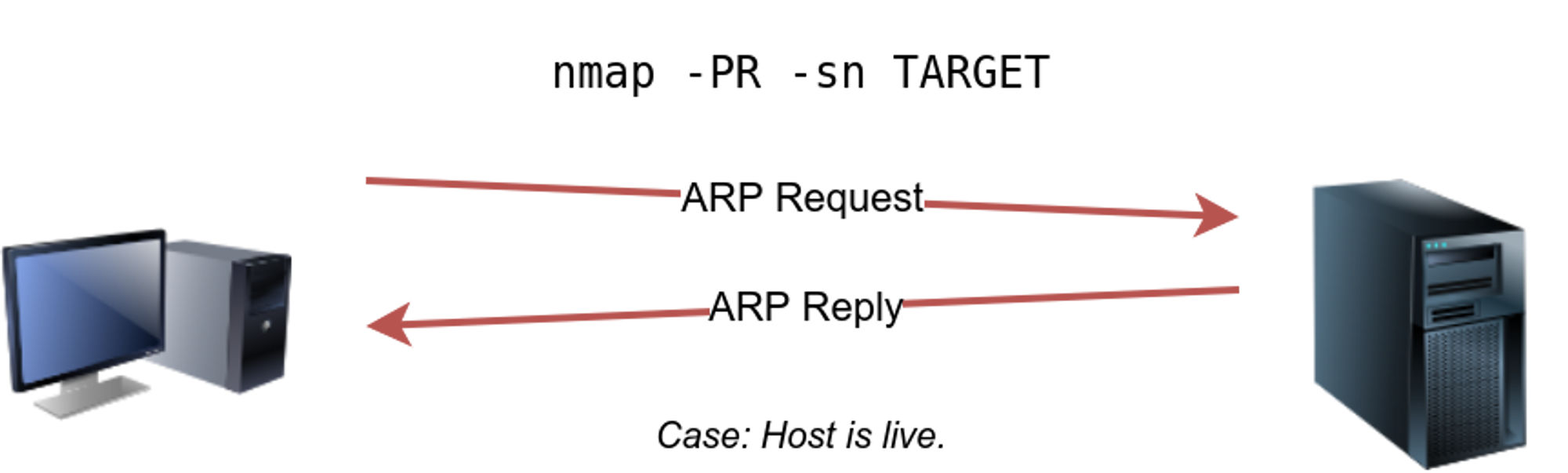

nmap -Pr [target]
⚡ ICMP scan: -PE, -PP,-PM [mainly blocked by firewalls]
In this we ping every IP address in the subnet, whoever replies the host is up.
ping request: ICMP Type 8/echo
ping reply: ICMP Type 0
Though there is an issue with this scan, It is blocked by the firewalls.
nmap -PE [target]
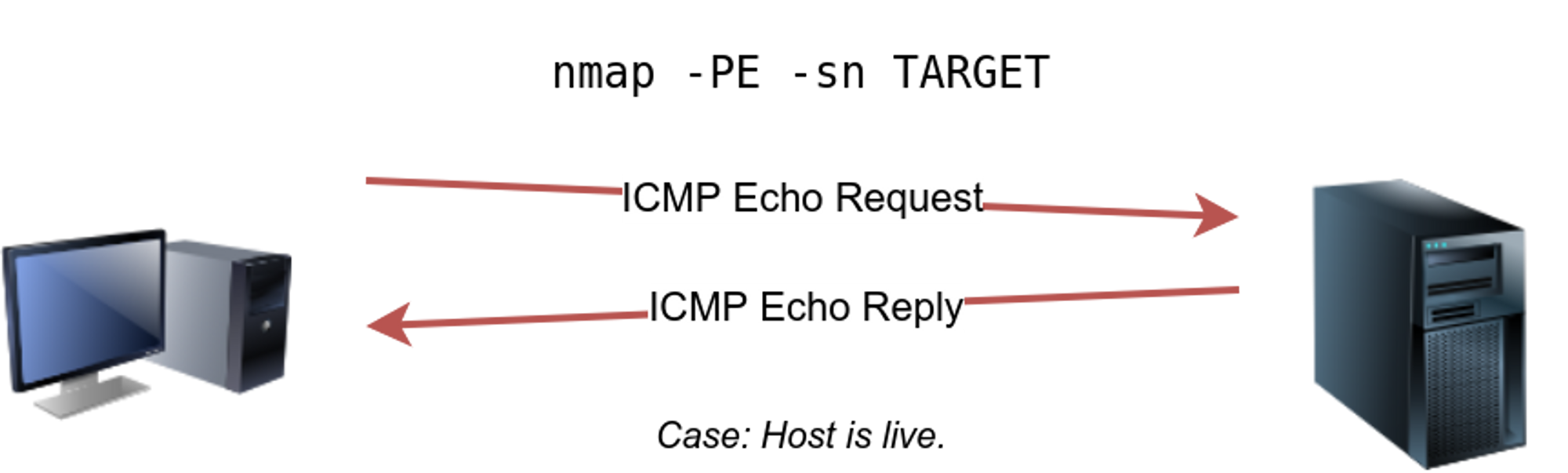
As the ICMP type 8 tends to be blocked we can also use ICMP timestamp to check if a host is up or not.
ICMP timestamp request: ICMP TYPE 13
ICMP timestamp reply: ICMP TYPE 14
🔥 ICMP timestamp is used by -PP
nmap -PP [target]
Similarly, we can also use Address mask queries (ICMP Type 17 ) and check whether it gets an address mask reply (ICMP Type 18).
🔥 ICMP Address mask is used by: -PM
nmap -PM [target]
⚡ Traceroute: If you want Nmap to find the routers between you and the target, just add --traceroute.
Works slightly differently than tracert and trancert in another os, here starts with a packet of low TTL (Time to Live) and keeps increasing until it reaches the target. Nmap’s traceroute starts with a packet of high TTL and keeps decreasing it.
sudo nmap -sS --traceroute MACHINE_IP
🔥 Tip : If you want to scan only host is up or not use -sn. It will not cause to scan the ports
⚡ Reverse-DNS Lockup:
Nmap’s default behavior is to use reverse-DNS, online hosts. Because the hostnames can reveal a lot, this can be a helpful step. However, if you don’t want to send such DNS queries, you use -n to skip this step.
By default, Nmap will look up online hosts; however, you can use the option -R to query the DNS server even for offline hosts. [gives domain from IP address]
📌Port Specification :
⚡ port specify : -p
nmap -p [port] [target]
eg: nmap -p 89 192.168.2.45
how to ask to scan all ports?
nmap -p-
how to give a range of ports?
nmap -p 1-10 , nmap -p 67,989,65
⚡ port exclusion: --exclude-ports
nmap--exclude-ports <port ranges> 🔥
nmap --exclude-ports 1-100
⚡ Fast mode - Scan fewer ports than the default scan: -F
nmap -F [target]
nmap -F 192.178.67.90
⚡ Scan ports consecutively - don’t randomize -r
nmap -r [target]
nmap -r 192.89.27.251
⚡ Top ports: --top-ports
nmap --top-ports [target]
nmap --top-ports 192.168.29.90
Service/Version Detection :
⚡ Determine service and version on the open ports -sV
nmap -sV [port] [target]
nmap -sV -p 22 192.168.22.90
⚡ Version intensity :
You can set the intensity or how much verbose you want the result.
nmap -sV --version-intensity [1-9] [port] [target]: 9: most verbose
nmap -sV --version-intensity 8 -p- 192.168.23.45
🔥 --version-trace: Show detailed version scan activity (for debugging)
Operating system detection :
⚡ Helps in detection of operating system running on the target
nmap -O [target]
nmap -O 192.134.56.76
Timing and Performance :
⚡ Timing templete:
nmap -T<0-5> 🔥 [target] #the higher the faster
nmap -T5 192.168.22.34
⚡ Packet speed:
nmap --min-rate <number> 🔥 # Send packets no slower than <number> 🔥 per second
nmap --max-rate <number> 🔥 # Send packets no faster than <number> 🔥 per second
⚡ Parallelism:
Nmap probes the targets to discover which hosts are live and which ports are open; probing parallelization specifies the number of such probes that can be run in parallel.
nmap --min-parallelism
nmap --max-parallelism
📌 Scan Types
TCP AND UDP :
🔥 A port is usually linked to a service using that specific port number.
Conditions/ States of a port:
- Open: indicates that a service is listening on the specified port.
- Closed: indicates that no service is listening on the specified port, although the port is accessible. By accessible, we mean that it is reachable and is not blocked by a firewall or other security appliances/programs.
- Filtered: means that Nmap cannot determine if the port is open or closed because the port is not accessible. This state is usually due to a firewall preventing Nmap from reaching that port. Nmap’s packets may be blocked from reaching the port; alternatively, the responses are blocked from reaching Nmap’s host.
- Unfiltered: means that Nmap cannot determine if the port is open or closed, although the port is accessible. This state is encountered when using an ACK scan -sA.
- Open|Filtered: This means that Nmap cannot determine whether the port is open or filtered.
- . Closed|Filtered: This means that Nmap cannot decide whether a port is closed or filtered.
TCP Scans
⚡ Flags of TCP
- URG: Urgent flag indicates that the urgent pointer filed is significant. The urgent pointer indicates that the incoming data is urgent, and that a TCP segment with the URG flag set is processed immediately without consideration of having to wait on previously sent TCP segments.
- ACK: Acknowledgement flag indicates that the acknowledgement number is significant. It is used to acknowledge the receipt of a TCP segment.
- PSH: Push flag asking TCP to pass the data to the application promptly.
- RST: Reset flag is used to reset the connection. Another device, such as a firewall, might send it to tear a TCP connection. This flag is also used when data is sent to a host and there is no service on the receiving end to answer.
- SYN: Synchronize flag is used to initiate a TCP 3-way handshake and synchronize sequence numbers with the other host. The sequence number should be set randomly during TCP connection establishment.
- FIN: The sender has no more data to send.
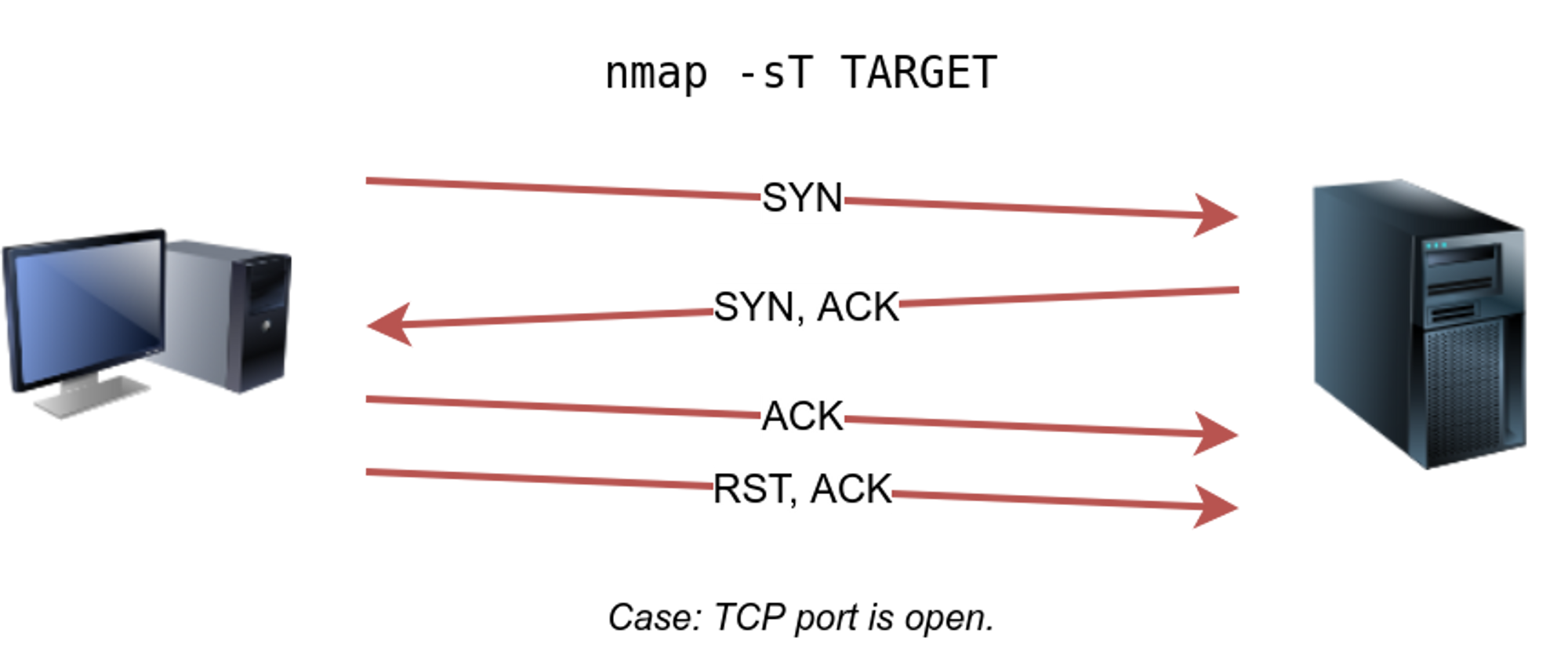
⚡ Tcp Connect -sT
In this a Tcp packet is sent with the SYN flag. If the port is open 3-way handshake takes place. In this in case of a TCP connect we do not form a tcp connection like the other two scans as soon as we know the port is open we instantly sends a packet with flag RST/ACK set and it closes the connection instantly. You need to be root to run it
🔥 We use -sTto perform TCP connect scan.
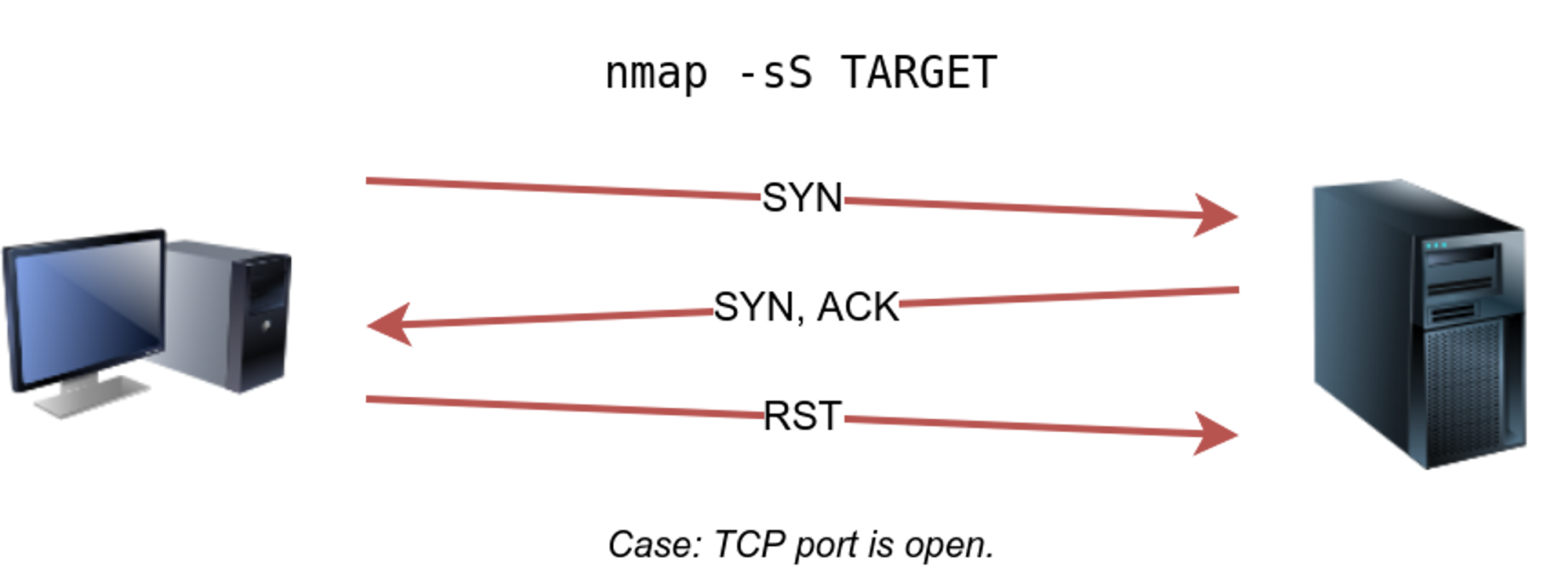
⚡ TCP SYN SCAN [Stealth scan] : -sS
SYN scan does not need to complete the TCP 3-way handshake; instead, it tears down the connection once it receives a response from the server. Because we didn’t establish a TCP connection, this decreases the chances of the scan being logged.
🔥 We use -sS to use tcp syn scan.
⚡ TCP ACK SCAN : -sA
An ACK scan will send a TCP packet with the ACK flag set. The target would respond to the ACK with RST regardless of the state of the port. REQUIRES ROOT
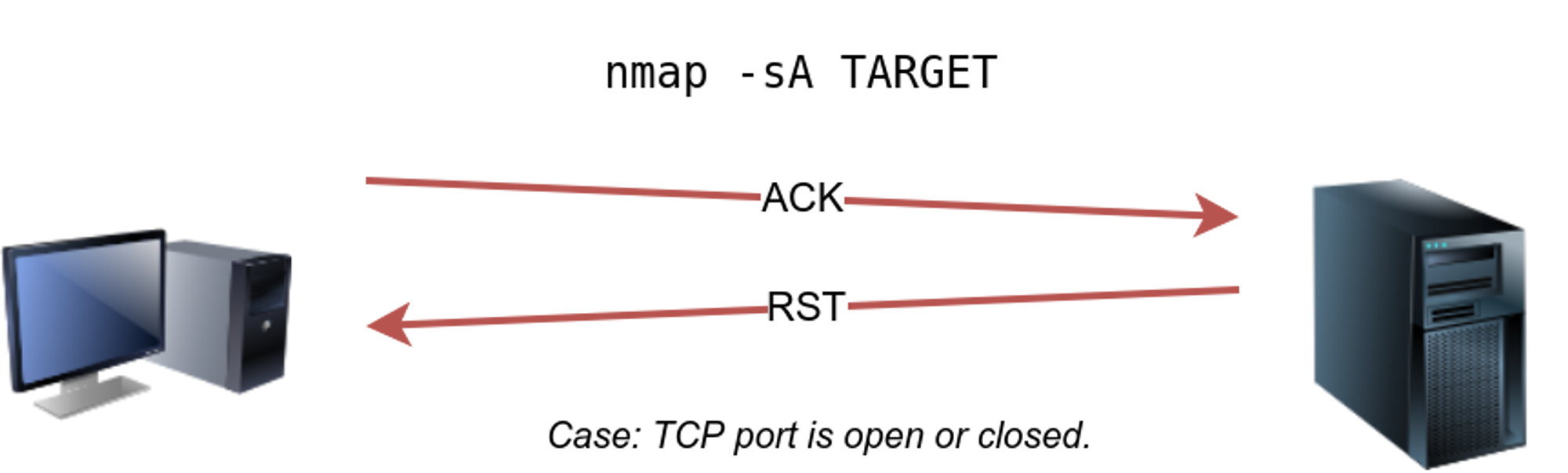
🔥 This kind of scan would be helpful if there is a firewall in front of the target. Consequently, based on which ACK packets resulted in responses, you will learn which ports were not blocked by the firewall. In other words, this type of scan is more suitable to discover firewall rule sets and configuration.
⚡ TCP window scan : -sW
The TCP window scan is almost the same as the ACK scan; however, it examines the TCP Window field of the RST packets returned. On specific systems, this can reveal that the port is open.
🔥 This can be used by -sW
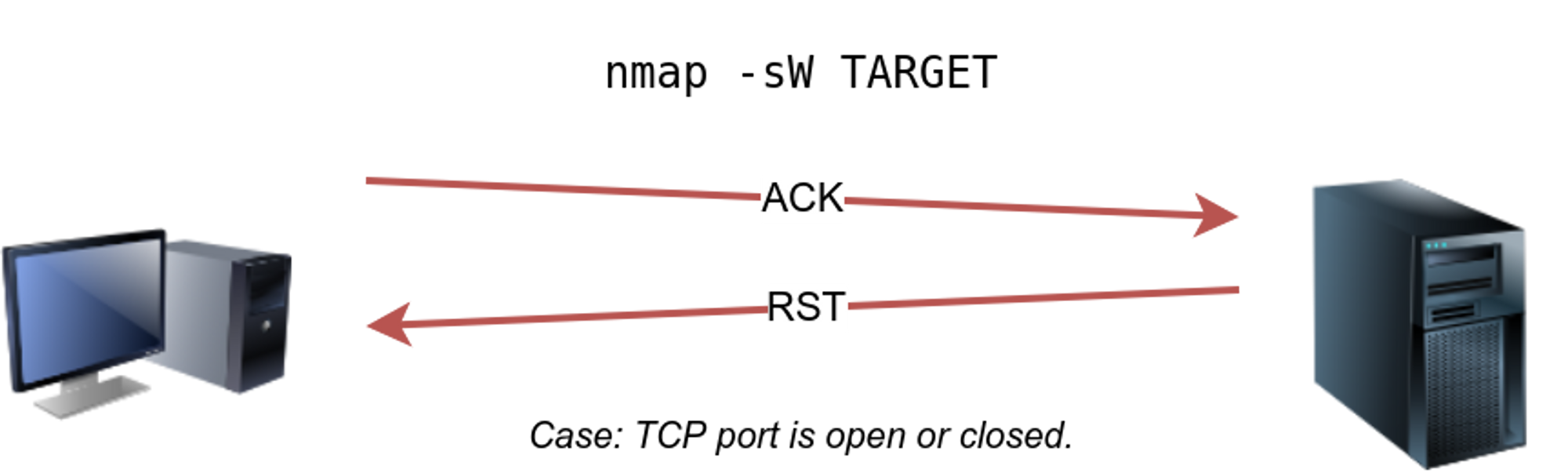
🔥 if we repeat our TCP window scan against a server behind a firewall, we expect to get more satisfying result
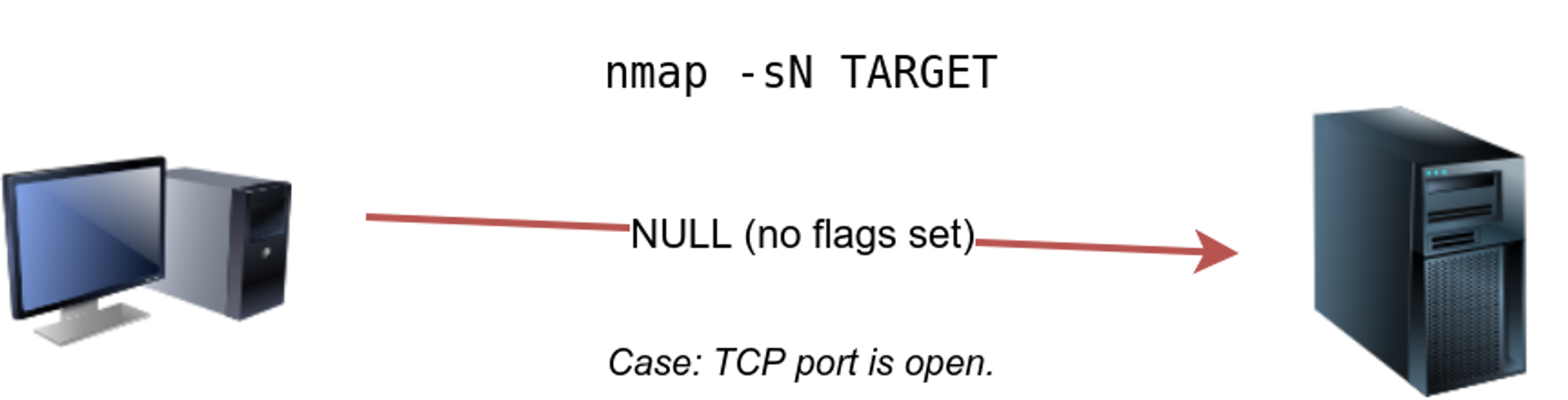
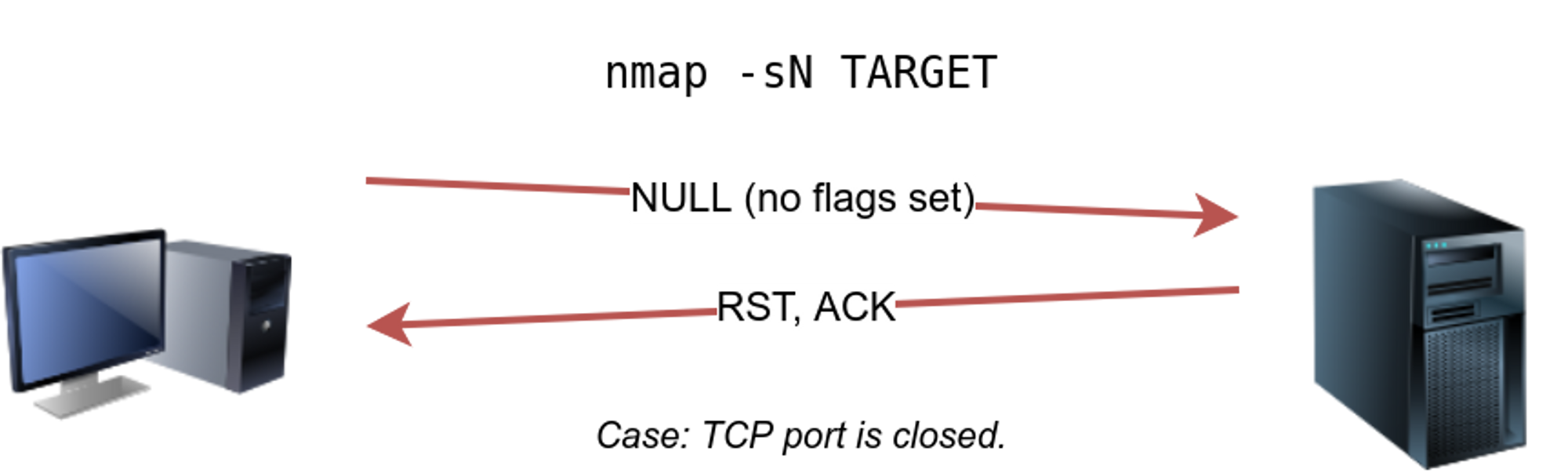
⚡ TCP NULL Scan : -sN
The null scan does not set any flag. A TCP packet with no flags set will not trigger any response when it reaches an open port so it will presume the port is filtered | open . But it will give a rst packet if the port is closed. REQUIRES ROOT
🔥 Null scan is used by -sN
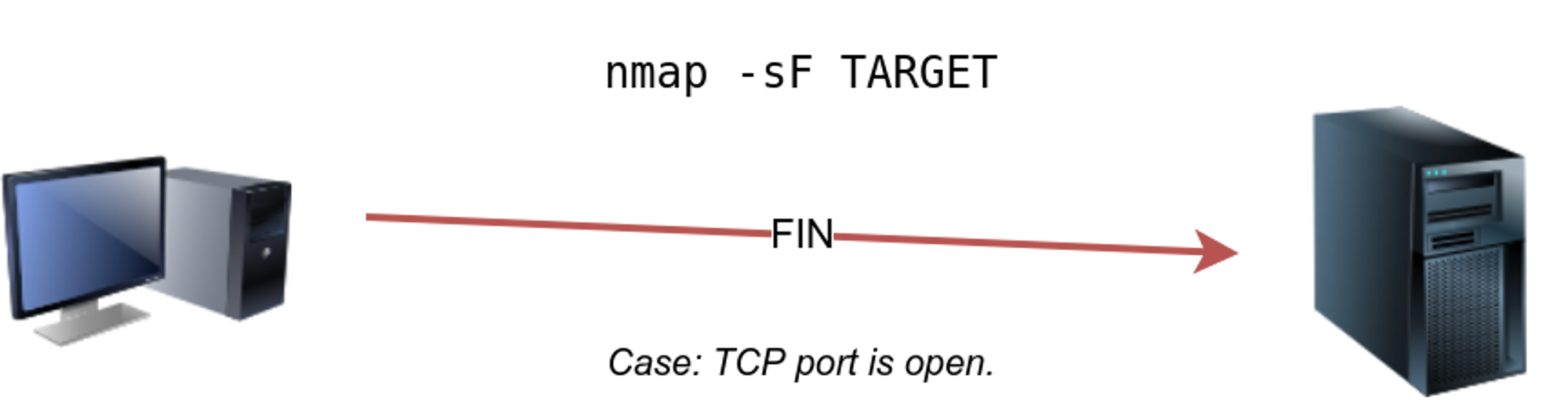
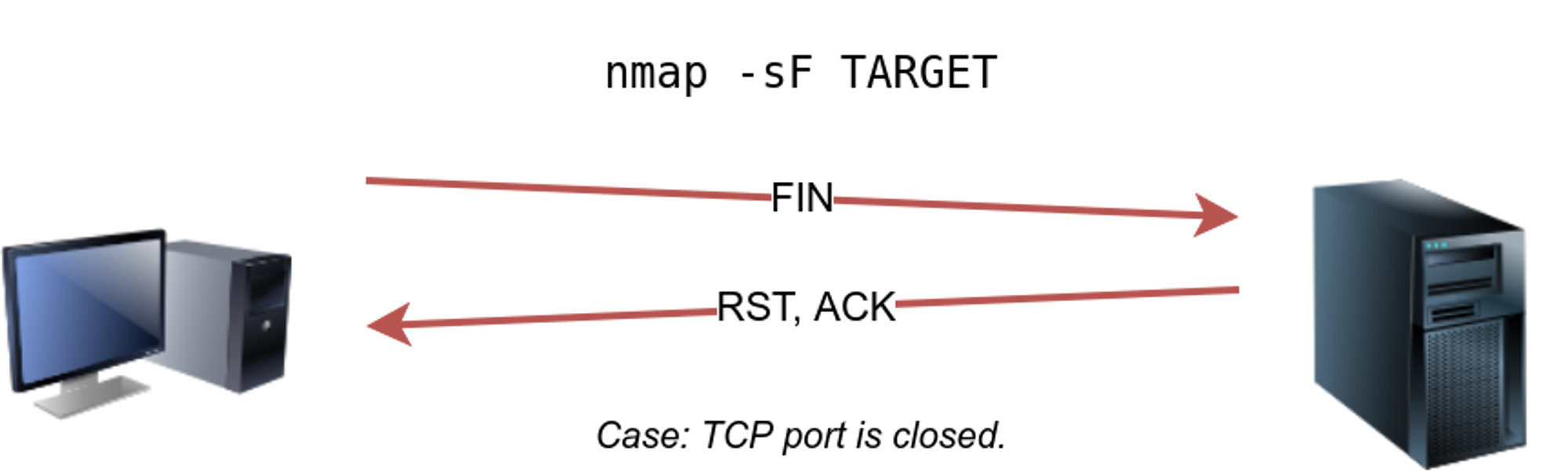
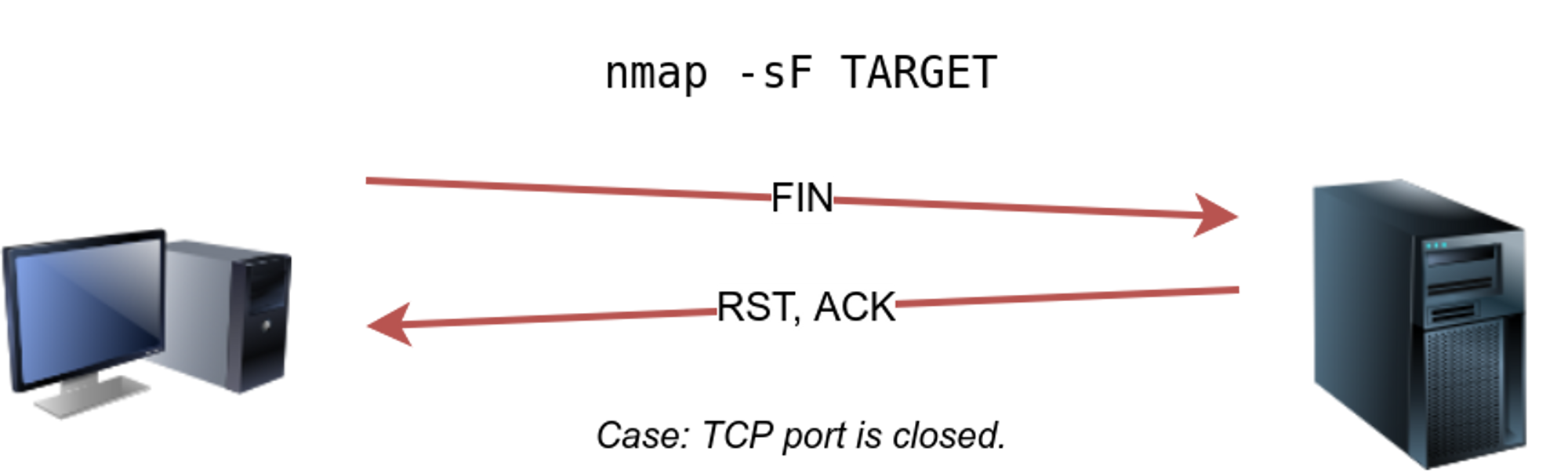
⚡ TCP FIN SCAN : -sF
The FIN scan sends a TCP packet with the FIN flag set. No response will be sent if the TCP port is open. Again, Nmap cannot be sure if the port is open or if a firewall is blocking the traffic related to this TCP port. But if the port is closed it gives out a RST packet. REQUIRES ROOT
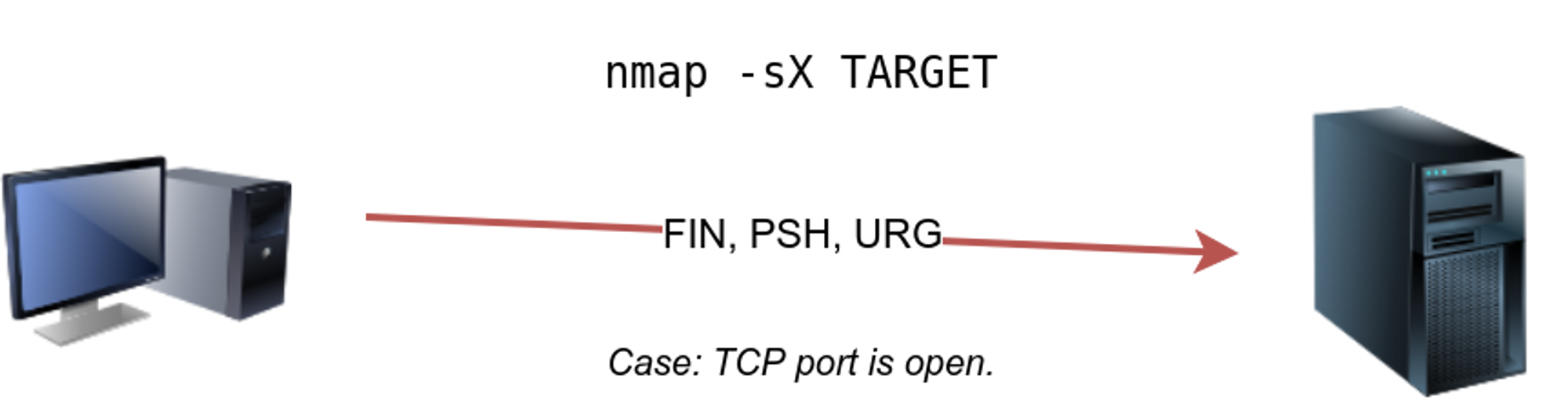
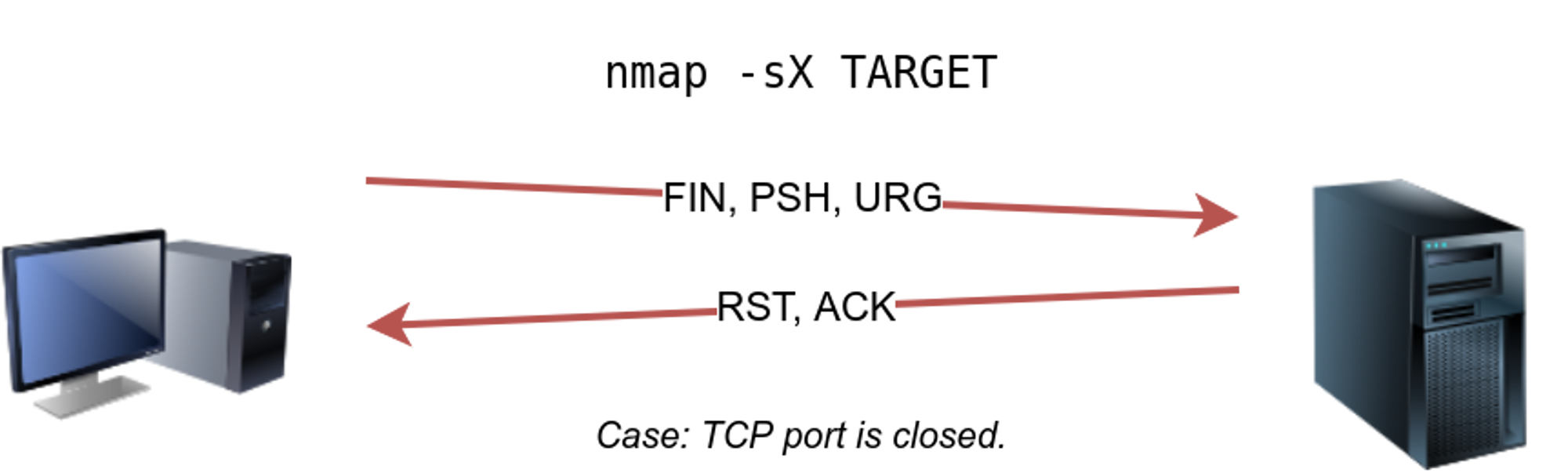
⚡ TCP XMAS Scan : -sX
In Xmas scan packet is sent with flags FIN ,URG ,PSH set in it . Like others it also receive a rst if the port is blocked . Otherwise, it will be reported as open|filtered.
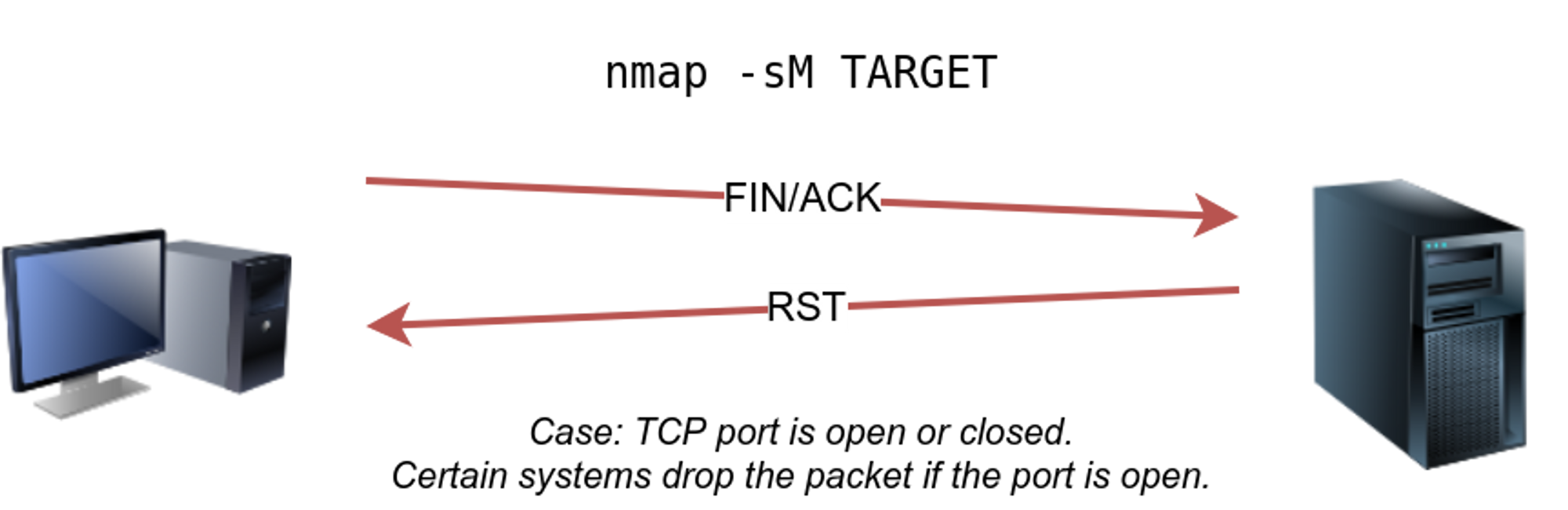
⚡ Maimon Scans : -sM
In this scan, the FIN and ACK bits are set. The target should send an RST packet as a response. Most target systems respond with an RST packet regardless of whether the TCP port is open. REQUIRES ROOT
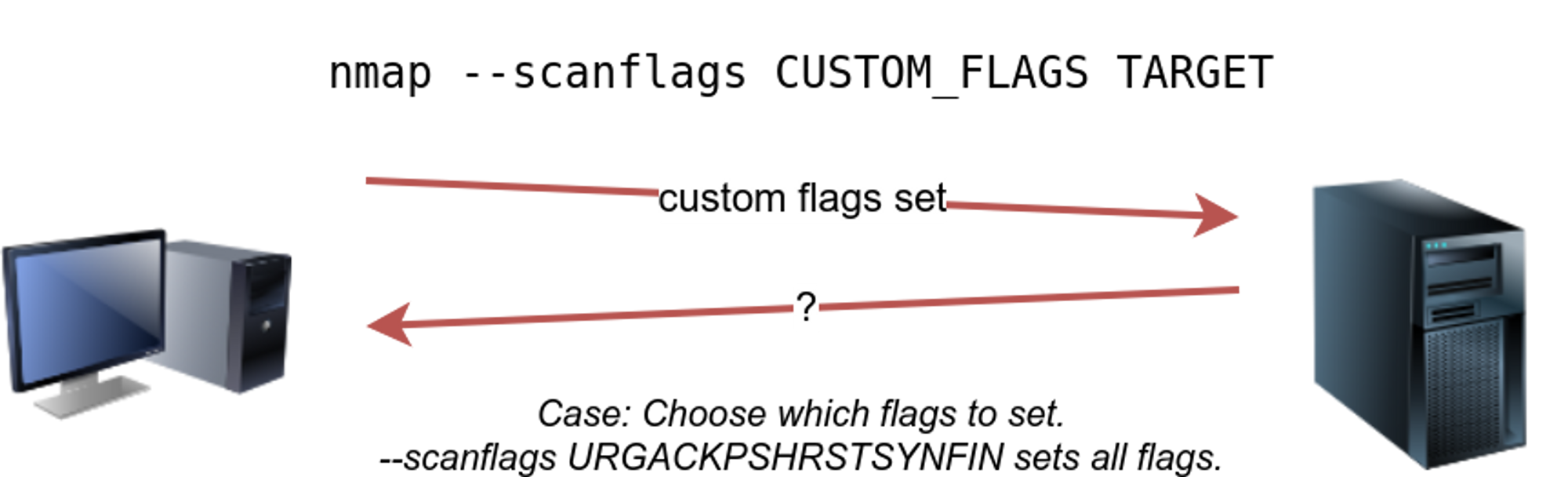
⚡ Custom scan
If you want to experiment with a new TCP flag combination beyond the built-in TCP scan types, you can do so using --scanflags <custom flag> 🔥.
📌 UDP SCANS -sU
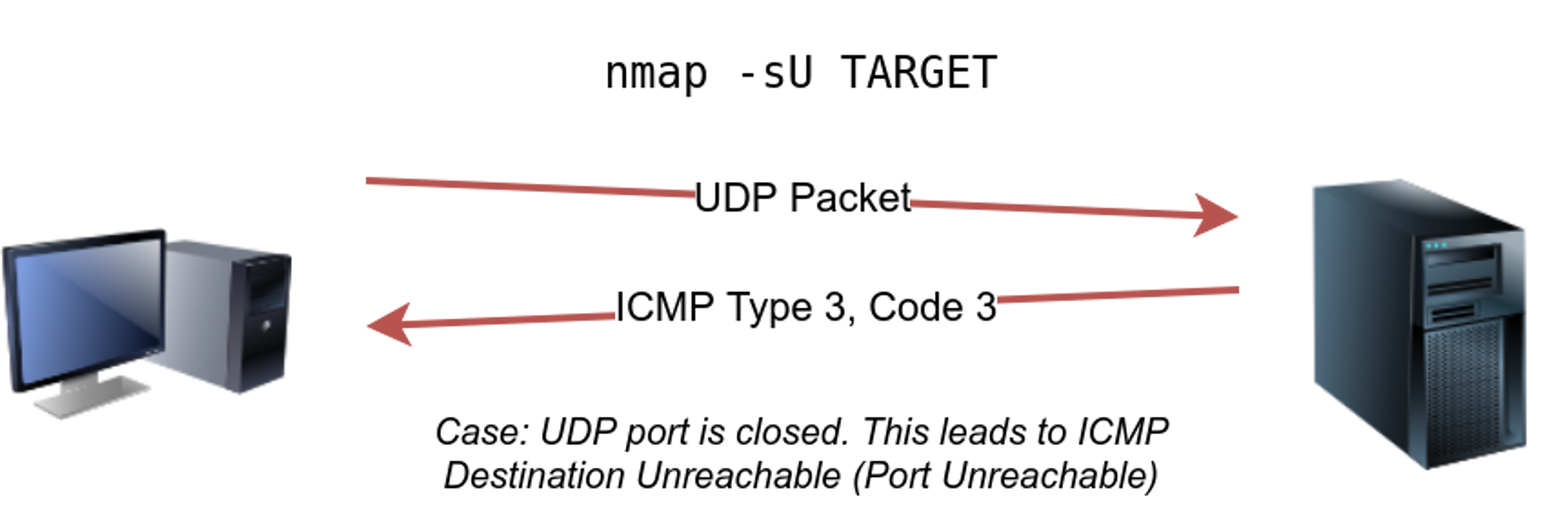
If a UDP packet is sent to a closed port, an ICMP port unreachable error (type 3, code 3) is returned.
🔥WE use -sU to do udp scan.
🧟♀️ Zombie /IDLE scan -sl
It requires a idle system on the same subnet and you can communicate with. Nmap makes it appear that every packet is coming from that host(zombie) then it will check for indicators whether the idle (zombie) host received any response.
The idle (zombie) scan requires the following three steps to discover whether a port is open:
- Trigger the idle host to respond so that you can record the current IP ID on the idle host.
- Send a SYN packet to a TCP port on the target. The packet should be spoofed to appear as if it was coming from the idle host (zombie) IP address.
- Trigger the idle machine again to respond so that you can compare the new IP ID with the one received earlier.
Attacker made a syn/ack packet and zombie replied with a rst and we got the ip id of the zombie ip.
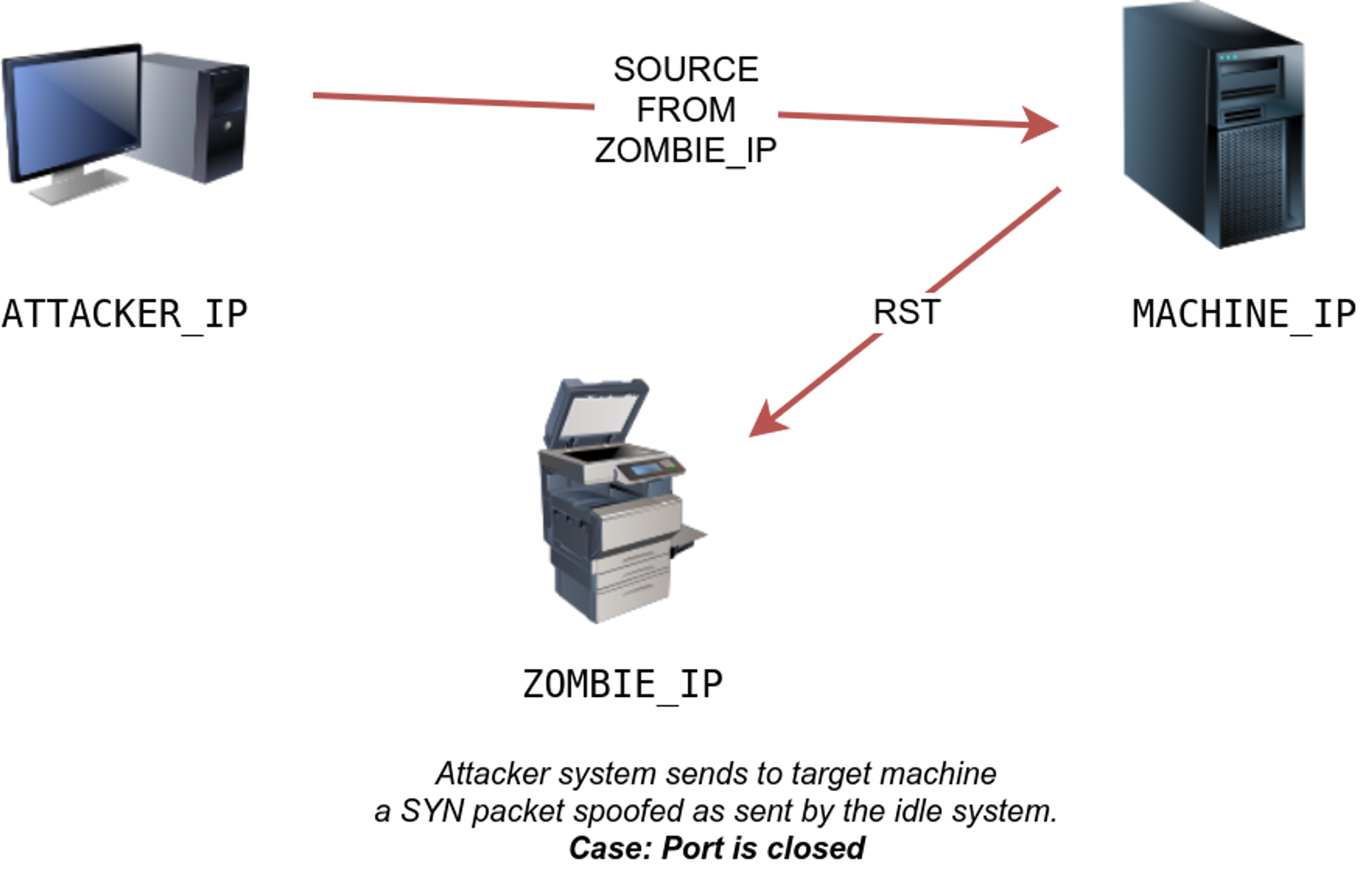
SCENEARIO 1: Port closed
The TCP port is closed; therefore, the target machine responds to the idle host with an RST packet. The idle host does not respond; hence its IP ID is not incremented.
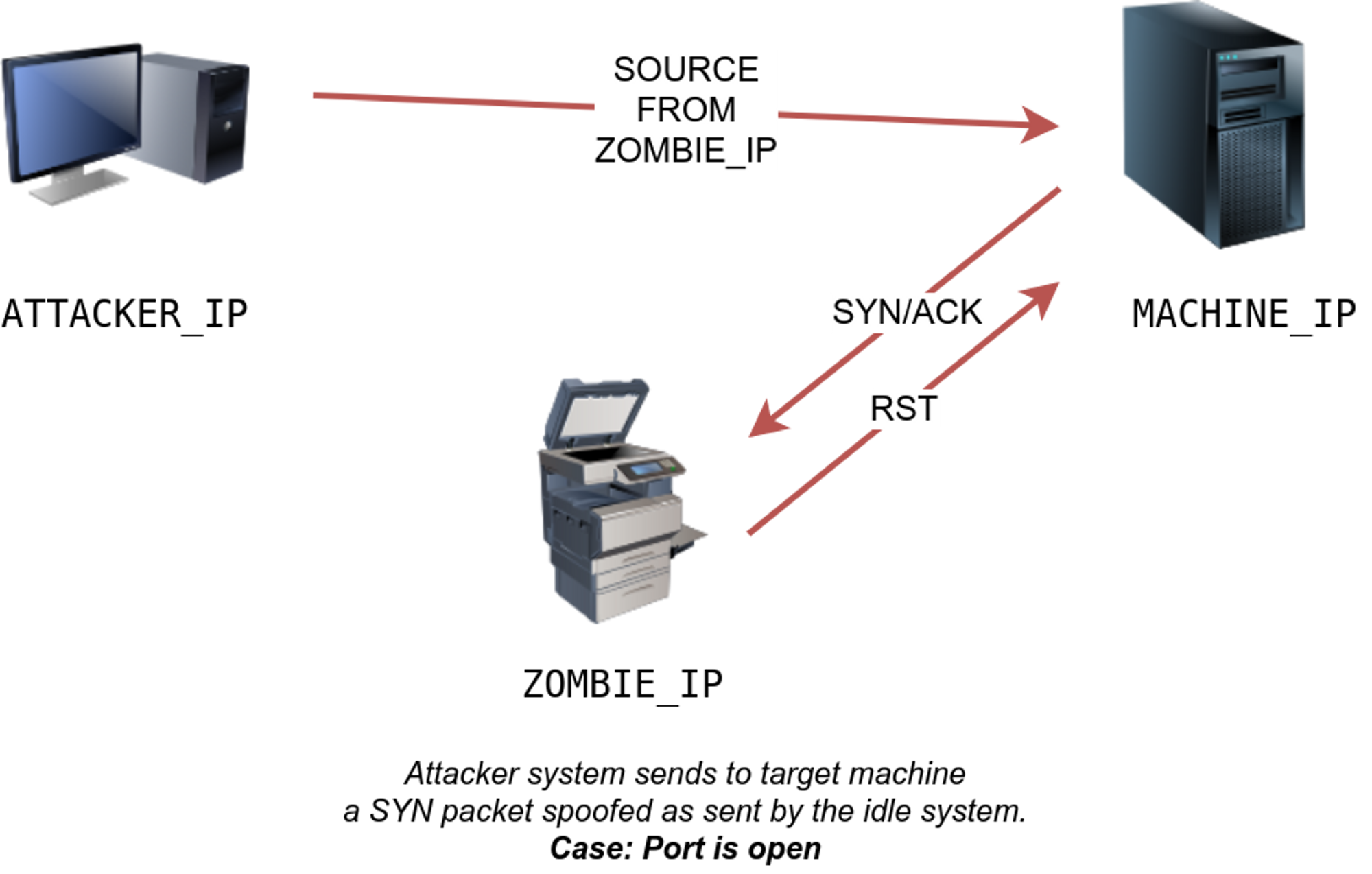
Scenario 2 : Port open
TCP port is open, so the target machine responds with a SYN/ACK to the idle host (zombie). The idle host responds to this unexpected packet with an RST packet, thus incrementing its IP ID.
Scenario 3 :
In the third scenario, the target machine does not respond at all due to firewall rules. This lack of response will lead to the same result as with the closed port; the idle host won’t increase the IP ID.
nmap -sI ZOMBIE_IP MACHINE_IP
🐱👤 Spoofing and Decoys:
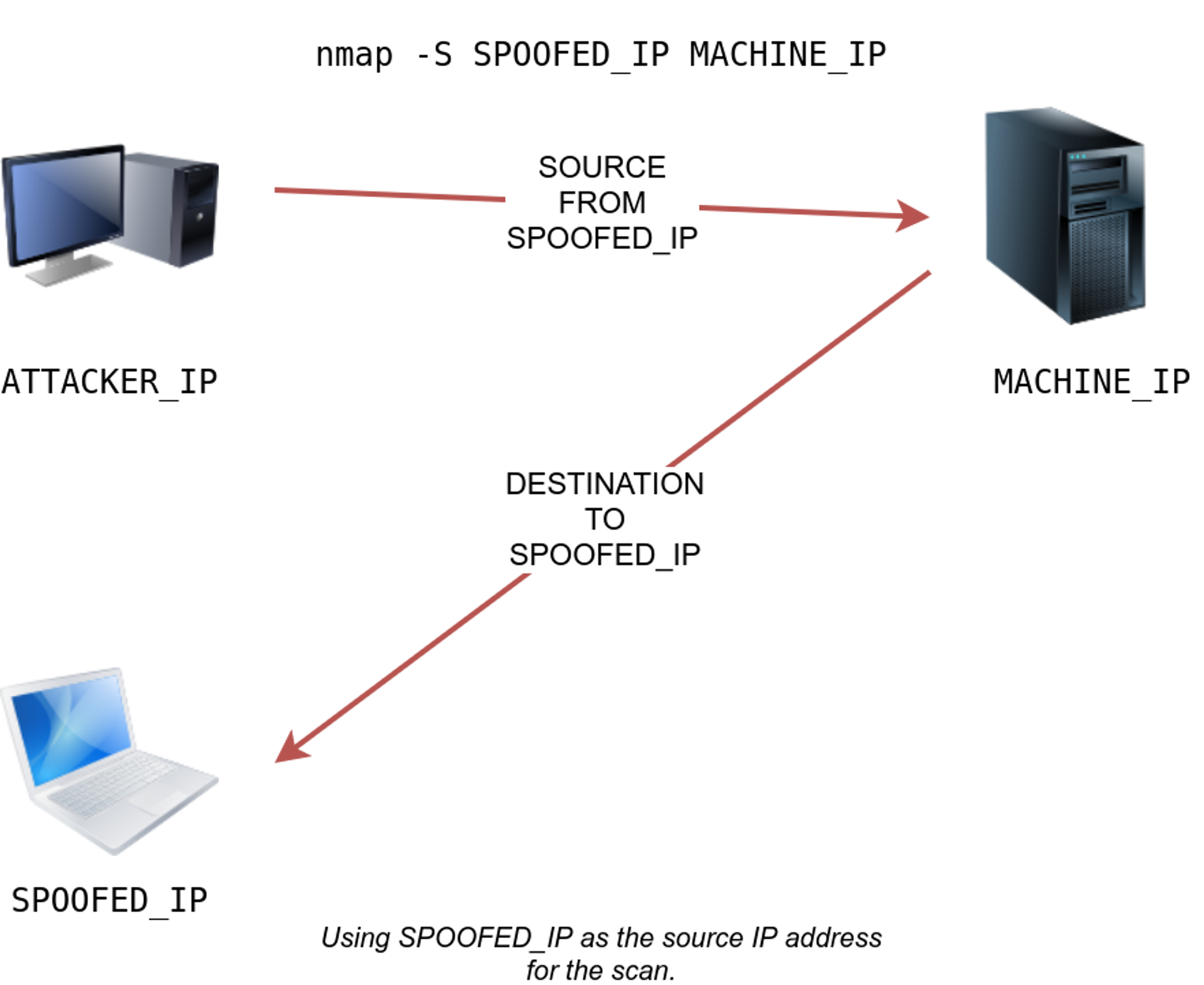
SPOOFING : -S
Nmap will craft all the packets using the provided source IP address SPOOFED_IP. The target machine will respond to the incoming packets sending the replies to the destination IP address SPOOFED_IP.
scanning with a spoofed IP address is three steps:
- Attacker sends a packet with a spoofed source IP address to the target machine.
- Target machine replies to the spoofed IP address as the destination.
- Attacker captures the replies to figure out open ports.
When you are on the same subnet as the target machine, you would be able to spoof your MAC address as well. You can specify the source MAC address using -spoof-mac SPOOFED_MAC
nmap -S SPOOFED_IP MACHINE_IP
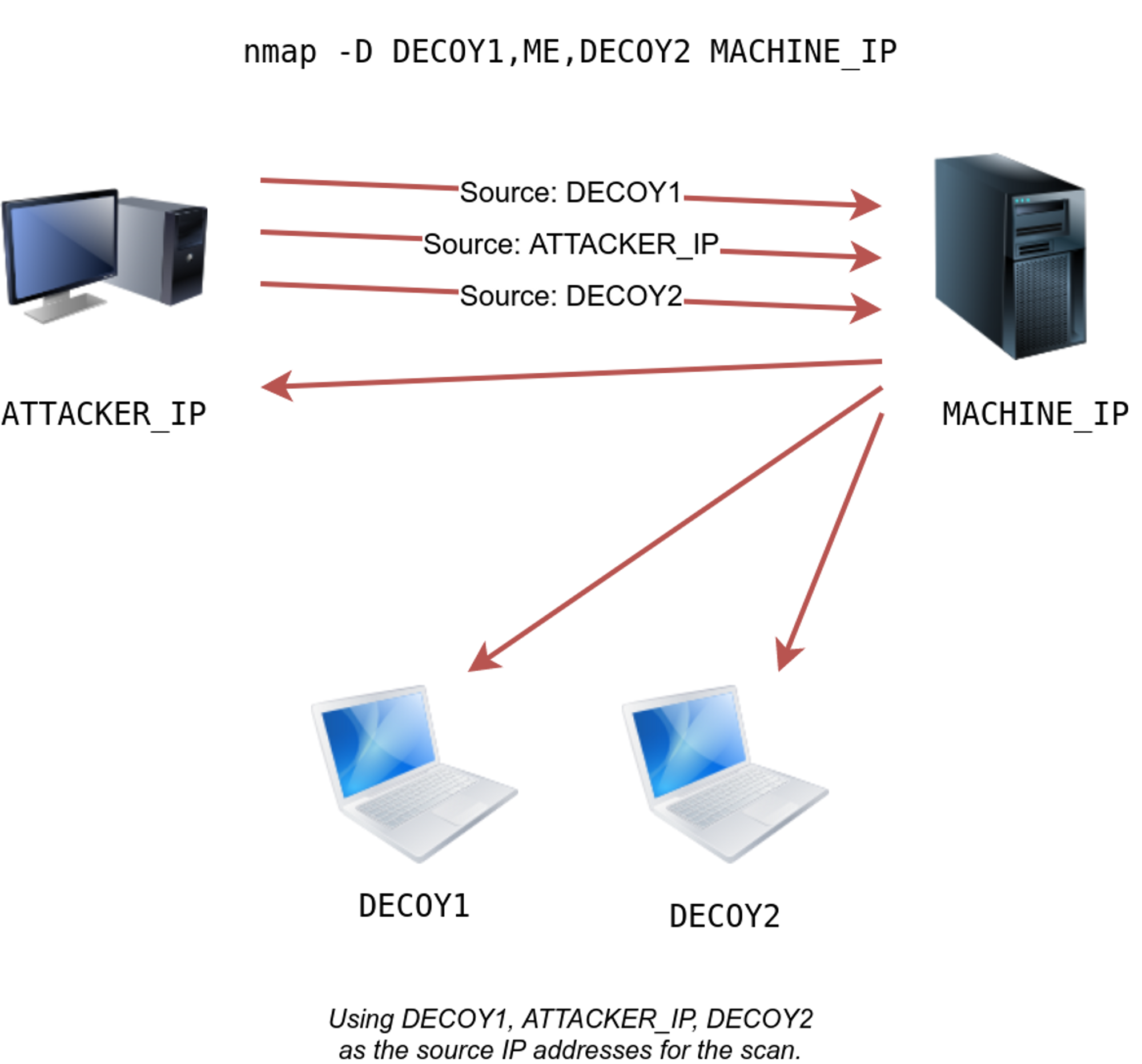
Decoys: -D
In this we make the scan appear to be coming from many IP addresses so that the attacker’s IP address would be lost among them.
nmap -D 10.10.0.1 , 10.10.0.2 , ME MACHINE_IP
⚡ Getting more info :-
- –reason : if you want Nmap to provide more details regarding its reasoning and conclusions
- -v, -vv : you can consider using -v for verbose output or -vv for even more verbosity.
📌 Output :
There are four ways through which we can save the output of nmap scan .
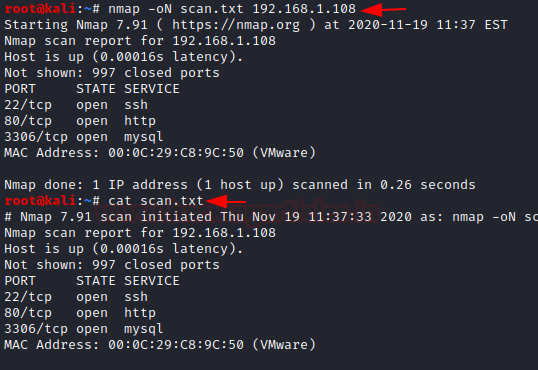
⚡ Normal -oN
As the name implies, the normal format is similar to the output you get on the screen when scanning a target. All the output is just transfered to the a file .
nmap -oN [filename] [target]
⚡ Grepable -oG
It makes filtering the scan output for specific keywords or terms efficient
nmap -oG [filename] [target]
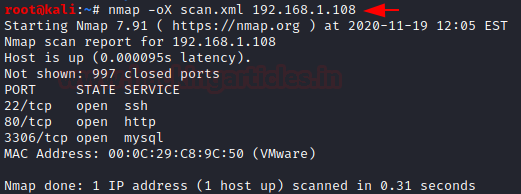
⚡ XML -oX
The XML format would be most convenient to process the output in other programs.
When an XML report is generated, it contains information like an executed command, Host and port states, Nmap Scripting Engine output Services, Timestamps, Run statistics and debugging information.
nmap -oX [filename] [target]
 ]
]
Sometimes, Pentesters prefer getting an html stylesheet as their report as it gives much-organised scan results:
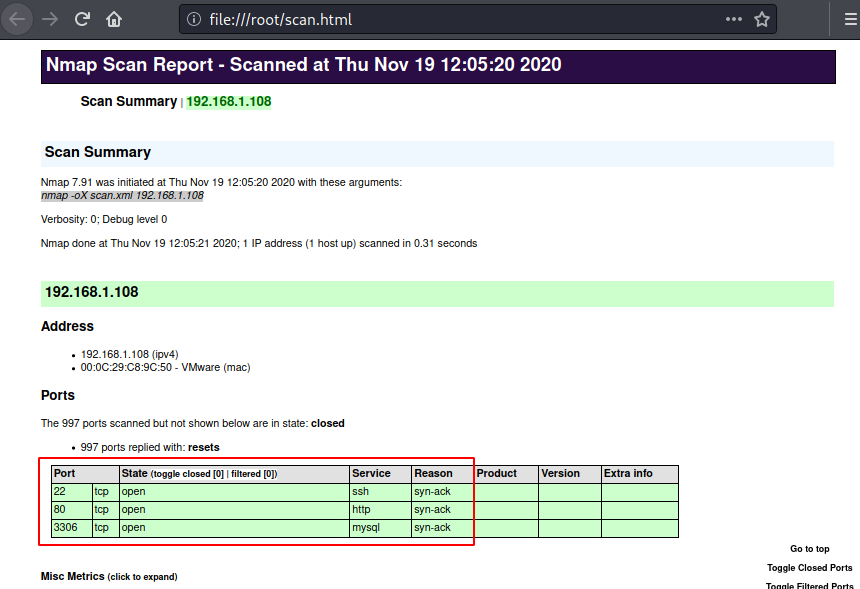
⚡ Script kiddie -sS
useless format 🙁
e.g
nmap -sS 127.0.0.1 -oS FILENAME
🦀 Sources Used :
- Nmap : Tryhackme rooms Series | Link
- The Official Nmap Project Guide to Network Discovery and Security Scanning | Link to buy