Analysis of Malicous APK using MobSF (Part 1)
What is APK:
APK files are a sort of zip or package that include resource files and.dex files. Apk files can only be installed on an Android device.
Android applications can be infected with malware. The main purposes of these malwares are to spy on people or to steal private data.
Installation of Mobsf
Installing using docker:
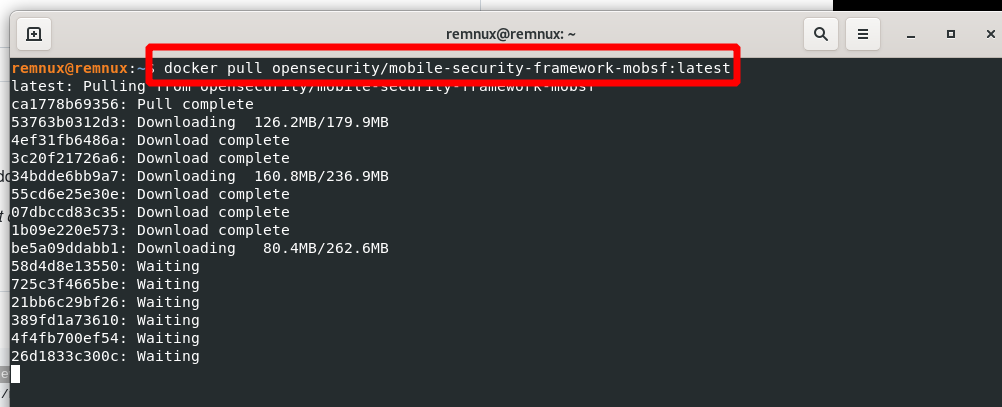
Run:
docker pull opensecurity/mobile-security-framework-mobsf:latest
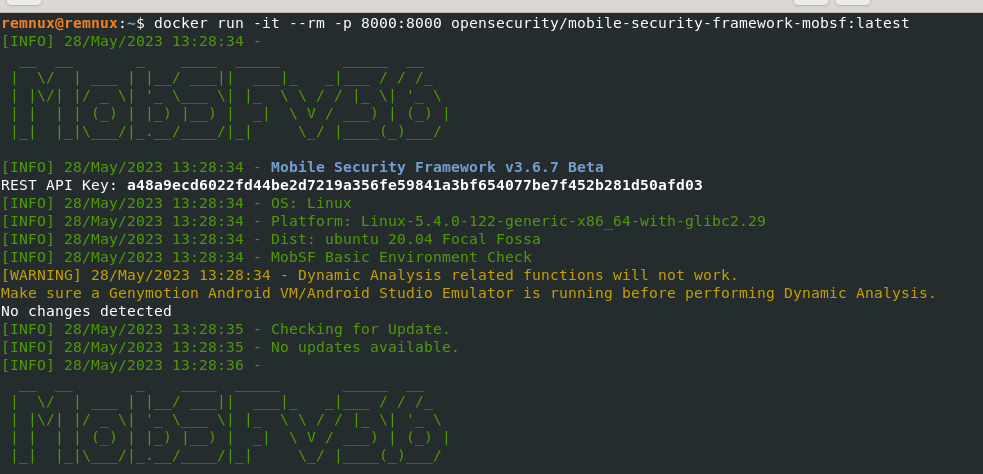
Run:
docker run -it --rm -p 8000:8000 opensecurity/mobile-security-framework-mobsf:latest
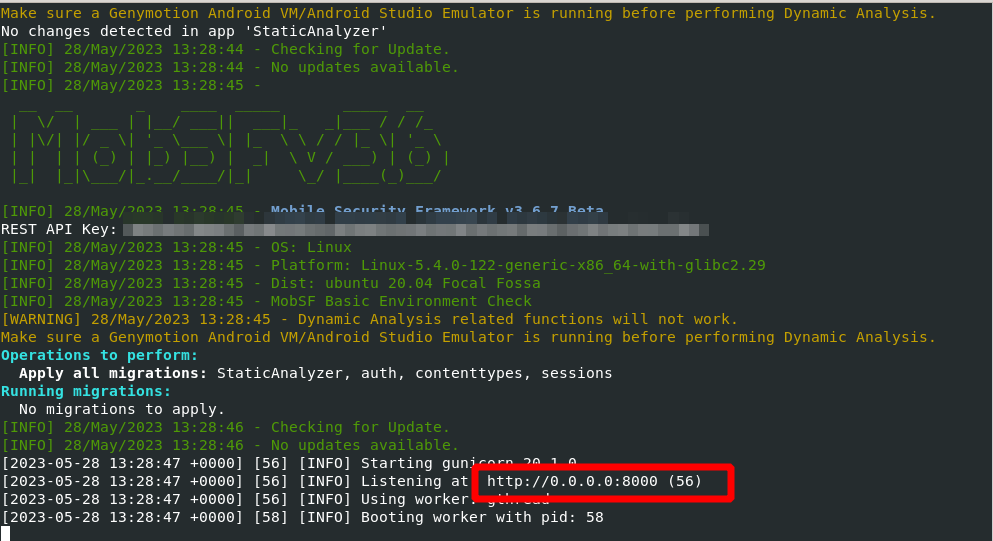
Now open http://0.0.0.0/8080 in web browser to access Mobsf
Malware for Practice:
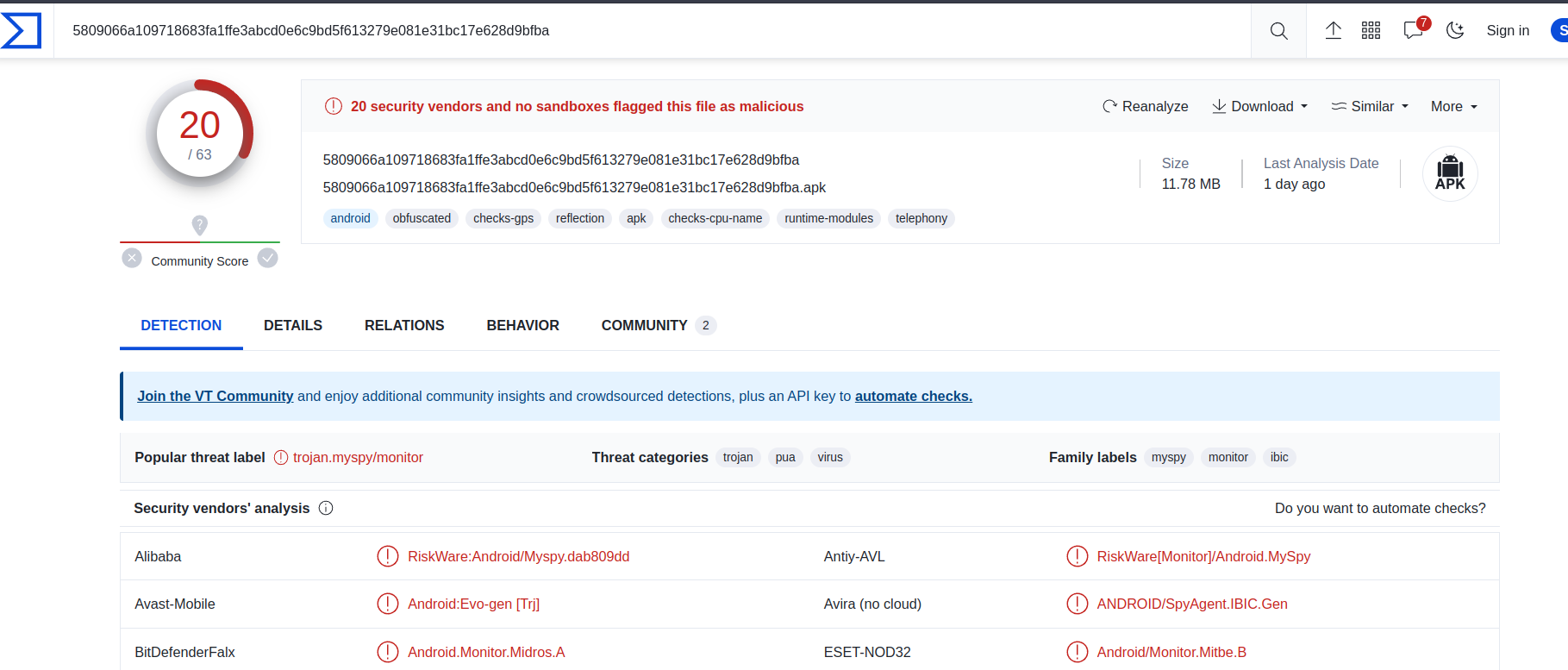
https://bazaar.abuse.ch/download/5809066a109718683fa1ffe3abcd0e6c9bd5f613279e081e31bc17e628d9bfba/
Practical Time:
Upload apk file to Mobsf
Wait for some time:

Now Analyze the Result
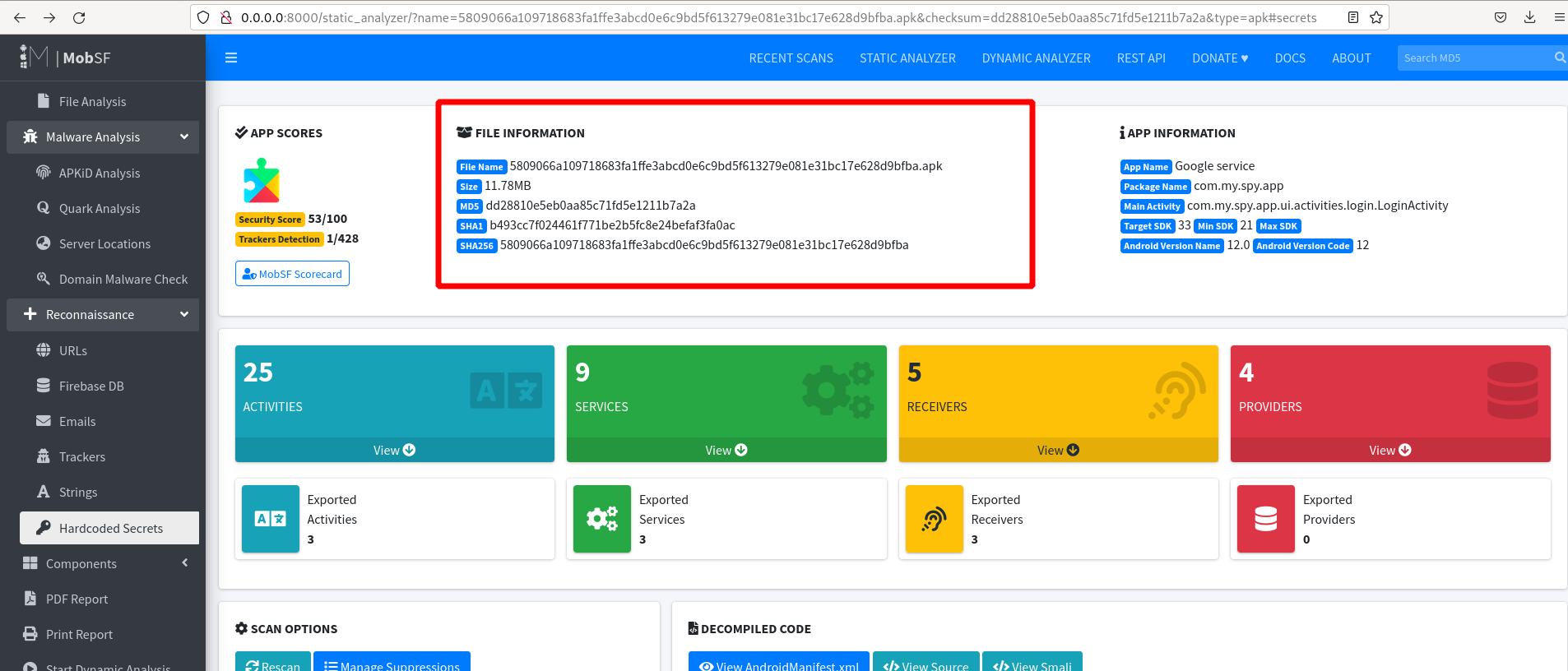
The mobsf result dashboard is shown here. After analysing the metadata of the apk and the manifest.xml file, this includes information about the APK.
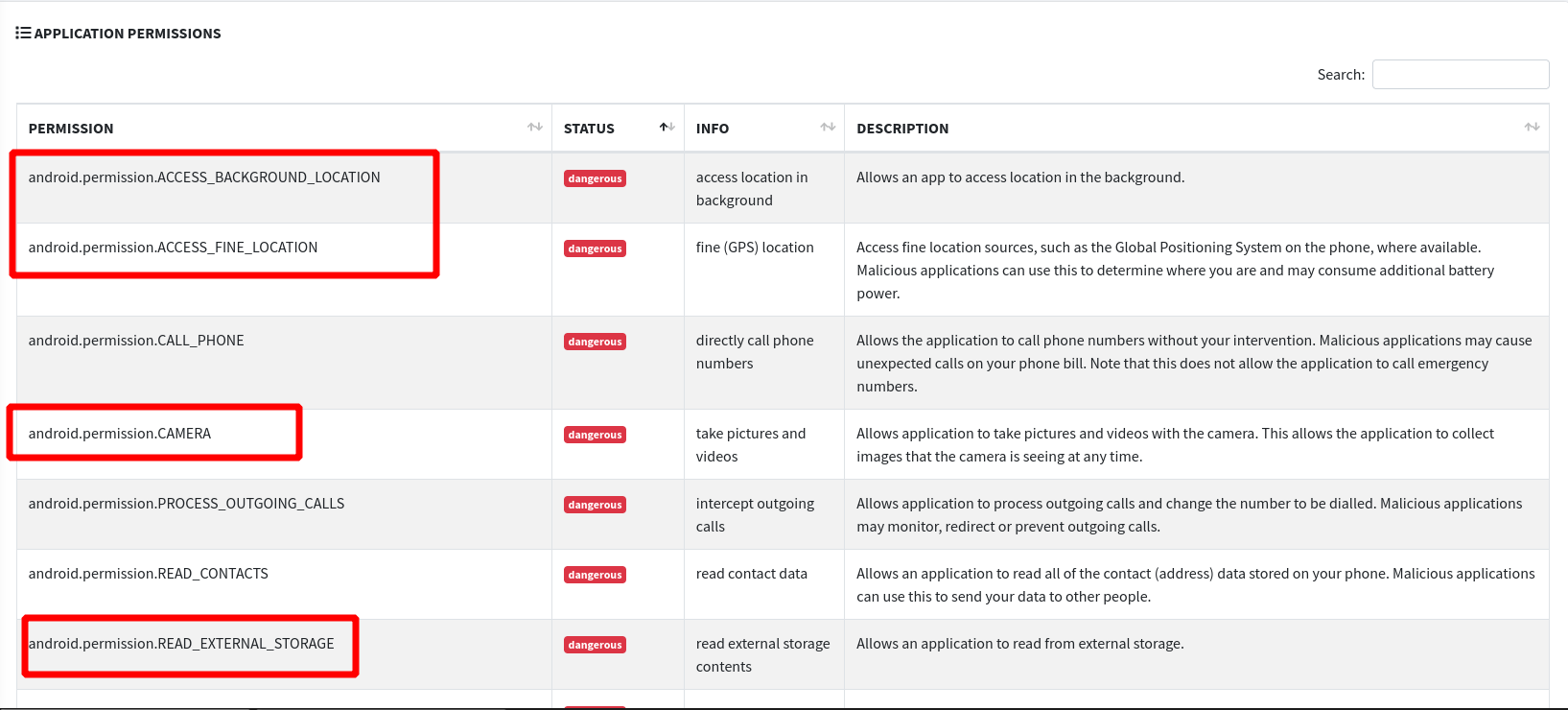
It indicates if a programme is obtaining sensitive or risky permissions.
Some dangerous permissions are:
- GEO location
- Calling
- Camera
- External Storage
- etc..
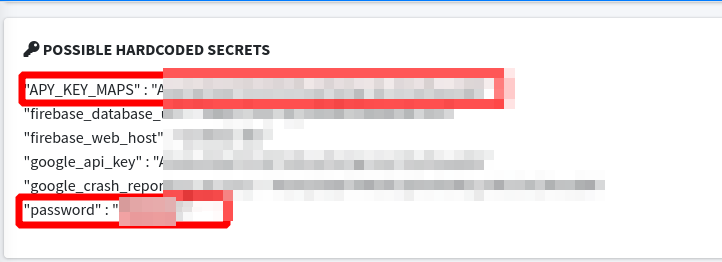
Upon examining the apk’s source code, MobSf also assists in identifying any potentially sensitive hardcoded strings.
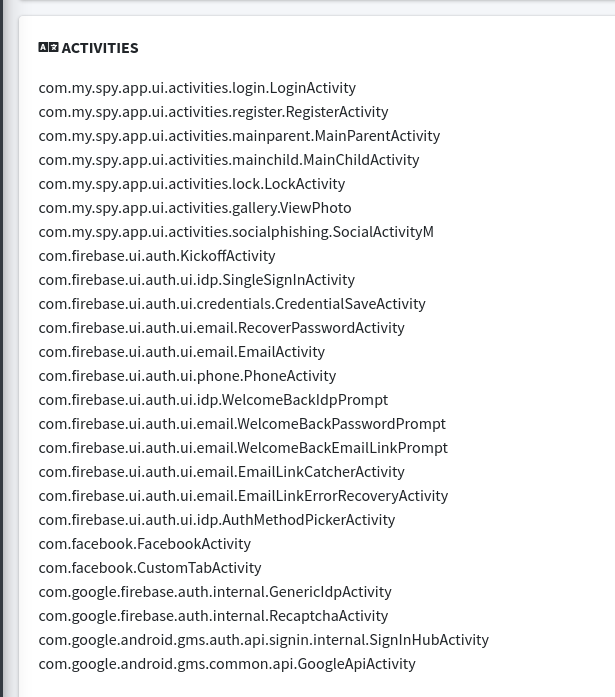
Some important Activities discovered by tool:
Analysis of Source Code:
Lets see some important activities:
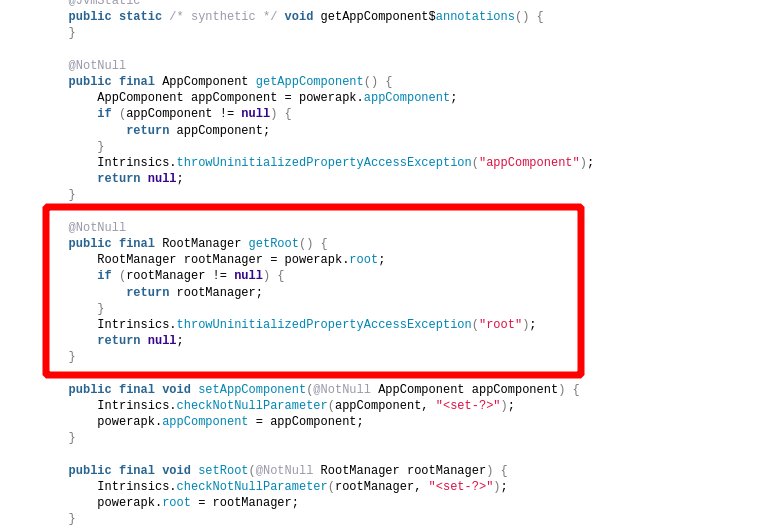
There is powerapk.java file that has function related to root access.
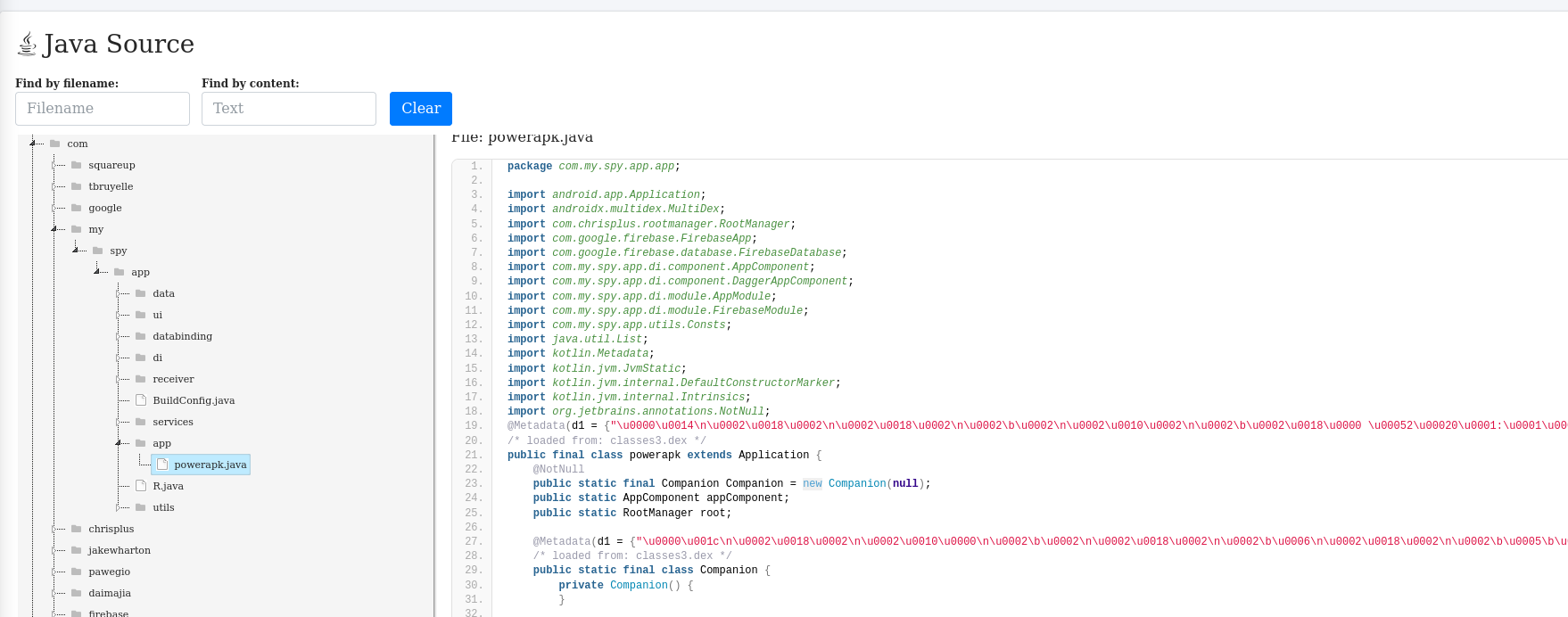
Function that help to manage root access on rooted android devices:
LoginActivity.java
This activity contain login functionality.
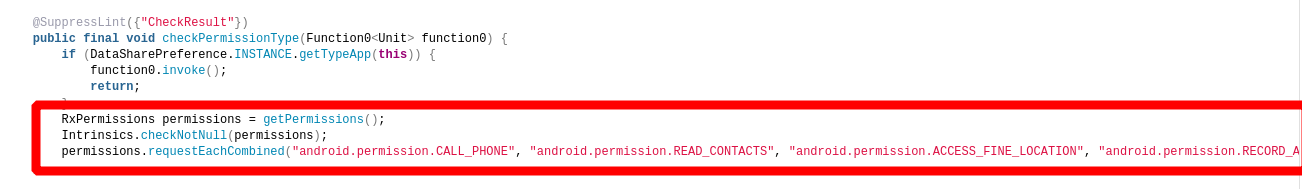
As seen in below picture, permissions that application access:
Some Other Activities that needs to check:
As of now, we are aware of the fundamental features that an application has.

After that, we may do dynamic application testing to better understand how applications function.
Refernces:
🤙 Contact: